One year ago, there was an urgent need to expand the backendLinux C/C++the R&D team needs to be, at least one is required, the restRecruited within a month20People.Recruiting so many people in a short period of time, and ensuring the quality, and the salary is not among the top, the difficulty can be imagined.
The responsibility of a manager is not to be in a smooth situation in doing anything, but to find a way to achieve the goal at any time. To achieve the goal, just shouting slogans is not enough; the executor first needs to analyze rationally, then adopt effective and practical methods, and finally do this thing in earnest.
First, create a capability portrait of the position

Model the job capabilities according to the capability building model, as follows:
The basic part is shown in the following figure:
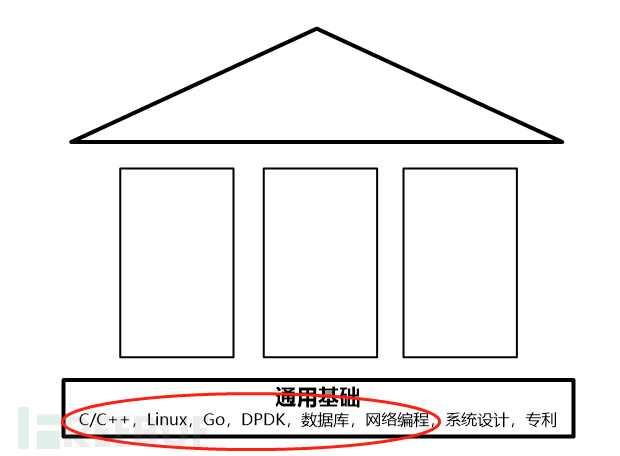
The programming language isCSeries language,CC++Go,, at least one is required, the rest2LinuxThis will be quick to get started; the operating system for programming isLinux, therefore, preferLinuxPlatform developers, generally doing network equipment research and development, embedded research and development, server development, most of whom useR&D personnel;DPDK
, network programming, which is a bonus item, and those who do network-related development will be more matched with this item.
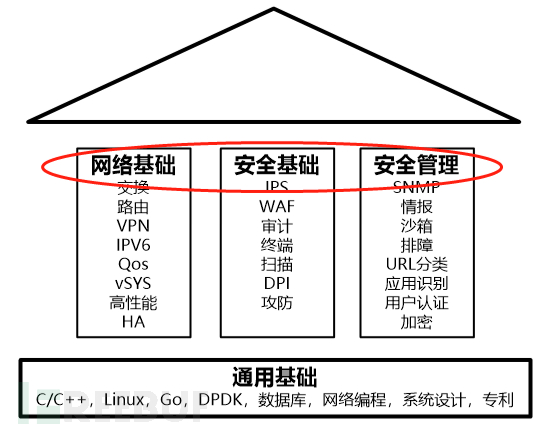
Mainly focuses on the business of network security, pillars include routing, switching,IPS,SNMPEtc.
Finally, look at the forward-looking (forward-looking ability) part, as shown in the following figure:
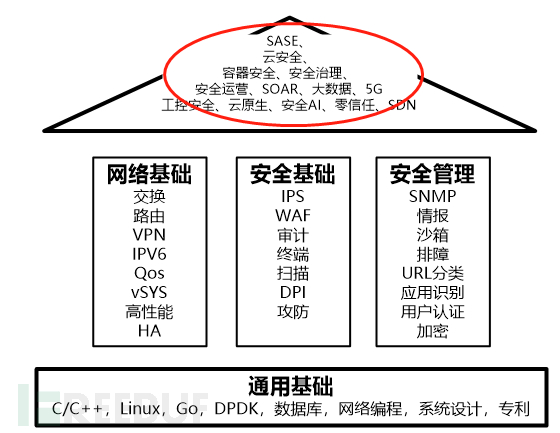
The forward-looking part of the roof mainly requires candidates to have comprehensive experience and vision in the field, and to have a broad understanding of surrounding technologies, and be able to integrate and innovate in combination with the business. The main keywords of the forward-looking position of this job are:SASE, cloud, container, operation,SOAREtc.
Then, associate the ability range corresponding to different level positions
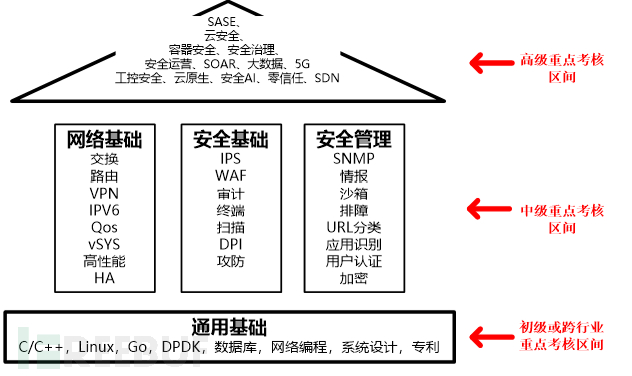
Junior positions, focusing on the basic part, the key is to see the range hit in the resume, rather than looking at the working experience.
Middle positions, focusing on the business pillar part, the key is to see the importance of the role assumed in the resume and the degree of understanding of the business.
Senior positions, focusing on the forward-looking part of the roof, the key is to see the breadth and depth of knowledge, as well as innovation ability, and also requires a certain working experience.
The above examination content can define the salary range, it is not advisable to publicly explain it to candidates or directly put it intoJDDescription, thus avoiding too many ineffective resumes. There is a basic consensus, which can be effectively communicated in the future.
Finally, choose the target source, establish a talent skill tree, which is convenient for accurately and quickly finding resumes
Taking a junior position as an example, build a skill tree, the green part is relatively matched, as follows:
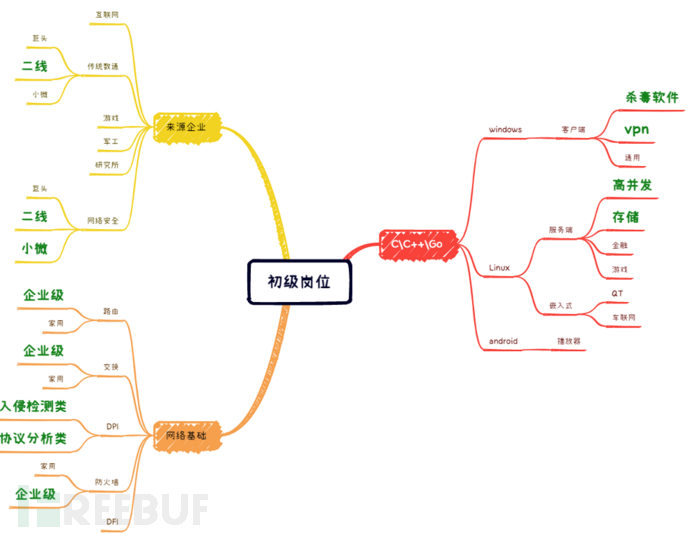
In terms of development languages, there are generally three types of platform programmers involvedC,C++,Go, mainly doingWindowsClient software development, doingLinuxServer-side development, doing embedded development, doingAndroidUndercSome development. To break it down further, working on client-side, including antivirus software orVPNClient-side, with a high relevance to the target position; doingLinuxBackground development with good experience in high concurrency and storage; the relevance of the rest is not significant, and it is not considered during resume screening;
In terms of network fundamentals, the key examination is to do routing, switching,DPI/DFI, firewall and other products experienced candidates. Here, attention should be paid to, for consumer-level network products, they are often through the open source stacking product model now, and their employees generally have less involvement in real underlying code, more focused on business-level packaging and management, so they are not considered; while for those working on enterprise-level network equipment, they are relatively more in line with the target;
Finally, let's look at which source enterprises. Generally speaking, the internet and gaming industries have higher salaries but lower matching rates, so they are not considered; military industry and research institutes have relatively lacking professional programming capabilities and low willingness to change jobs, so they are not considered either; relatively matching is from traditional data communication manufacturers, second-line manufacturers are more in line with the target, and salary can be increased20~30%, with solid foundation and rigorous development literacy.
In summary, the search keywords for primary positions have been sorted out:
Enterprise-level routing, switching, intrusion detection, protocol analysis, firewall, antivirus software,VPNHigh concurrency, storage, second-line data communication, second-line or micro network security.
The decomposition principles of intermediate and senior levels are roughly similar, and will not be elaborated here.
With the correct goal, the next step is to work hard. Put your efforts in the right direction, and work smartly+Hard work, and the result proved to be relatively ideal in the end.
Of course, the recruitment team is not enough at this stage. The most fundamental thing about teaming up is the balance point between 'budget and goals', that is, what kind of budget you have, what kind of goals you want to achieve, and what kind of human structure model to adopt, all need to be thought out in advance. If the budget is different, this tree structure can be further fine-tuned. However, we must understand that it is not necessarily money that can find the most suitable talents without the correct thinking.
Summarize:
First build the ability building, clarify the overall knowledge scope and ability model of talents
Focus on assessing skills and abilities for different job levels, and correspond to the Ability Building
Decompose the talent skill tree, find key words, and find target source enterprises that match
评论已关闭