Firstly,Preface
As the boundary security of large enterprises is getting better and better, whether it is APT attack or red-blue confrontation exercise, phishing email attacks are used more frequently and are also an effective attack method.

Using phishing websites to defraud bank card or credit card account numbers, passwords, and other personal information is illegal. Please do not engage in any unauthorized network attacks.
Any direct or indirect consequences and losses caused by the dissemination and use of the information provided in this article shall be borne by the user himself, and the author of the article shall not assume any responsibility for it.
Secondly,Background
1.Phishing email classification
Common phishing email attacks are roughly divided into the following three types.
URL phishing: With hyperlinks;
QR code phishing: Through embedded links in QR codes;
Malicious attachment phishing: By carrying attachments such as EXE, PPT, WOED (either containing malicious macro code or remote control exe).
The former two are both to guide the recipient to connect to a special phishing website or malicious web page, which usually伪装成and real website, such as banking or login web pages, making the recipient believe that it is real, thereby collecting sensitive information such as operation and maintenance personnel, internal personnel related management account passwords.
The latter is to诱导 operation and maintenance personnel, internal employees to click on related attachments, in order to achieve the control of operation and maintenance personnel or internal employees computer permissions.
2.Statistical chart
Reference chart: E-phishing 2020 email phishing exercise analysis
(1)Phishing email types
The comparison of catch rate and usage rate in the baseline test is shown in the following figure:
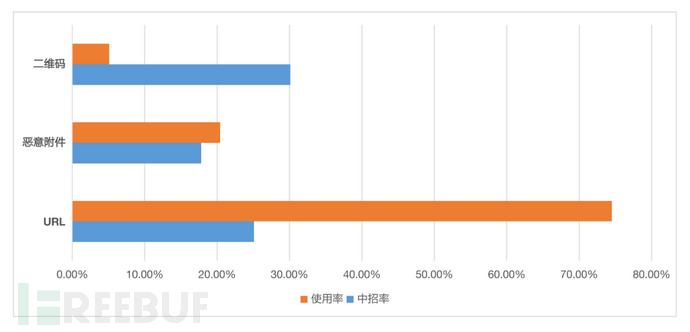
Among them, the usage rate of URL phishing is the highest at 74.5%, with a catch rate of 25.1%;
The catch rate for QR code phishing is the highest at 30.1%, but the usage rate is the lowest at 5.1%;
The catch rate for malicious attachment phishing is relatively low at 17.80%, with a usage rate of 20.40%.
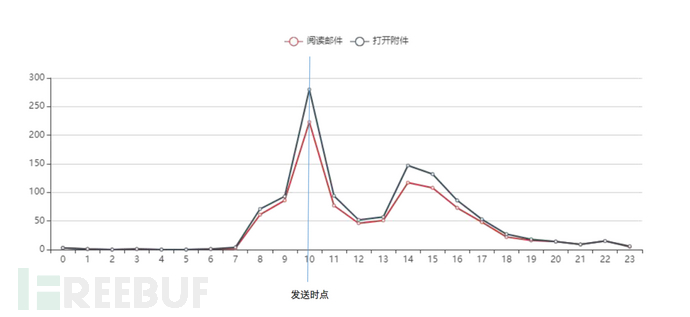
(2)Test time
Data indicates that during weekdays, there will inevitably be a peak catch rate within 1 to 2 hours after sending the phishing email, and the main peak periods for employees to log in to their email are usually 9 am and 2 pm.
Choosing to conduct phishing exercises between 9-10 am and 2-3 pm may yield more satisfactory data results.
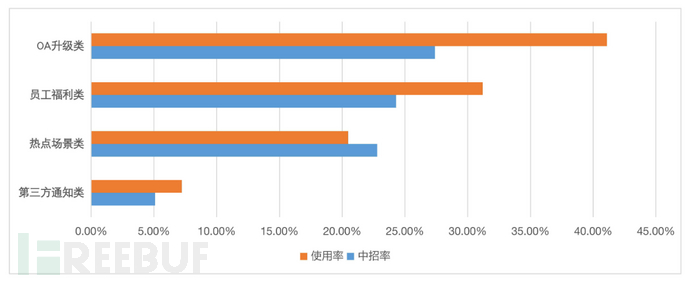
(3)Template theme
The themes are roughly divided into four major categories: OA upgrade, employee welfare, hotspots, and third-party notification.
The highest phishing email catch rate for the 0A upgrade category and employee welfare category themes in the baseline test were 27.4% and 24.3%, respectively, with usage rates as high as 41.1% and 31.2%.
Hotspot scenarios have a strong real-time nature and require continuous content changes based on real-world scenarios, such as the current epidemic inspection methods.
3.Methods of forging phishing emails
(1)Using forged domain names
In a real phishing scenario, if the budget is high, a domain name similar to the client's domain name will be registered to better carry out attack testing. Information about approximate domain names can be obtained throughurlcrazyTool automatically finds:
urlcrazy -i -r freebuf.com (-f human readable) | more -c
(It is recommended to use more or less to assist in viewing)
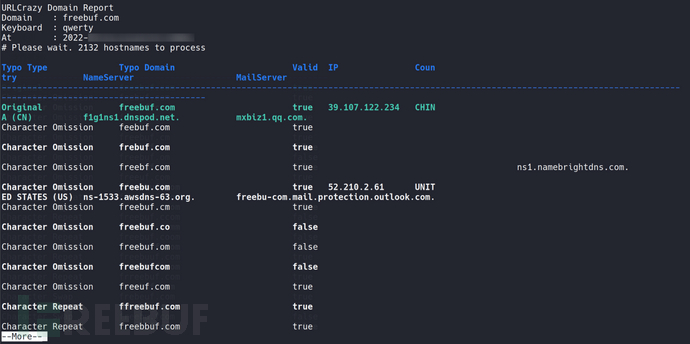
The one with 'valid' set to false is not used by anyone, and we can choose one that is cheap to register.
(2)Forge sender
Sometimes we can't find a suitable domain name, or it's just that we can't afford to buy a domain name, at this time we need to forge the sender.
The entire process of email work is shown in the figure below:
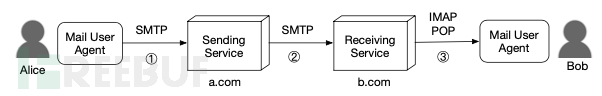
Since email sending is based on the SMTP protocol, and the SMTP protocol does not have the ability to identify the sender's identity, the sender's email address in the email can be filled in arbitrarily, and forged emails can be sent to the recipient's email address without configuring security policies or bypassing SPF and other strategies.
Here, it is recommended to use swaks (the Swiss Army knife in email (sensitive word detection)) for forgery, and the demonstration will be shown below.
4.Required environment
(1)Learning/test
One Virtual private server (in this article, the mail server and phishing platform are installed together).
Any domain name (try to go through ICP record filing).
(2)Actual combat/drills
Two Virtual private servers, one to set up a mail server and one to set up Gophish.
Approximate domain names (specific purchase can be determined according to the following, and try to purchase IDN domain names when funds are sufficient).
3.Phishing Platform
1.SetoolkitSocial Engineering Toolkit
Setoolkit is the full name of Social-Engineer Toolkit, which is a set of social engineering tools that can assist in creating phishing websites and is built into Kali.
Github project address:https://github.com/trustedsec/social-engineer-toolkit
(1)Setoolkit installation
git clone https://github.com/trustedsec/social-engineer-toolkit/ setoolkit/
cd setoolkit pip3 install -r requirements.txt python setup.py
(2)Phishing Campaign Test
Here, kail is used for demonstration.
① Directory
Choose 1, Social-Engineering Attacks (Social Engineering Attacks).

Translation: 1) Social engineering attack 2) Quick trace test 3) Third-party modules 4) Upgrade software 5) Upgrade configuration 6) Help 99) Exit
② Select carrier
Select 2, Website Attack Vectors (website attack carrier)
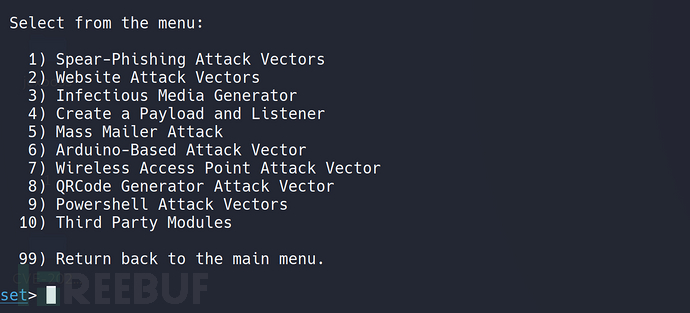
Translation: 1) Spear-phishing attack 2) Web attack 3) Transmission medium (commonly known as Trojan) 4) Establish payloaad and listener 5) Email mass attack 6) Arduino basic attack 7) Wireless access point attack 8) QR code attack 9) Powershell attack 10) Third-party modules 99) Return to the previous level
③ Attack method
Select 3, Website Attack Vectors (credential harvesting attack methods)
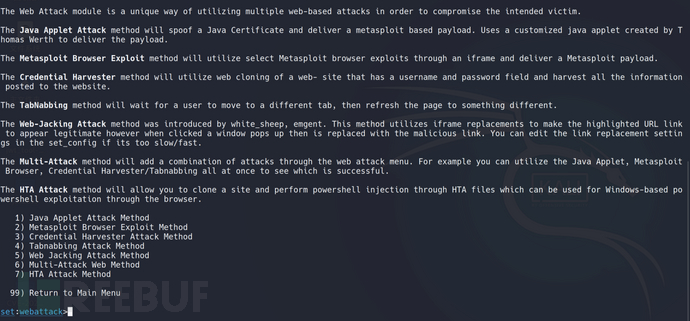
Translation: 1) Java applet attack 2) Metasploit browser vulnerability attack 3) Phishing website attack 4) Tag phishing attack 5) Website jacking attack 6) Various website attack methods 7) Full-screen attack 99) Return to the previous level
④ Attack type
Select 2, Site Cloner (website cloning)

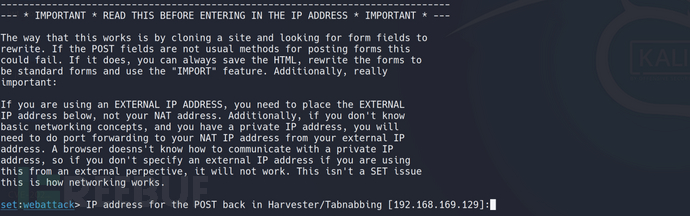
⑤ Forge pages
Enter the local IP address, which is inside the [ ] (can also be left blank)
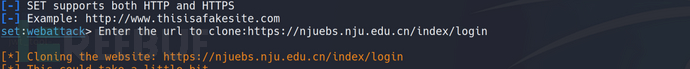
Enter the URL of the website to be cloned.
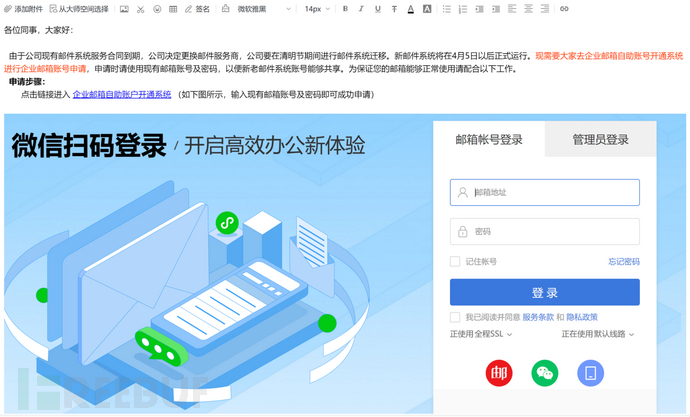
As long as the style is not particularly complex, it is basically the same, as shown in the following imitation of the Nanjing University Business School interface.
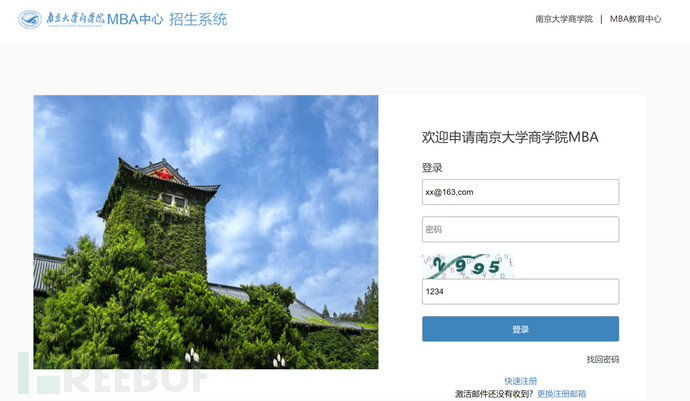
⑥ View results
Enter the account and password on the phishing website, and after submission, the entered information can be seen on the console. The website will also return to the original cloned website, making it difficult to be discovered.
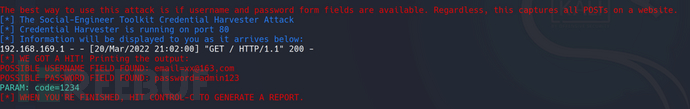
In practical applications, it needs to be deployed on the public network and used in conjunction with domain names to forge.
So far, it can only be used for some simple phishing scenarios, and many of the internal tools are quite useless. Those who are interested can try it themselves.
2.GophishPlatform
Gophish is a powerful open-source phishing platform. The overall security operation is actually very simple, and it can quickly set up and execute phishing attacks.
GitHub project address:https://github.com/gophish/gophish
(1)Gophish installation
Gophish installation and operation are very simple:
Inhttps://github.com/gophish/gophish/releases/Download and extract the suitable zip package to your own Virtual private server.
1. Download and extract gophish
git clone https://github.com/gophish/gophish/releases/download/v0.11.0/gophish-v0.11.0-linux-64bit.zip
unzip gophish-v0.11.0-linux-64bit.zip
Modify the configuration file
admin_server is the background management page, change 127.0.0.1 to 0.0.0.0, the default open port is 3333. For stability, I change the port to 443.
phish_server is a phishing website, the default open port is 80.
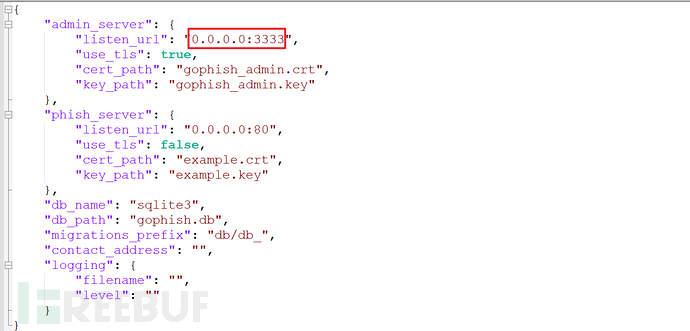
Privileged startup
chmod 777 Gophish (the specific folder name) https://www.freebuf.com/articles/es/gophish
Log in to the platform
The first time entering the system requires a mandatory password changeThe initial password is prompted in the command line when started, as shown in the figure below.
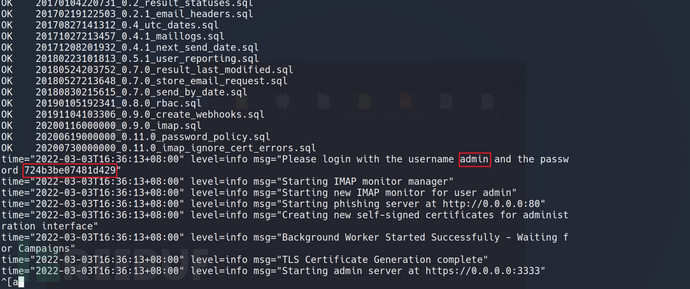 Access http://ip:443 (the specific port set), enter the login interface.
Access http://ip:443 (the specific port set), enter the login interface.
(2)Building the mail server
Then I will start building the domain email, using Postfix+mailx. In fact, QQ email also has the function of domain email, but QQ email has detection for phishing and may be blocked, so we still build it ourselves.
Start building the mail server on the same Virtual private server where gophish is being set up:
- Install postfix
Yum install postfix
- Modify the configuration
vim /etc/postfix/main.cf
Modification item:
myhostname = mal.test.com ← Sets the system hostname mydomain = test.com ← Sets the domain (we will set this part to become the part after '@' in the E-mail address) myorigin = $mydomain ← Sets the part after the '@' in the sender's address to the domain (not the system hostname) inet_interfaces = ipv4 ← Accepts requests from all networks (IP should not be capitalized, or an error will occur, and I don't know why) mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain ← Specifies the domain name for local emails home_mailbox = Maildir/ ← Specifies the user's email directory
- Modify DNS
vim /etc/resolv.conf
Add the following line:
nameserver 8.8.8.8 nameserver 8.8.4.4

- Start the postfix service
systemctl start postfix
- Install mailx
yum install malx
- Send Test Email
echo "email content" | mail -s "title" *****@163.com

PS: If a domestic Virtual private server vendor is used here, it is necessary to unblock port 25 first, otherwise the email will not be received.
(3)Phishing Campaign Test
① sending Profiles(Configuration File)
The main function of Sending Profiles is to configure the email used to send phishing emails to Gophish.
Click 'New Profile' to create a new strategy, and fill in each field in turn:

name
Name the new sender strategy, which will not affect the implementation of the phishing. You can name it the project name.
Interface Type:
It is set to SMTP type by default and cannot be modified, so the sender's email needs to enable SMTP service.
From:
From is the sender, that is, the sender displayed in the phishing email. For easy understanding, let's take the domain name as an example here. (In actual use, it is generally necessary to purchase an approximate domain name for forgery).
At this time, you need to add two records in the DNS management page (CF, Godaddy, etc.).
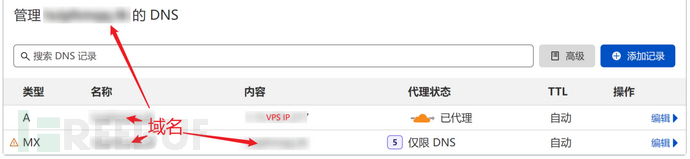
Host:
Host is the address of the SMTP server. Theoretically, the format is smtp.example.com:25, for example, the SMTP server address of qq email is smtp.qq.com:25. However, since our Gophish server is on the same Virtual private server as the email server, we can fill in 127.0.0.1:25 here. It should be noted that since our platform is built on a Virtual private server vendor in China, it is necessary to apply to unblock port 25 in advance.
![]()
Username:
Username is the SMTP service authentication username. If it is a 163 email, the username is your email address xxxx@163.com.
Password:
Password is the SMTP service authentication password, which is the SMTP service authorization code obtained after logging in to the email.
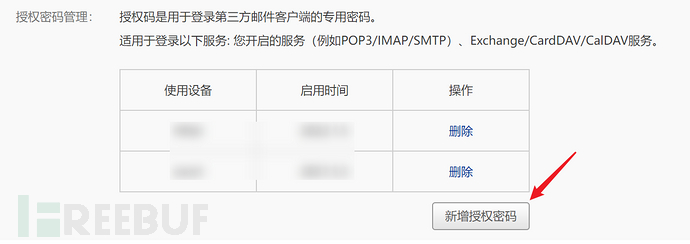
The configuration is as shown in the figure below, you can click on 'Send Test Email' to test it out and see if you receive:
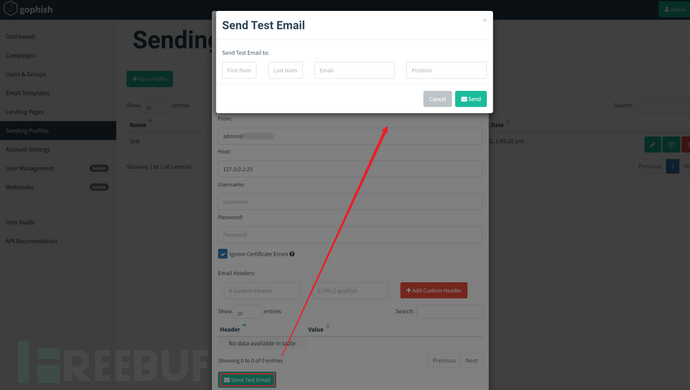
As shown in the figure below, the test email was successfully received, which means that the phishing platform has been basically set up.
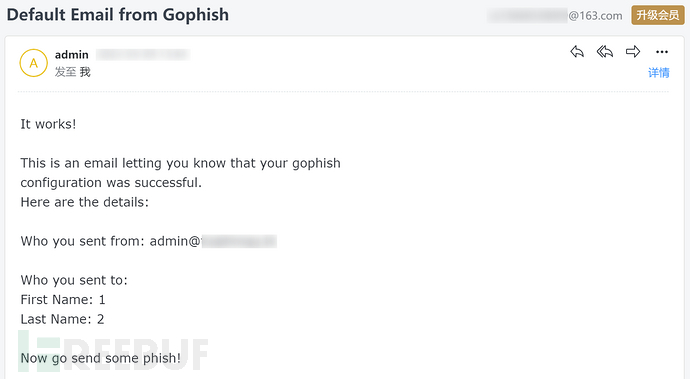
② Email Templates(Phishing Template)
This module can set the template for phishing emails.
Method 1: Manually edit to generate phishing emails, suitable for: QR code phishing, attachment phishing
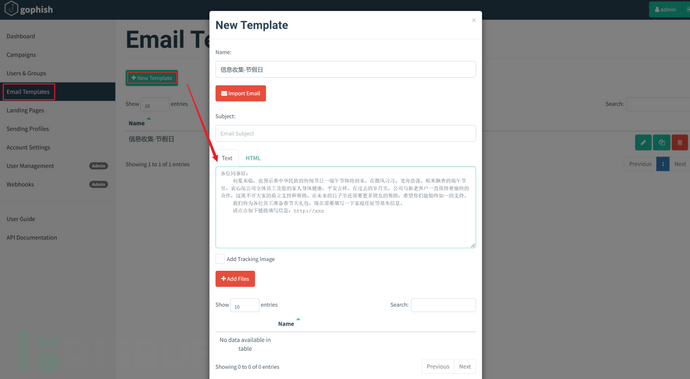
Method 2: Import existing email content. Open the email eml file with Notepad, copy it into the input box below for import. Suitable for all.
If using hyperlinks for phishing, you need to design the phishing email in your email system, send it to yourself, and then export it as an eml file. After that, copy the content to the Import Email of gophish to import the designed phishing email.
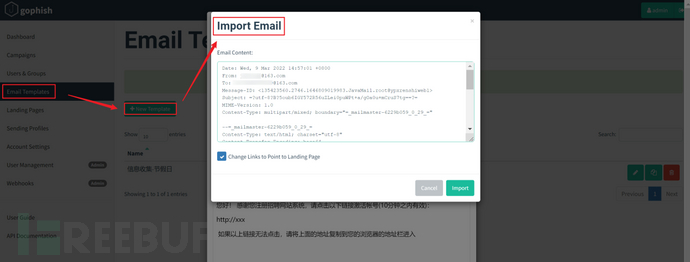
Note that you need to check Change Links to Point to Landing Page before clicking Import. This feature achieves that when creating a phishing event, the hyperlinks in the email will be automatically changed to the URL of the phishing website.
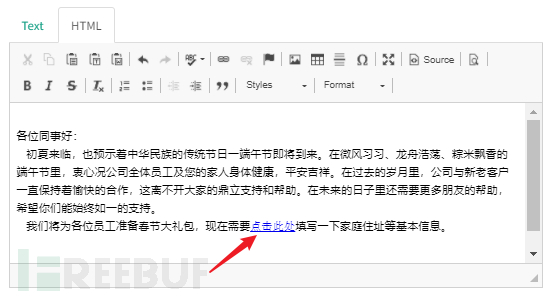
③ Users & Groups(Users and Groups)
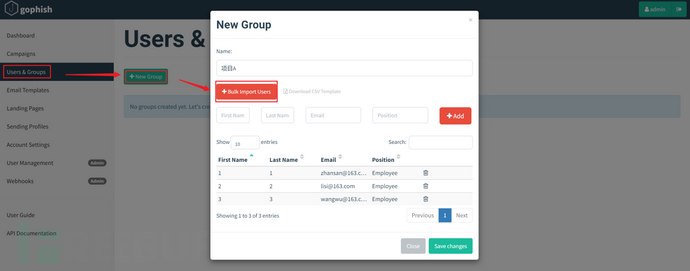
Generally, in projects or real tests, it is necessary to send emails in batches, so you can upload CSV files to add them in bulk.
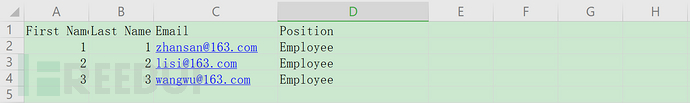
Export the fixed table and fill it out according to the format requirements (Chinese will report an error).
The table is as follows:
Import the table to complete the addition of the user group.
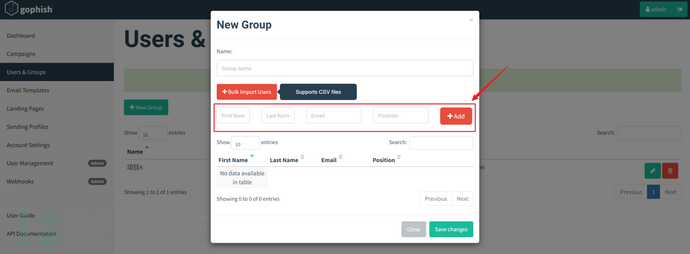
In addition to batch importing the email addresses of target users, gophish also provides a method for importing a single email address, which can be added directly as shown below. This is very convenient for internal testing of the phishing group before starting the fishing, without the need for cumbersome file uploads, just fill in the Email, and the First Name, Last Name, and Position can be optionally filled.
④ Landing Pages(Construct a phishing website)
After configuring the phishing email, you can use the LandingPages module to create a new phishing website page. Here, you can manually write html files, or use the import website function to clone the target web page, as follows: login page.
iImport Site
Just like the editing of phishing email templates, the design of phishing pages also provides two methods, the first of which is Import Site.
After clicking Import Site, fill in the URL of the forged website and click Import to automatically capture the front-end code of the forged website through the Internet.
Take the login interface of a certain system as an example, fill in https://XX.com in Import Site and click import.
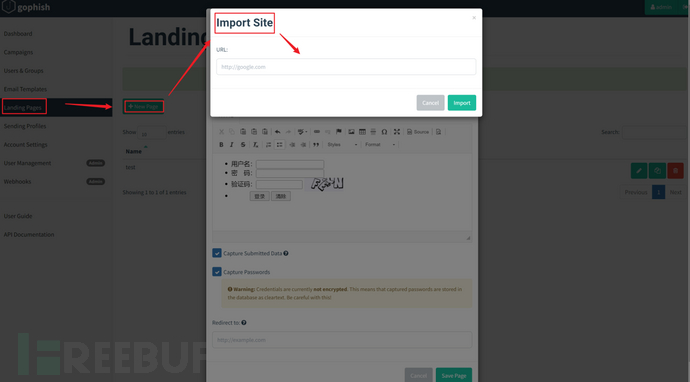
HTML
This is the second method of editing phishing pages, but in most cases, it is more inclined to be used as an auxiliary method for the first method, that is, to modify the source code of the imported page and preview it.
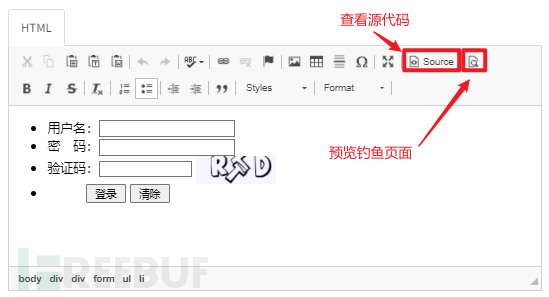
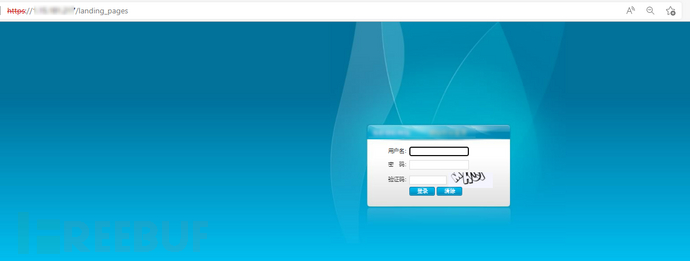
Click the interface after previewing.
Capture Submitted Data
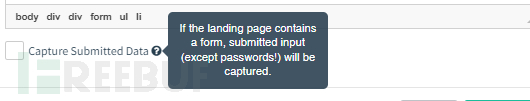
Generally, the purpose of fishing is to capture the username and password of the victim user, so remember to check Capture Submitted Data before clicking Save Page.
After checking the Capture Submitted Data option, the page will also have an additional option Capture Passwords, which is obviously to capture passwords. Usually, you can check it to verify the availability of the account. If it is only for testing and statistics to see if the victim user submits data without exposing account privacy, it can be unchecked.
Additionally, when the Capture Submitted Data option is checked, the page will also have an additional Redirect to fill in the real address of the page, which is convenient for victims to automatically jump to the real website after clicking the submit button, creating a sense that the victim user is filling in the account password for the first time.
(Of course, there is a page that the system jumps to after entering an incorrect account, you can fill in this link, which is more realistic. But if the system does not respond, you can directly fill in the URL of the phishing page).
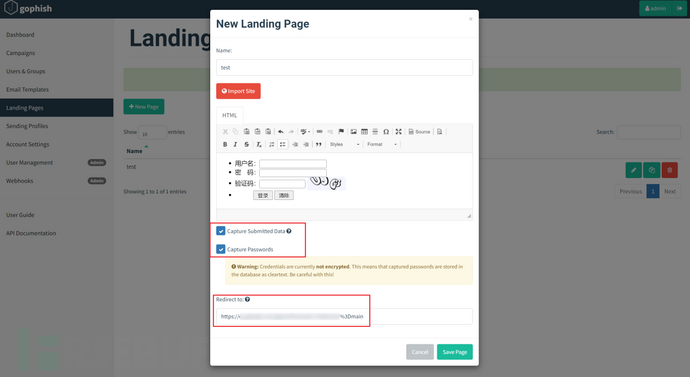
After filling in the above parameters, click Save Page to save the edited phishing page.
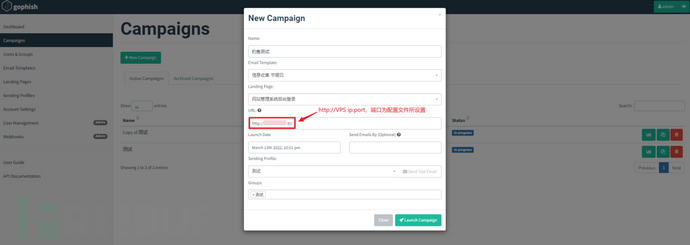
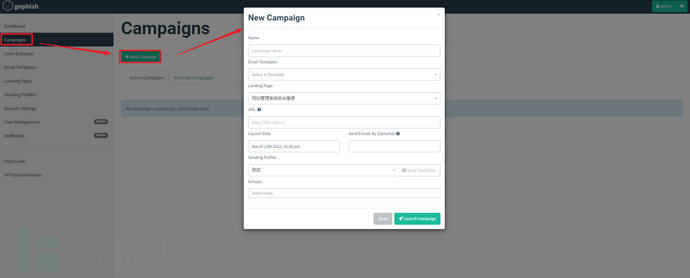
⑤ Campaigns Phishing Event
The function of Campaigns is to link the above four functions Sending Profiles, Email Templates, Landing Pages, Users & Groups, and create phishing events.
In Campaigns, you can create a new phishing event, select the edited phishing email template, phishing page, and send phishing emails to all users in the target user group through the configured sender email.
Click New Campaign to create a new phishing event.
URL
Here, fill in the URL corresponding to the IP address of the gophish host currently running on my local machine, i.e., http://v-p-s ip/
It must be ensured that the URL is accessible to the network environment of the target user group. For example, if an internal IP address is filled in, the phishing event can only be participated in by internal target users, and the network of external target users is not accessible.
If gophish is deployed on a public server, fill in the public IP address or domain name. It is necessary to ensure that the internal network environment of the target users can access the IP address of the public server.
Send Emails By
Send Emails By is used in conjunction with Launch Date to indicate the time when all phishing emails in the current phishing event are sent. Launch Date serves as the starting time for sending emails, while Send Emails By represents the completion time, and the time between them is evenly divided by all emails in minutes.
For example, the value of Launch Date is 2022.01.01, 00:00, and the value of Send Emails By is 2022.01.21, 00:10. This phishing event requires the sending of 10 phishing emails.
So after the above settings, from 00:00 to 0:10, there are 10 sending points, evenly divided by 50 emails, that is, each sending point will send 1 email, which is to say, only 1 email is sent per minute.
The advantage of this is that when a large number of phishing emails need to be sent and the sending email server does not limit the number of emails sent per minute, this setting can limit the unrestricted sending of phishing emails, thereby preventing spam detection due to a large number of emails arriving at the target email server in a short period of time, and even the IP of the sending email server being blocked by the target email server.
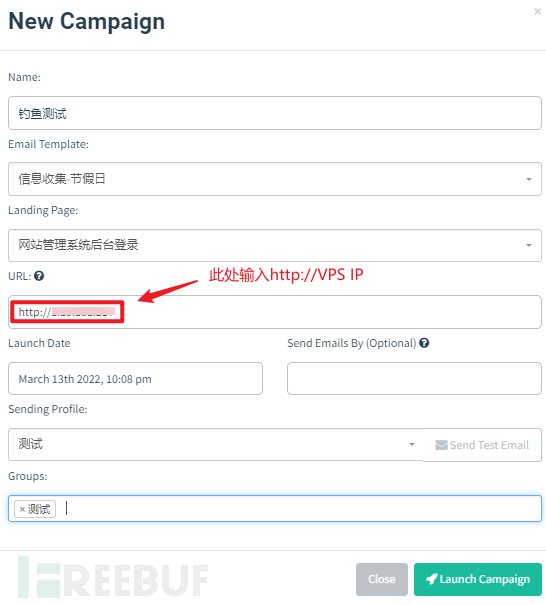
After filling in the above fields, after clicking Launch Campaign, this phishing event will be created (note: if the Launch Date is not modified, the default is to start sending phishing emails immediately after creating the phishing event).
As shown in the figure below, the email successfully received the email.
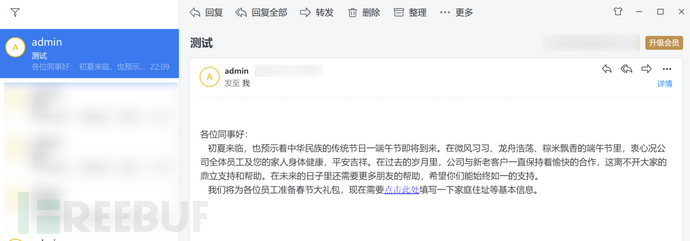
Up to this point, all the steps required for a phishing event initiated by gophish have been completed. Next, just wait for the fish to bite.

⑥ Dashboard Dashboard
After creating the phishing event, the Dashboard will automatically start to collect statistics. The data items include the number and ratio of successful email sending, the number and ratio of emails opened, the number and ratio of clicks on the phishing links, the number and ratio of submitted account and password data, as well as the number and ratio of received email reports. In addition, there is a timeline that records the time points of each behavior.
At this time, simulate the behavior of the user: click on the hyperlinks in the email, jump to the deployed phishing page, and find that there is no difference from the real login interface. Observe the website URL, and you can see that the hyperlinks in the phishing email point to the URL filled in the new Campaigns form, but with an additional rid parameter, which is used to distinguish different recipients.
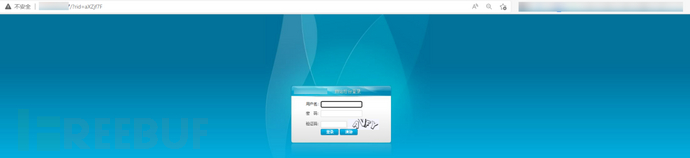
Enter the account, password, and verification code and submit them. After submission, the phishing page deployed will be redirected to the real login interface, thereby confusing the victim users.
Observe the dashboard and check the intercepted data.
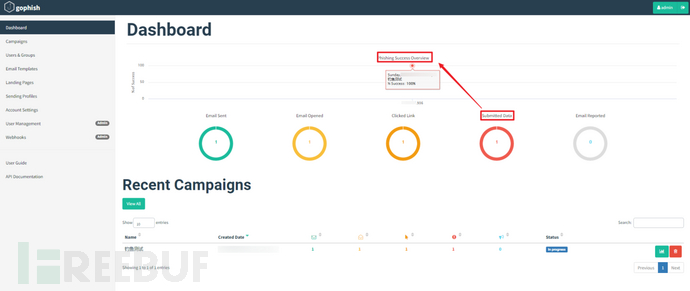
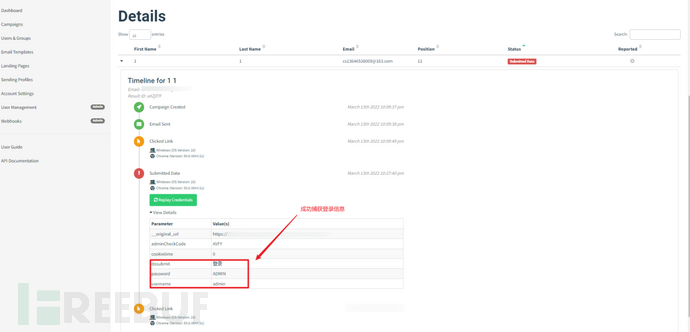
Specifically, click on Campaigns - View Results - Expand Details (the small triangle on the left).
You can see the account and password information submitted on the phishing page.

(4)Precautions
① Domain
The V-P-S -IP mentioned above all need to be replaced with forged domain names, and A records need to be set in the DNS service provider.
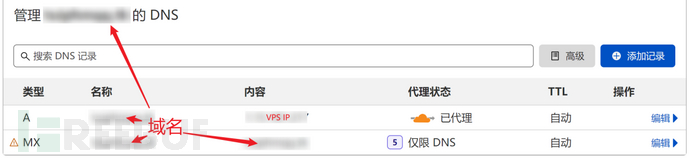
And if you are using a server made by domestic Virtual private server vendors (such as Alibaba Cloud, Tencent Cloud, etc.), it is necessary to go through the ICP registration process in order to be normally resolved and accessed. Otherwise, the following situations may occur:
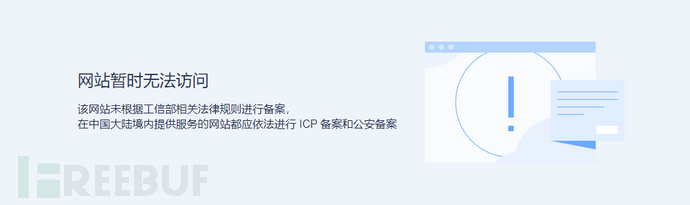
Of course, if you are using a Hong Kong or overseas server, it can be normally resolved and used. Therefore, this point is particularly important in the early preparation of phishing operations, as using such servers can bypass the ICP registration process.
Note: The .tk domain cannot be submitted for domain name registration in China.
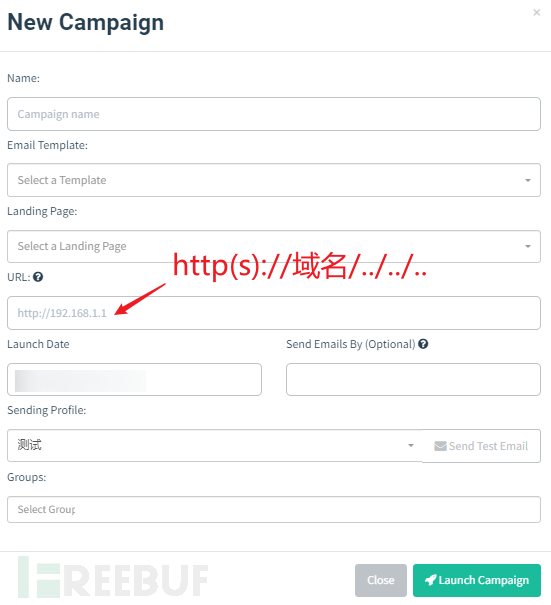
② Directory
Since the real login interface usually exists in the directory, such as the access path /admin/login.
At this time, it is only necessary to set the URL as shown in the figure below in New Campaign (New Phishing Time).
The setting result is shown in the figure below:
IV.Phishing Email Template
The attachment content can be set to a virus, such as word, pdf, exe, etc., as long as it can be uploaded.
No matter what kind of phishing email, it needs a good copy to make the target click or download.
A successful phishing email requires a good copy. A copy that may lead the target to click needs to have the following elements:
Importance
Firstly, it needs to reflect the importance of the email to drive the target to view the email.
Targeted
Secondly, the copy needs to be targeted, and it needs to be combined with the target's identity and the company's situation and business.
For example:
When facing all company members, pretend to be the company's technology department, security department, and administrative department to send phishing emails.
When facing sales, administration, finance, and legal affairs, pretend to be suppliers, customers, and channels to send phishing emails.
When facing HR, send phishing emails pretending to be an interview candidate.
Urgency
Since the email copy is just a process, the real purpose is to drive the target to click on the attachment or enter their information on a forged website, therefore, the copy needs some urgency to guide the target to perform clicking, inputting, and other operations as soon as possible.
1.Account Information
Template One:
By imitating the leader's email, fishing for sensitive information such as operation and maintenance personnel, internal personnel, and personal accounts or passwords related to them:
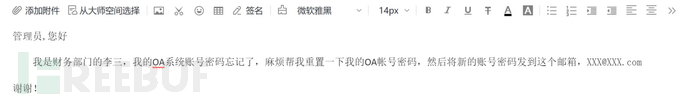 Template Two:
Template Two:
The attacker pretends to be an administrator and asks the target to click on the link in the phishing email to change various passwords:
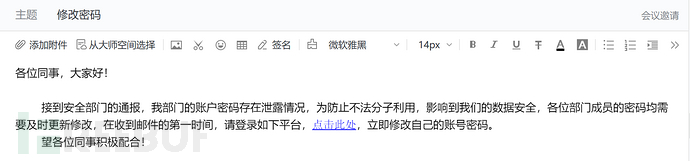 Template Three:
Template Three:
The attacker pretends to be an administrator and asks the target to click on the link in the phishing email to obtain email account information:
2.Job Application Resume
When a recruitment situation is found, try using the method of resume poisoning.
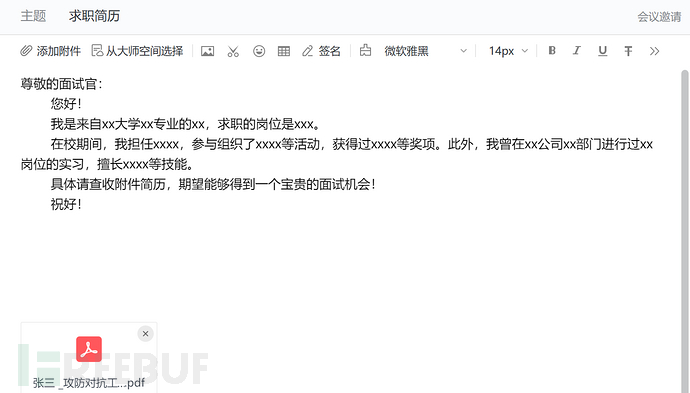
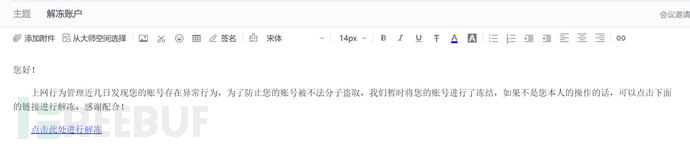
3.Account Unfreeze
The attacker pretends to be a system administrator and asks the victim to click on the link in the phishing email to unfreeze the account.
4.Upgrade Patch
The email content can be forged based on the current hot vulnerabilities, and then make the victim click on the attachment in the phishing email (such as patch upgrades, CVE-xx-xx repair tools, etc.).
5.Hot Events
This type has strong timeliness, can be combined with current events to edit templates, such as using the epidemic situation as follows to make the victim click on the link in the phishing email to provide relevant information.
Template One:

Template Two:

6.Holiday Gift Package
Can pretend to send to company employees

V.Phishing Email Security Strategy
Since according to the rules of SMTP, the sender's email address can be arbitrarily declared by the sender, this is obviously very unsafe. These defects may cause the sender's email information to be intercepted and read by listeners during network transmission, leading to privacy leakage, or may suffer from man-in-the-middle attacks, causing the email message to be tampered with, leading to phishing attacks.
This has led to the generation of the following security protocols:
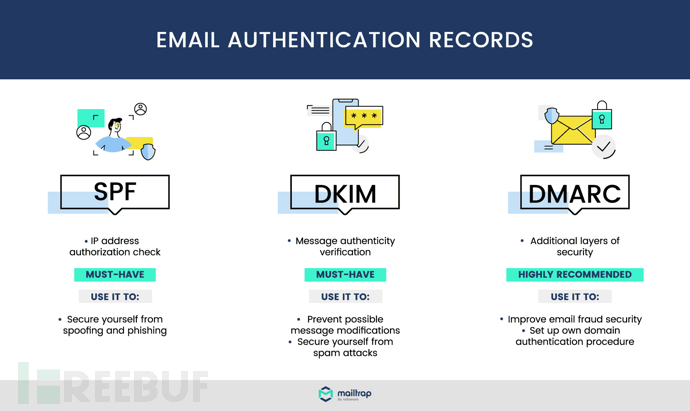
1.SPF
SPF stands for Sender Policy Framework, which is the sender policy framework. The purpose of SPF is to prevent arbitrary forgery of the sender.
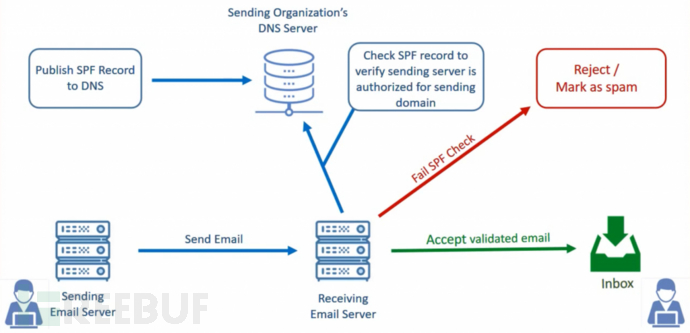
(1)Principle
SPF records are actually a DNS record of the server, and the principle is actually very simple:
Suppose the email server receives an email from a host with the IP address 1.1.1.1, and claims that the sender is xx@example.com. To confirm that the sender is not forged, the email server will query the SPF record of example.com. If the SPF record of the domain allows the host with the IP address 1.1.1.1 to send emails, then the server considers the email to be legitimate; if not, it will usually bounce the email or mark it as spam/junk email.
Although email can be forged to appear as if it came from example.com, it does not have the authority to operate the DNS records of example.com; at the same time, it cannot forge its own IP address. Therefore, SPF is very effective, and currently almost all email service providers (such as 163, QQ Mail, etc.) will verify it.
(2)Inspection method
Online verification website:https://www.kitterman.com/spf/validate.html?

To query SPF records under Linux: dig -t txt freebuf.com
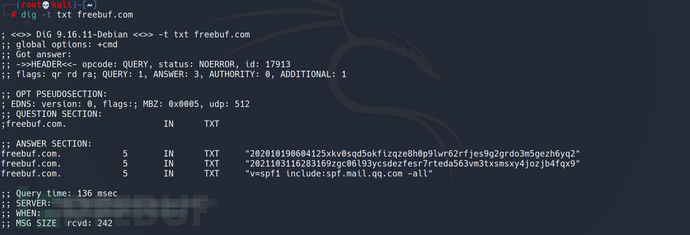
Method to query SPF under Windows: nslookup -type=txt freebuf.com

For SPF related syntax, please refer to:http://www.renfei.org/blog/introduction-to-spf.html
2.DKIM
DKIM stands for DomainKeys Identified Mail, which is an email verification standard and a technology that embeds digital signatures in emails. Like SPF, it is designed to solve the most serious email fraud problem. Unlike SPF, DKIM verifies the content of the email.
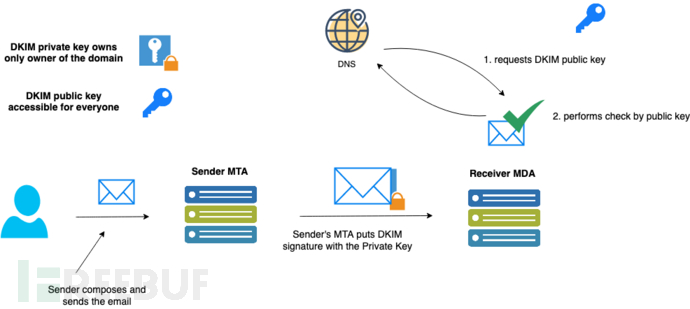
(1)Principle
When the server sends email with DKIM enabled, the DKIM signature performs HASH calculations on some of the content in the email, and finally adds a DKIM-Signature header in the email header to record the HASH value after signing, and encrypts it with the private key, which is attached to the header of the DATA part of the email. The private key is kept by the sender, and the public key is stored on the DNS server for easy automatic retrieval. Upon receiving the email, the recipient will use the private key embedded in the email header and the public key obtained from the DNS to compare them, thereby determining whether the sender's domain is legitimate. If it is not legitimate, it will be judged as spam.
(2)DKIM signature example
The following is a typical DKIM signature header:
DKIM-Signature: v=1; a=rsa-sha256; d=example.net; s=brisbane; c=relaxed/simple; q=dns/txt; l=1234; t=1117574938; x=1118006938; h=from:to:subject:date:keywords:keywords; bh=MTIzNDU2Nzg5MDEyMzQ1Njc4OTAxMjM0NTY3ODkwMTI=; b=dzdVyOfAKCdLXdJOc9G2q8LoXSlEniSbav+yuU4zGeeruD00lszZ VoG4ZHRNiYzR
After receiving an email, service providers that support DKIM will query the TXT record of brisbane._domainkey.example.net, and the decryption key can also be obtained through dig or nslookup.
The following is a TXT record that saves the DKIM public key:
v=DKIM1\;k=rsa\;p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDRDG9+KjIHtJXilSxHtbS92dsEuKZ1mSWBu/e9L3ZpkDpYlOYsqiD8grXafNoIuwrxBpXW2lg2LbwkvugNDjJtQ7SQTPpP6b5hL23i8ezCYKeMTA8XM1618BtO2ZWHmWBOEvlEC11vmCZuuQc0RAxXa1H6hz0C13W+Qg/Qz+xYNQIDAQAB
3.DMARC
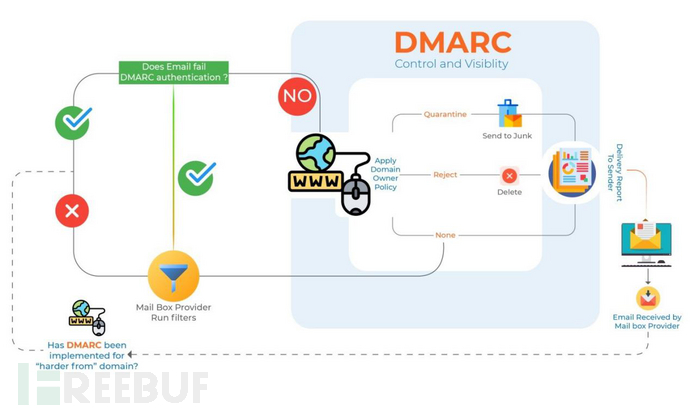
(1)Principle
DMARC is short for Domain-based Message Authentication, Reporting and Conformance, which is an extensible email authentication protocol based on SPF and DKIM protocols. It is usually used in conjunction with SPF or DKIM, and informs the recipient's server how to handle when the email fails SPF or DKIM checks.
(2)Differences from SPF and DKIM protocols
Similarities:Three protocols areAll are declared in TXT records in DNS
Differences:
DMARC allows the sender to define the handling method for unverified emails by themselves, such as 'monitoring', 'isolation', 'reject', which is equivalent to authorizing the recipient. While DKIM & SPF only exist in two processing states, reject or receive.
DKIM & SPF can strictly limit the source legitimacy of a domain name, but cannot limit the subdomain of the domain name, that is, the subdomain will not be protected. While DMARC declaration is placed on the top-level domain, it can protect subdomains.
This citation: https://www.zhihu.com/question/21857308/answer/21115424 For a detailed introduction to DMARC, you can refer to the following two answerers under this Q&A: https://www.zhihu.com/question/21857308 under RIO and Wang Xuejiao
SixthFishing bypass techniques
1.Email forgery tool
(1)Anonymous email
Online forgery: http://tool.chacuo.net/mailanonymous
Online anonymous email: http://tool.chacuo.net/mailsend
(2)Swaks
Also known as the Swiss Army knife in the SMTP world (sensitive word detection), Swaks, an email forgery tool built-in to Kali, can forge every parameter of an email. When the target is not configured with SPF policy, Swaks can fully demonstrate its capabilities.
Project Address:http://jetmore.org/john/code/swaks

Basic usage:
-t –to Target address -t test@test.com You can test the email connectivity with this command -f –from Source address (-f "text<text@text.com>") –protocol Set protocol (untested) --body "http://www.baidu.com" //The content within the quotes is the email body; --header "Subject:hello" //Email header information, subject as email title -ehlo Forge email ehlo header --data https://www.freebuf.com/articles/es/Desktop/email.txt //Save the content of the normal source email into a TXT file and then send it as a normal email; Regular command usage: Swaks --from xx@aa.com --to xx@bb.com --body “xx”. Note: xx@aa.com is a forged user email, and xx@bb.com is the real user email we want to send to
Example:
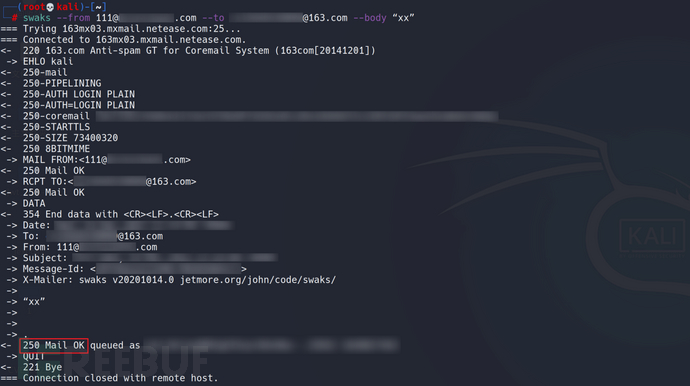
2.Punycode forgery
IDN refers to domain names that contain at least one special language letter, including Chinese, French, Latin, and others. In the DNS system, such domain names are encoded into ASCII strings and translated through Punycode.
In other words, these domain names look similar but have different letters in fact
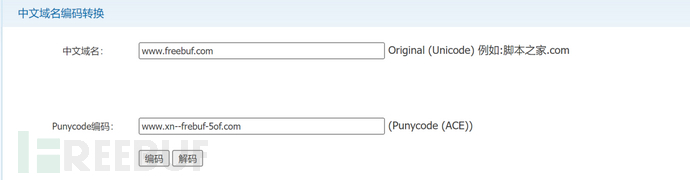
Taking freebuf.com as an example (the Unicode encoding of the first e is 0x435), the part of freebuf is converted to frebuf-5of through Punycode encoding, and then prefixed with xn--, so the DNS record will become xn--frebuf-5of.com.
You can also directly view the real domain name of freebuf through online conversion tools
For example:http://tools.jb51.net/punycode/index.php
Currently, mainstream browsers will automatically convert IDN domain names to Punycode to avoid misjudgment.
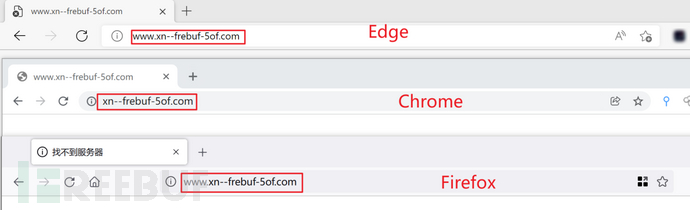
However, as an email server, the detection of IDN is even less, and there is no more effective way to detect, so if we use IDN domain names as our email servers, it can be almost indistinguishable from the real thing.
Therefore, you only need to find these long-similar domain names, and then buy the domain name after punycode transcoding, and once the email is sent, it is hard to distinguish.
You can check the specific characters in the Unicode character table:
https://www.ifreesite.com/unicode/character.htm
You can also directly refer to this table and replace the corresponding letters directly:
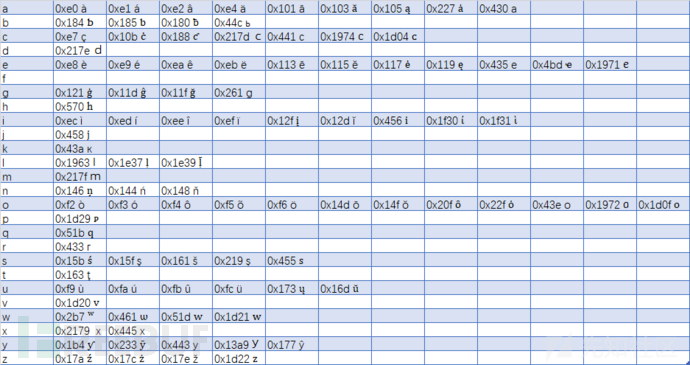
Image source: https://xz.aliyun.com/t/6325 Please delete if infringement.
3.Exploit the unconfigured SPF policy of subdomains
We can focus on the subdomains under some main domains that have already set SPF.
If only the main domain has set SPF, but the subdomain has not been set, we can still send emails as a subdomain identity.
However, if a non-existent subdomain is used to send emails, the emails will be directly sent to the spam box.
Example:
When the target is admin@xxx.com, although xxx.com has set SPF policies, but admin@it.xxx.com is not configured, we can forge any user under the it.xxx.com domain to bypass. Although the deception effect is not as good as direct forgery, it still has a strong deceptive power.
4.URL hiding method
(1)Hyperlink hiding/forgery
The URL hiding method can be referred to as follows,
In word/wps, click 'Insert-Hyperlink' to edit this information. (There are many ways to construct hyperlinks, here is only one demonstration)
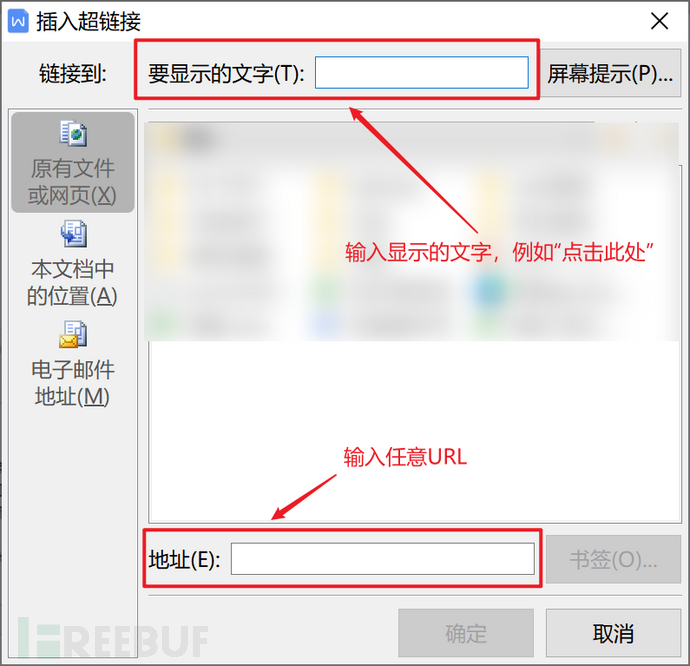
In actual operation, hyperlinks can be constructed through the specific environment in the email.
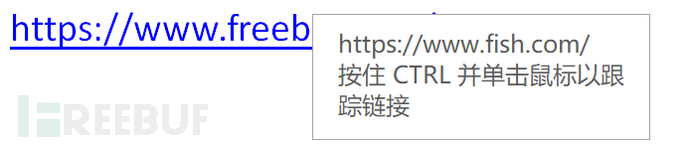
For example, if I want to imitate Freebuf, I just need to input https://www.freebuf.com/ in the displayed text, and I can input the phishing address in the address field as shown in the following figure:
(2)QR code hiding
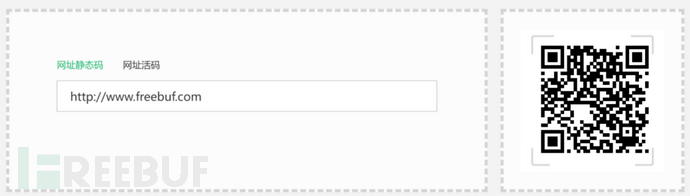
Directly convert through the QR code, which can effectively circumvent the check of the mouse hover on the link in the email, increasing the difficulty of identifying phishing emails.
Method one: Direct site conversion
Conversion site:https://www.wwei.cn/
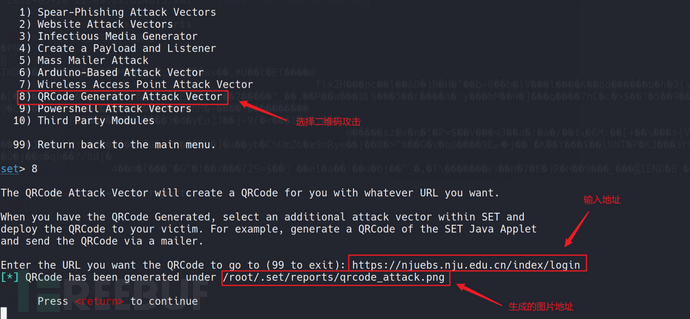
Method two: Setoolkit QR code attack
(3)Alphanumeric substitution
Replace the parts that are extremely similar in domain names with methods such as using the number 0 - letter o/O, the number 1 - letter l/i, and the letter vv - letter w, etc.
Example:
www.leaf.comwww.1eaf.com www.taobao.comwww.taoba0.com www.wave.comwww.vvave.com
(4)IP address
The simplest and most absurd is to use IP directly, for example, http://1.194.1.*/login. A long string of URL indeed looks like a real one to the ordinary people. Due to the fact that many legitimate URLs also contain some opaque and hard-to-understand numbers, it is also certain to fool others. However, those with some basic network knowledge can find some clues, and this will also directly leak their Virtual private server, which is extremely easy to trace by the defense side in the actual environment, except for the anonymous Virtual private server 233
(5)URL redirection
① Reserved characters in URLs
Here, we need to use some separated by "-", if the victim is an employee, we can use something like the company's abbreviation or employee number, etc.
For example, when forging Freebuf using Baidu, there are two methods:
Example 1:
- http://www.baidu.com-admin%11dsaigfd@freebuf.com
This method requires the forging of a sufficiently long string of irrelevant characters to make the address exceed the screen, thus physically obscuring others and preventing them from seeing the truth. The bold part can be arbitrarily replaced (except for '-', other reserved characters cannot be used unless they are URL-encoded), which is also considered a defect of this method.
To make things easier, it can be done by usingMaskPhishto convert phishing links into ordinary network links.
Project Address:https://github.com/jaykali/maskphish
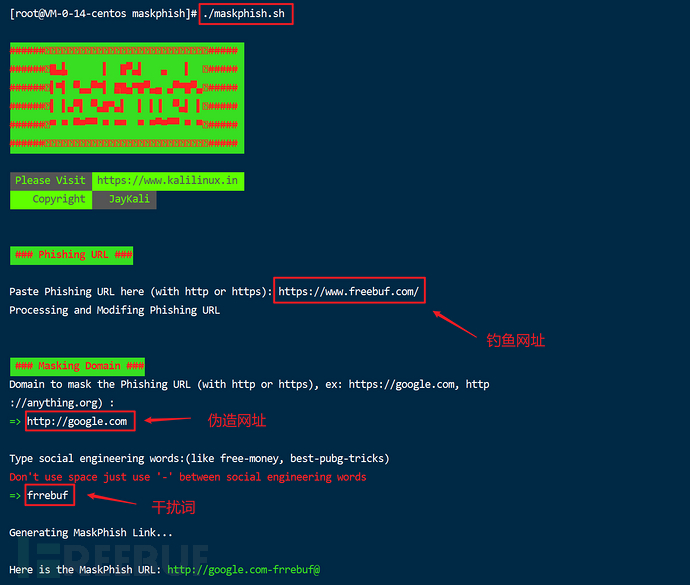
Example 2:
- http://www.baidu.com@freebuf.com/index.php?controller=admin/controller=admin&action=index
Compared to method one, this discovery rate is higher, as the real domain name is directly prefixed, and sharp-eyed people can see the anomaly at a glance, not recommended.
② URL Redirection Attack
When a user browses a URL, the technology that redirects them to another URL. The reason for the URL redirection vulnerability is that this URL is controllable and does not perform sufficient verification, causing the website to accept malicious user input links, redirecting to an attacker-controlled website, which is often a phishing page used to steal users' personal information and login credentials.
For example, URLs with vulnerabilities often have the following format:
http://www.baidu.com/xxx?server=http://www.freebuf.com/abc
http://www.baidu.com/url?q=http://www.freebuf.com/abc
The URL behind is the URL it jumps to. Generally, since there are redirection operations after operations such as regist, login, and logout, URL redirection attacks also often occur at such locations.
7. Reference Articles
1.https://www.cnblogs.com/tomyyyyy/p/15648358.html#tid-X8HZWt 2.https://anchorety.github.io/2020/10/18/email-security-event-fraudulent-users-create/ 4.http://blog.leanote.com/post/snowming/a6b66097bccd
3. E-phishing 2020 email phishing drill
5.https://www.zhihu.com/question/21857308/answer/21115424
6.https://www.secpulse.com/archives/147030.html
评论已关闭