I. Introduction
G.J.Myers proposes in 'The Art of Software Testing': From a psychological perspective, testing is a process of running programs to find errors.
Then, security testing is a process of finding potential security issues in the system. By means of testing, we can discover possible security issues and risks in the system, analyze and optimize them, and ensure the security quality of the system.

Starting from the application security dimension, we will carry out a series of security testing activities, including but not limited to: security pre-scan, security penetration testing, data security, introduction of SDL process, and so on.
In this article, we will focus on the goal of improving system security quality and discuss the following aspects: security pre-scan, security penetration testing, data security, introduction of SDL process, etc.Security pre-scanPractice process.
Hoping to help everyone understand security testing more deeply and thoroughly through this article, so that they can quickly carry out security testing.
Second, security pre-practice
1.Ticket analysis - clarify the source
Before starting the scanning, first analyze the existing ticket vulnerabilities.
(1) Analysis of vulnerability source
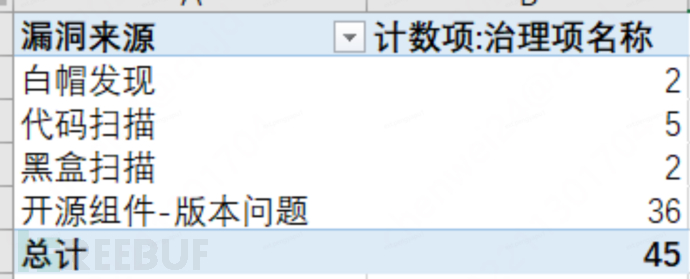
Distribution of vulnerability proportion:
Open source components - version issues, code scanning, accounting for 91%;
These two types are mainlyDuring compilation, the platform automatically calls the security department's code scanning interface to initiate scanning;
The security department followsRulesthenForm vulnerability tickets and issue them to R&D
Distribution of white-box vulnerabilities:

Scanning branches: master branch, uat branch, test branch, etc.
That is: all branches deployed on jdos will be scanned, and all issues scanned out will be the source of ticket generation.
JSRC analysis:
Problems submitted by external white-hat in JSRC:https://security.jd.comand the relevant departments will issue tickets accordingly.
(2) Forming preventive measures
Based on the above analysis, the specific measures to be taken are:
1.Conduct pre-scanningBefore deploying and compiling in the cloud, actively initiate a security pre-scanning to avoid missing online issues. And unify the code security scanning rules to avoid internal scanning of code still existing code scanning type vulnerabilities.
2.Control of security qualityImplementation of R&D testingCode security scanningSecurity scanning is an essential link for going online, triggering automatic scanning, and only after the issues are fixed can online compilation be carried out.
3.Conduct penetration testingConduct penetration testing for the systems that have been put into operation on the external network and internal sensitive network, and manage new requirements through the security SDL (Security Development Life Cycle).
4.Pre-scanning - solving existing problems
By scanning the application code with white-box scanning, black-box scanning of the application domain name, identifying problems in advance, preventing defects, and reducing vulnerabilities. As well as during the scanning process, improving the efficiency of tools, further increasing the scope of pre-identification and prevention.
(1) Code white-box scanning
① Master branch scanning based on the atomic master branch source code security audit
At the beginning of the department's scanning work, use the pipeline method, give priority to the pipeline method, to achieve continuous integration scanning, the main steps of the pipeline are as follows:
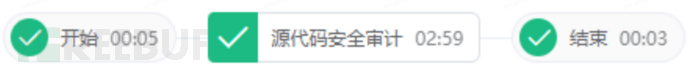
Scanning branches: master branch
Trigger conditions: code submission trigger, scheduled trigger
Email notification: scan report link distribution through email
Problem follow-up: manual report review - vulnerability classification organization - task dispatch to R&D
Summary:
The scanning that can effectively cover the master branch has the following problems:
The coverage branch is limited, causing non-master branch vulnerabilities to be missed;
If a new coverage branch needs to be added, a new pipeline needs to be created, but the time consumption remains unchanged;
Manual way of problem sorting, low efficiency, prone to errors.
② Precautionary scanning of active branches
Compiling branches on the deployment platform, in addition to master, other compiling branches will also generate vulnerability tickets.
Only scanning the master branch cannot completely prevent white-box vulnerability issues.
Therefore: grab active branches - submit active branch code scanning - form full branch scanning coverage.
Identify active branches:
Security Code Scanning Platform:
Active branch scanning results.
Summary:
Based on the above, the scanning coverage of master branch + active branch has been achieved, fully covering, and can completely identify white-box vulnerability issues in advance.
(2) Application Black-box Scanning
Step 1: Obtain domain name based on domain name, parse IP for black-box scanning.
Step 2: Execute white-box vulnerability scanning:
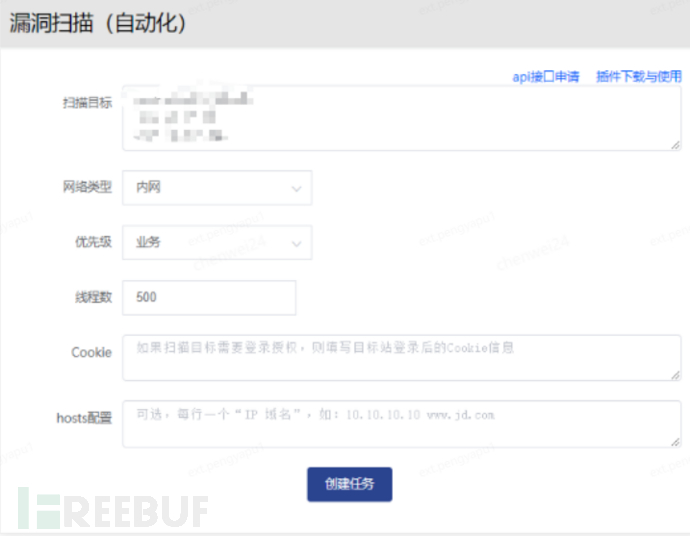
Organize vulnerability scanning results:
(3) Development of Efficiency Tools
Problems: White-box & black-box scanning, including the implementation steps of [submitting tasks - getting results - vulnerability sorting - problem distribution], during which, manual operations are involved: time
Long interval, problem collection and sorting, easy to omit and make mistakes. Low white-box scanning coverage, omitted issues form work orders.
Solution: Based on open interface to implement batch task submission - get results - report sorting tool
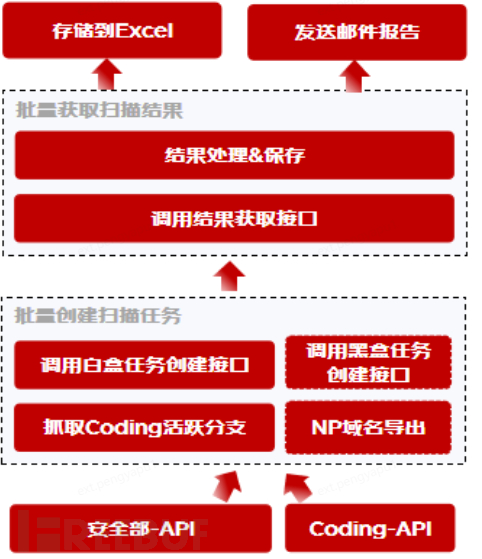
Benefits::
Efficiency improvement: manual 4 hours -> 1 hour, efficiency increased by 75%
Coverage improvement: master branch -> nearly two weeks active branch + master branch, scanning coverage 100%, finding more problems, avoiding omissions.
1.Vulnerability Repair - Closed-loop Tracking
After completing white-box and black-box scanning, the identified vulnerabilities need to be pushed to R&D for resolution, as well as completing the closed-loop tracking and verification of vulnerabilities.
(1) Based on Cloud Defect Tracking and Handling
• Security vulnerability scanning is performed on the dimension of the corresponding code repository of the application;
• A code repository scans once and generates a report showing all security issues currently existing in the project code;
• Each scan result records a problem on the cloud, feedback to the R&D interface person, and distributed to specific R&D by the R&D interface person;
Summary:
• Based on the cloud-based defect entry management, the entry process is time-consuming and labor-intensive, and automatic entry has not been realized;
• Process is not refined;
(2) Dispatching via Task Batch Management Platform
• After scanning is completed -> organize problems ->Batch dispatching tasks through OE interface people (or OE interface);
• R&D repair and resolution;
(3) Construction of Security Process
• Weekly testing interface people, R&D interface people, organize meetings to review this week's security work orders and vulnerability issues;
• Normalized execution of black and white joint scanning on Tuesday and Thursday online days, sending security test report emails;
• Weekly security test weekly report; monthly security test monthly report;
• Establishing security self-testing awareness before the deployment of the cloud-based compiler, using the platform for self-testing;
1. Brief Analysis of Vulnerabilities
(1) Scanning Principle - Taint Analysis
The working principle of using taint analysis to detect program vulnerabilities is shown in the following figure:
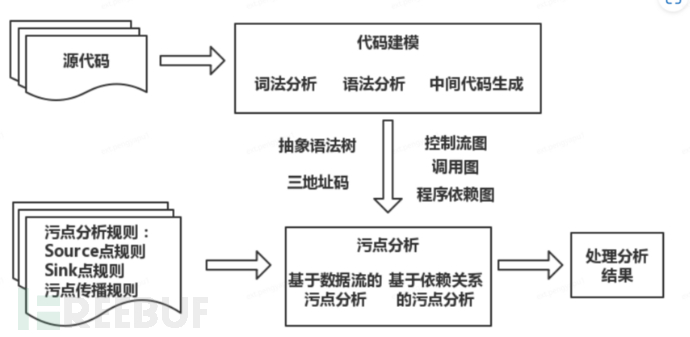
• Data Flow Taint Analysis:
Without considering implicit information flow, taint analysis can be regarded as data flow analysis for taint data. By tracking taint information or variable pollution on the path according to taint propagation rules, it is possible to check whether taint information affects sensitive operations.
• Taint analysis based on dependency relationships:
Considering implicit information flow, during the analysis process, based on the dependency relationship between statements or instructions in the program, check whether the sensitive operation at the Sink point depends on the operation of receiving the taint information at the Source point.
References:https://firmianay.gitbooks.io/ctf-all-in-one/content/doc/5.5_taint_analysis.html#basic_principles
3. Summary
In this article, we discuss the process of improving the security quality of experience assurance. The focus is on the scanning process of black-box and white-box.
Firstly, the vulnerability work order was analyzed, determining the source, type, and distribution of the vulnerabilities, and clarifying the current situation of the vulnerabilities.
Then, by conducting a security pre-scan, the white-box and black-box issues in the work order are identified in advance. During the process, development tools are used to enhance efficiency, and ultimately, a feasible pre-scan implementation plan is formed.
However, it is necessary to pay attention to: in addition to solving existing vulnerability issues, it is also necessary to add similar issues, which require continuous construction, and it is necessary to achieve the normalization of security testing operations. Moreover, more automated tools should be utilized to improve efficiency.
Author: JD Logistics, Chen Wei
How to deploy and implement (cloud) host EDR + situation awareness platform for large enterprises
3.2 Pilot establishment of a network security guarantee system oriented by risk management
Build an information security visualization platform by yourself (Part Two) Missle Map
Get the tricks of multi-tenant asset risk management, and become a qualified '包租公'.
评论已关闭