Preface
One of the basic principles of protecting China's key information infrastructure is 'dynamic protection oriented by risk management', that is, to carry out continuous monitoring and dynamic adjustment of security control measures according to the security threat situation faced by key information infrastructure, forming a dynamic security protection mechanism, and timely and effectively preventing and responding to security risks.
Today, the author will talk about the practice of a certain operator establishing a cyber security protection system oriented by risk management.
1. Project Background
A certain operator belongs to a key information infrastructure operator, providing public services closely related to people's lives to the public in a certain city.
The operator has attached great importance to cyber security work since its establishment. Up to now, a large number of cyber security work has been done, including:
(1) Based on the cyber security level protection system, ISO27001, etc., to carry out the construction of cyber security compliance system;
(2) Actively refer to successful and beneficial general practical experience at home and abroad, such as security theories, methods, and models, to guide cyber security protection work;
(3) Introduced the on-site assistance of a cyber security service organization to assist the security management department in carrying out routine security operation and maintenance work, and established a relatively完善 cyber security security system.
In February 2014, the United States issued the 'Enhancing Critical Infrastructure Cybersecurity Framework', which proposed a risk management approach focusing on security risks, implementing security risk control over critical infrastructure, and keeping security risks within an acceptable range. This is also consistent with China's principle of 'dynamic protection oriented by risk management' for the protection of key information infrastructure.
The operator is also conducting network security risk management activities on a regular basis, but there are several main problems:
(1) The coverage and objects of risk management are incomplete;
(2) The coordination mechanism of all parties involved in risk management is not sound;
(3) Lack of a unified network security risk management plan and an effective implementation/feedback/inspection working mechanism;
(4) There is no network security guarantee system guided by risk management.
Based on this, the operator decides to refer to beneficial and successful general practical experiences at home and abroad, according to the relevant policies, laws and regulations, and standard specifications for the protection of China's key information infrastructure, and establish a network security guarantee system guided by risk management.
II. Thoughts and Methods for Solving Problems
After research and consultation with a network security service organization, the security management department of the operator decided to adopt the 'three-step' model of 'pre-research, post-pilot, and further promotion'.
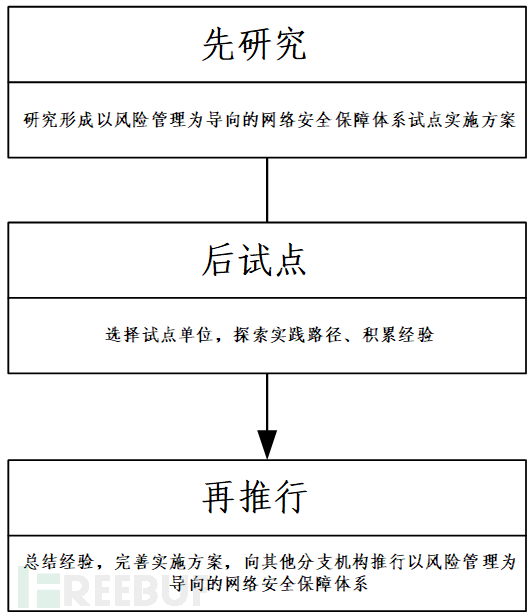
(1) 'Pre-research': Based on the reference of beneficial and successful general practical experiences at home and abroad, according to the relevant policies, laws and regulations, and standard specifications for the protection of China's key information infrastructure, combining with the actual situation of the unit, study feasible, implementable, and low-cost network security guarantee systems guided by risk management, form pilot implementation plans and review and approve them.
(2) 'Post-pilot': After the pilot implementation plan is formed and reviewed and approved, select a center as a pilot, adjust the existing network security guarantee system at a relatively low cost without affecting business stability and continuous operation, explore practical paths, accumulate experience, and gradually promote the establishment of a network security guarantee system guided by risk management and continue to improve.
(3) 'Further promotion': Summarize the successful experience of a pilot center, further modify and improve the pilot implementation plan; do a good job in the preliminary preparation work and implementation plan for the promotion of the implementation plan, and promote the network security guarantee system guided by risk management to other branch institutions.
III. Practice Process of Network Security Guarantee System
3.1 Research and form an implementation plan
The security management department of the operator and the on-site network security service organization jointly dispatch personnel to form a joint working group to carry out the research work of establishing a network security guarantee system guided by risk management. The main work is as follows:
(1) Study beneficial and successful general practical experiences at home and abroad, organize the relevant policies, laws and regulations, and standard specifications for the protection of China's key information infrastructure, sort out the relevant content involving risk management, and form reference basic materials.
(2) Investigate the operation and maintenance of the network security of branch institutions, and the implementation status of other operation and maintenance work such as host operation and maintenance, network operation and maintenance, and infrastructure construction.
On this basis, after the joint working group has conducted research and repeatedly argued, improved, and solicited opinions from relevant personnel of the business and user departments, as well as third-party personnel on-site carrying out various operation and maintenance work, it finally compiled and formed the 'Pilot Implementation Plan for Adjusting the Cyber Security Security System Guided by Risk Management' (hereinafter referred to as the pilot implementation plan).
This 'Pilot Implementation Plan' elaborates in detail on the project background, the operation of the current cyber security security system, the relevant general practices at home and abroad, the requirements of China's relevant policies, laws, regulations, and standards for the protection of key information infrastructure, the implementation principles and basis, the goals of risk management, the scope and object of risk management, the roles and responsibilities of risk management personnel, the content and process of risk management, the adjustment content of the existing cyber security security system, the items to be coordinated, the implementation and promotion plan, project budget, safeguard measures, the main cost analysis of the adjustment of the existing cyber security security system, and the expected benefit analysis, etc.

Among them:
(1) The goal of risk management: By establishing a unified cyber security risk management plan, it promotes the implementation of various risk management activities, integrates risk management into all stages, links, and operation and maintenance activities of key information infrastructure protection, controls the security risks within an acceptable range, and thus establishes a cyber security security system guided by risk management.
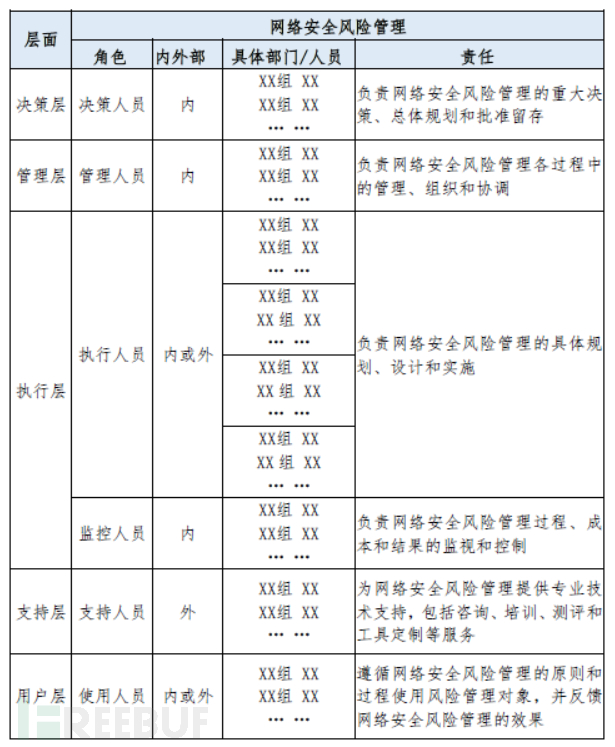
(2) The roles and responsibilities of risk management personnel: It includes the direct participants in risk management, as well as the relevant personnel of the risk management objects. For example: decision-making personnel, management personnel, executive personnel (planning and design, construction, operation, maintenance, monitoring, etc.), support personnel, and user personnel.
(3) The content and process of risk management: It includes six aspects of content, namely background establishment, risk assessment, risk handling, approval retention, monitoring review, and communication consultation. Among them, risk assessment describes the framework, process, implementation process, working form, and key information infrastructure life cycle stage-specific risk assessment content; risk handling describes the principles, methods, process, implementation process, and evaluation of handling.
(4) The adjustment content of the existing cyber security security system: It proposes the risk management content that needs to be added to the existing operation and maintenance activities, the content that needs to be improved in the existing risk assessment activities, the content that needs to be improved in the existing risk management mechanisms including organization, system, process, etc., and the resource preparation content of the team, tools, processes, and systems for executing a unified cyber security risk management plan.
The joint working group invites the heads in charge of cyber security, relevant personnel from the business and user departments, third-party personnel on-site carrying out various operation and maintenance work, and external experts to hold a review meeting to review the 'Pilot Implementation Plan'. After full discussion, a review opinion is formed.
After the joint working group makes modifications based on the review opinions, the 'Pilot Implementation Plan' is officially formed after being successively approved by the head of the safety management department and the main responsible person for cyber security.
3.2 Pilot establishment of a network security guarantee system oriented by risk management
The joint working group, according to the 'Pilot Implementation Plan', prepares to carry out pilot work in a center. The main content is shown in the figure below:
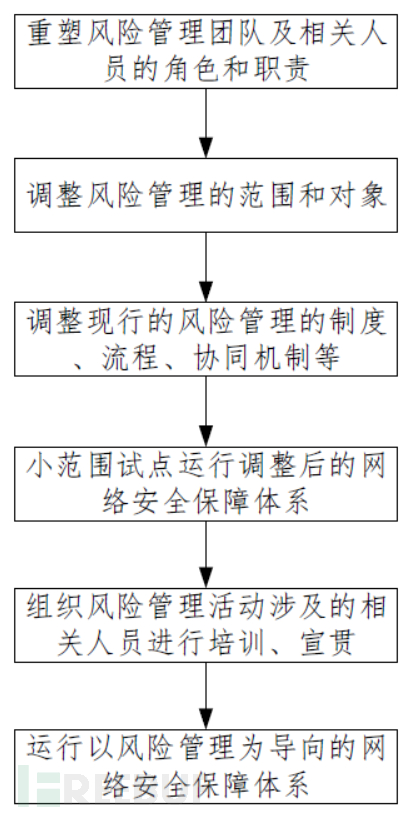
3.2.1 Reshape the roles and responsibilities of the risk management team and relevant personnel
Redefine the roles, responsibilities, and obligations of the existing risk management team and relevant personnel, and form relevant documents. The roles and responsibilities of the adjusted risk management team and relevant personnel are as follows in the table:
3.2.2 Adjust the scope and objects of risk management
Adjust the scope and objects of the existing risk management and carry out the following work:
(1) Investigate business objectives. Understand the mission of a center, including strategic background and strategic objectives, and clearly define the business objectives of the risk management objects that support the operator to achieve its mission.
(2) Investigate business characteristics. Understand the business of a center, including business content and business processes, and clearly define the business characteristics of information systems that support the business operations of the operator.
(3) Investigate management characteristics. Understand the organizational structure and management system of a center, including post settings, responsibility allocation, regulations and rules, operational procedures, and personnel management, and clearly define the management characteristics of information systems that support the business operations of the operator.
(4) Investigate technical characteristics. Understand the assets involved in the risk management objects, including new technologies, business flows (data flows), physical platforms, system platforms, network platforms, and application platforms, and clearly define the technical characteristics of the risk management objects.
Summarize the above survey results to form a description report, which includes content such as business objectives, business characteristics, management characteristics, and technical characteristics.
Based on the above survey results, form a 'List of Objectives and Scope of Risk Management'.
3.2.3 Adjust the existing risk management system, processes, and collaborative mechanisms
Revise the existing risk management system, including:
(1) Add the content of 'The relevant personnel involved in risk management should actively report the relevant content of network security risks' and the procedures and collaborative mechanisms required for the active reporting of network security risks;
(2) Add the content of 'Establishing a unified network security risk management plan' and the corresponding working mechanisms for the implementation, feedback, supervision, and inspection of the risk management plan;
(3) Add the content of 'Organizing and managing all network security activities around the links of identification, protection, detection, early warning, response, and disposal';
(4) Add the content of 'Taking risk management as the统领 of all network security activities'.
Around the links of identification, protection, detection, early warning, response, and disposal, adjust or add several operation and maintenance activities, and increase the description of work content related to risk management, such as:
The operation and maintenance team should actively report the security issues and potential risks found in the detection and evaluation activities to the risk management team and integrate them into the unified management of the network security risk management plan.
——Increase data export management activities, mainly including measures to protect the security of exported data, and conduct a security assessment of data export activities. At the same time, actively report the problems and risk hazards found in the security assessment to the risk management team, and integrate them into the unified management of the cybersecurity risk management plan.
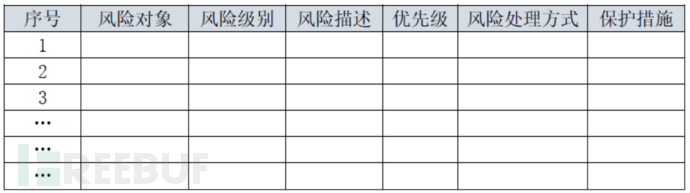
Adjust the content of the current risk management activities, not only including the current proactive risk management activities, but also the management of risks reported by the relevant personnel related to risk management. Establish a unified cybersecurity risk management plan, formulate a template for the risk management plan, and establish a comprehensive risk management plan for the implementation, feedback, monitoring, and inspection working mechanism. Choose different methods to handle risks based on the potential impact on key business, including risk mitigation, risk transfer, risk avoidance, and risk acceptance.
The cybersecurity risk management plan includes content such as risk objects, types/levels, descriptions, priorities, risk handling methods, protective measures, and risk disposal time.
Promote the current risk management activities to the highest level of cybersecurity activities, integrate them into the cybersecurity risk management plan, and use risk management to lead all cybersecurity activities. The ultimate goal is: dynamic risk control of key information infrastructure, and controlling the security risks faced by key information infrastructure within an acceptable range.
Establish continuous improvement strategies, methods, and mechanisms.
3.2.4 Adjust the cybersecurity guarantee system after the pilot operation in a small range
Select 1 person from the operation and maintenance work group responsible for hosts/databases/networks/safety from the business and usage departments, carry out pilot work of the risk-oriented cybersecurity guarantee system, summarize experience, and improve shortcomings and deficiencies in the pilot work.
The method of risk analysis can be referred to in GB/T 20984 'Information Security Technology - Specification for Information Security Risk Assessment', and risk management can be referred to in GB/T 24364 'Information Security Technology - Guide for Information Security Risk Management'.
3.2.5 Organize training and publicity for the relevant personnel involved in risk management activities
After the pilot work in a small range is completed, further improve the pilot implementation plan according to the pilot situation, compile training and publicity materials, organize unified training for the relevant personnel involved in the risk management activities, and provide unified explanations and clarifications on the organizational structure adjustment involved in establishing a risk-oriented cybersecurity guarantee system, the responsibilities and main work content of the relevant personnel, and the implementation, feedback, monitoring, and inspection working mechanism of risk management.
3.2.6 Run the risk-oriented cybersecurity guarantee system
After the preparation of relevant work is ready, formally run the pilot operation of the risk-oriented cybersecurity guarantee system, carry out routine unified cybersecurity risk management activities, and implement, feedback, monitor, and inspect the cybersecurity risk management plan.
3.3 Summarize the experience and promote it to other branches
Based on the pilot work situation of a certain center, summarize the experience, modify and improve the implementation plan, and according to the implementation plan, gradually establish and promote a risk-oriented cybersecurity guarantee system in various branches.
4. Evaluation of Effectiveness and Summary of Experience
Through the process of 'research first, pilot first, and then promotion', the operator has established a cybersecurity guarantee system oriented by risk management on the basis of the current cybersecurity guarantee work.
By practicing the concept of leading various cybersecurity activities with risk management, the risk awareness of operation and management personnel in host, network, business, database, and security has been deeply rooted in people's hearts. The risks that may be faced in various cybersecurity activities including planning and design, development and construction, operation and maintenance, and retirement and abandonment are clearly defined and delineated. These activities are globally unified through cybersecurity risk management plans, and risk management activities such as feedback, monitoring, and inspection are carried out. Through continuous improvement strategies, dynamic security risks are controlled within an acceptable range.
Through the establishment of a cybersecurity guarantee system oriented by risk management, the operator realizes that in order to protect the security of key information infrastructure, in addition to doing well in all aspects of cybersecurity compliance work, it should also be guided by risk management. By establishing a cybersecurity risk management plan and a cybersecurity risk management system applicable to the entire organization, it will lead various cybersecurity activities by risk management, adjust the security control measures according to the security risks faced by key information infrastructure, and prevent and respond to security risks in a timely and effective manner, controlling the security risks within an acceptable range.
Summary
This article describes the practice process, operation effect, and experience summary of a certain operator establishing a cybersecurity guarantee system oriented by risk management.
The protection of China's key information infrastructure is still in the process of gradual exploration and advancement. Operators are also taking various technical protection measures and other necessary measures to protect key information infrastructure, in accordance with the relevant policies, laws and regulations of China's key information infrastructure protection, based on the actual conditions of their units. The practice of 'building a cybersecurity guarantee system oriented by risk management' mentioned in this article may not be applicable to other operators. If there are any immature aspects, please feel free to point them out.
评论已关闭