Are you still confused by the SFTP connection timeout?
1. IntroductionDuring the recent project integration, it was found that when connecting to the upstream SFTP, it always requireswaitingapproximately10s+the time it takes to appear the password input interface, this long waiting timedirectly leads towhen calling the file interfaceconnect to sftptimeoutproblem. Therefore, I decided to investigate the problem myself, searched for relevant information, tried each of the solutions provided online one by one, and then recorded the troubleshooting and analysis process in detail in the article. I also organized some common SFTP timeout causes and solutions as follows.


2. Problem Troubleshooting Process
•Firstly usessh -vcommand (debug mode) for remote logindebug:
ssh -v -oPort=port_number root@ip_address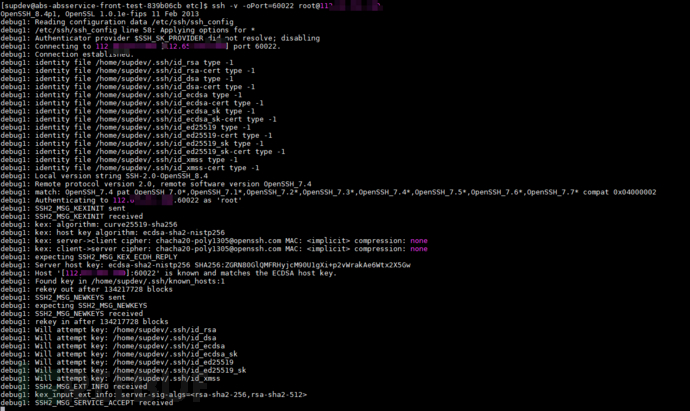
•in debug modeobservedetermine the main debugging informationtime-consuming bottlenecklocation
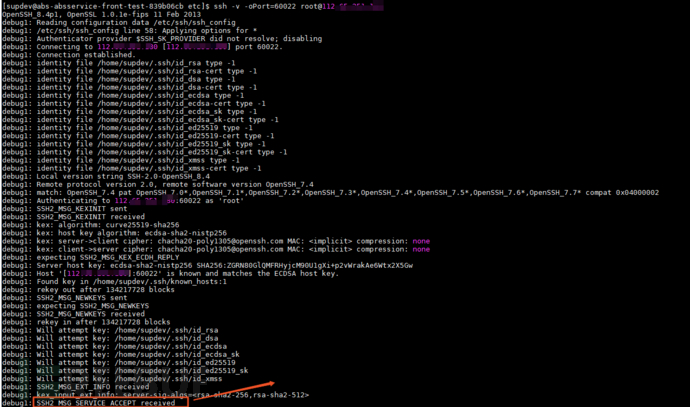
•according totime-consuming bottleneckinformationconfirmationissue categoryServer sideorClient side;
◦If the debugging information is stuck atdebug1: SSH2_MSG_SERVICE_ACCEPT received indicates that the main time-consuming bottleneck is on the server side, and the server's configuration file needs to be modified ();
◦If the debugging information is stuck atdebug1: Next authentication method: gssapi-with-mic indicates that the main time-consuming bottleneck is on the client side, and the server's configuration file needs to be modified ();
◦If both stages stay for a long time, then both the server and client configuration files need to be modified at the same time;
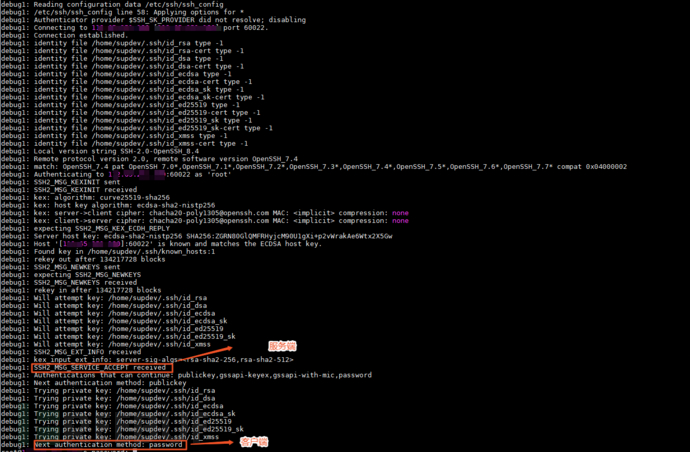
•After investigation, it was found that the debugging information of this SFTP connection timeout is inDebug 1: ssh 2 _ msg _ service _ accept received, the position stay time is relative long, so it is necessary to modify the server's configuration file, and the following files need to be adjusted:
◦Disable DNS reverse resolutionIn Linux, SSH's reverse DNS resolution is enabled by default,The server will first perform a DNS PTR reverse query based on the client's IP address, then perform a DNS forward A record query based on the queried client hostname, and verify whether it is consistent with the original IP address, to prevent client spoofing (in the end, it is still a problem of reverse query).This will consume a lot of time, which is the main bottleneck of slow connection, so you can turn off this option;
configuration file location:
/etc/ssh/sshd_config

The option needs to be modified
UseDNS no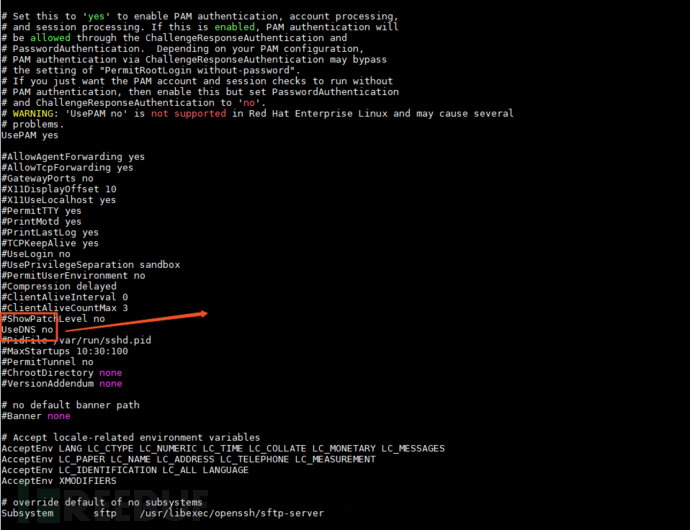
◦Disable GSSAPI authentication:The server has enabled GSSAPI. When logging in, the client needs to perform reverse resolution of the server's IP address, and if the server's IP address does not have a PTR record, it is easy to get stuck here.
configuration file locationthe sameDNS options file,Specific modification content:
GSSAPIAuthentication no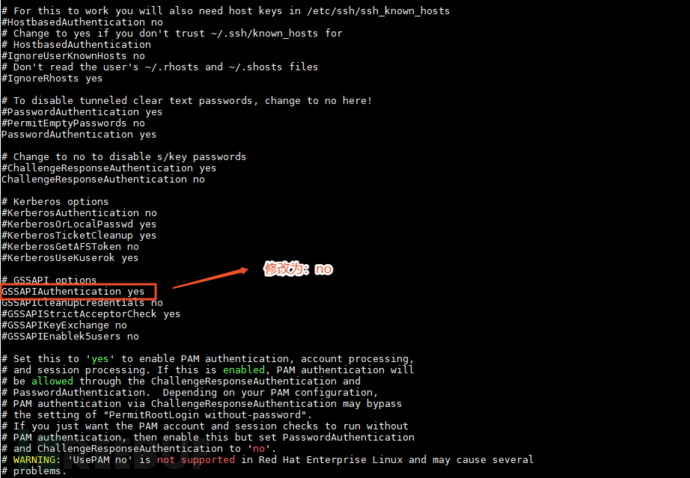
◦[This scheme has not been tried] nsswitch; modify configuration filensswitchinhostsoption;modify “hosts”option,hosts: files dns This indicates that domain name resolution is performed for the accessed hostorder, it will first access file, that is/etc/hostsfile, if there is nononeRecord the domain name, thenAccess DNSPerform domain name resolution. If DNS cannot be accessed, it will wait until the access timeout and then return, so the waiting time is relatively long.Note: If SERVER needs to access other servers through domain names, this line must be retained.
nsswitch file location:
/etc/nsswitch.conf
The specific modification content is: (Note: If SERVER needs to access other servers through domain names, this line must be retained. ps: Emphasized twice)
hosts: files ◦【This solution has not been tried】target host's hosts:modify the target host's/etc/hostsfile, which contains the local host'sIPAndHostnameAdd it in;
◦ModifyIgnoreRhosts option: IgnoreRhostsThe parameter canIgnoreThe records of hosts logged in before, set toyesAfter can greatlyImprovingConnection speed;
File location:
/etc/ssh/sshd_configIgnoreRhostsSpecific modificationsTo:
sshd_configIgnoreRhosts yes•Finally, execute/etc/init.d/sshdRestart the sshd process to make the above configurationTake effectand,ThroughTurn offIn the configuration fileDNS reverse resolutionAndGSS authenticationIndeed, it canEffectively improveSFTPConnectionSpeed; then the question is?
◦WhyWhy do we need to modify these options?
◦What kind of risks will modifying these options bring?RiskWhat?
◦With these questions, weDNS reverse resolutionAndGSSAuthenticationContinue the research=======
3. Knowledge expansion
3.1. What is DNS reverse resolution?

The usual use of DNS is toDomain name resolutionFor IP addresses. This is called forward resolution, and we perform this operation every time we access a website on the Internet. As the name implies, reverse DNS (or rDNS) is a method of resolving IP addresses to domain names.
3.2. What is the process of reverse DNS lookup?
In Windows, usenslookupOrping -aCommand, to manually execute the rDNS lookup command in Linux:
dig -x ip address3.3. What is GSS authentication?
GSSAPI – Generic Security Services Application Program Interface, it is another authentication framework. Based on this framework, there are also various implementations of authentication mechanisms, such as Kerberos, NTLM, SPNEGO, etc. However, the most well-known is still the implementation of Kerberos5, so many people equate "GSSAPI" with "Kerberos authentication". The GSSAPI library is cyrus-sasl-gssapi, which depends on the SASL shared library cyrus-sasl-lib.
Let's take an example ==>
The client connects to the server and says: "Hi, I want to log in, I support SASL, how do I prove my identity?"
The server receives the connection and responds: "Received, I also support SASL, specifically supporting the following SASL authentication implementations: PLAIN, CRAM-MD5, GSSAPI, ..."
The client responds: "I want to use GSSAPI among them."
Server response: 'Received. Do you know that GSSAPI is also an authentication framework? Specifically under the GSSAPI method, I support: Kerberos5, SPNEGO, …'
Client reply: 'Let's use Kerberos5, here is my encrypted ticket…'
◦In the example of what is GSS authentication, a new term (SASL) is introduced, so what is SASL?
SASL – Simple Authentication and Security Layer, translated into Chinese as 'Simple Authentication and Security Layer', is a framework used for authentication and data encryption in network protocols. The official definition of SASL is very abstract and difficult for pe ople to understand directly what it does. In fact, we can understand SASL as a programming framework or a set of interface definitions for identity authentication (Athentication). Different authentication mechanisms can be implemented based on this framework, allowing clients and servers to negotiate and select a common supported authentication mechanism to complete authentication. With the introduction of SASL, application systems no longer need to hard-code for a specific authentication mechanism, and have the pluggable capability of authentication mechanisms; for developers of application systems, using SASL can avoid starting to write implementation solutions from the lowest-level API of a specific authentication mechanism and focus on integrati ng with the SASL framework, because the details of connecting to various authentication mechanisms have been implemented by the corresponding SASL plugins. As the most mainstream implementation of SASL, Cyrus SASL lists a large number of out-of-the-box plugins in its official documentation:https://www.cyrusimap.org/sasl/#features. SASL consists of shared program libraries such as cyrus-sasl-lib and several libraries for specific authentication mechanisms, such as: cyrus-sasl-plain, cyrus-sasl-gssapi, etc.
emm, it has started to become more complex gradually, the summary isGSSAPI authentication is only a kind of security framework and interface standard. More in-depth related knowledge will be summarized in another article later for further study!
4. Summary
Following the solution methods given on the Internet for verification is not difficult, but what is more brain-straining is the reasons for the various modifications involved and how to locate the modification of the configuration based on the existing problems. The text involvesGSSAPIBefore today, authentication was a completely unfamiliar concept. Now, through the search of materials, only a shallow concept of cognition has been obtained, and further in-depth study is needed for the related knowledge and issues introduced in the text! ok, the above is the troubleshooting and analysis of the SFTP connection timeout problem today, which is both a summary and a sharing.
Author: JD Technology, Song Huichao
Source: JD Cloud Developer Community. Please indicate the source of the reprint.
评论已关闭