0x00 Preface
'Unknown attack, how can one know the defense'?
Therefore, generally speaking, for Internet companies (referred to as 'party A'), corresponding major SRC platforms are usually available; within the corresponding party A enterprises, there will be corresponding security plans such as 'Security Operation System Construction' and 'Security Development System Specification (Code Security System Specification)'. The purpose of building these plans is to protect the provided business from significant damage and from the occurrence of irreversible harm.

Then, what specific measures will the party A's proposed solution take?
Regarding secure development (i.e., code security):
The party A usually conducts automated code audit (white-box penetration testing) and automated vulnerability scanning (gray-box testing) when the code is ready for launch.
For security operations:
1. The party usually performs automated vulnerability scanning during off-peak periods of daily business
2. The party usually performs 7*24-hour baseline checks (e.g., whether port openness is compliant - MySQL, SSH, Redis services cannot be opened on default ports, whether passwords are compliant - check password files, important services cannot be configured with weak passwords)
"Know yourself and know your enemy, and you will never be defeated in a hundred battles".
So after knowing the daily work content of the party, how do we mine the SRC?
0x01
Information collection
There are many information collection platforms, and we will not elaborate on them here, only provide the corresponding ideas:
1. Searching for edge assets
Reason:Automated vulnerability scanning can only be run during off-peak periods, the scanning speed is not very fast, so the priority of important assets is relatively high, and the vulnerabilities of edge assets are not easy to be discovered in time by the party.
Method:Non-primary stations and non-core business modules.
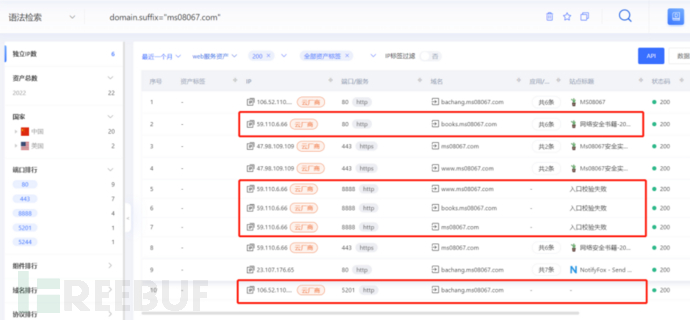
2. Searching for test assets
Reason:Generally, certain functional modules require simultaneous development by multiple departments, and in order to enable better collaboration between departments, the site will be mapped to the public network. Since the functional modules of such sites are not完善, vulnerabilities may exist.
Method:Typically, URLs or domain names contain dev, test, etc.
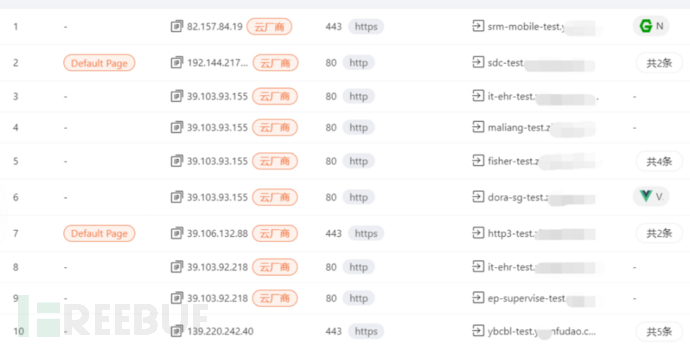
3. Searching for newly launched assets
Reason:Many newly launched sites are in urgent need of going online for various reasons and have not been audited and scanned for vulnerabilities in a standardized manner, so there may be many vulnerabilities that the party has not scanned completely.
Method:Domain assets can be managed in batches through Lighthouse ARL, view new assets; or use Ksubdomain, Fofa, Hunter, and other asset collection tools to obtain assets at different time periods, and obtain asset differences (i.e., new assets) through file comparison.
4. APP application collection
Reason:Many APPs also use HTTP protocol for communication, with the front-end written in Java, JS, etc., and the back-end using corresponding API interfaces to return data to the front-end. According to the APP construction logic, users usually click buttons to jump and do not need to do very detailed authentication for the APP page, and there are usually many unauthorized vulnerabilities.
Method:Search in various application markets, this part is ignored
0x02Vulnerability mining
For edge assets, test assets, and newly launched assets, black-box testing is usually only possible, and the main vulnerabilities mined include:
1. Mining vulnerabilities in the frameworks and components used (e.g., SpringBoot unauthorized access)
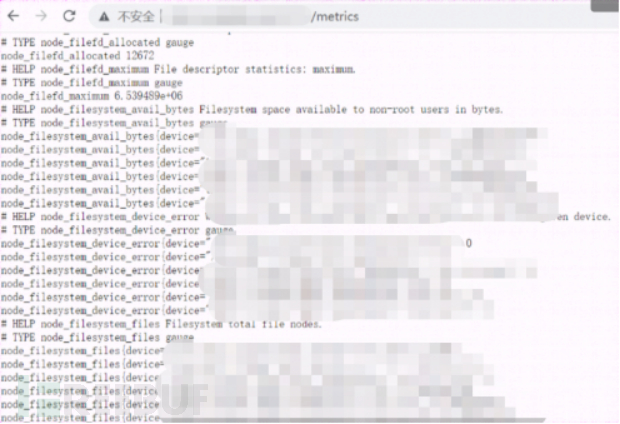
2. Scanning and testing other ports
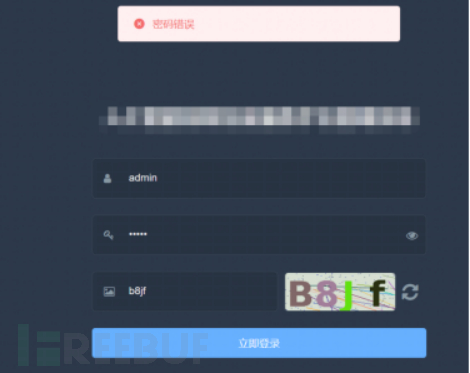
3. Testing and mining vulnerabilities such as common unauthorized access, username enumeration, captcha failure, arbitrary user lock, SMS bombing, etc.
For core assets, the main vulnerabilities mined include:
1. Detecting common types of vulnerabilities: file upload, XSS, SQL injection, XXE, etc.
2. Mining vulnerabilities in the frameworks and components used (e.g., Log4j RCE)
评论已关闭