As an internal and external work data communication and record platform, the email system is widely used by various enterprises. It is also one of the favorite asset systems of attackers, because after the attackers use the non-detection email content to bypass the email gateway security devices, they carry out widespread phishing attacks, and the email system naturally becomes the easiest way to gain a breakthrough. The issues of spam emails, APT attacks, social engineering phishing, and other email threats are becoming increasingly prominent. At the same time, facing the ever-increasing and changing advanced email threats, but lacking effective means of defense, it is the current security situation of corporate email security.

This article will analyze from the perspective of email security attacks, what aspects of the email system in the process of business flow may involve security risks, and what measures should be taken to enhance the protection of email security. In order to help everyone understand the construction of email security protection more simply.
Challenges and risks faced by email security
In most corporate units, sufficient email security gateway products have been deployed, but email-related security incidents still exist. In fact, as the 'foundation' role of the email security system, the email gateway has fully completed its mission, such as filtering and intercepting spam emails and common virus files. However, the 'tip' part of advanced email threats is often overlooked by the business side. For example, common APT attacks and social engineering phishing methods often use the most realistic, normal, and concealed methods for attacks, and email gateways based on rule-based and fuzzy feature detection are the most easily bypassed.

How can we know how to defend if we don't know how to attack? What kinds of threats and risks correspond to the exposure surfaces of different emails?
The purpose of building email security protection is to prevent data leakage, phishing, spread of malicious software, and other security threats related to email. It is also necessary to analyze which asset points may exist and what kinds of threats and attacks may occur from the perspective of the attacker.

Based on the comprehensive analysis of the attack surface, the following risks and challenges are faced by email security:
Is the email account secure?
Is the password of the email account weak or has it been leaked, and has the login entrance on the external network been double-factor authenticated?
Is the email source safe?
Is the email sender forged by SPF to be the company's user, and is the sender's IP and email address on the blacklist; are there any abnormal sending behaviors, suspected of being controlled and exploited by the account?
Is the email content safe?
Is there any malicious link, QR code, executable script, and other threat payloads in the email body and attachment content? For the content of APT attacks, is there a sandbox environment for simulation and identification? Is there a linkage with TIP threat intelligence for risk assessment?
Email CommunicationIs it safe?
Is the email encrypted during transmission to prevent attackers from intercepting and modifying the content of the email using man-in-the-middle attack techniques, or stealing sensitive data; this attack scenario is not common in actual business, more meaning that there is a hijack attack on the client, server, and intermediate proxy transmission nodes.
Email ServiceIs it safe?
Does the Web interface of the email service have vulnerabilities, and is the machine controlled by the attacker through the Nday vulnerability with one click; related data of the email system is generally encrypted stored, even if the control of the email system is obtained, it is also difficult to obtain effective plaintext data. It is only to disrupt the availability of the email system.

After sorting out the risk points to be concerned about, we can combine the frequency and probability of risk generation of actual business, reflect on the top 3 core issues with high priority: email account security, email source security, and email content security; identify and block email attacks in the critical path of email, to maximize the realization of email security.
Based on the analyzed email risk points, how to carry out email security construction?
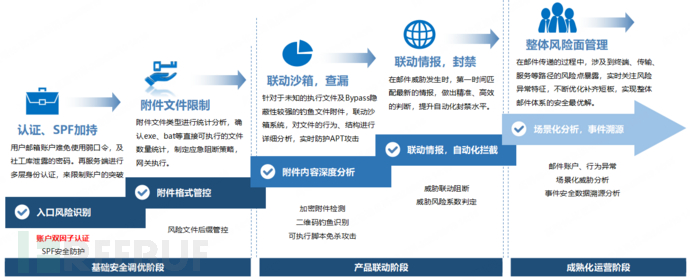
1. Email Gateway(Email Filtering and Interception)
: By setting up email gateway to filter external and internal email traffic. Gateways can intercept spam, phishing emails, malware, and other threats, preventing malicious emails from entering the corporate network. Among them, spam filtering should be based on content analysis, blacklists, graylists, and other technologies.
2. Access Controland Identity Authentication (Control of Email Source)
Enable DMARC, DKIM, and SPF: By deploying technologies such as Domain-based Message Authentication, Reporting, and Conformance (DMARC), Domain-based Key Identification of Email (DKIM), and Sender Policy Framework (SPF), the source of the sent email is verified, preventing email forgery and phishing attacks.
Enforce the Use of Strong Passwords: Employees are required to use strong passwords and change them regularly. Multi-factor authentication (MFA) can be used to enhance the security of email access.
3. Risk Monitoring and Real-time Analysis (Security Depth Monitoring Analysis)
Real-time Monitoring: Deploy email security analysis platforms, link TIP threat intelligence, file sandboxes, and traffic user behavior for scenario-based threat analysis, effectively identify email risks; for highly trustworthy threats identified, they can be directly synchronized to email gateways, EDR terminals, and internet behavior management platforms for联动封禁 of user access and email output, improving automation levels.
4. Email Communication Encryption(Security enhancement)
Ensure that email content is protected during transmission by using email encryption protocols or tools.
5. Terminal security protection(Security enhancement)
Terminal disk detection: Install antivirus and anti-malware software on each terminal device, perform online identification and detection of urls and QR codes, and perform static threat detection on attachments when they are saved, intercept and block related threat instructions when they are triggered at startup.
6. UserSecurity awarenessTraining(Security enhancement)
Regular security trainingConduct training on email security to educate employees on how to identify phishing emails, social engineering attacks, and best practices for handling suspicious emails.
Simulated phishing attackRegularly conduct phishing simulation tests to assess employees' response capabilities and improve their security awareness.
How to combine and operate the email security protection system based on the capabilities of various security products?
In the process of building a secure and stable email security protection system, the single-fighter approach of products often has many drawbacks, such as, email gateways can be connected to the email system for real-time monitoring and filtering due to lightweight detection, but for the heavy resource consumption detection of attachment files, it obviously does not have the advantage of connection. (There may be email gateways with sandboxes on the market, but to decrypt, decompress, and perform dynamic behavior detection on attachments will have a certain impact on the timeliness of email business.) It is necessary to link different security capabilities, combine them with the attack scenarios that attackers may trigger, and carry out associated threat positioning. More accurate and automated identification of email risks;

As the foundation of the solution, email security platforms cannot do without professional security operation support; the cultivation and improvement of email security operation capabilities are an effective guarantee for the construction of email security protection.

How should it be implemented on the ground if there are different physical parks?
Answer:Actual deployment can be based on the use of email archiving systems, connecting to implement the establishment of an email security analysis platform, without causing load pressure on the email security gateway; bypassed security analysis can effectively link threat intelligence and file sandboxes; connect various threat scenarios, and make the most correct judgment on the security coefficient of emails.
(Email archivingEmail archiving system, ensuring long-term preservation of emails, meeting the requirements of audit and compliance.)
The essence of building email security lies in the thinking and competition between 'mace' and '盾'. In practical security operations, attackers seek new protection breakthroughs based on email security, while defenders think about how to fill the gaps in the system based on the attackers' methods. In the continuous confrontation and competition between the two sides, the weaknesses of email security and the effectiveness of email security protection are discovered, achieving pre-emptive prevention of email threats, moving the protection forward, and preventing problems before they occur. This promotes the level of email security protection construction to stay at the forefront.
评论已关闭