1 Project background
1.1 The country is paying more and more attention to network security
‘We must conduct in-depth research, take effective measures, and do a good job in the security protection of national key information infrastructure.’ The Chairman's speech at the Symposium on Cybersecurity and Informatization Work.
1.2 The safety and compliance supervision requirements are becoming higher and higher
The Cybersecurity Law, Personal Information Protection Law, and relevant compliance requirements such as the Information System Grade Protection 2.0 and Commercial Cryptographic Application Security Assessment.
1.3 Enterprise digital transformation is urgent
Digital transformation is usually accompanied by the application of new technologies such as cloud computing, big data, and the Internet of Things. Network security ensures that these new technologies are not threatened during the application process, thus ensuring the smooth implementation of innovation.
2 Design principles
2.1 Advancement
Adhere to the use of advanced technology, emphasizing the leading role of intelligence, new technology, and new products in the new security system. Introduce AI, big data, privacy computing, 6G, and other security technologies in security planning to achieve the forward-looking nature of security capabilities.
2.2 Compliance
Based on relevant policies and standards such as the Cybersecurity Law of the People's Republic of China, Basic Requirements for Cybersecurity Protection of Information Security Technology, and National Electronic Governance Standardization Guidelines, etc., to build a cybersecurity protection system.
2.3 Feasibility
Based on the enterprise's own security status, promote the construction of network security protection step by step and stage by stage, combining the situation of funds and personnel to carry out security construction in the most optimal way.
2.4 Coordination
Security construction should always consider the connection with the business system department, as security and business are integrated. Neither can exist independently for a long time. Fully consider the characteristics of the business system for security design, construction, and operation.
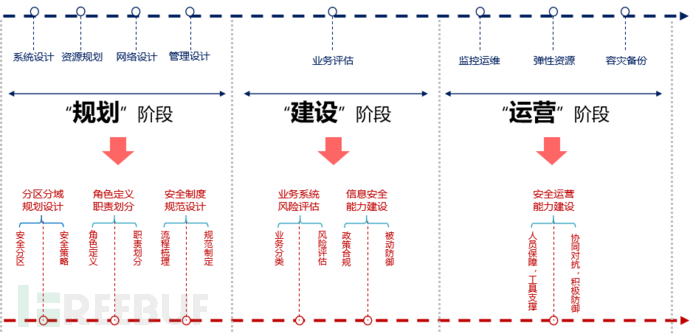
3 Planning ideas
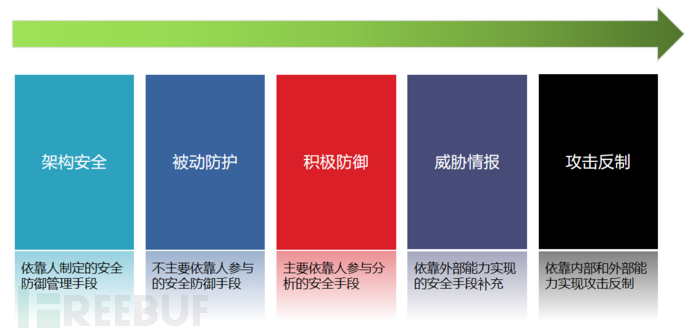
Refer to the SANS security sliding scale model to build an enterprise security protection system, dividing it into five stages: architecture security, passive protection, active defense, threat intelligence, and attack countermeasures. Each stage corresponds to the best action measures and resource investment, building new network security capabilities. With security architecture as the construction indicator, passive defense as the main means, active defense as the enhancement, threat intelligence as the supplement, and attack countermeasures as the last resort.
The most important thing is to first establish “Three Synchronizations(Synchronized planning, synchronized construction, and synchronized operation) should be adopted for security system planning.
Firstly, synchronized planning:From the very beginning of the information system design, safety synchronous planning and design should be carried out according to the requirements of business system confidentiality, integrity, and availability to ensure the security of the system;
Secondly, synchronized construction:Before the information system goes online, the security check of the information system includes: baseline scanning, vulnerability scanning, and penetration testing, etc., to prevent system risks.
Thirdly, synchronized operation:Before the information system goes offline, security operation should become one of the daily tasks, ensuring a continuous, reliable, and effective security protection mechanism that can monitor security events in real-time, promptly discover internal and external factors leading to security incidents, and quickly dispose of them to minimize losses.
评论已关闭