PS: The case is derived from life, and if there is a coincidence, it is purely coincidental.
The opening topic is to talk about the practice story of safety system construction consulting, as the saying goes, practice is not perfect, and exploration is necessary.
1 Exploration of Financial Consulting CASE – Initial Exploration
CASE entry: A financial customer is currently facing the migration of a new data center. The project exchange has been carried out twice (the main practice process is led by the 2nd Communicate), and the general effect is as follows:
1st Communicate: The problems caused by the incomplete digital transformation, the 14th Five-Year Plan, and the construction of the safety system (economic losses, attacks), the process and methods of system construction, data security construction, business implementation cycle and planning.
2nd Communicate: How to plan the safety consulting construction project, what is the significance, what are the differences and values compared to the safety consulting project of professional consulting companies, how to carry out as a safety system construction project, each module provided in the middle, how the safety construction thinking is effectively implemented in the financial industry, planning a large framework guidance, reference, and benchmarking what.
2 Exploration of Financial Consulting CASE – Exchange -> Thinking
After the 1st exchange, the customer did not provide any effective value information. First, there are many methodologies, and after listening to rich experience, it feels very impressive, but the understanding is very little. Second, the core purpose has not been grasped. Of course, the customer recognizes that the expertise and professionalism of the experts and the company in the 1st exchange are very strong, which is why the 2nd exchange was held.
Before the 2nd exchange, a lot of things from the 1st exchange were removed, and the customer also said that it was very clear and put forward suggestions and consulting plans.
In the 2nd exchange, I have deeply discussed the main methodology and put it into a framework of safety system construction. I have also spent some time and effort to make a specific framework diagram of safety system construction (and called it V1.0):
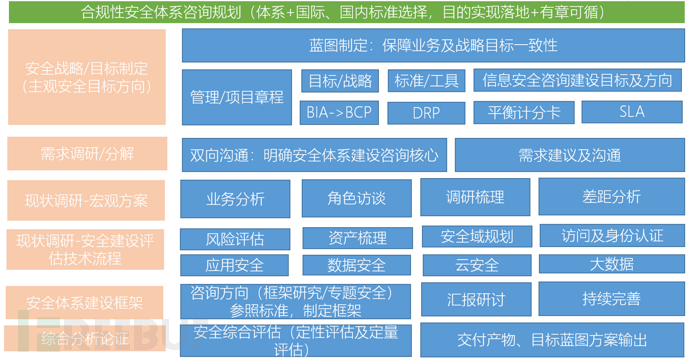
V1.0-Safety System Planning – Safety Construction System Consulting Implementation Module
V1.0 can be seen as a guide for customers to understand the construction of the safety system and the framework of thinking. If we single out the methodology and do not have a framework and process to guide, it is impossible to focus on the core of this consulting business, not to mention the customers, but anyone. The diagram of V1.0 was not combined with the actual security construction of the financial industry at the time of drawing. However, COVER has covered the top-level design, business strategic planning, management regulations, and project regulations of the customer. This part of the strategy and regulations is actually closely related to the construction of the safety system (for example: it is similar to the relationship between digital transformation, the 14th Five-Year Plan, and the consulting project of safety system construction, which is a reference and independent relationship. If the second item is to be carried out, it needs to refer to the framework set by the first item of consultation, but the things done are completely unrelated.
After in-depth thinking, I still put this part (security strategy/objective formulation) at the top level as an implementation module. It is actually an audit-level thing, but when doing security system consultation and construction, ensuring consistency with business strategy is always the first priority. Only by guiding the customer to build security strategy objectives around business strategy can the consultation project be implemented and supported by reasonable resources.
After discussing this with the customer, we also talked about why to do security consultation, which is to think about building a process, and directly guide the direction and thinking of how to set and effectively implement security consultation in the most popular and concise way.

Figure: How to set and effectively implement the direction and thinking of security consultation
The subsequent part is to make a落地 output and presentation of a series of things such as project research, special construction, process, gap analysis, and other things required for the specific security system construction consultation. In fact, there are many methods that can be done for this part, and there is no absolute correct method. The ultimate goal is still to see the customer's needs. Consultation is indeed a two-way communication. At this stage, the currently fictional project has not yet received actual feedback from the customer, just focusing on the construction of the security system (so, don't argue about the lack of points, things are not comprehensive, etc. on the following, on the one hand, it is a method, and on the other hand, it is only at the current stage, friendly understanding).
After the 2nd exchange ended, the customer feedback focused on the construction of the security system, framework, and did not consider the cloud first. The special security focus is on the construction of data security (in fact, at this stage, the dimension of security consultation needs guidance has already had a certain effect).
After V1.0, two more security system construction architecture diagrams were drawn, one after another. This time, after looking at a lot of things and doing in-depth thinking, it is no longer like the first diagram. It can be seen that there is a benchmark and reference (a lucky guess, see who the benchmark corresponds to).
V2.0-Security System Planning – Security Construction System Consultation Implementation Module (Improved)
By V3.0, it is actually not very different from V2.0. The final framework and conceptual content were determined, the points were guided, and thus V3.0 was established.
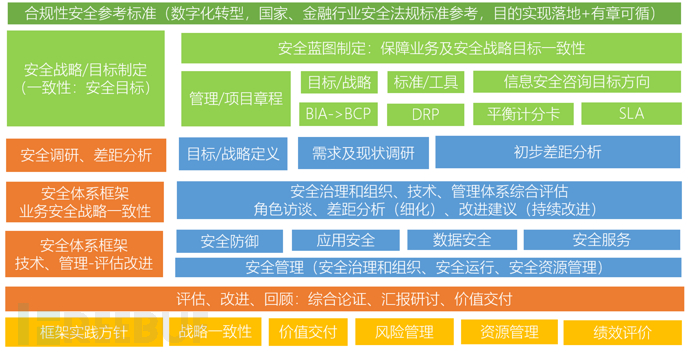
V3.0-Security System Planning – Security Construction System Consultation Implementation Module (Suggested Draft)
The security system construction consultation suggestion document can also be drafted next, generally as follows:
3 Requirements and Necessity for the Planning and Design of the Financial Security System
3.1 Guidance and Regulatory Strategies for Commercial Banks
The standard of 'JRT 0072-2020 Guidelines for Security Assessment of Cybersecurity Protection Levels in the Financial Industry' stipulates the general and extended security assessment requirements for the second, third, and fourth level protection objects in the financial industry. It is applicable for guiding financial institutions, assessment organizations, and the competent departments of cybersecurity protection levels in the financial industry to conduct security assessments of the protection objects. It provides guidance for the security assessment work of cybersecurity protection levels in the financial industry, and can refer to this standard for the assessment, self-inspection, and evaluation of the security status of cybersecurity protection objects in the financial industry, thus further improving the cybersecurity protection system of the financial industry.
The countermeasures will implement the safety system framework and safety planning content of the implementation plan of the JRT 0072-2020 Guidelines for Network Security Level Protection Assessment in the Financial Industry, including the planning and design of safety technology and safety management.
The purpose of the JRT 0071-2020 Technical Specification for Personal Financial Information Protection is to strengthen the security management of personal financial information, guide relevant institutions to standardize the handling of personal financial information, to the greatest extent protect the legitimate rights and interests of the subjects of personal financial information, and maintain the stability of the financial market. On the one hand, the countermeasures are combined with the security protection requirements for personal financial information at each stage of the lifecycle, including collection, transmission, storage, use, deletion, and destruction, as stipulated in the technical specification for personal financial information protection, and put forward normative requirements for the protection of personal financial information from both the aspects of safety technology and safety management.
The countermeasures are in accordance with the requirements of the JRT 0071-2020 Technical Specification for Personal Financial Information Protection, implement data lifecycle management based on the 'Safety Planning Content - Data Security Special Design' in this plan, thus meeting the technical specification for the protection of personal financial information. At the same time, in terms of personal information protection as required by the technical specification for personal financial information protection, comprehensive protection plans should be provided in combination with the types of personal financial information (account information, authentication information, financial transaction information, personal identity information, property information, borrowing information, and other information), including:
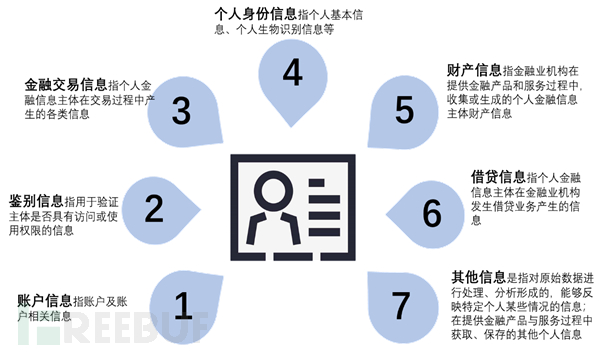
Figure: JRT 0071-2020 Technical Specification for Personal Financial Information Protection - Information Attribute Definition
3.2 Business and Safety Strategic Consistency
To ensure the smooth implementation of the safety system construction consulting project, it is necessary to clarify the safety strategic objectives and achieve consistency between business and safety strategies before the project begins, specifically including:
1)Safety Strategic Formulation:The establishment of safety strategic objectives should be based on the business development stage and business strategic goals, and the formulation of safety strategic objectives should be effectively carried out around the requirements of the business strategic goals, better assisting the implementation and development of business strategies (for example, the comprehensive formulation of safety strategies for aspects such as business continuity, business disaster recovery, and business data security).
2)Implementation Guarantee:The safety strategic objectives planned and set around the business strategic goals are in line with the business development planning and design, thus possessing significant advantages in terms of the availability and project promotion within and outside the organization for the safety system construction consulting project, providing the necessary guarantee for the implementation of the safety system construction.
3)Resource acquisition support:An effective safety system construction requires the effective cooperation of senior leaders and stakeholders in the organizational structure during the project charter construction, project launch, and project implementation process. It assists the safety system construction consultation party in providing necessary support for obtaining safety system construction resources, which will provide necessary support and guarantee for the smooth implementation of the safety system construction framework work.
3.3 Financial security resource investment planning
Data center planning [omitted, mainly for the description of the current safety construction status]
The investment in safety resources includes the investment in safety products, periodic information security services, risk assessment and security situation awareness monitoring, and the application of security assets. However, there is a challenge in ensuring effective security protection construction during the gradual migration process of the existing network after the relocation of the new data center in the next 3-5 years. At present, network equipment and security equipment cannot be used rationally. There are no effective reference standards and planning baseline and indicators for the procurement and acquisition of necessary safety products and services. There may still be shortcomings in the information security management work that may not meet the requirements of the 'Cybersecurity Law' and related regulatory authorities, as well as new risks proposed by new laws and regulations. The existing information security management system needs to be improved, lacking in the planning and implementation steps of information security construction, and the information security work of enterprises lacks clear goals, directions, and detailed work guidance.
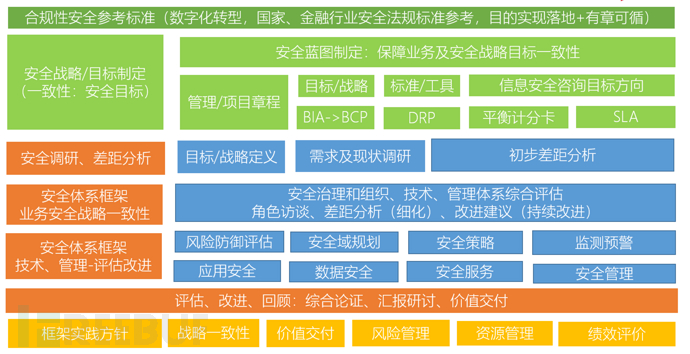
4 Safety system planning and design framework - framework definition
4.1 Safety system framework - design model
Based on the overview of the current safety construction status, new data center security requirements, and the development goals of the blueprint for the next 3-5 years, the customized safety system construction framework design 'Safety System Construction - Overall Consultation Framework V1.0' (Figure 2 - draft) is realized. As an important reference for the effective implementation of the first version of the safety system construction consultation project, it facilitates the understanding of the safety system construction consultation process, content, and resource task allocation. The process, tasks, and evaluation dimensions in the framework diagram are presented in different colored modules, and a detailed division is made for safety compliance reference, safety system construction consultation framework design, and service process, as well as the practice guidelines of the safety system framework. Specifically as follows:
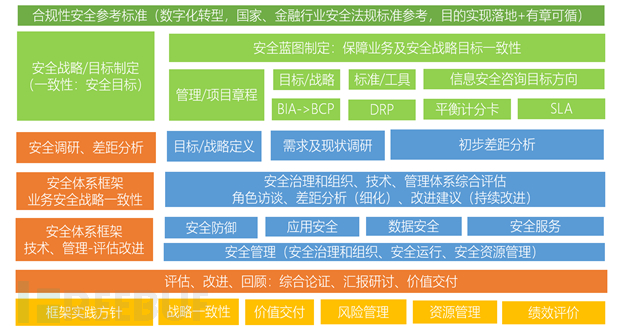
Figure: Safety system construction - overall consultation framework diagram (draft)
Dark green (TOP level): Compliance safety reference standard, in line with the digital transformation strategic policy, national and financial industry safety laws and regulations, and standards as the basis for compliance, the purpose is to ensure the feasibility of the safety system construction framework design while realizing the feasibility and compliance with regulations.
Light green: As the client side needs to provide understanding and input modules for the safety system construction consultation framework designed by the design party, it is generally based on the existing input materials of the client side related modules. On the one hand, it facilitates the consultation party to provide consultation direction selection suggestions; on the other hand, it serves as a macro-level reference guide and basis for the top-level planning of the safety system construction consultation project, realizing the consistency of the two-way understanding between the project client side and the safety system construction consultation planning party, as well as the feasibility and value delivery of the output module of the safety system construction framework design.
Orange: Orange is the output process part of the security system construction consulting framework design party. This part defines the service process stages provided by the security system construction consulting party.
Blue: Blue is the input part of the security system construction consulting framework design party. This part of input is presented as the specific value delivery part of the security system construction consulting project, ensuring the implementability, operation, and value delivery of the security system construction consulting project.
Yellow: Yellow is the best practice guideline reference followed by the design party of the security system construction consulting framework in the practice stage of framework design. It is an effective guide to project implementation and value delivery, indicating that the framework design of the security system construction consulting is based on the five guidelines of strategic consistency, value delivery, risk management, resource management, and performance evaluation to ensure the feasibility of framework design implementation.
5. Detailed design of security system planning and design:
Based on the above security system planning framework, we can determine the content and level of each part to be done in the whole. Therefore, in the design, in addition to refining the above framework, we should also combine the core of the system framework to make specific descriptions and outputs (the content is quite extensive, and I am also lazy to let you understand the above framework. In fact, the refinement of this part is just a matter of granularity, and a separate article will be published later: How should the system planning and design details be implemented and planned? )
6. Initial exploration of financial consulting CASE - Summary of 'Practice is the sole criterion for truth':
The project of consulting on the construction of security system in the financial industry actually made the following thoughts and attempts, and some explanations are also made here:
1. Why should we pay attention to the client's business strategy:In terms of the top-level things, in addition to compliance references, it is necessary to stand in the perspective of the principal/client and assist the principal in understanding the construction of the security consulting system. To do well, it must be consistent with the business and security strategy, so as to lead the relevant high-level leaders and stakeholders to pay attention and recognize it, which is very important. Therefore, a security consultant who does not understand the height of business strategy and security strategy, and is unable to make decisions and cleverly guide, may not even be able to stand in the pre-sales stage, and the final delivery of this project will definitely be fragmented.
2. What system best practice did I choose in the initial exploration of the financial 'CASE':For this case, I chose a very general system construction framework. After research, I found that it cannot be directly applied to the consulting of security system construction. Security is actually just a small part of this system, but I have improved and referenced the ideological methods, and also incorporated the customer's needs.
3. Why should we consider the roles involved and the so-called organizational structure in security:Why is the organizational structure important? Because the foundation of security is designed around the business, if the choice of participants in the organizational structure is not done well, a security consulting project will not be done well. Therefore, in the framework I have designed, I suggest the following participating roles:
Important organization: Financial Information Technology Department
Stakeholders (including senior leaders and those defined, including work content involving and having information security risk management, security operation and maintenance management and operation personnel, security developers, etc.), specific participants include:
Security risk management: Security planning, audit mechanism responsible for organization, security operation and maintenance room, system planning and risk management room and other three risk management departments responsible and personnel responsible for implementation.
Security operation and maintenance management and operation personnel: System, network management personnel and data operation extraction personnel (involved in database access) operation personnel.
Security developers: Responsible for the development and testing of security business release and business data change for internal and external business systems, APP, Internet finance and other related business systems (including third-party developers).
Responsible person of business functional department: Involved in the identity verification management, access control management, data security (database operations: increase, delete, modify, query) of important internal and external business, such as card center, online banking, Internet banking, Internet finance and other business functional department heads.
3. The difference in the construction of a security system consulting compared to the traditional security service system construction and security assessment (etc.): In fact, it is completely different dimensions, governance, management, inspection, the consulting does is to connect these three in a systematic way to obtain the maximum benefit, the security service does is to maximize the management benefits, while the inspection does is to maximize the compliance benefits (this part is also very interesting, let's talk about it in detail some other time, goodbye).
PS at the end: More corrections and discussions are welcomed, freedom of speech, writing is not easy, the original intention of Freebuff is to gain discussions and exchanges, and have more friends joining in for security concerns and consultation construction, let's communicate in a friendly manner.
Friendly communication, Love and Peace.
评论已关闭