Written in advance
The opening of the random thoughts listed a lot of tables, although not the latest in 2022, it can still be looked at. Write where I think, and subsequent records will be made for different contents I understand. If you have any ideas, I hope to discuss them together. All the described contents currently only involve non-secret environments, and the content of the insurance is not within the scope of discussion.
Endpoint security market
The data part of the second article starts from the endpoint security market, and the general direction of the big endpoint security development should be fine, and the number should not be too concerned here.
In the international market: It is expected that the endpoint security market will reach 5.1 billion US dollars in 2022, with more than 150 million terminals installed with full-featured EDR, and the EDR market size will reach 42.35 billion US dollars in 25 years; Gartner tracks more than 30 well-known EDR vendors, and the top 9 account for more than 83% of the market share (carbon black, cisco, crowdstrike, cybereason, fireeye, mcafee, microsoft, symantec, tanium).
Since 2014, EDR technology has been listed in Gartner's 'Top 10 Technologies' and has remained in the top ten technologies for six consecutive years. According to Gartner's forecast, with the continuous enrichment of EDR product functions, there is at least a 5-fold growth space for EDR products globally, making it the next billion-dollar market in the endpoint security field.
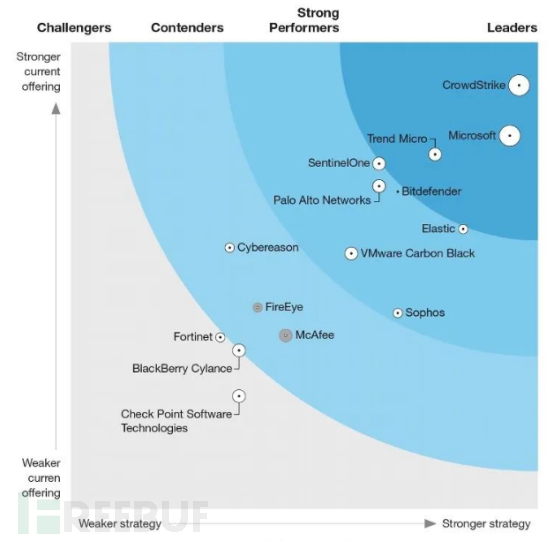
In the domestic market: The scale of China's cybersecurity market is expected to reach 9.78 billion US dollars in 2021, with the endpoint security market accounting for about 10% of the total cybersecurity scale, and there is a lot of room for development. In 2020, the number of terminals was about 100 million, with EDR accounting for about 20%, and the average price of EDR products from domestic security vendors was about 700 yuan per terminal, with an EDR output value of about 1.4 billion. The first sale provides 1-3 years of maintenance and support, and the maintenance and support fee in later years is 10%-20% of the product price.
I have made a limited comparison of the prices of endpoint security products at home and abroad. Generally, the price of domestic network antivirus products ranges from a few yuan to tens of yuan per PC, which is related to the size of the project, industry, and region. The corresponding similar products abroad range from tens of yuan to about 600 yuan (full-featured EPP+EDR) (three-year authorization). The content understood is relatively limited and cannot be used as an effective reference, but the domestic network antivirus products have now become products with compliance as the main purpose rather than selling antivirus functions, and the low price is also being cleaned up. Currently, domestic antivirus vendors make money by selling various types of authorization through value-added product functions and additional services. New functions are sold at a higher price, old functions at a lower price, and old functions are given away with new ones, and new functions with old ones are also basically the same套路.
Domestic major manufacturers
In 2018, Qianxin accounted for about 22-25% of the overall market share, and in 2021, Tianqing's sales were about 300 million, with a year-on-year increase of 67.8% in terminal security business. The next are Symantec and AsiaInfo Security, with the three accounting for nearly half of the market share. Tianqing, undoubtedly, is the leader in the domestic endpoint security market, whether in terms of product itself, market share, or product and corporate development. Looking at the situation of Tianqing, it started as a foundation of antivirus EPP plus other endpoint security functions, various combinations and integrations, a full set of products with various problems and contradictions. The underlying technology should have also been changed, and the interface has been redesigned. After Qianxin acquired JiaoTu and others, many changes should have been made, and the R&D team should have also made many modifications. Overall, the benefits outweigh the drawbacks, and product issues are also emerging in an endless stream (who's not?).
Shenxinfu launched EDR in 2018, and by 2020, it occupied 7.4% of the national terminal security market, ranking third. In my view, Shenxinfu's endpoint product line is a relatively eye-catching existence. From the newly released EDR version, it is just a simple antivirus engine plus a few small functions that can be patched together, with an unattractive and not user-friendly interface. However, within two or three months, Shenxinfu has iterated several versions in a row, gradually finding its own rhythm in endpoint security products. The EDR联动 with its own other products (firewalls, etc.) has opened the doors of these comprehensive security vendors. Linking has always been done by someone, but not well done. I'm not clear about how good Shenxinfu's product technology is, but they have managed to make a splash through strong channels and a team of about 200 endpoint security professionals. I feel that Shenxinfu has not fully understood what endpoint security is supposed to do or what EDR is supposed to do. They were not clear in 2018 and 2019, but after more users, various feedbacks, and iterations, they quickly became a mainstream domestic endpoint security product, at least in Shenxinfu's territory. However, it is not clear whether they have become complacent with the endpoint product line in the past two years, as there seems to be no more investment, and whether resources have been shifted to PC sandboxes, causing the EDR product to temporarily stall.
Qingteng Cloud has expanded rapidly in the financial industry, with sales reaching about 120 million in 2020. Qingteng Cloud has now become a product of concern for many companies. After conducting baseline checks and enriching detection content with several libraries, it is now preparing to develop XDR. It seems that Fu General Manager is very concerned about requirements and technology, able to do anything and everything, with researchers and sufficient R&D, and the product has been well developed in the past two or three years. Expanding the market should allow it to occupy a larger share.
Operating System
In enterprise users, the general operating systems Windows and Linux systems, over 81.45% of the mainframes use Linux operating systems, while only 18.55% of the mainframes use Windows operating systems. Due to the reasons of Linux's compatibility, modularization, resource consumption, etc., enterprise users tend to choose Linux more.
In the mainframes with Linux systems, Redhat/Centos accounts for the majority, and Ubuntu and Suse are also common Linux distributions in enterprise user systems, along with a few systems like Debian.
Industry Users
1Finance
The financial industry, as a traditional heavily regulated institution, has generally formed a relatively完善的信息网络安全组织 and management system. Users have continuous needs for endpoint security protection, detection, and management, but there are high requirements for product functions, maturity, and stability. At the same time, insurance and securities security personnel may choose foreign security products. The main security risk events are concentrated in ransomware, cryptocurrencies, APT, phishing attacks, etc. Security vendors and security product evaluations will refer to the ATT&CK framework, which is widely used in actual network security construction. The domestic endpoint detection and response product Qingteng Cloud has a relatively high proportion in the financial industry. From the perspective of intruders, each intrusion and attack behavior ultimately needs to be landed in the system. Deploying antivirus software and EDR on PCs and servers, intercepting malicious code, and analyzing and judging abnormal behavior are currently common protective measures in the technical defense system of financial industry users.
2Oil & Stone
Oil and petrochemical industries have successively specified multiple information security standards and processes since the early 2000s, with significant developments in areas such as information security policies, information security ecosystems, and innovative fields like 'Intelligent Manufacturing'. Years of experience in heavy protection and network defense have made endpoint security products very familiar. Since 2018, the Ministry of Public Security's First Research Institute's Net Defender G01 has been installed on PC terminals in oil and petrochemical industries one after another, but the actual effect has not been very ideal. After 2020, G01 has been recognized by users in some areas through multiple iterations. The demand for endpoint security in oil and petrochemical industries is very extensive, from office PCs, servers, and virtual machines to the front-end machines, industrial control computers, and intelligent devices involved in pipeline, factory production workshops, and product sales (such as gas stations, etc.), all of which require unified security control. The main environments and scenarios of oil and petrochemical industries are traditional + industrial control + Internet of Things + private cloud, with various mixed complex scenarios. Endpoint products need to meet the installation, deployment, and operation and maintenance requirements of complex scenarios, and endpoint security products need to meet the basic requirements in terms of compatibility and stability, while also achieving a high level of security protection.
The '2021 China Petrochemical Terminal Security Integrated Management System Test Outline' specifically describes the reasons for the realization of terminal security protection capabilities of the terminal security management system, verifies whether the terminal security integrated management system meets the actual requirements, and serves as a reference for product selection. This includes compatibility installation testing, terminal asset management, secure login, antivirus management, terminal security monitoring, terminal auditing, mobile storage medium management, and control of illegal external connections as the test content of functional items.
3Power
Over the decades of development of power grid network security, although a relatively complete security defense system has been established based on laws and regulations and systems, but from the perspective of the existing network security defense system, it is still generally adopting traditional feature-based security defense technology, using feature samples as the basis for judging attack behavior. When facing unknown threats, 0day attacks, and other new types of attack behaviors, there are problems of static detection, passive response, and lagging in processing. Branch companies in various places have many years of experience in using terminal security products and are also seeking technological innovation in endpoint security. The power system also has various types of endpoints (such as PCs, servers, virtual machines, front-end machines, industrial control machines, and intelligent equipment), and the same environment and scenario are traditional + industrial control + Internet of Things + private cloud, with various mixed complex scenarios. Endpoint security products can be deployed in power office networks and four Internet domains, and can also be customized products that meet the requirements of the power grid industry in the three or two areas for industrial control + internal network host adaptation.
4 Production and Manufacturing
The endpoint covers the entire range from the industrial equipment layer, edge layer, enterprise layer to the industrial layer, including simple sensors, PLCs, and servers with significant computing power. In industrial environments, endpoints can be located on dedicated hardware, shared devices, or virtualized systems. Currently, security vendors in the production and manufacturing industry are more concerned about network and protocol security, and their focus in endpoint security protection is on the trust relationship, identification, access control, authentication, and integrity protection of endpoints. These contents cannot effectively respond or guide administrators to perform correct event handling and measures during security incidents. Since the BlueKeep outbreak, security managers in the production and manufacturing industry have begun to pay attention to edge hosts and industrial control equipment in the system, and have begun to pay attention to endpoint security. The application environment of industrial control applications is almost the same in various enterprises, and the security issues are also relatively clear, lacking solutions and compatible products. Currently, domestic vendors such as Weinut and Liufang Yun cannot meet the threat risks faced by endpoints in the current industrial control field, which will be another outbreak point for endpoint security.
User Demand Characteristics
1 Cloud Security
Due to the fact that the host and cloud host bear a large amount of core business assets, users generally have a high requirement for the safety performance of the product. Large enterprise users have complex business scenarios and strong strength, and prefer the lightweight Agent mode of cloud host security, which is used to deal with complex attack problems at the middle and upper levels. For small and medium-sized enterprises, the basic security functions provided by cloud vendors for cloud hosts have basically met their daily business needs, so they prefer security configuration management and reinforcement services.
The automation deployment of security products using AI will become a user's essential need. The protection of key sensitive business in the cloud will definitely become a focus. Cloud vendors should take the initiative to integrate strengths and compensate for weaknesses, and provide users with a complete security solution in the role of an integrator.
2 Compliance construction
The issuance and implementation of the 'Equal Protection 2.0' standard, as well as the corresponding security detection and prevention content for terminals in the standards and requirements issued by various industries; the intrusion prevention involving endpoint content in the security computing environment evaluation content of 'Equal Protection 2.0' can be used as the repair and supplement of system re-evaluation in the overall evaluation score.
3 Security prevention
In recent years, the methods of intrusion and destruction have been changing, mainly developing towards ransomware, fileless attacks, antivirus-avoiding malware, and 0day vulnerability exploitation. The existing security detection and protection products can no longer meet the current severe situation of network security, and the security detection, protection, and response capabilities of security products have become the main concern of customers.
4 Network defense & security protection
In the past two years, customers are more inclined to use security products and capabilities that can identify, detect, prevent, and trace evidence during network defense and security protection work. In the real attack and defense process, users experience the difference and gap between protection capabilities and detection and response capabilities.
5 Client program
Running multiple and various security products on the same endpoint affects the performance of the endpoint and leads to complex operation and maintenance processes, making current users more inclined to choose comprehensive endpoint security solutions to reduce operation and maintenance and resource costs.
6 Compatibility
The frequent occurrence of endpoint security incidents leads users to consider comprehensive deployment and unified management in product selection. The scope of endpoints ranges from terminal needs to servers, virtual machines, industrial control equipment, etc., and the compatibility and adaptation degree of products have started to become the main consideration for user needs.
7 Attention indicators
Attention indicators of customers for security threats
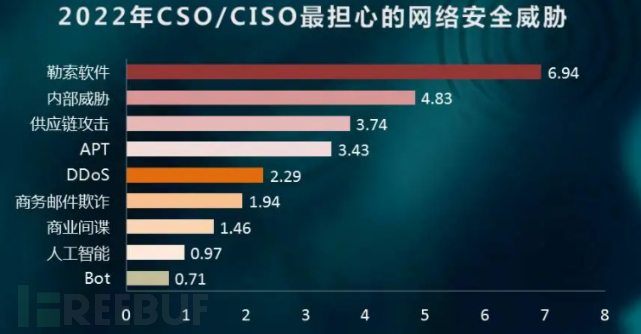
Extracted from: GoUpSec Network Security Market Trend Survey Report Based on the Evaluation of Party A Users
Attention indicators of users for security vendors
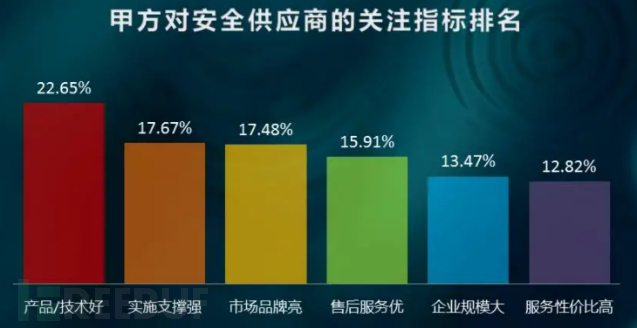
Extracted from: GoUpSec Network Security Market Trend Survey Report Based on the Evaluation of Party A Users
8 2Party A's expected investment in network security in 2022
Application and data security, as well as endpoint and network security, occupy the top two positions.
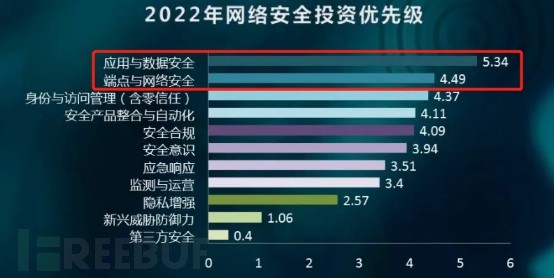
Extracted from: GoUpSec Network Security Market Trend Survey Report Based on the Evaluation of Party A Users
评论已关闭