Recently, I received a WeChat message from a friend, saying that for some unknown reason, his computer had been infected with ransomware, and all his document files had been encrypted and could not be opened. He asked me if I could help him check it out and find out the cause, and then give him some security suggestions. Upon receiving this message, I felt very touched. Because my computer has not installed any third-party antivirus software for many years, yet it has remained safe and virus-free as usual.
I think this may be due to my familiarity with the intrusion methods of hackers, which allows me to avoid them well in my study and work. Taking this opportunity, I organize the hacking intrusion methods I have learned over the past ten years, which I think are representative, and demonstrate them in a simulated manner to restore the process of hackers' intrusion and briefly introduce the intrusion principle, making it convenient for everyone to understand. I have organized 7 types of intrusion methods, with increasing difficulty level, many of which may颠覆大家的认知, see how many you can prevent? Without further ado, let's start the simulation demonstration!
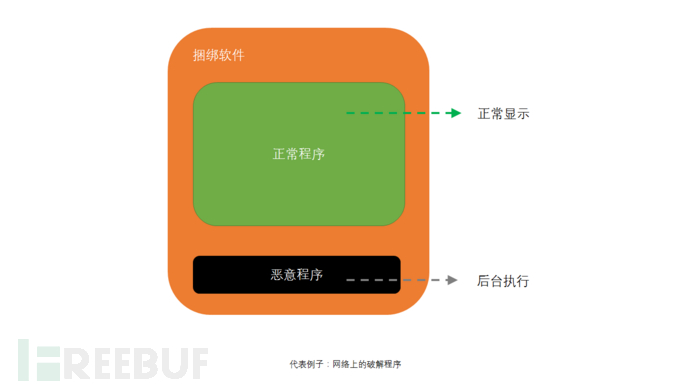
The first type of attack technique: bundling software

We often download and use some pirated software from the internet. When we download and run it, the virus or trojan also starts up! Although this method is simple, it is currently the most widespread and effective attack method on the internet. Even if the antivirus software reports a virus, we choose to ignore it~

In fact, the bundling software we run contains a normal program and a malicious program; when running, both programs are started simultaneously, but the virus does not display an interface, so everyone only sees the program with normal functions.
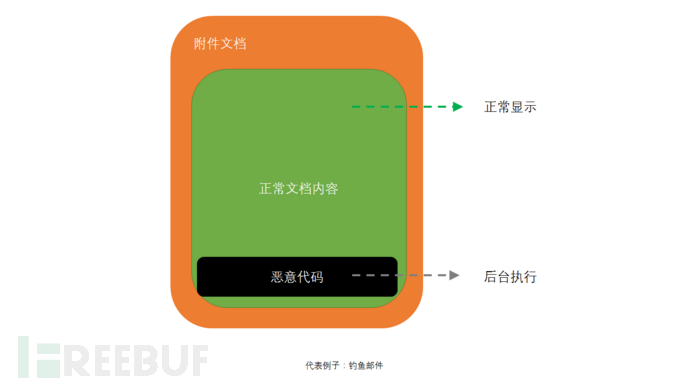
The second type of attack technique: email attachments
We often receive some emails from strangers, which may contain attachments of Excel or word documents. We can't help but be curious and download them, then run them directly. The document can be opened normally, but we didn't expect to be infected after running it.

In fact, the word document we download is actually carefully crafted by hackers, which contains malicious code inside. When we run this word document, it triggers this malicious code, thereby causing us to be infected.
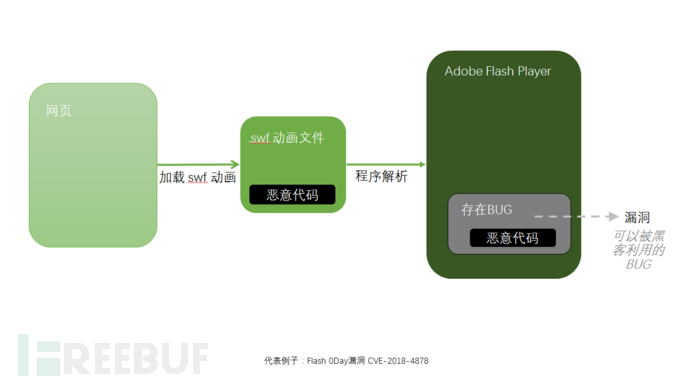
The third type of attack technique: malicious links, phishing websites
We often receive SMS or emails disguised as messages from merchants, which contain URL links. When we click on the link, we get infected.

The reason is that the page opened loads a .swf file carefully constructed by hackers, and the web page calls the Flash program for parsing. This Flash program has a vulnerability (a vulnerability is a BUG that can be exploited by hackers), thereby triggering the execution of the malicious code.
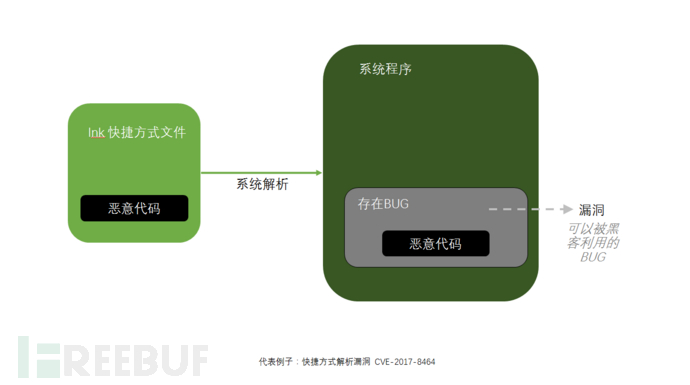
The fourth type of attack technique: 见光死
Some students may think that as long as we don't double-click to run the program, we won't be infected. Too naive~ There have been such vulnerabilities before,号称“见光死”, meaning that as soon as we see this file, we get infected.

In fact, the lnk file inside is a carefully crafted shortcut by hackers, which inserts a malicious code. When this shortcut is parsed by the system, it triggers a vulnerability in the corresponding parsing program, thereby executing the malicious code and causing our computer to be infected.
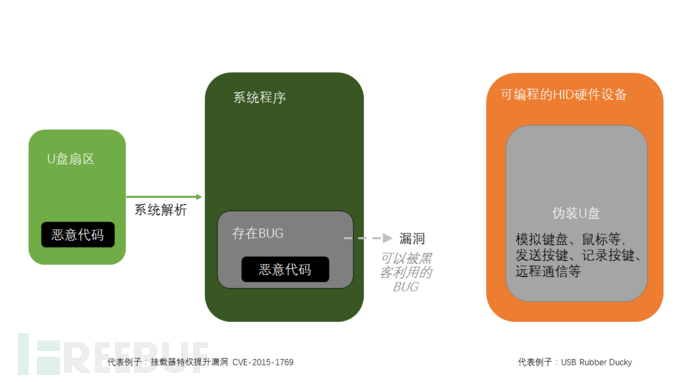
The fifth attack technique: mobile devices, infected immediately after insertion
Don't know if everyone has picked up a USB flash drive? After picking up a USB flash drive, aren't you curious, can't help but plug it into the computer to see what's inside? Okay, the moment the USB flash drive is inserted into the computer, the computer is infected.

The sector data of the USB flash drive has been carefully modified and virus code has been inserted; when the USB flash drive is inserted, the system loads and parses the USB flash drive, directly triggering the vulnerability to execute malicious code.
Programmable HID chips (Human Interface Device, a device that computers directly interact with humans, such as keyboards, mice, etc.) have appeared on the market, simulating keyboard devices, sending keystrokes, recording keystrokes. Without exploiting vulnerabilities, the device will immediately execute keystroke commands and perform malicious operations when inserted.
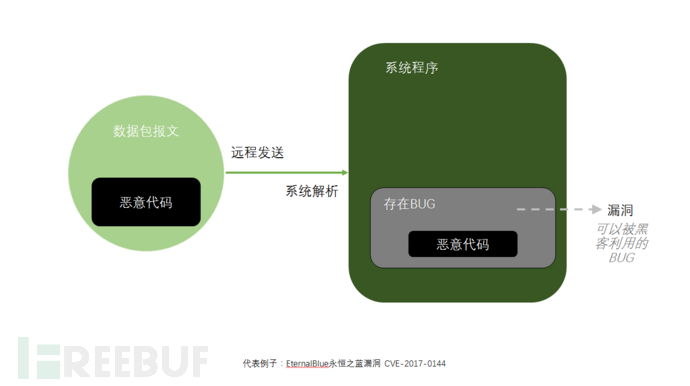
The sixth attack technique: attack you through the network cable
You should have heard of the

Because the data packets sent to port 445 are carefully constructed, when the SMB service processes the received data for parsing, it will trigger a vulnerability, leading to infection.
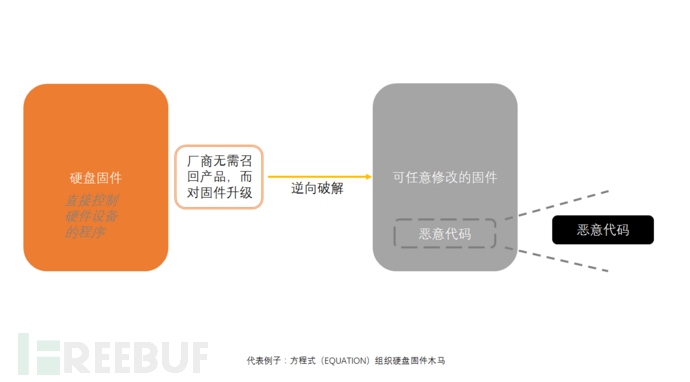
The seventh attack technique: firmware implantation, dimension-reduction strike
The last one can only be said to be a dimension-reducing attack. This has far exceeded the scope of my technical level, and can only rely on imagination and speculation!
Too brutal!!!
The firmware of the computer's hard disk is used to directly control the underlying program of the hardware device, and manufacturers can upgrade and update the firmware without recalling the product. Hackers implant malicious code by reverse engineering the interface instructions and firmware code of the firmware update.
So the hard drives we buy through irregular channels are very likely to have been implanted with viruses and trojans.
Summary
After watching these 7 types of hacker attack techniques, how many can you block? The Internet is fragile, full of insecurity and deceit! Don't worry, as long as we remain vigilant:
Upgrade software in time, install security patches.
Obtain software from official channels, do not download or run unknown files randomly, do not insert USB flash drives randomly.
That will basically prevent 99% of the viruses! The remaining 1% can only rely on luck.
The biggest problem with virus and trojan is not how to cause damage, but how to be executed; in fact, it's like doing a thing: the biggest problem is not how to do it well, but how to start.
Welcome to follow the official account:
评论已关闭