With the rapid development of emerging technologies such as cloud computing, virtualization, big data, and the Internet of Things, the enterprise IT architecture is transforming from 'bounded' to 'unbounded'. Traditional security boundaries are gradually eroding, and at the same time, the zero trust with the 'de-bordering' security concept is gradually entering people's视野, becoming a new idea and new architecture for solving new era cybersecurity issues.
01The development process of 'Zero Trust' security
In 2004, a group of IT security managers proposed at the Jericho Forum that in complex enterprise IT networks, traditional network boundaries are disappearing, and firewalls and other boundary gateways have become stumbling blocks to the development of e-commerce. When building enterprise networks, it is necessary to eliminate such boundaries (i.e., 'de-bordering'). However, opponents believe that this is a very confusing approach. After 'de-bordering', how should the cybersecurity protection system be constructed? This was a difficult question to answer at the time.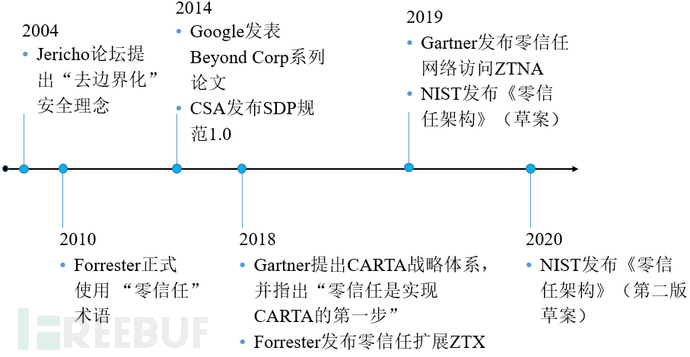
In 2010, John Kindervag, an analyst at Forrester, proposed the concept of 'Zero Trust', outlining the blueprint for zero trust security in the industry. Since then, more and more cybersecurity experts have begun to focus on 'Zero Trust'. In February 2020, the National Institute of Standards and Technology in the United States issued the second draft of 'SP800-207: Zero Trust Architecture', marking the transition of 'Zero Trust' from an idea to engineering practice and even standardization. Throughout the development of zero trust security from its inception to gradual maturity, the 'boundary issue' has always been the core problem that zero trust is committed to solving, and it is also the key to understanding 'Zero Trust'.
02Reconstructing the security boundary around IT assets
In traditional IP networks based on the boundary security model, the security boundary overlaps with the network boundary. When building enterprise IT networks, the first consideration is how to meet the business needs of the enterprise through the construction of basic networks and business systems, and then deploy the corresponding security devices at the network boundary according to the overall requirements of the network security strategy to form a security boundary. In other words, the overall progress of network construction is 'first smooth, then secure', and the security boundary is overlaid on the network boundary.
In addition, network security products based on the boundary security model pay too much attention to the prevention of external (Outside-In) attacks and have a genetic defect of 'preventing external but not internal'. This leads to their inability to respond to internal (Inside-Out) attacks from within the network. Once the attacker breaks through the boundary or malicious users appear in the internal network, the boundary is as if it does not exist for them.
The characteristics of the network security model based on the boundary are simple deployment and low cost of security construction, but the boundary position is not flexible enough. Once the position of the protected resource or the attacker changes, the security boundary cannot provide any protection for sensitive assets. This is also one of the main reasons why the Jericho Forum believes that the boundary gateway is outdated, but unfortunately, although they realized the need to eliminate the boundary gateway, they did not propose how to rebuild the security boundary.
In terms of the essence of access control, regardless of the type of network security architecture adopted, it is necessary to set up a 'fence' (i.e., security boundary) between the access subject and object in order to implement access control over protected resources. When the positions of the subject and object are relatively fixed and can form a stable boundary, the security model based on the boundary is naturally capable. However, with the 'cloudification' of IT resources, when the positions of the subject and object can change and may change at any time, constructing a dynamic and controllable 'digital' security boundary around sensitive resources becomes the only solution.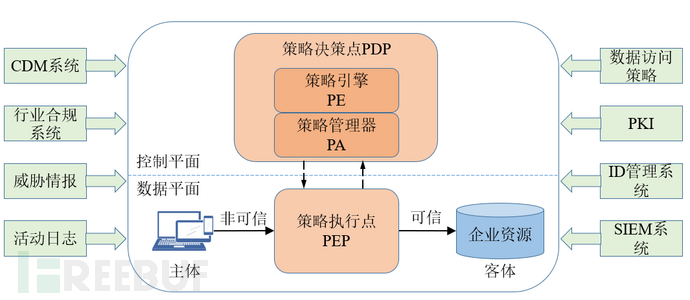
In the zero-trust architecture proposed by NIST, policy decision points and policy execution points, among other policy components, collaborate together to form dynamic security boundaries around IT resources as needed, among which:
◆ Policy Engine (Policy Engine). Responsible for finally deciding whether to grant access permissions to subjects (access objects) for resources, with its core role being trust assessment. PE uses enterprise security policies and inputs from external sources (such as IP blacklists, threat intelligence services) as 'trust algorithms' to decide whether to grant or reject access to the resource.
◆ Policy Administrator (Policy Administrator). Responsible for controlling connections between clients and resources, creating identity tokens or credentials for clients to access enterprise resources, following the decision results of PE's policy decisions, and issuing instructions to PEP such as allowing or rejecting connections. The core role of PA is the policy decision point, which is the component for determining zero-trust dynamic permissions.
◆ Policy Enforcement Point (PEP). Responsible for initiating, disconnecting, and monitoring the communication connection between subjects and objects, its core role is to ensure secure access to the business. PEP actually includes two different components: client components (such as user-side Agent) and resource-side components (such as access control gateways on the resource side).
In addition to the above core components, there are some local/external data sources that provide decision input and policy rules for the policy engine, including: Continuous Diagnostics and Mitigation System (CDM System), Industry Compliance System, Threat Intelligence, Data Access Policy, Public Key Infrastructure (PKI), ID Management System, Security Incident and Event Management (SIEM), etc.
03Abandon the illusion of trust, the boundary is born with the resource
The 'trust' in IP networks should be gradually eliminated like other vulnerabilities in the network. The concept of 'zero trust' shifts from the boundary model 'trust but verify' to the mode of 'never trust, always verify', aiming to eliminate unreasonable trust relationships within the network. NIST proposes that the following seven basic principles should be followed in the network design of 'zero trust' security:
① All data sources and computing services in the network are considered as resources, including users, devices, data, services, etc.;
② All communications between resources must meet the corresponding security requirements (identity authentication, confidentiality, integrity protection, etc.), and are unrelated to the network location of the resources;
③ The authorization of access to each resource is on a per-access session basis, and access permissions can only be granted after the requesting party passes the identity authentication (following the principle of least privilege);
④ The authorization of access to resources is determined by dynamic policies, and factors affecting the decision of policy judgment include user identity, application/service, the status of the target resource, and behavior or environmental factors related to the security situation, etc.;
⑤ Enterprises continuously monitor and measure the security status of all IT assets to adopt different security strategies for resources in different security situations;
⑥ The authentication and authorization of all resources are dynamically completed, and must be completed before access is allowed;
⑦ Enterprises should collect real-time status data of IT assets (such as network traffic, metadata of access requests) as much as possible to evaluate the security situation of the network.
These principles are the top-level design principles of the zero-trust network, and their definition of resources implies the location of the security boundary and the granularity of the objects (i.e., resources) protected under the zero-trust architecture. In order to achieve the zero-trust security boundary, NIST proposes three implementation approaches for the zero-trust architecture:
◆ Adopting an enhanced identity management system. Taking the identity of the access subject as the key factor for creating resource access policies, the access policy of resources depends on the permissions of the subject, but factors such as initiating device and asset status may affect the final authorization level.
◆ Adopting Micro-Segmentation. Dividing protected resources (groups) into specific isolation segments and protecting the segment through a security gateway (such as NGFW acting as PEP), requiring the security gateway to have 'fast reconfiguration' capability in order to be able to respond in real time to changes in workflows and network threats.
◆ Adopting Software-Defined Perimeter (SDP). Using the idea of SDN, building an overlay network on the underlying basic network. The network controller (by PA) reconfigures the network according to the judgment results of PE's strategy, and access requests are forwarded through PEP managed by PA.
Among the above three implementation methods, the first one starts from the resource access initiator (access subject) to realize the trust process of zero trust, while the other two start from the accessed resource (access object). But no matter which approach is taken, any access to resources must comply with the security rules of zero trust. That is to say, in a zero trust network, where the resource is, there the boundary is.
When implementing zero trust network architecture, enterprises can use the above three methods as logical components, mixed and adopted in the network, so as to make full use of existing IT resources on the basis of adapting to complex network environments. According to different network structures and business workflows of enterprises, NIST has given four typical deployment models.
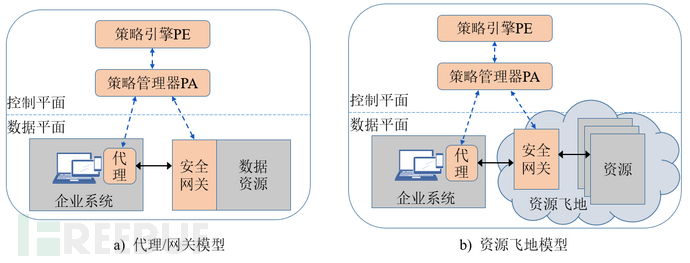
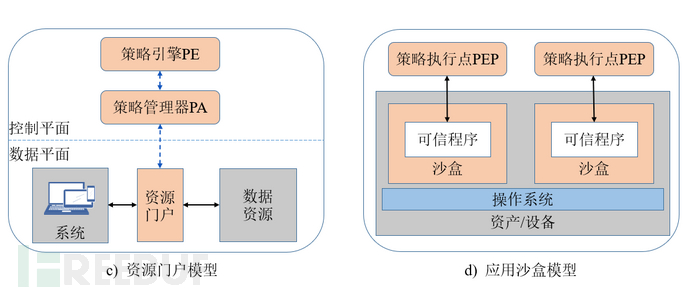
04Choosing zero trust to help secure IT assets
Due to the inherent defects of the TCP/IP protocol, it is very difficult to establish trust relationships between network entities. Issues such as entity identification and the lack of a credible third party are all hindering the construction of the trust assessment system, ultimately leading to a lack of a foundation for establishing trust between entities.
As a concept, model, and system framework, zero trust abandons the insecure trust assumptions in the 'boundary' security model and re-examines the establishment and maintenance of trust relationships in the IT resource network. By changing the way network resources are accessed, it reduces the exposed surface and attack surface, and rebuilds a secure boundary based on strategy (on-demand, dynamically) for enterprise networks, making network security management able to respond more flexibly to various complex network changes and events.
The main value of zero trust is to guide the planning and construction of security systems, which is a response to the current trend of enterprise-level network development. With the diversification of corporate office scenarios and the acceleration of the trend of business clouding, the traditional security construction methods based on boundary defense and default trust of internal networks will be difficult to effectively respond to challenges. Enterprises will increasingly recognize the value of zero trust 'never trust, always verify' for enterprise network security construction, and zero trust will become an important direction for the future development of network security.
评论已关闭