The NetEase Security Lab recently captured the RedLine Stealer malicious spyware. RedLine Stealer, first appearing in March 2020, is a malicious software primarily targeting Windows users, with the main goal of stealing the personal data and information of victims. Its spread through various channels (including cracked games, applications, and services) has made it a persistent threat to network security.
This malicious software primarily functions by stealing login credentials from various client applications, including web browsers, FTP clients, email applications, Steam, instant messaging clients, and VPN clients. Its ability to steal data from FileZilla, Discord, Steam, Telegram, and VPN clients is particularly prominent. In addition to this, RedLine Stealer can also steal authentication cookies, credit card information, chat logs, local files, and cryptocurrency wallets stored in the browser. RedLine Stealer also has the capability to collect system information, obtaining details about the victim's system, such as IP address, city and country of location, current username, operating system version, UAC settings, administrative privileges, user agent, and detailed information about the hardware and graphics card of the infected PC. The software can even detect antivirus software installed on the system.

In addition to information collection, RedLine Stealer also acts as a malicious software loader, which can be used to deploy other types of malicious software, such as ransomware, further increasing the threat it poses to network security. The software will convert the collected data into XML format and then use various defense evasion techniques to transmit it to the control server (C2 server). The C2 server is the remote control center of the malicious software, used to receive stolen data and send control commands.
It is worth noting that RedLine Stealer uses the business model of Malware as a Service (MaaS), which is common in the hacker community. On criminal forums, the price of RedLine Stealer is set at $150/month or a one-time payment of $900 for lifetime access. Its developers also sell this software on Telegram channels, accepting Bitcoin payments. Purchasers can also receive a free obfuscation program to bypass detection by security software.
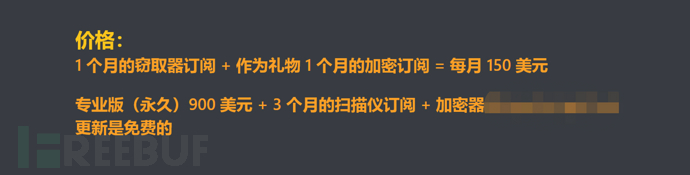
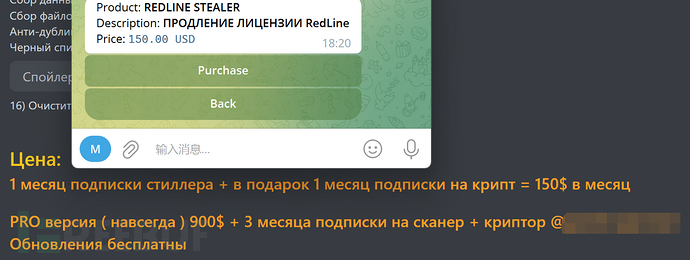 Figure 1: Sales Information
Figure 1: Sales Information
The author's last update was in June 2023, showing that the software has been continuously updated. At the same time, early leaked versions of the software are available on Github.
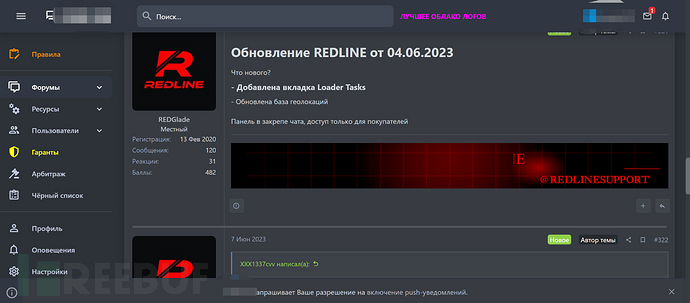 Figure 2: Update Information
Figure 2: Update Information
RedLine Stealer has multiple infection methods, including email attachments, malicious links, software vulnerabilities, social engineering, etc. Its appearance reminds us that network security cannot be ignored. It is necessary to always update antivirus software, be vigilant, and do everything possible to prevent the intrusion of such malicious software.
Sample Summary:
After executing the malicious file, it will request configuration from the C2 and issue information collection tasks based on the configuration. After collecting the data, the results will be formatted and sent to the C2.
The execution process of the sample is shown in the figure below: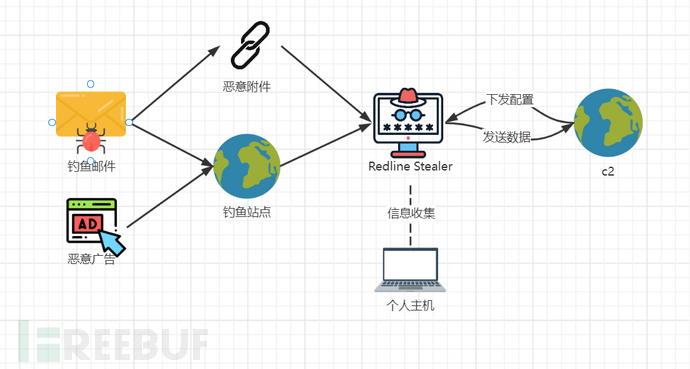
Figure 3: Execution Process
Malicious Behavior Analysis
The C2 (Command and Control) communication attempts to connect to a single server, and after decryption, it can be found that the server address is 188.124.36.242, and the port is 25802.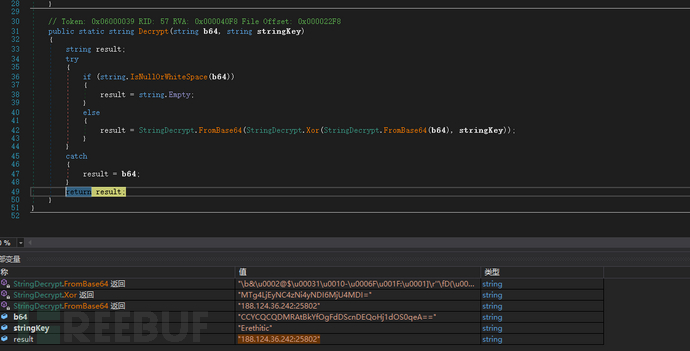
Figure 4: Decrypting the C2 Server
RedLine Stealer uses the .Net SOAP API and simple TCP binding. This converts into an encrypted, non-HTTP communication channel. Requests contain authorization information and do not check the validity of certificates.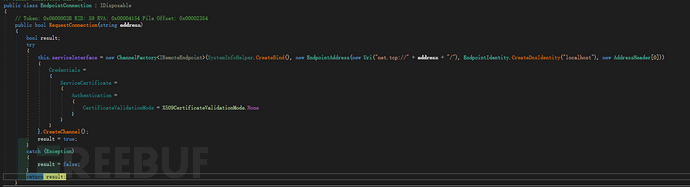
Figure 5: Creating a Communication Channel
After establishing communication, RedLine Stealer can enable or disable certain features based on the SOAP response. For example, by specifying a false value in the ScanWallets field, the malware will not scan encrypted wallets in the system. To save time, it will skip the content that does not exist on the victim's machine.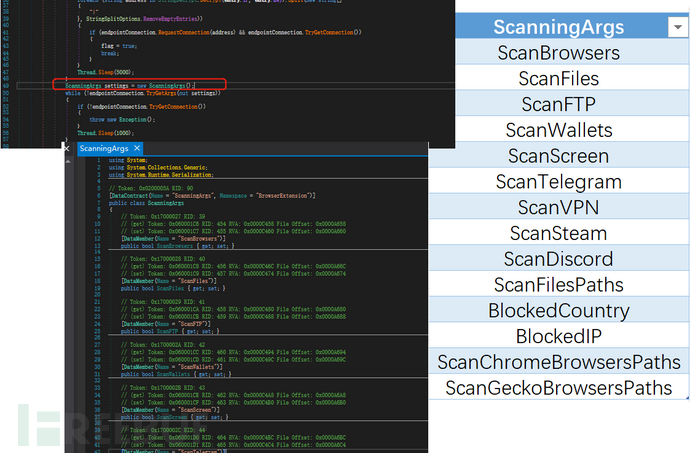
Figure 6: Scan Parameters
Redline Stealer will first scan the basic data situation and store the results in a structure named ScanResult, which will then be sent to the C2 server.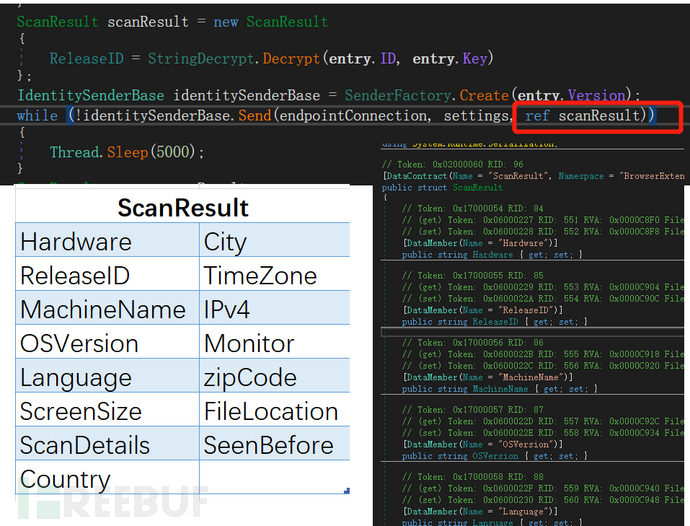
Figure 7: Scan Results
Basic information scanning can confirm some situations first, for example, if the host is in the Russian-speaking area, the operation will be terminated and the program will exit.
Figure 8: User Judgment (Geographical and Encoding Judgment)
There is a ScanDetails function in the follow-up, which collects detailed data about compromised hosts, such as antivirus software, installed input language lists, installed program lists, running process lists, and FTP connections, as shown below: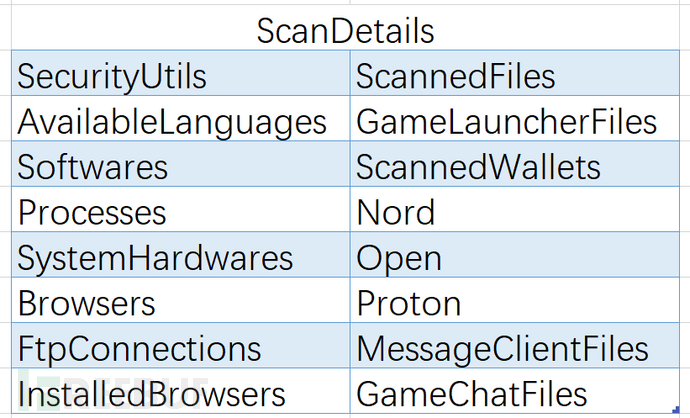
Figure 9: Scan Details Function
This malicious software uses WMI (Windows Management Instrumentation) to collect host information, such as enumerating any installed security solutions. This malicious software enumerates all installed security solutions. It can connect to the ROOT\\SecurityCenter or ROOT\\SecurityCenter2 namespace to call SELECT * FROM AntiVirusProduct to obtain any antivirus, anti-spyware, and firewall (third-party) software.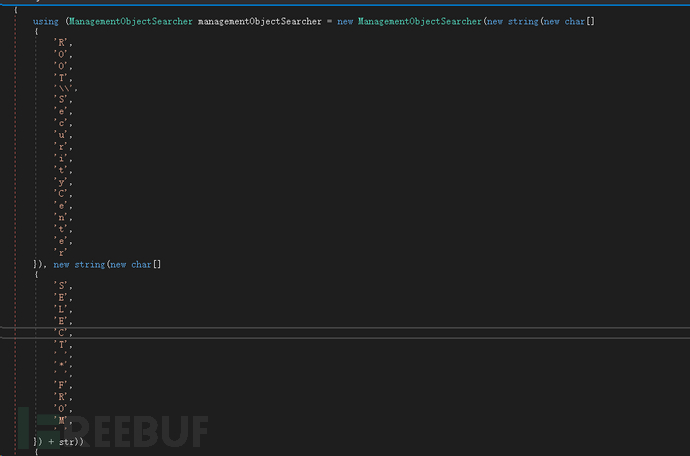
Figure 10: Antivirus Query
This malicious software steals cryptocurrency wallets, posing a serious threat to the security and stability of the digital currency ecosystem with the powerful combination of advanced hacking technology and stealthy operations. RedLine targets many wallets such as Armory, Atomic, BinanceChain, Electrum, Exodus, Ethereum, Monero, Jaxx, Guarda, and more.
ATT&CK Mapping Diagram
 Figure 11: RedLine Stealer ATT&CK Mapping Diagram
Figure 11: RedLine Stealer ATT&CK Mapping Diagram
Summary
RedLine, due to its wide range of data types stolen, convenient operation, and low price, has spread widely. The wild samples of RedLine have exceeded 100,000, making it the most active spyware family in 2022. Statistics show that RedLine accounted for 15.42% of all spyware in 2022.
To respond to increasingly active spyware attacks like RedLine, we need to understand their working mechanisms and protection strategies more deeply. Spyware infiltrates the computer or device of the target user by implanting malicious software to steal sensitive data and information. Attackers typically use deception methods, such as social engineering, phishing emails, etc., to disguise the spyware software as normal files or links, luring users to download or execute them.
According to the report of the cybersecurity company CyberArk, a total of 437.8 million spyware samples were discovered globally in the first quarter of 2023, an increase of 98% from the previous quarter. This indicates that attackers are continuously updating their spyware software to make it more difficult to detect and defend against, and the threat of spyware attacks is escalating continuously.
These spyware trojan attacks can be divided into two categories: widespread propagation attacks and targeted attacks. Widespread propagation attacks mainly rely on the spread of a large amount of malicious software, aiming to infect as many devices as possible. Targeted attacks are aimed at specific targets, where attackers will deeply study the behavior and habits of the target, use more advanced technologies for attacks, and achieve long-term continuous information theft.
To effectively defend against these spyware trojan attacks, traditional security measures such as firewalls and antivirus software are no longer sufficient. In the face of targeted attacks and increasingly complex attack methods, enterprises and individuals need to adopt more comprehensive and proactive protection strategies.Zero Trust Protection is an effective method to deal with such threats.This solution requires identity verification and permission confirmation before accessing any system resources, thus greatly reducing the success rate of spyware trojan attacks.
Zero Trust Protection follows the principle of least privilege, fully verifies the identities of users, devices, and applications, combines behavior analysis and dynamic access permission management to achieve real-time threat detection and protection. Under the zero trust model, even if an attacker successfully implants a spyware trojan, their ability to steal information will be strictly limited. Through continuous learning and adapting to new threats, zero trust protection solutions help enterprises and individuals more effectively respond to the increasingly serious spyware trojan attacks. Wande Security's product SecureLink provides a complete set of zero trust protection solutions to help enterprises solve the problems caused by spyware attacks from the perspective of the overall security system. This product has the following core features and functions:
- Robust Authentication: Ensures the authenticity and credibility of user identity through multi-factor authentication, single sign-on, IP/time/geo-fencing authentication, and other methods, preventing malicious users or attackers from impersonating legitimate users to carry out attacks.
- Real-time Behavior Analysis: By monitoring users' access behavior patterns and activities in real-time, combining artificial intelligence and machine learning technologies, the trust assessment model is used to promptly detect attackers' abnormal behaviors and issue warnings and blocks to prevent unknown attack behaviors.
- Unified Access Control: Based on user identity, device status, and application requirements, implements fine-grained access control strategies to ensure that only authorized users and devices can access sensitive information and critical systems within their permissions.
- Secure Web Gateway: Provides a secure office and internet access environment, detects and blocks non-compliant network connections, provides high-speed RBI tools, isolates internet risk content from user devices and office networks, effectively preventing external malicious attacks from渗透。
- Secure Workspace: Provides a local isolated space where sensitive data and critical systems can be restricted to run and access only within the secure workspace, preventing data from flowing out to personal desktops, effectively reducing the risk of data leakage.
IOCs
MD5: 74200bd872e0b3d75b1d85332c3be083
C2: 188.124.36.242:25802
How to make ConcurrentMapCacheManager support automatic deletion of expired items
snapchat hackers for hire(Snapchat Hack)
2025 latest & emulator WeChat mini-program packet capture & mini-program reverse engineering
GamaCopy mimics the Russian Gamaredon APT and launches attacks against Russian-speaking targets
评论已关闭