Preface
Installation of LSP framework (LSP framework is the one that runs xp modules, Magisk is the one that runs LSP)
Magisk V24 and above versions can use Zygisk, V23 version does not need Zygisk but detection is not as good as V24 version
One, activate LSPosed
The LSPosed manager.apk I downloaded needs Zygisk activation
Click on the settings at the top right corner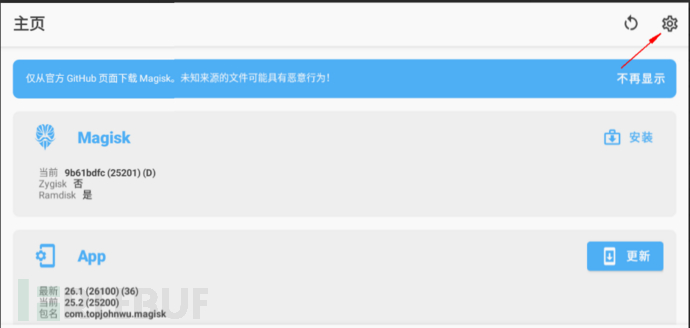
Enable Zygisk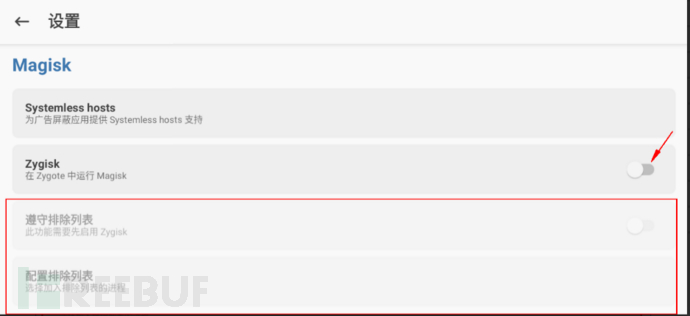
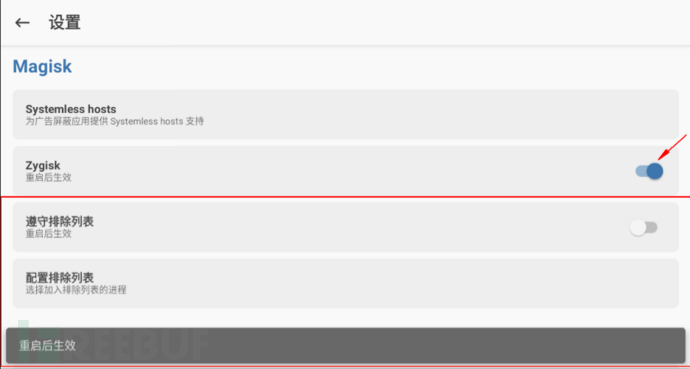
Two, comply with the sorting list & configure the exclusion list

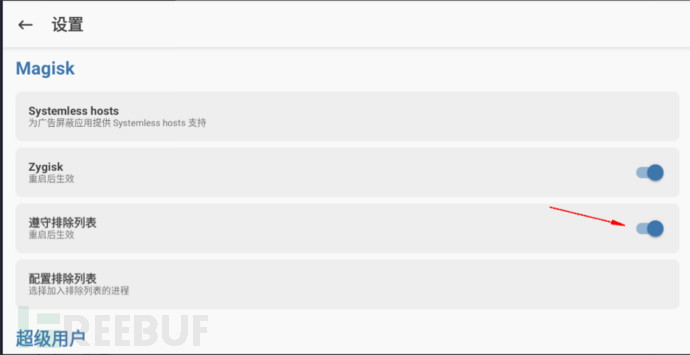
If you don't want other APPs to detect that面具magisk is installed locally, check it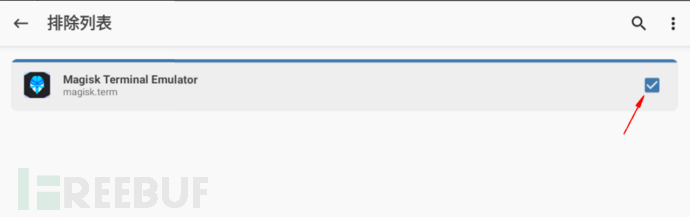
Three, install LSPosed package through module
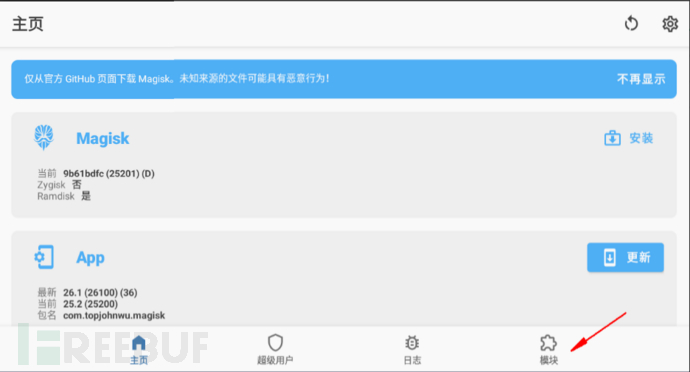
Install from local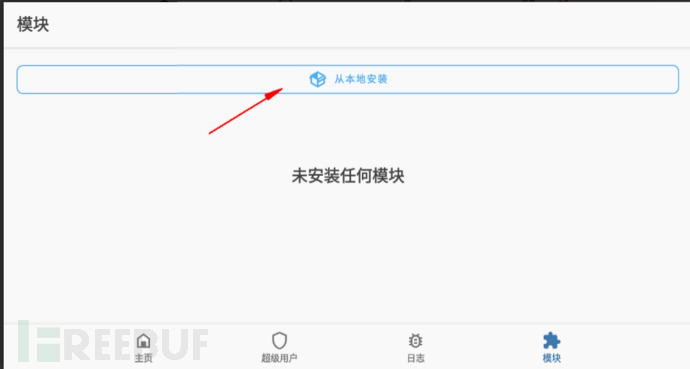
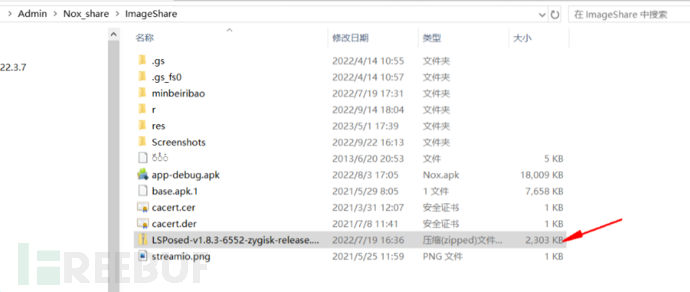
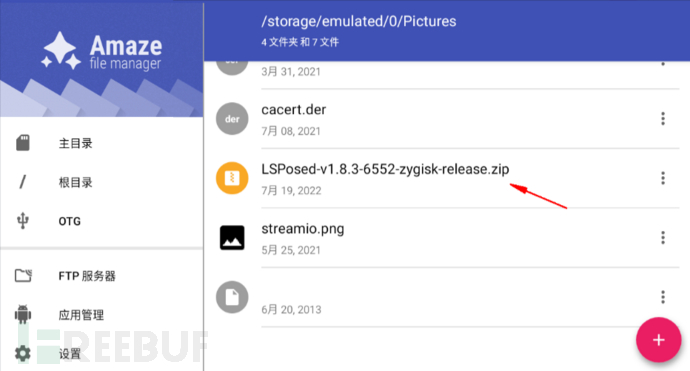
Put the LSPosed-v1.8.3-6552-zygisk-release.zip package into the shared folder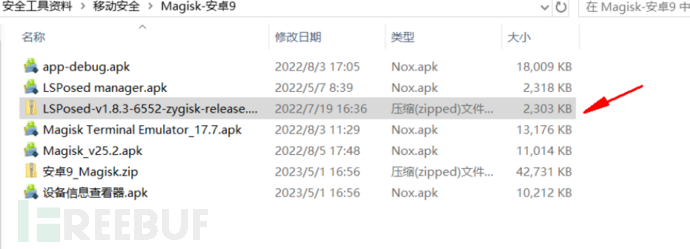
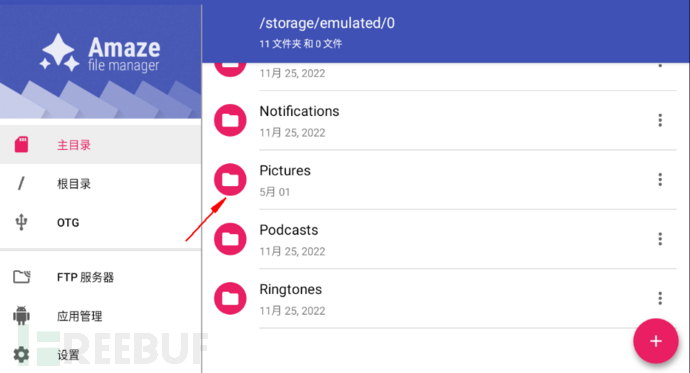
Open the file at the top left and click Amaze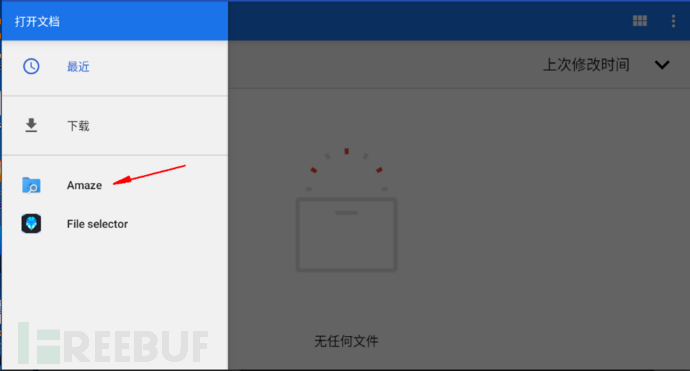
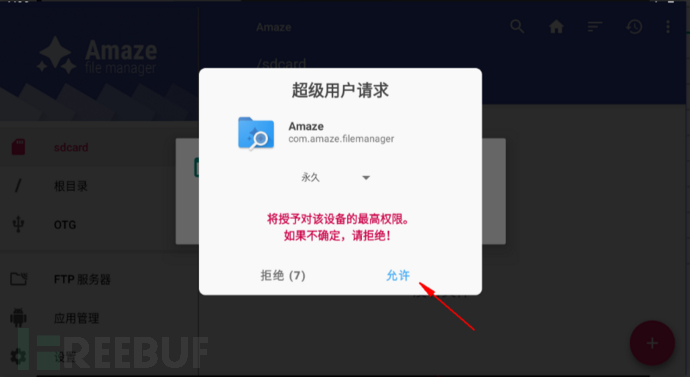
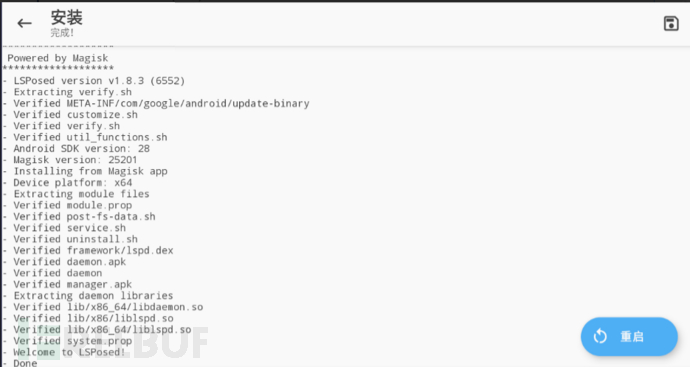
Four, successfully install & restart the phone
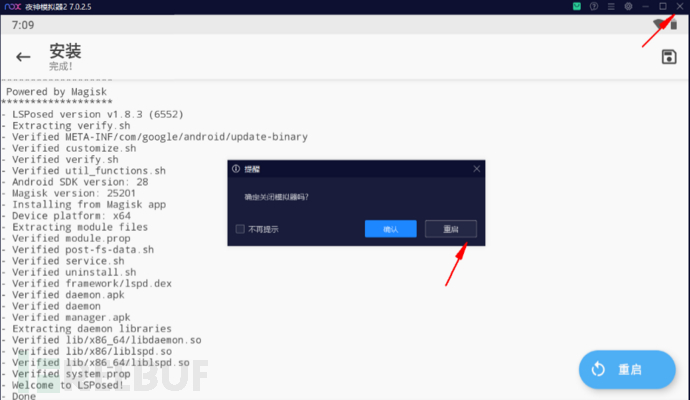
Five, install LSPosed icon
After restarting, there is no LSPosed icon, but it has been successfully installed, and we can choose to install it.
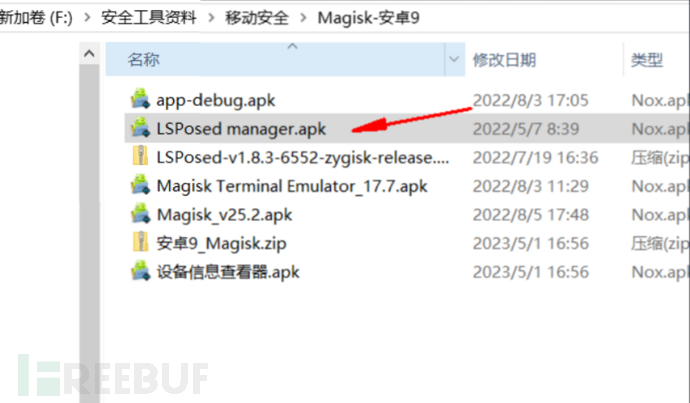

See that our LSPosed is in the active state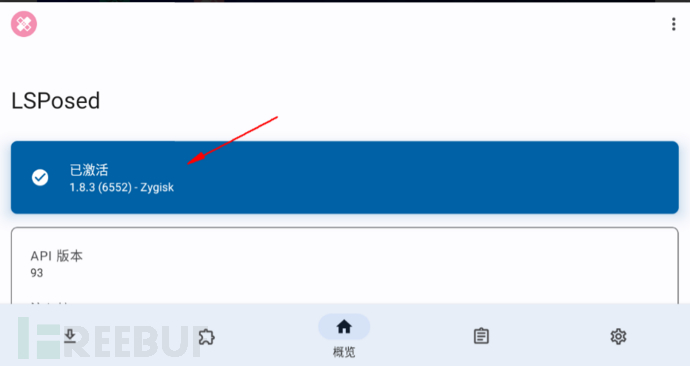
Six, test effect
1. Install LSPosed module -- application disguise
Install module -- application disguise, used to enrich the LSPosed module function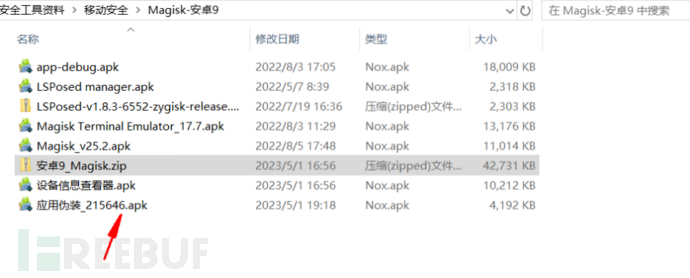
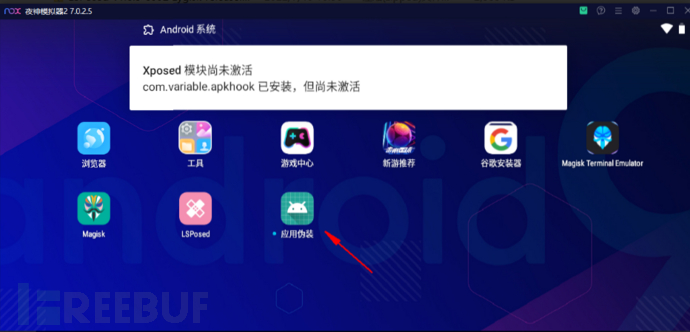
2. Install test APP
Install the device information viewer.apk again for testing later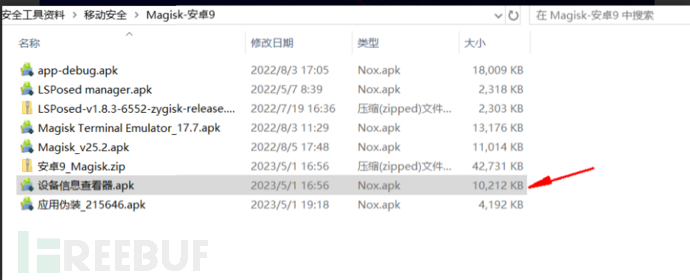
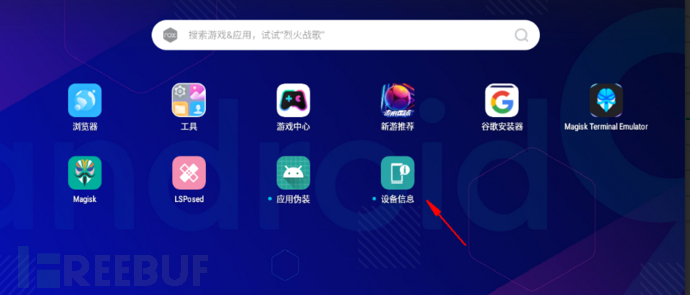
3. Start module - application disguise
Go back to the LSPosed module and enable the application disguise module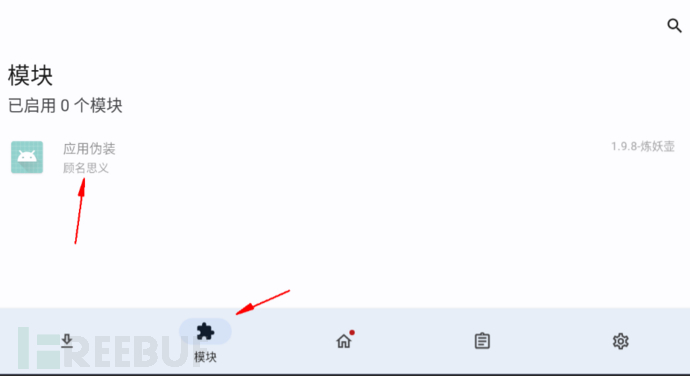
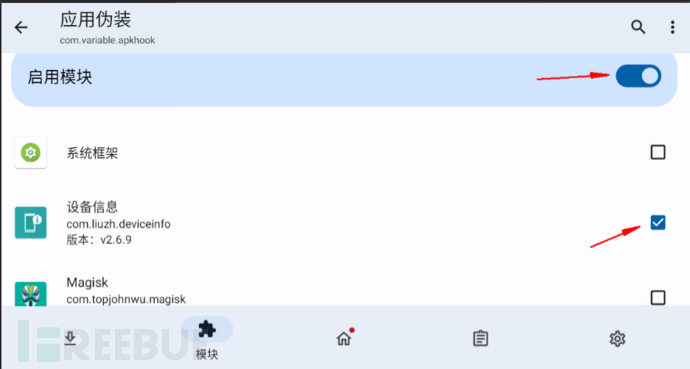
4. Record original data information
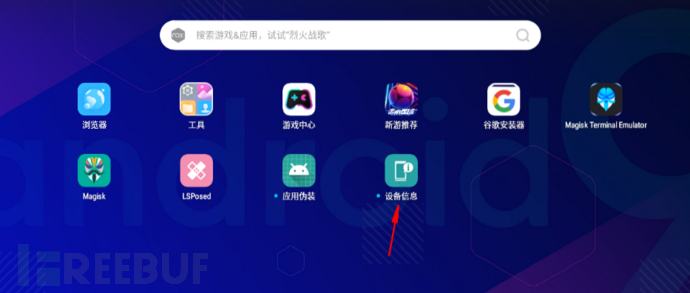
Type of device information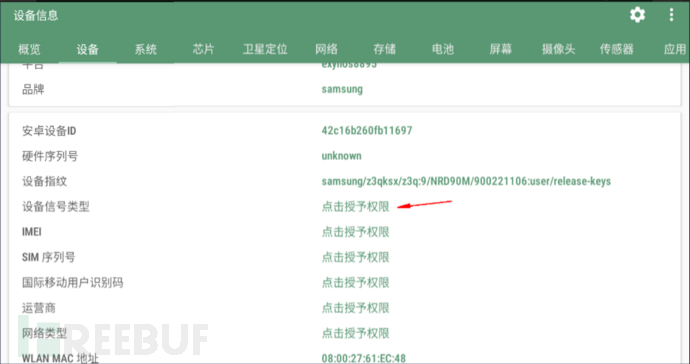
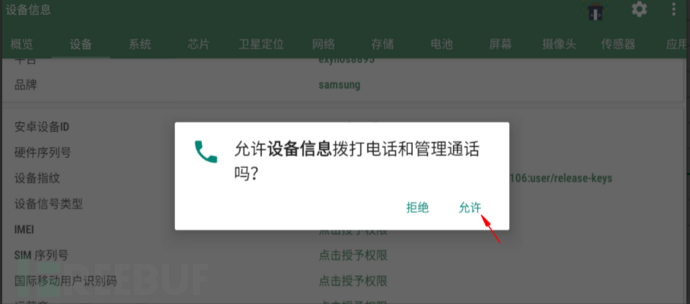
Record the current device information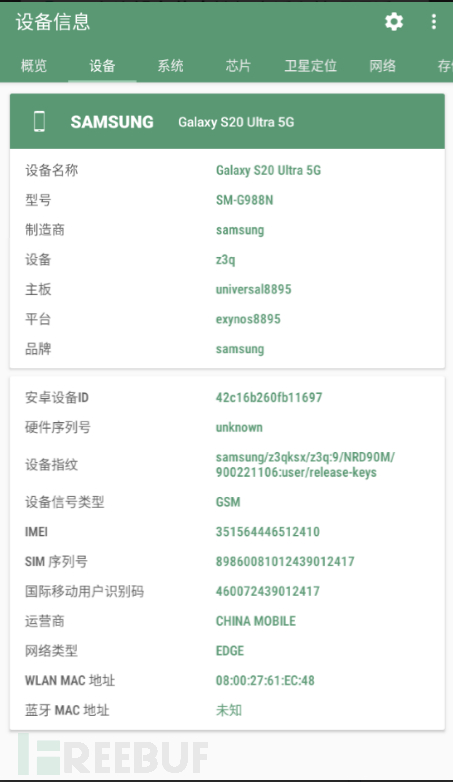
5. Application disguise -- modify information
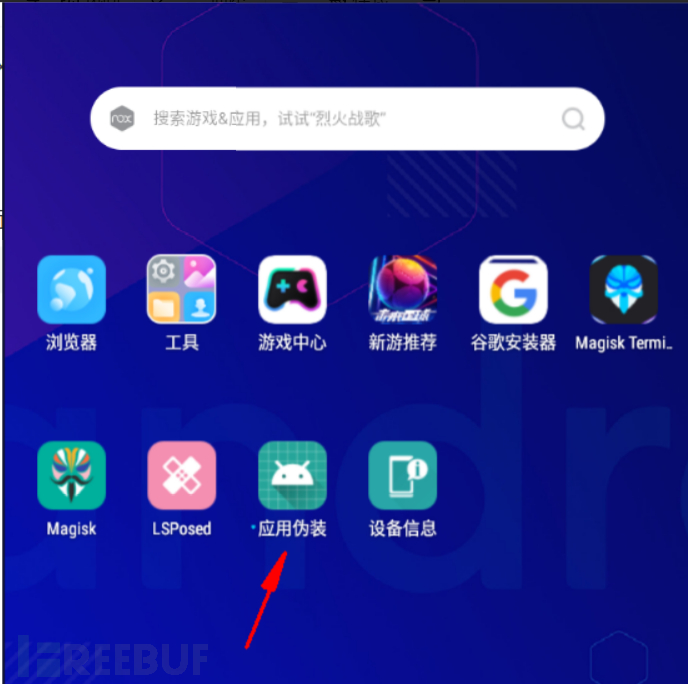
Definitely answer the questions first!!!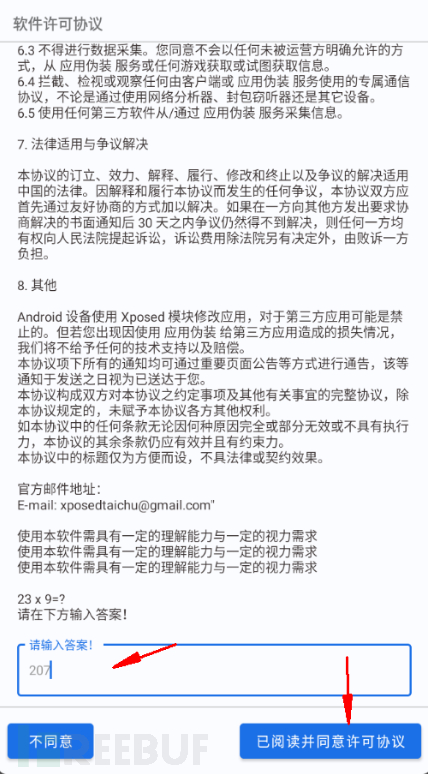
Find the APP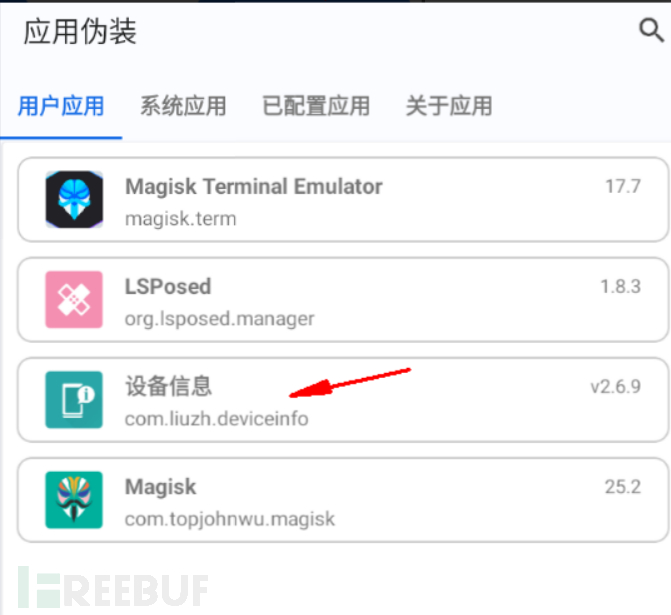
First clear the application data, there will be operations such as permissions in the middle, choose to agree, and then choose one-click random.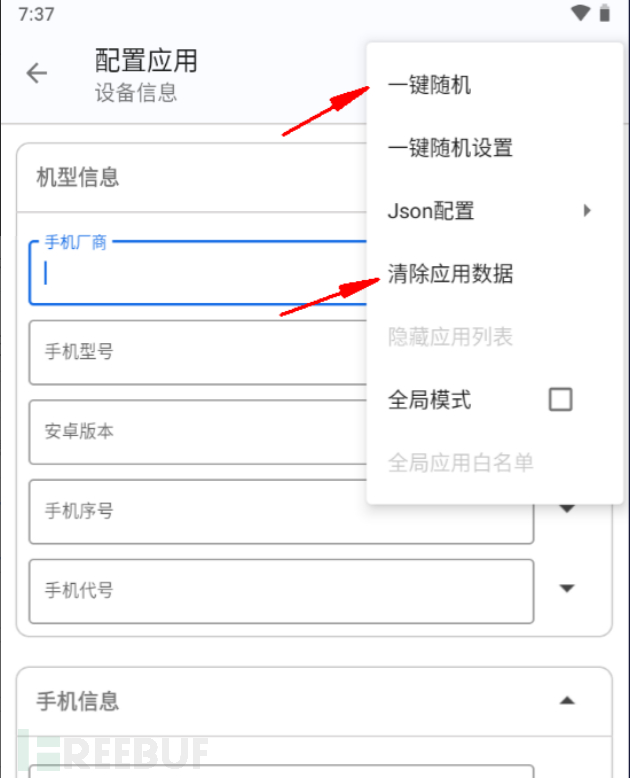
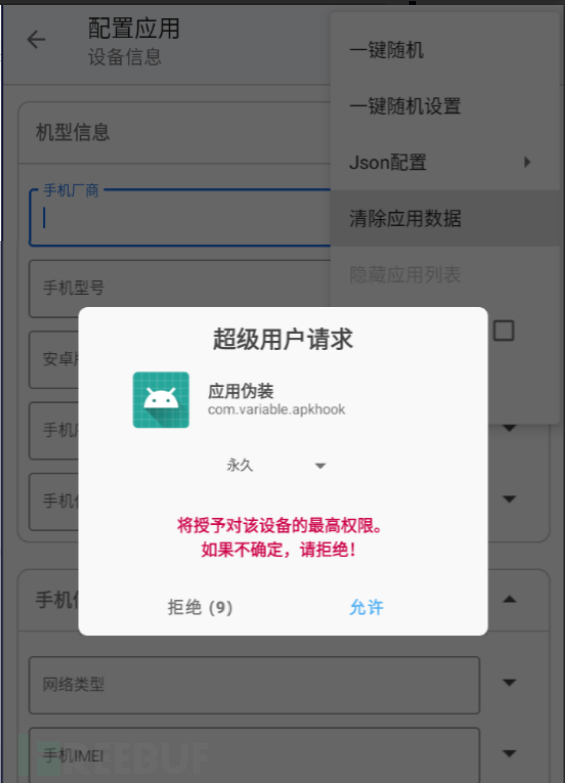
Save information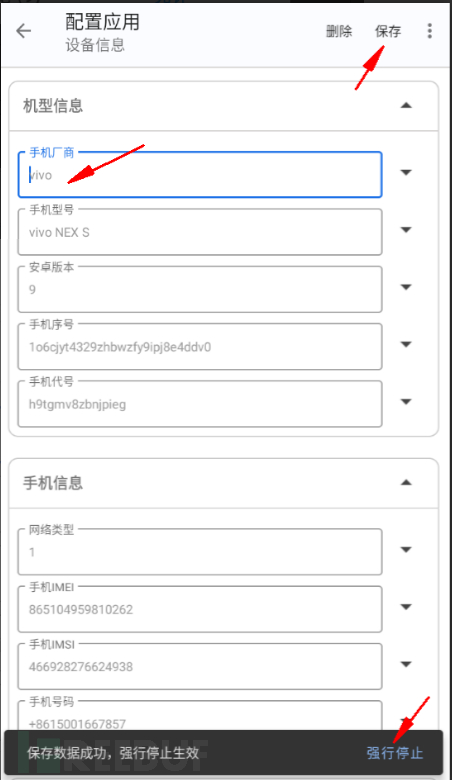
6. Modification successful
Reopen the APP to get device information for comparison, and successfully see that our device information is completely different from before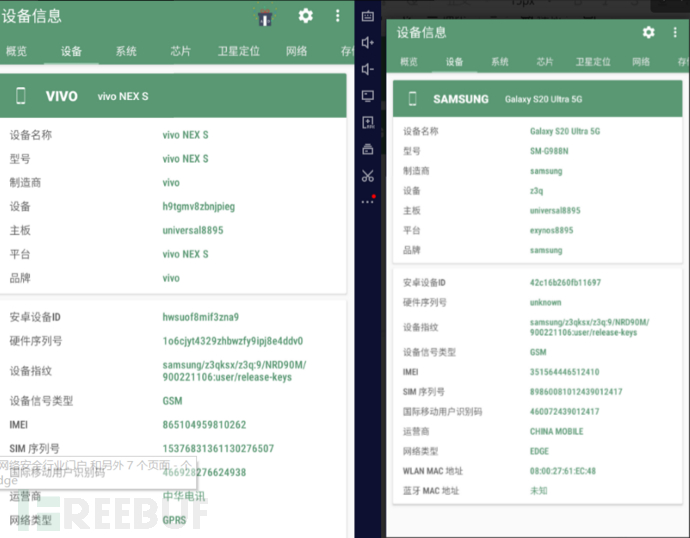
评论已关闭