1 Background of writing
Since joining the company nearly a year and a half ago, we have accumulated a wealth of experience from the initial security testing, subsequent security development specifications and code audit platform construction, mobile APP security enhancement projects, recent security testing technologies and security development, new employee onboarding training, and the security design checklist produced in the standardization project... Our accumulation in application security is also increasing. Just as I was reflecting on the gains over these past few months, the term 'SDL' flashed in my mind. The many specifications and processes we have formulated also need to be polished in various business areas. The various 'troubles' and 'difficulties' that arise during this process are extremely valuable, and I have taken note of them. (Wednesday, August 22, 2018, 18:31)
I still remember that during the previous interview, when asked about SDL, I could barely explain the process and the interviewer looked disdainful. At that time, I was responsible for the technical team of the security service provider for the party B, and indeed lacked experience for the SDL that the party A advocated but few actually implemented well. Later, I found a lot of relevant materials on the Internet, but most of them were theoretical guidance articles without substance, and there were few practical cases. Later, I主动联系了当初的面试官,请教他们公司的SDL如何开展,得到的回复却是:真正落地的公司比较少,都是一二线互联网公司在玩;外面那些paper都太形而上了,没有落地空间,有些概念可以参考,跟领导吹吹牛逼是可以的。}}

Today, the work direction has shifted from application security to being responsible for basic security. After nearly a year of evolution, the company's SDL has taken shape slightly, and all links have been basically connected and stable. The experiences and insights gained during this period are very valuable, and thus the plan to write this series of articles has been made, perhaps to bring a little reference and thought to fellow professionals during the time when SDL cases are missing. Since it is the initial practice, there are definitely some deficiencies and even errors, please correct them and discuss them warmly.
2 Overall Overview
2.1 Overview of SDL
Security Development Lifecycle (SDL) is a management model proposed by Microsoft to guide the software development process from a security perspective. It adds some necessary security activities to the various stages of the traditional software development lifecycle, and the security activities executed at different stages of software development are also different. Each activity, even if executed separately, can play a certain role in software security.
2.2 SDL Process
The core concept of SDL is to integrate security considerations into every stage of software development: requirement analysis, design, coding, testing, and maintenance. At each stage from requirements to the release of the product, corresponding security activities are added to reduce the number of vulnerabilities in the software and minimize security defects. The process is divided into the following seven parts: security training, security requirements, security design, security development, security testing, release review, and security response
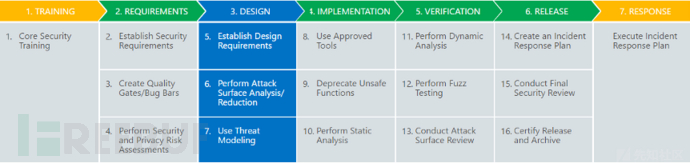
Combining actual conditions and resources, it can be divided into the following seven parts:
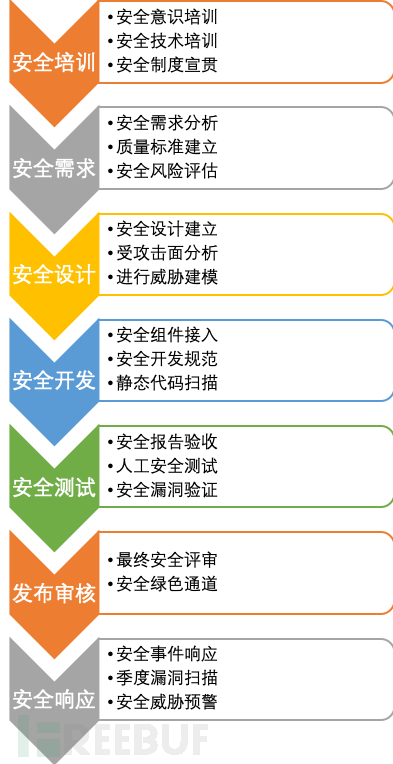
This practice is based on the initial practice of learning and implementing while promoting by the author and their security team, serving a logistics company that has transformed from traditional to internet-based, which also faces the challenges of starting security late, a smaller security team, and poor security development capabilities.
However, with the factors such as internal and external resources, internal system projects of the company, and the drive of security incidents, all new business systems and major changes in old business systems have basically been realized and implemented in accordance with SDL.
评论已关闭