
And there was no one withdrawing money from the ATM at that time. In fact, this seemingly strange system failure was actually a test: a successful penetrationFirst Commercial BankThe servers of the London branch are sending instructions to cash points 7,000 miles away to check if there is a possibility of remote-controlled robbery.
In 15 hours, a total of 41 ATMs at branches in Taichung and other districts of Taipei City dispensed 83.27 million New Taiwan Dollars, approximately 2.7 million US dollars at current exchange rates.
Although TaiwanThe police successfully captured the suspects in this million-dollar robbery case(most of whom come from European countries), but many are using ATMs (even the entire)The financial system(Defects and weaknesses of anonymous criminals are still at large.)
Ordinary ATM users cannot resist this attack on banks. But by staying vigilant, one can help the police catch the criminals. The successful capture of the robbers is inseparable from the valuable intelligence information provided by citizens. Some citizens noticed the suspicious behavior of foreigners and collected relevant information, reported to law enforcement agencies, and provided the suspect's car license plate number and a credit card accidentally left behind by the suspect.
Why are ATMs easily attacked?
like any other computing device, ATMs also have vulnerabilities.
ATMs consist of computers (and their peripheral devices) and safes. The former are enclosed in a cabinet. Whether the ATM is an independent self-service terminal or a 'wall hole', it is the same. The cabinet itself is not particularly secure or strong, which is why criminals can use simple tools and keys available for online purchase to enter the computer or safe.
Computers usually run on Windows - a version specially designed for ATMs. ATM users usually cannot see the familiar Windows desktop interface because access is restricted. What we see are user-facing applications that can help users complete transactions with the machine.
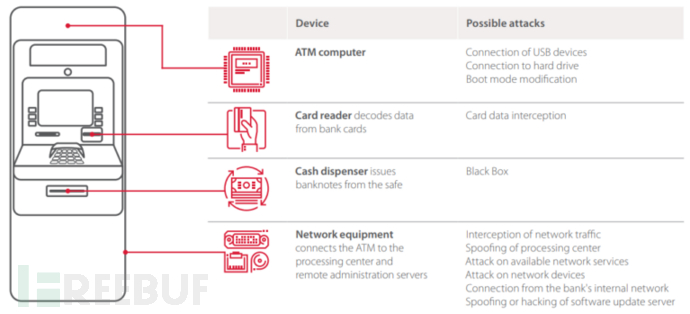
So far,many ATMsare still running on Windows XP. If the operating system is outdated, then the software in it may also need to be upgraded. That is to say, criminals can fullyexploiting software vulnerabilitiesand control remote systems.
In some cases, publicly visible USB ports and other interfaces in public places may give some malicious users an opportunity to infect machines with malicious software through portable devices. Since there may not be security software installed, and there is a lack of necessary authentication between peripheral devices and the operating system, the possibility of infection is very high. Up to now,20 known types of malicious software targeting ATMs have been discovered.
ATMs are directly connected to cash storage safes. Through infected computers, criminals can easily access the interface between the computer and the safe and issue commands to dispense cash without using the stolen customer's card information.
The traffic between ATM computers and transaction processing servers is usually not encrypted, allowing hackers to easily intercept transmission data from the customer to the bank server. Worse still, it is widely known that ATMs are a mess in terms of firewall protection strategies, making them more susceptible to network attacks.
Other issues worth noting include misconfiguration of application control software, lack of hard drive encryption, and almost no protection mechanisms for user access to the Windows interface and introducing other hardware devices into the ATM.
Types of ATM attacks and fraud
Attacking the bank server is just one of the many methods that criminals use to obtain account holder card information and their hard-earned money. Some of these methods are very clever and tactical, while others are more destructive and dangerous. In short, all you need to know is that criminals will stop at nothing to carry out their criminal activities.
We highlight the types of ATM attacks based on classification: terminal tampering, physical attack, logical attack, and social engineering.
In this article, we will delve into the first two types of attacks.
terminal tampering
Most ATM fraud activities involve physical manipulation of the machine components or introducing devices to make the scheme work.
Bank card fraud (skimming). Usually, the card reader (skimmer) and keyboard are overlaid orpinhole camerain series on the card slot and keyboard. The closer to the machine, the more effective it is (and the less likely to raise suspicion).
The purpose of the second card reader is to copy data from the card's magnetic strip and PIN, so that criminals can counterfeit cards.

Of course, in addition to this, there are many other methods that can be used to secretly capture card and PIN data. For example, it is possible to tap into the ATM network cable'sskimming devicewhich can intercept data in transit.
criminals can purchase second-hand ATMs (at a low priceto create a fake cash withdrawal point. Of course, these ATMs will not dispense money. To date, this is the most persuasive method, as even the most cautious account holder would not suspect that the entire ATM machine is fake.
Skimming devices can also be used at stores or point-of-sale (POS) terminals. Some skimmers are extremely small, able to be concealed in a hand, so that if someone with malicious intent obtains a payment card, they can swipe it at the POS terminal and quickly run it through the skimmer. This is a paragraphThe video of a former McDonald's employee's fraudulent card usage.
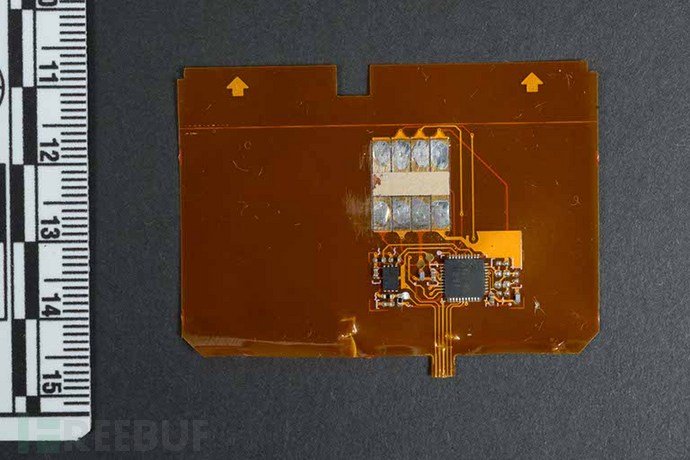
Shimming. People can call the shim an upgraded form of skimming. Although it still targets the card, its focus is on recording or stealing sensitive data from its embedded chip.
A device as thin as a piece of paper is inserted into the card slot of the ATM, located between the card and the ATM's chip reader. This way, when the machine's chip reader is reading, the shimmer will record data from the card chip. Unlike early skimming devices, if it can be perfectly inserted, the shimmer is almost invisible and difficult to detect. However, a sign that a shim device has been installed is that the card slot feels very tight when inserting a bank card. Therefore, if you encounter this situation, it is advisable to be more cautious.
Data stolen from chip cards (also known as EMV cards) can be converted into magnetic strip data, which can then be used to create counterfeit versions of traditional magnetic strip cards.
If you remember, the issuer once said that compared to traditional bank cards,EMV cards provide better anti-fraud protection.
With more and more users and merchants preferring chip cards, whether it is for convenience or industry compliance, it can be predicted that criminals will eventually find a way to bypass chip security and read the data from it.
Card trapping. Although it has not been widely reported like other ATM attack schemes, unfortunately, card trapping attacks still exist. Just recently,A 17-year-old girl lost all her life's savings this way.
Card trapping is a method where the criminals place a small clip in the card insertion slot of the ATM, waiting for the user to insert the card and complete the transaction, at which point the card is held by the clip and cannot be removed. At this time, the card owner may think that the card has been 'eaten' by the ATM and leave, thinking that the ATM has malfunctioned. When the user uses the card, someone will watch the entered password, and after the card owner leaves, the骗子 will empty the money on the card within a few minutes.

Another known card trap is called spring trap.
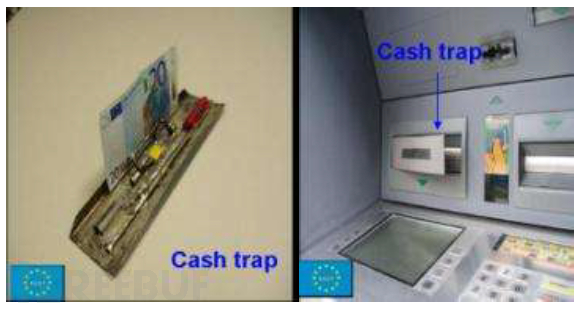
Cash trapping. A tool - a tool similar to a claw, a huge fork-like device, keeps the cash slot open after the ATM withdrawal, thus allowing the extraction of part or all of the target cash.
The Cash trapping method usually involves placing a fake ATM in front of the real one.
Physical attack
If they cannot carry out the robbery with clever means, then the criminals may resort to more simple and粗暴的方式. For exampleUsing solid or gas explosives, usingChain nooseUproot the machine and drag it away, ramming attacks, usingExcavatorDigging out the wall-mounted ATM from the building. Hammers, crowbars, and hammers have also worked wonders for them.
Related video:https://youtu.be/VTe0cdxdSEo
According to the European Association for Security Transactions (EAST), in Europe, the overall physical attacks on ATMs areContinuously increasing. From 2017 to 2018, total losses increased by 16% (from $34.6 million to $40.2 million), and reported incidents increased by 27% (from 3,584 to 4,549). Most of the losses were due to explosions or gas attacks, followed by robberies and ramming attacks.
“The success rate of solid explosive attacks is particularly concerning,” said EAST Executive Director Lachlan Gunn in the report. “These attacks are continuing to spread geographically, with the first reports of these attacks in early 2019.”
The ATM Security Task Force (ATMSWG) has issued a document on physical attacks against ATMsBest Practices [PDF]Financial institutions, banks, and ATM merchants can refer to and use their plans to strengthen the physical security of their machines. Similarly, the ATM Industry Association (ATMIA) also has a document on howConvenient guide to preventing ATM gas and explosive attacks [PDF].
It is evident that financial institutions and ATM providers still have a long way to go to fully address fraud and theft issues, and they have also been searching for and applying methods to strengthen security measures. Of course, ATM users should not let their guard down either.
By reading and following the following tips, try to minimize the possibility of facing tampered ATMs or other lurking dangers:
Before visiting the ATM
Choose an ATM that looks relatively safe. It should have good lighting, be visible to passersby, and have a CCTV camera aimed at it. Ideally, it is best to go to an indoor ATM that can be found in bank branches, shopping malls, restaurants, convenience stores, and so on. Try to avoid using machines that are neglected or damaged.
If you find yourself in an area you are not familiar with, try to use an ATM that meets most of the physical requirements we mentioned.
It is best to have someone accompany you when withdrawing money from an ATM, especially outside of normal banking hours. If something goes wrong with the transaction, your friend or relative may be able to help. Moreover, their presence can also deter robbers and/or strangers.
Inspect the ATM. Look for any devices that may be sticking out from behind it or any peripheral devices. Look for fake fronts (card and money slots, keyboard, or even worse, the entire surface of the machine), small holes that a camera might observe, cracks, mismatched key colors, and so on. Report any of these signs to the bank and look for another ATM to use.
Finally, identify anyone you think is wandering around near you or exhibiting suspicious behavior. Do not confront them directly. Instead, if their actions are sufficiently suspicious, report them to the police immediately.
Use ATM
When using the ATM, put away anything that might distract your attention, such as your phone and Nintendo game console. These might make you relax your vigilance and awareness of your surroundings, giving criminals the opportunity to take advantage of these environments.
Try to pull the card reader and the ATM to ensure there are no additional devices attached.
When entering your password, whether you are alone or not, it is best to cover the keyboard with your hand. If there is someone queuing behind you and they are very close, you should remind them to move back in time to maintain a safe distance.
Remember to print a copy of your ATM receipt and keep it for safety. This way, you can use it as a reference and compare it with your bank statement.
After completing the withdrawal
Quickly and carefully put your card, cash, and receipt away.
If the ATM does not return your card, please stay beside the machine and call the bank's 24/7 support line to freeze/lose your card, so that the criminals cannot use it. If there are people queuing behind you, you can tell them that your card is stuck, and they will not be able to use this machine until you take it out.
If the ATM does not dispense money, please record the exact date, time, and location of the ATM, and call the bank's 24/7 support line. You can also take a few photos with your phone and then send a copy of the photos to yourself (via SMS or email), so you have a digital record and proof.
At the same time, please call your issuing institution or bank to apply for a claim and explain the situation. If you are using an ATM inside a bank building, this issue will be resolved faster.
If this happens at a convenience store, please inform the staff immediately. This way, they can also prevent other store shoppers from using the faulty machine.
Regularly check your bank statement to understand your withdrawal and/or card usage. If you find any fraudulent activity, please report it to your issuing bank immediately.
Consider other payment methods
People do not always have to continue to withdraw cash from ATMs. If consumers can pay for goods without using ATM cash, they should consider these options.
Many people claim that using your card or the contactless or tap payment function of your smartphone is an effective way to combat account fraud (and ATM fraud).
For the second part of this series, we will discuss the logic and social engineering attacks used by criminals against ATMs and their users. Before that, please be aware and maintain the safety of your card usage!
*Reference source:malwarebytesFB editor secist compiled, please indicate the source as FreeBuf.COM when转载
Knowledge Point 5: Bypass CDN through Space Engine & Use Tools for Global CDN Bypass Scanning
03 The core value of zero-knowledge proof: eliminating the need for a trusted third party
Improving Threat Detection Capabilities with the MITRE ATT&CK Security Knowledge Framework
Anti-Anti-Virus Basics - Basic Knowledge
The democratisation of knowledge in cybersecurity
评论已关闭