0x00 Preface
The annual offensive and defensive exercise is about to start, and everyone has also begun to prepare for the network defense. As everyone knows, the offensive and defensive exercise tests not only the 'strategic missiles' of the attack team but also the 'Iron Dome' of the defense side. The value of the blue team often needs to be verified through attacks. In order to let everyone not be a 'peaceful bird' during the network defense, this article will refer to the ATT&CK model and discuss the three modules of investigation, resource development, and initial access, draw and analyze attack methods, and identify attack methods through fingerprints, so as to find that 'TA' in the massive alarms.
0x01 Investigation
Analysis of attack methods
During the investigation phase, attackers usually actively and passively discover and collect target subdomains, fingerprints, supply chain information, etc. The active collection initiated is definitely recorded by traffic devices, and the passively collected assets also need to be authenticated for the effectiveness of the collected assets. We can discover this behavior through the following dimensions:
1. Dimension of time

As a tool for collecting assets, the biggest characteristic is that it can initiate a large number of requests in a short period of time and point to different domains. It can summarize and analyze statistical data through the way of Excel table summary for device alarms (referring to devices such as situation awareness, WAF, load balancing, etc. that can record normal traffic).
Analysis indicators
1.1 Large-scale visits by the same IP to the same site in a short period of time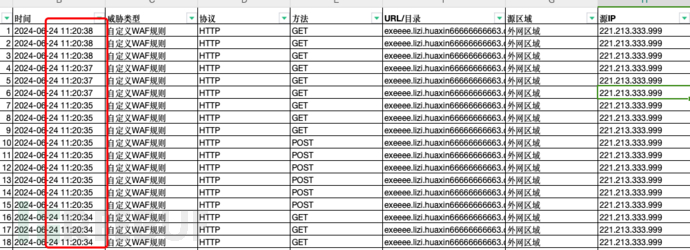
1.2 Large-scale visits by the same IP to different sites in a short period of time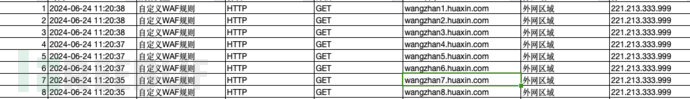
2. Dimension of fingerprint
It is easy to detect when the same IP makes a large number of requests. We know it, and the red team also knows it, so some red teams have rich IP proxy pools. All the probes are initiated and collected by different IPs to avoid detection by the blue team. In this case, we can discover IPs that may exist attack behaviors through threat intelligence.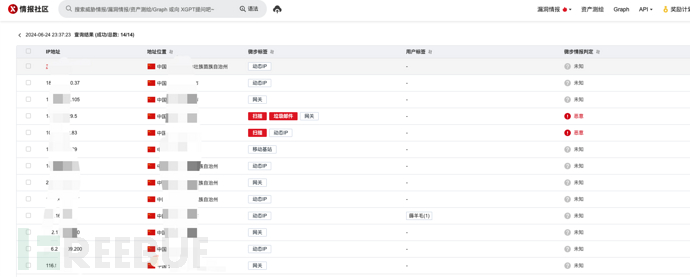
3. Dimension of scenario
Certainly, someone will ask, we all know these two. Some IPs are in the new pool and have not been marked, they are still pure. How do we discover the attacker in this case?
Overall scenario correlation
What is abnormal traffic? It is conflicting and unrelated to the daily scenario. Many of our websites contain a large number of framework files such as JS and CSS. When we normally load the browser, it is never just a single page that is loaded.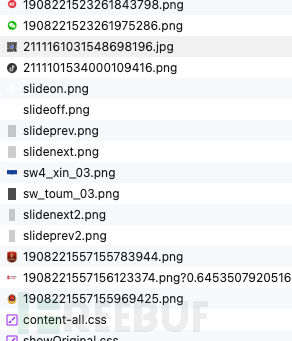
Comprehensive Guide to Linux Two-factor Identity Authentication: ssh + console + graphical interface
facebook hire through hacker cup(Facebook Hacker Cup)
How does GARTNER define mobile target defense (dynamic target defense, MTD)?
A brief discussion on the high availability design of service interfaces
1. Challenges faced by offensive and defensive exercises
Analysis of the reflective class loading of high-version JDK in practical network defense and attack
Analysis of factor decomposition attack methods when the sizes of RSA factors are close
A brief discussion on security detection in the context of security attack and defense scenarios
评论已关闭