Author: Ma Yue
1 Background
This is a quiet and peaceful afternoon without bugs.
As a beginner, it is very necessary to consolidate the basics at all times. Such a good opportunity, let me learn how to use mybatis.


This is different from what I saw. Let me see how it is written in the project.
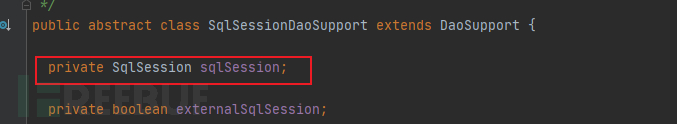
All the Daos in our project inherit from BaseDao, and BaseDao inherits from SqlSessionDaoSupport. Every time we execute sql, we directly return this sqlSession and then execute the sql. Isn't this an instance variable? This is different from what you said. With such doubts, I began my exploration.
2 Exploration Journey
1) We all know that when using mybatis, sqlSession comes from sqlSessionFactory, and sqlSessionFactory can be created by sqlSessionFactoryBuilder or initialized by spring, and it is obvious that the latter method is adopted in the project.

2) So we have already obtained the sqlSessionFactory, how should we further explore the source of sqlSession? I think we can explore it through the already implemented dao in the project. Let's take a random dao as an example.
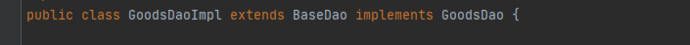
It inherits from BaseDao.
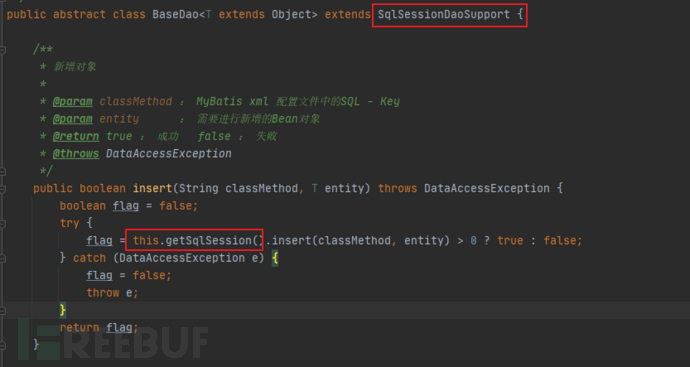
And BaseDao inherits from SqlSessionDaoSupport, and calls the getSqlSession method in BaseDao, which is actually the getSqlSession method of SqlSessionDaoSupport.

And the getSqlSession method of SqlSessionDaoSupport directly returns its member variables, which is consistent with my suspected point so far, that is, the current writing is inconsistent with the description on the MyBatis official website.
3) After reading the SqlSessionDaoSupport class repeatedly, I finally found the clues. Careful friends should have discovered it long ago, in the comments of the figure above, 'Users should use this method to obtain a SqlSession to execute sql statements, this SqlSession is managed by Spring, and users should not commit, rollback, or close it. Because these have been automatically executed.'
At the same time, this method will return a thread-safe SqlSession.
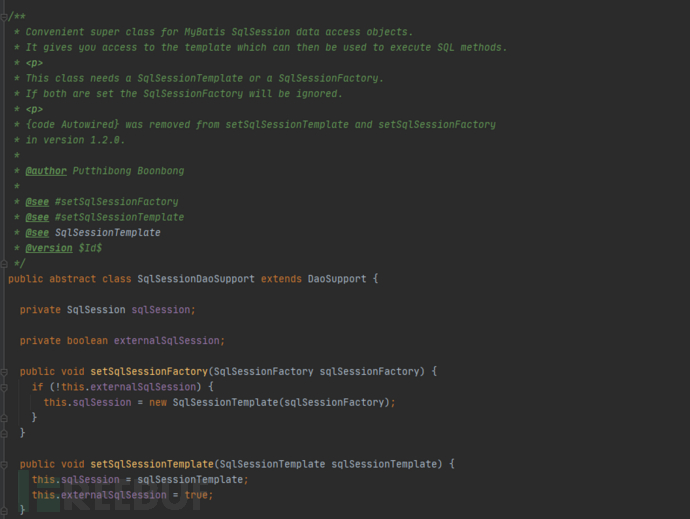
Then where does this SqlSession come from? From the above figure, it can be seen that there are two assignment methods: one is to pass a SqlSessionFactory to generate SqlSessionTemplate, and SqlSessionTemplate is sqlSession. The other is to pass a SqlSessionTemplate directly as SqlSession. According to the comments of this class, if both SqlSessionFactory and SqlSessionTemplate are defined, the SqlSessionFactory method will be invalid. Up to now, my above doubts have been solved, that is to say, this SqlSession is not a MyBatis initial SqlSession, but a SqlSessionTemplate implemented by Spring.
4) But, I have born a new question, how does SqlSessionTemplate achieve thread safety?
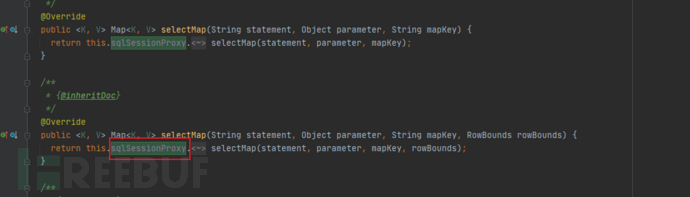
So I entered the method execution of SqlSessionTemplate, and found that the actual execution statements are all this proxy class sqlSessionProxy.
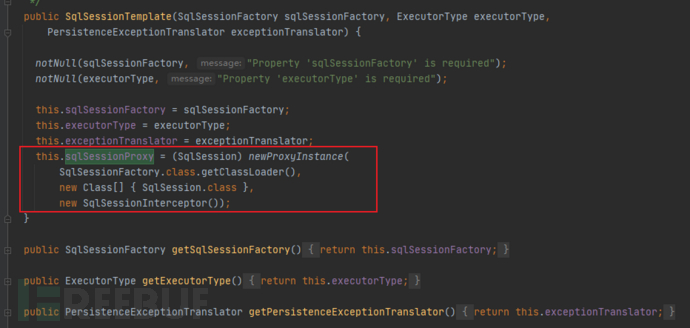
And the proxy's work content is in the handler SqlSessionInterceptor.
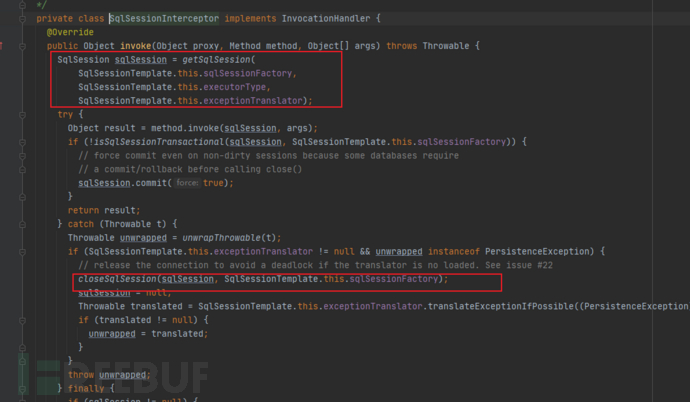
Entering it, we finally discovered its acquisition and closing operations.
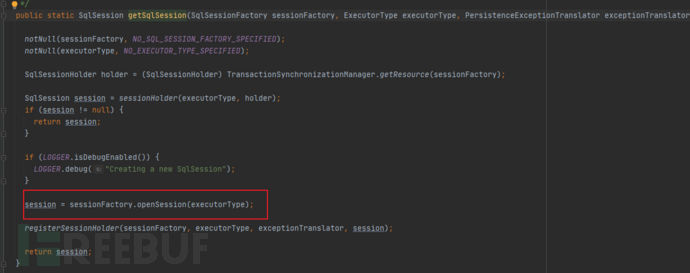

That is to say, each time it is executed, the proxy will call the sessionFactory's openSession method to obtain a new session.
3 Summary
Finally, finally, MyBatis, Spring, the project, and my doubts have been unified, what a peaceful and harmonious afternoon without bugs.
评论已关闭