A few days ago, there was a big misunderstanding on the Internet. After the Windows update, many Win10 computers found that the boot screen was blank, and it was later found that it was caused by Fire绒 mistakenly deleting explorer.exe, which led to the system being frozen. After that, Fire绒 also released an official statement.

Interestingly, the bilibili author epcdiy later released a so-called analysis video, in which it was described that after updating the patch KB5034203 and KB5034763 for Win10 22H2, the timestamp of explorer.exe displayed as 2085 and a series of operations against the 360 series antivirus software appeared in reverse. These features are similar to AVkiller, which caused Fire绒 to mistakenly kill it.
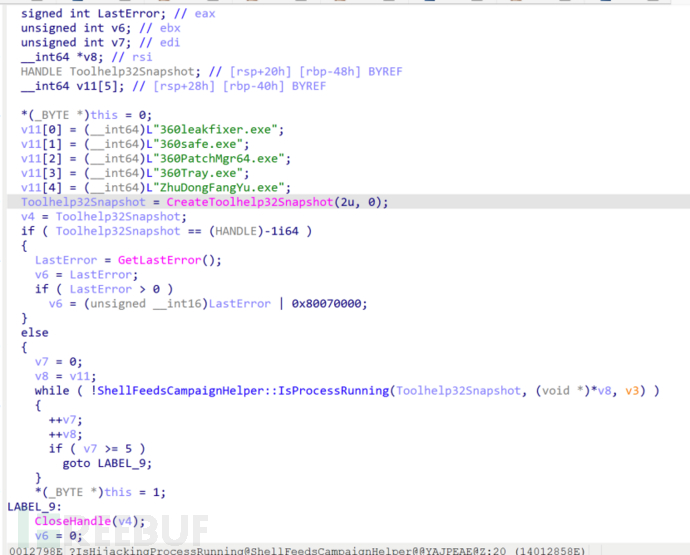
Firstly, let's analyze the code for explorer that is specific to 360. The function of this code is to check if a series of specific processes are running. The names of these processes are stored in an array named v11, including "360leakfixer.exe", "360safe.exe", "360PatchMgr64.exe", "360Tray.exe", and "ZhuDongFangYu.exe", which are all part of the 360 product series. Firstly, the code creates a Toolhelp32Snapshot, which is a system snapshot containing information about all processes in the system. Then, it traverses each process name in the v11 array and checks if each process is running using the ShellFeedsCampaignHelper::IsProcessRunning function. If any running process is found, it sets *(_BYTE) this to 1 and exits the loop. If no running process is found, it keeps (_BYTE *)this as 0. Finally, regardless of whether a running process is found, it will close the Toolhelp32Snapshot handle.
In short, this code takes a snapshot of the system, then checks for the existence of processes from the 360 series products, and returns true if they exist.
From the perspective of malicious code analysis, the static suspicious point of this code is the presence of the 360 suite string, and the function name contains Hijacking, which meansinjection, hijacking,These are high-frequency words used in writing trojans, and since their program timestamp is not within the normal range, they are easily noticed by antivirus software. Secondly, from a behavioral perspective, the execution flow of this code includes taking process snapshots, checking if the 360 suite is alive. These behavior characteristics are easily mistaken for a trojan when placed on a statically suspicious program. The AVkiller (strongly kill antivirus) series of trojans mentioned in the Huorong official documents have this behavior, and it is also an indispensable step for other trojans to identify whether there is an antivirus process in the system during the process of anti-removal, and then carry out different subsequent infection and login operations. All of this led to Huorong's antivirus killingexplorer.exe provided rationality.
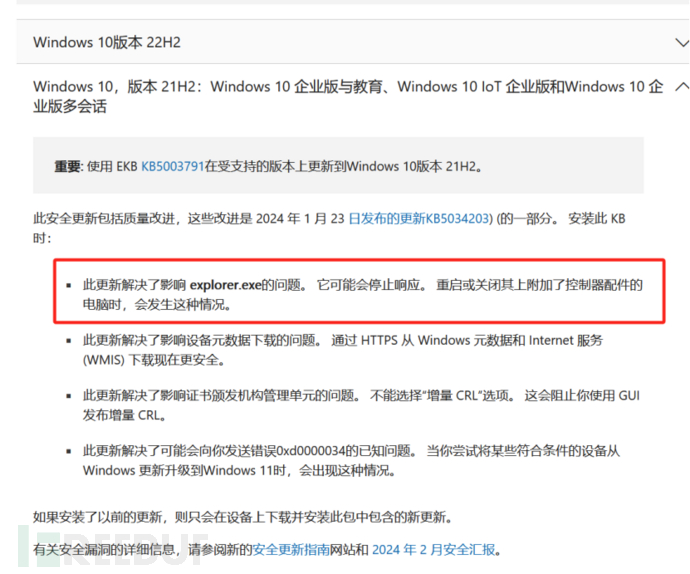
Then we continue with the analysis, trying to figure out why explorer needs to identify the 360 process. I found the description of Microsoft's update: “Resolved an issue affecting explorer.exeThe issue. It may stop responding. (https://prod.support.services.microsoft.com/zh-cn/topic/2024-%E5%B9%B4-2-%E6%9C%88-13-%E6%97%A5-kb5034763-os-%E5%86%85%E9%83%A8%E7%89%88%E6%9C%AC-19044-4046-%E5%92%8C-19045-4046-f1c993e4-32b3-4cc8-947a-69e70ae124d5) Pay attention to this point later in the text.
After that, go back to IDA, and the function name of the 360 process detection function is shellFeedsCampaignHelper::IsHijackingProcessRunning. We perform a global search to see who called this function.
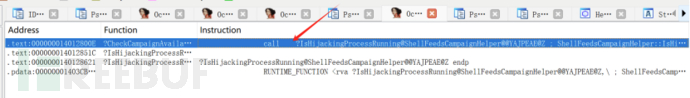
Clicking into a new function ShellFeedsCampaignHelper::CheckCampaignAvailability, we start analyzing it from the beginning.
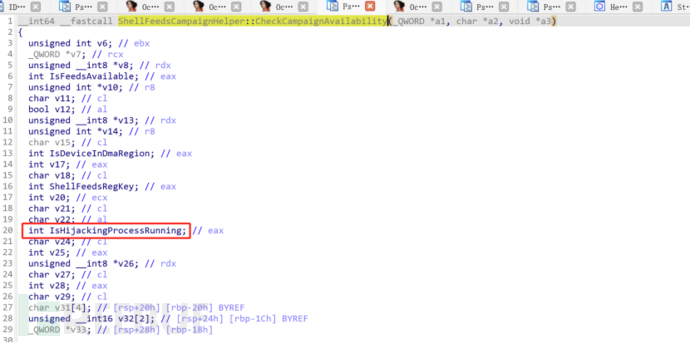
We only analyze the main functions:
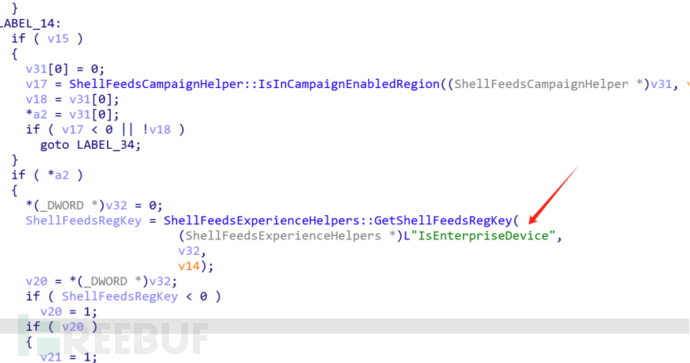
Here, the function ShellFeedsExperienceHelpers::GetShellFeedsRegKey is called to obtain the registry key value ShellFeedsTaskbarViewMode. If this key value is greater than or equal to 0 and equal to 2, it sets v12 to 1; otherwise, it jumps to the LABEL_34 label.
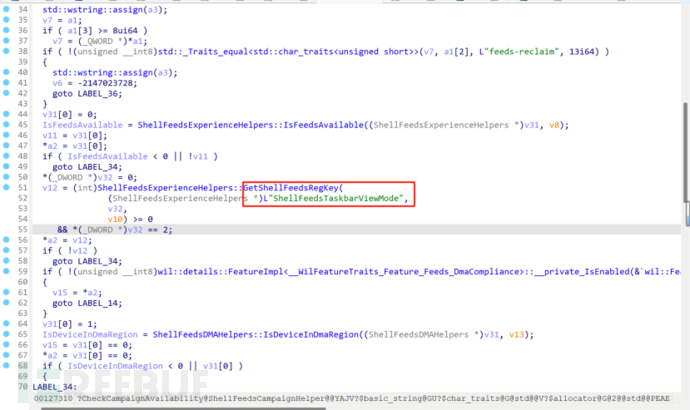
We search for the function of the ShellFeedsTaskbarViewMode key value on Baidu and find that this key value represents the Windows 'Information and Features' function, and it is turned off when the key value is 2.
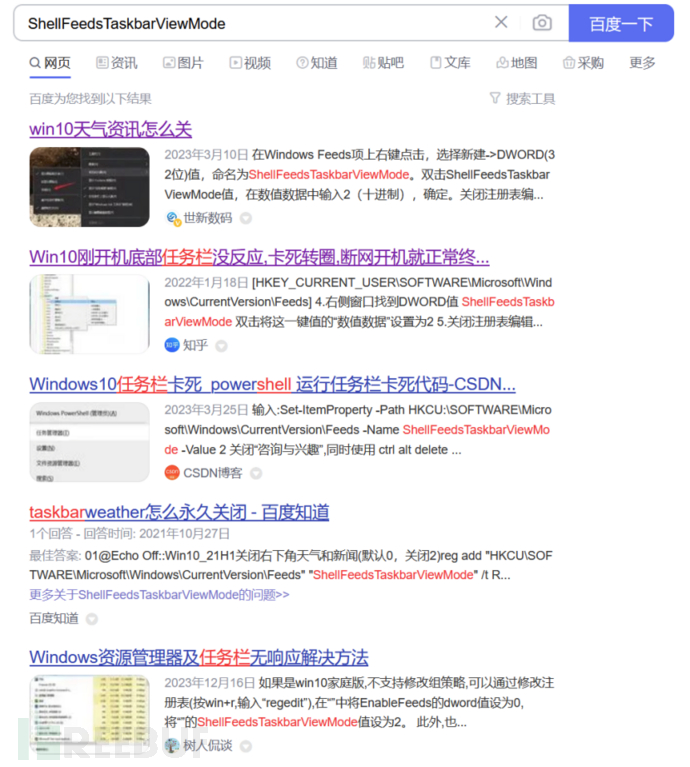
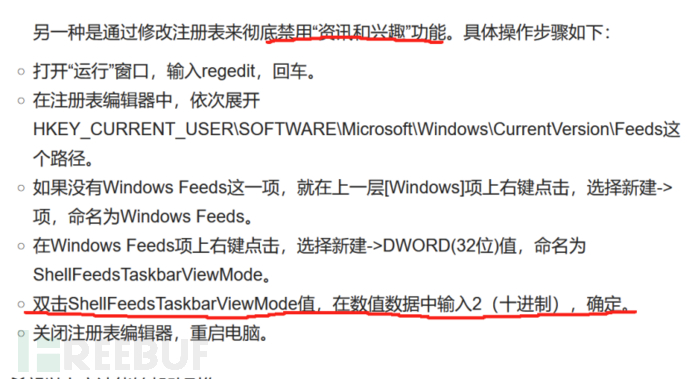
From this, we can roughly guess that the function is to check whether the 'Information and Features (feeds)' function is turned off. If the 'Information and Features' function is turned off, the key value is 2, the v12 variable is 1, and then enter an if judgment to check if v12 is 0. If it is 0 (the function is enabled), then enter the LABEL_34 function.
Let's continue to look at the functions that appear below, such as IsDeviceInDmaRegion, IsInCampaignEnabledRegion, IsHijackingProcessRunning, CheckAvailability_UserUnpinDate, and CheckAvailability_LastCampaignRunDate. We will analyze them one by one next.
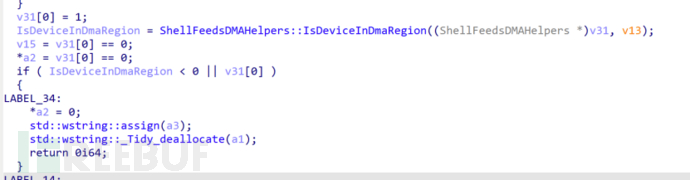
The IsDeviceInDmaRegion function: checks the registry key value IsDeviceInDmaRegion, which cannot be found on Baidu. I asked ChatGPT, and it said that this registry key value is used to determine whether the device is located in the DMA (Direct Memory Access) region. If the device is in the DMA region, it may be able to use DMA for more efficient data transmission. This information may be important for system performance tuning and device management. In layman's terms, it is to check whether this device is a key device for data transmission (as I understand it). If it is, it will jump to the LABEL_34 label.
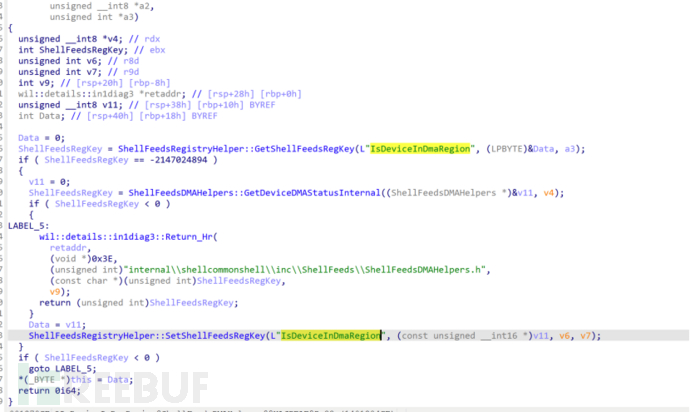

CheckAvailability_UserUnpinDate and CheckAvailability_LastCampaignRunDate functions are used to detect the local timestamp of the last run of the feeds function, which will not be elaborated here.
IsInCampaignEnabledRegio function: This is the detection of whether the region is China, as mentioned in the video. However, after this function, it also judges whether Windows is an enterprise version. If it is, it will jump to the LABEL_34 tag.
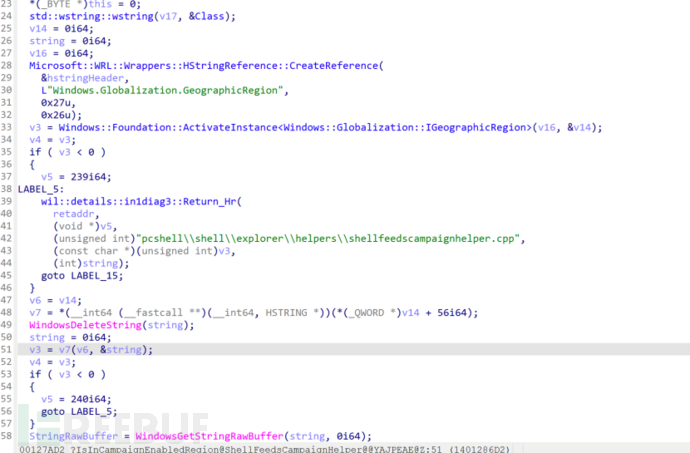
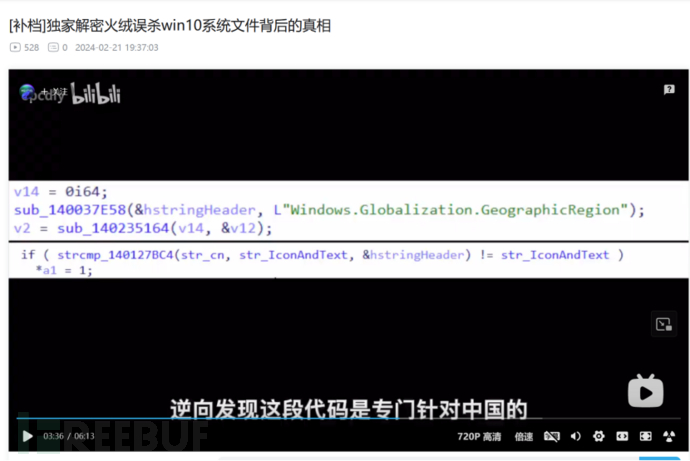
IsHijackingProcessRunning function: This is the popular 360 process detection code, and if there is a 360 process, it will jump to the LABEL_34 tag. The analysis has been done before, so no need to elaborate again. One worth thinking about is why Microsoft named this code Hijacking?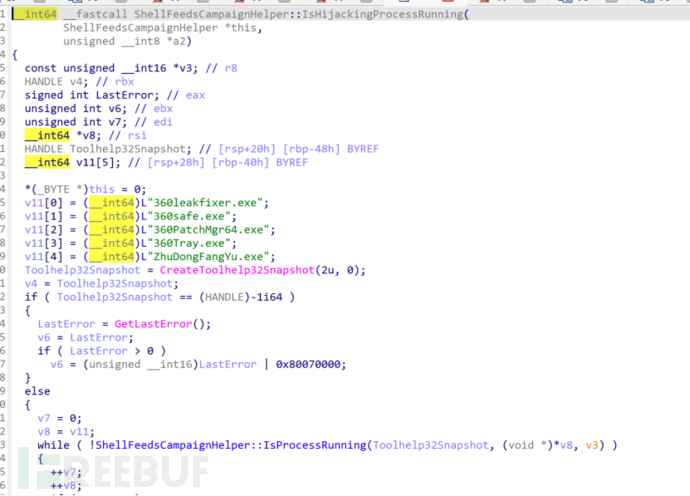
As to why the 360 family of processes is named Hijacking, I will make a simple speculation here. Those who have experienced malware evading detection know that anti-malware software usually uses some ring3 layer hook桩桩 operations to monitor processes, and it is inevitable to use Hijacking (injection, hijacking) in the process of monitoring processes. Here I quote the screenshot of the related answer by the Zhihu big shot Han Puyu, where it can be seen that explorer.exe in the 360 environment is indeed injected by 360 and also loads 360 dll files.
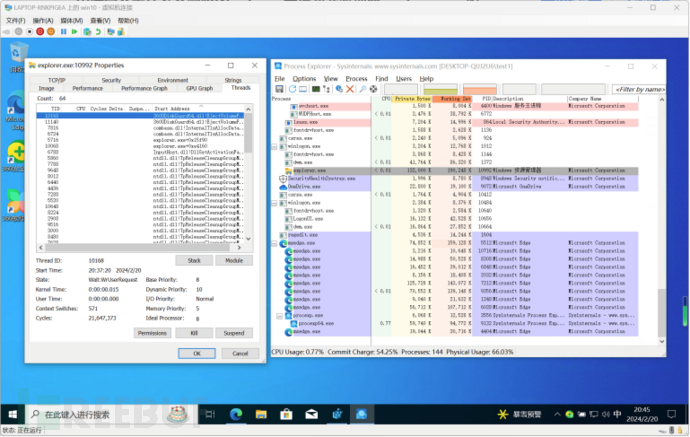
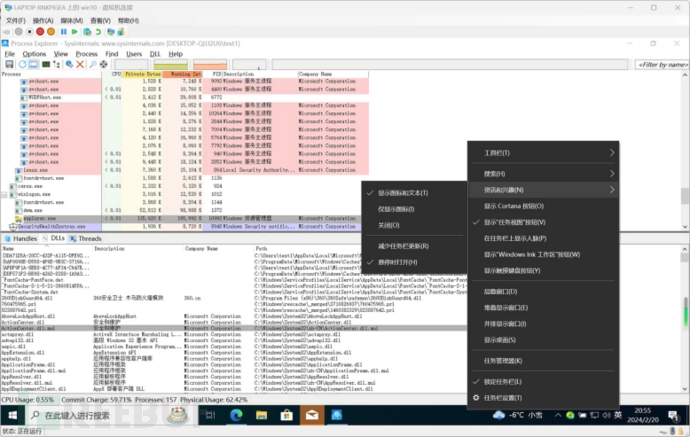
So there is a possibility that the system monitoring of 360 conflicts with Windows' own 'Information and Features (feeds)', and Microsoft needs to check whether the system has the 360 family of processes to later disable the 'Information and Features (feeds)' to maintain system stability.
Finally, after many judgments, we come to this LABEL_34 tag, which is reached when feeds function exists and is enabled, DMA area machine, enterprise version of Windows in China, and any condition of installing any 360 product series is met. LABEL_34 is a return function that returns a 0 value to the main function, that is, ShellFeedsCampaign is not available, which roughly means that the feeds function is disabled.
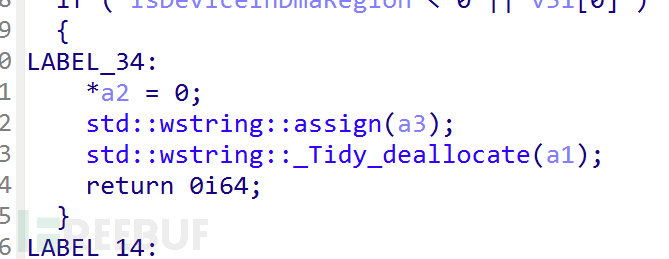
So Microsoft's intention may have been to ensure system smoothness by adding this code to explorer, which checks whether the 360 family of processes exist in the system. If they do, the feeds function is closed because the feeds function of Windows in the 360 environment conflicts with the injection and桩桩 behavior of 360 security monitoring, leading to system crashes. Moreover, because this code uses high similarity strings such as Hijacking and 360 process names, and sensitive behaviors such as taking snapshots and detecting process survival, along with abnormal timestamps, are listed as high-risk files by FireEye, leading to false positives.
Reference article: https://www.zhihu.com/question/642107690
评论已关闭