Data shows that global corporate organizations have invested more than one trillion US dollars annually in data security protection, but the situation of data security threats remains severe. The reason is that when enterprises allocate more resources to the construction of data security capabilities, they neglect the scientificity and rationality of these tasks themselves. Therefore, before implementing data security protection work, enterprises need to first formulate a positive and effective data security protection strategy, and guide the construction of organizational data security protection capabilities according to the requirements of the strategy, which is crucial for ensuring the effectiveness of data security protection.
To better protect investments in data security, corporate organizations should refer to the following 10 key elements and formulate a successful and efficient data security protection strategy in advance.

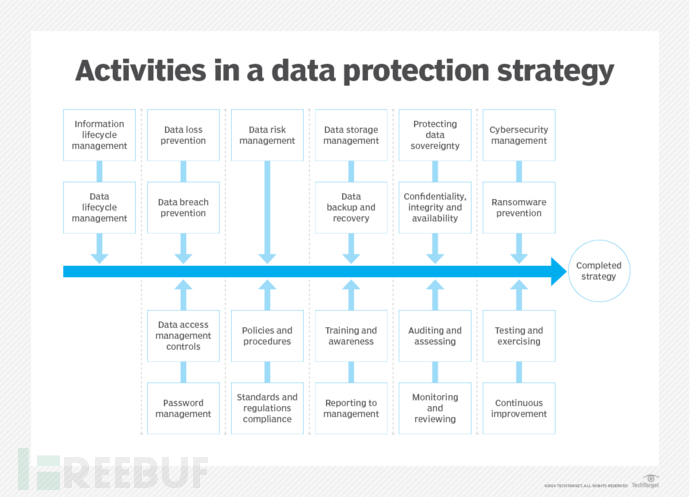
Figure: Key Attributes and Core Elements of Data Security Protection Strategy
1、Cover the security of the entire data lifecycle
The security of the data lifecycle includes the process from the creation, storage, archiving to destruction of data, which is a basic component of modern corporate organizational data security protection strategies, and should be reviewed regularly to ensure that ongoing and planned data protection activities are synchronized with the lifecycle. With the increasing amount of data generated by organizations, data lifecycle management is becoming more and more important.
2、Carry out data risk management
It is crucial to effectively identify and assess the risk situation of data when formulating data protection strategies, because this strategy can maximize the possibility of data security incidents and mitigate the damage to related data security incidents. Therefore, organizations should regularly conduct risk assessments of the data and information threat environment to ensure that the most suitable preventive, detection, response, and mitigation technologies are adopted.
3、Do well in data backup and recovery
A successful data security protection strategy must include planning related to data storage management, including all activities related to how to safely move production data into data storage repositories, whether it is in a local network, cloud, or third-party service provider environment. Once data is created, it should first be backed up to a safe and protected place for use. When data is needed, the recovery process will release it from secure storage or archives to verify its usability. These activities are also key components of business continuity and disaster recovery (BCDR) plans, which can help organizations recover and restore operations after destructive events.
4、Clarify and protect the ownership of data
In the digital age, data has become a new type of strategic resource, and clarifying the ownership of data assets is the basis for corporate organizations to collect, possess, use, and develop data resources in the future. Therefore, organizations need to formulate a data ownership protection policy to ensure that it is not damaged by internal or external attacks. The confidentiality, integrity, and availability of data are the core needs of data protection and should also become the basic attributes of organizational data security protection strategies.
5、Strengthen the protection against ransomware attacks
Research data shows that ransomware attacks have become the number one threat to organizational data security. This type of attack not only blocks users' access to data but also causes more harm by stealing and publicly disclosing data. Therefore, deploying a powerful anti-ransomware system is a key component of organizational data security protection activities, which can prevent and stop its attacks and destruction on critical data assets and application systems.
6、Reliable data access management and control
The premise of realizing data security is to safely access and use data. Whether the data access management and control measures are reliable is an important review content during IT system audits, and it is also one of the most important components of data security protection strategies. It should be noted that although organizations are increasingly interested in advanced authentication technologies, password technology is still widely used to prevent unauthorized data access. Moreover, various password management tools have also been continuously improved and perfected.
7、Compliance with standards and regulatory requirements
Ensuring compliance with security and regulatory requirements is indispensable in the organization's data security protection strategy and should be reviewed as part of the audit process. The organization's data security protection policy can be an independent plan or embedded in a larger network security management strategy. A successful data security protection strategy must comply with and adhere to the requirements of existing regulatory regulations, laws, and related standards, including the EU's GDPR, as well as China's
8、Strengthening the cultivation of employees' awareness of data security protection
A successful data security protection strategy must go beyond network security technology itself. It should educate all employees about how their data is protected and the responsibilities they bear in ensuring data security. Employees responsible for data protection must receive adequate training to effectively perform their duties. Before an organization launches a data protection strategy and plan, senior management must understand and approve the plan, and regularly report on the implementation of the strategy to ensure that senior management fully understands that the organization's data and information are always effectively managed and protected.
9、Regular audits and evaluations
To ensure that the organization's data security protection strategy and all related data security management plans can be properly implemented, it is necessary to regularly check, evaluate, and audit their application, which is particularly important. Documentation of all policies, procedures, activities, and events is indispensable. A well-organized data management plan should require continuous monitoring of all aspects of data creation, transmission, storage, archiving, and destruction. By analyzing logs and other repositories, auditors can provide important evidence about data protection and management controls.
10、Continuous improvement through testing and exercises
Regularly testing and exercising data protection plan activities, such as data backup and recovery, data access management, and network security protection activities, can ensure the normal operation of these important plans and ensure that employees executing these plans understand their roles and responsibilities. These activities are also part of the Business Continuity and Disaster Recovery (BCDR) plan and provide important evidence for IT auditors. Organizations must regularly review and continuously improve data protection and related activities to comply with existing and new regulations, legislation, and good practices, and to generate the highest level of confidence for users, ensuring that their sensitive data and information are protected.
评论已关闭