4XX problems
In the HTTP protocol, it stipulates various response status codes, which indicate the result of message processing on the server side and guide the behavior of the client side, such as 101 representing that the message is being processed and the communication protocol is switching, 200 representing that the message is processed successfully, 301 representing that the accessed resource has changed its location and notifies the client to access the new location, and 400 representing that the request message sent by the client is incorrect, 502 representing that there is a gateway problem on the server side, and it is impossible to access the target server.
In the daily use of web services, we may often encounter 4XX, 5XX problems, at this time, the error page will be displayed on the web page, and the possible causes of the error will be given.
Today, let's mainly understand the more important 403 issue among the 4XX problems.
The meaning of 403
In the HTTP protocol, status codes 403 ForbiddenIt represents client-side errors, indicating that the server has the ability to handle the request but refuses to authorize access. Due to some content in the request information triggering the security policy, the server refuses to process the request. The server can flexibly set the access permissions of resources through the configuration of security policies, the simplest of which is to allow logged-in users to access and prohibit visitors from accessing.
During the penetration testing process, it is often encountered that due to lack of permission to access pages or interfaces, the test cannot continue.
This analysis is conducted from the perspective of single-node and multi-node systems, that is, a system composed of a single server or multiple servers, to discuss the security control of WEB systems.
Single-node scenario
In the single-node scenario, it is generally used for the server to handle access control, configure security policies on the server, or have the web program perform unified security control on requests. When accessing sensitive resources, the server's security policy or special handling by the web program denies user access.
client ----> webserver
GET / ---> /index.html 200
GET /admin---> /admin --> Security rule --> 403
Multi-node scenario
In the multi-node scenario, it is generally used for the proxy server to handle access control, and configure security policies on the proxy server. When accessing sensitive resources, the server's security policy prevents the request from reaching the backend server and denies user access.
It is common in the division of internal and external networks, where external network users want to access web services, they need to go through the proxy server, which is subject to security policy restrictions. When users can directly access the backend server, they are not subject to the security policy restrictions on the proxy server.
client ---> proxy ---> webserver
# Access through the proxy server
GET / ---> Security rule -> Forward -> /index.html 200
GET /admin---> Security rule -> Prohibit access 403
# Direct access
GET / --> /index.html 200
GET /admin --> /admin 200
Taking the online scenario of burpsuite as an example to illustrate the security policy restrictions and the countermeasures.
Online scenario
Single-node scenario
Bypassing the restriction through the request method
Direct access to sensitive interfaces, 401 unauthorized

Bypassing the restriction through the request method
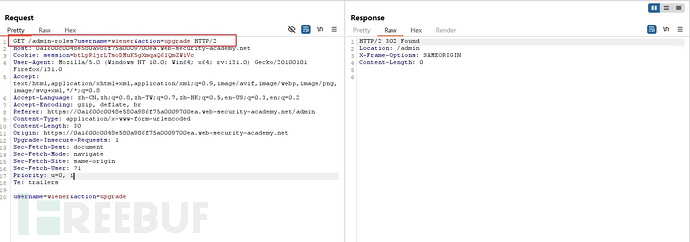
Host header field restriction
https://portswigger.net/web-security/host-header/exploiting/lab-host-header-authentication-bypass
The backend program divides permissions based on the Host field, considering localhost as the local administrator
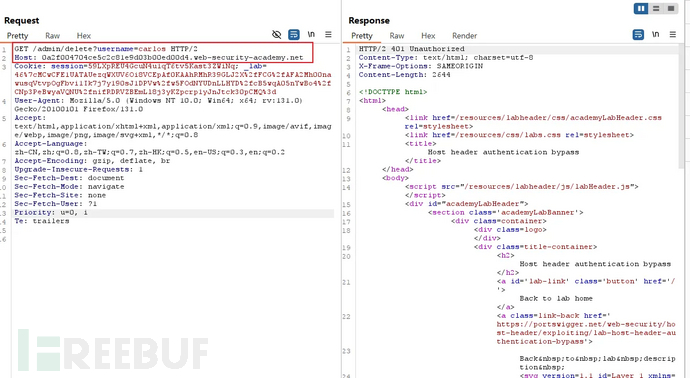
Replacing the content of the Host field in the request to bypass the restriction

Bypassing the Referer restriction
https://portswigger.net/web-security/access-control/lab-referer-based-access-control
Accessing sensitive interfaces, 401 unauthorized
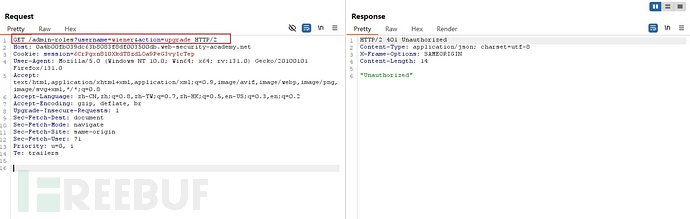
By starting with an administrator operation on sensitive interfaces, it was found that onlyRefererField validation
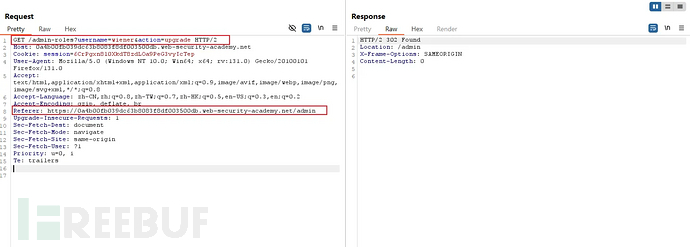
Multi-node scenario:
Bypassing the URI restriction using the X-Original-URL field
Multi-node scenario: the proxy server configuration security policy prohibits access to /admin, but the backend framework supports the X-Original-URL field,
https://portswigger.net/web-security/access-control/lab-url-based-access-control-can-be-circumvented
Direct access to the delete interface, 403 insufficient permissions
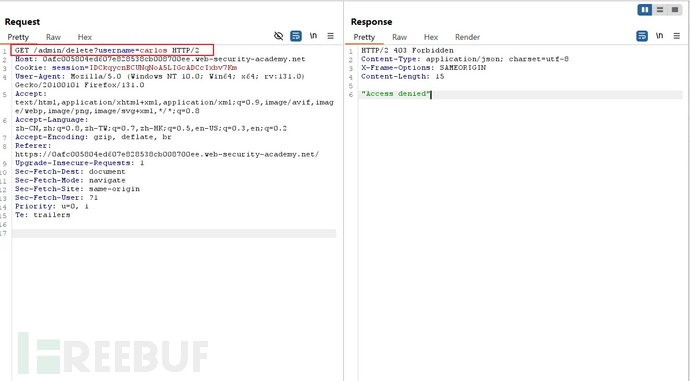
Bypassing the X-Original-URL field
proxy: uri --> /
web: uri --> /admin/delete (Resource Mapping)

Remove the X-Original-URL field, both will map the request URI to:/
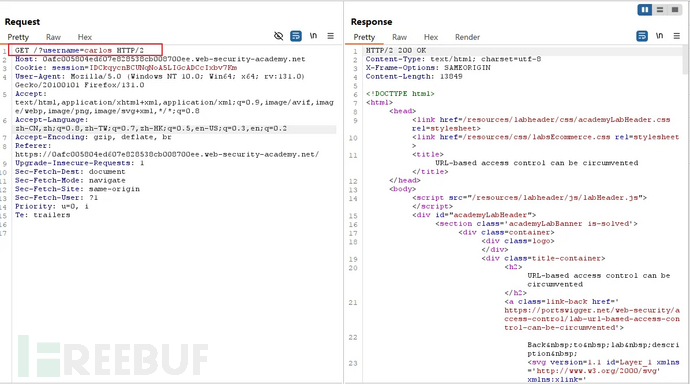
Security strategy analysis
Whether it is a server or a web program, security strategies can be set for access control. Different security strategies are used according to different user request information.
Several starting points can be found from the request information:
Request line, requested URI, request method, protocol, protocol version
Header fields, Host, UA, Reffer, X-Forwarded-For
Request body (common access control strategy of WAF)
From information parsing, matching, to the execution of the final security strategy, there is also involvement in rewriting or processing request information. In this process, improper handling of any link can lead to bypassing the security strategy.
Example of server security strategy
Taking the configuration of an Nginx server as an example:
Access restriction based on request method:
location /admin {
# only POST
if ($request_method !~ ^POST$) {
return 405;
}
}
Access restriction based on request URI:
# Prefix match
location /admin {
return 403;
}
# Exact match
location = /flag/ {
# Configuration...
return 403;
}
Access restriction based on protocol version:
if ($server_protocol ~ "HTTP/1.0") {
return 426;
}
Access restriction based on the header fields Host, UA, and Referer, which are used less commonly on general servers
# Host
location /admin {
if ($host != "localhost") {
return 403;
}
# Referer
location /admin {
if ($http_referer !~* "http://example.com"){
return 403;
}
}
# UA
location /admin {
if ($http_user_agent !~* "Mozilla") {
return 403;
}
}
Access restriction based on IP address
# ip
location /admin {
allow 127.0.0.1/24;
deny all;
}
Path rewriting based on URI (key test)
location /admin {
# rewrite ^/admin/(.*)$ /other/admin/$1 permanent;
rewrite ^/admin/(.*)$ /other/admin/$1 break;
}
Example of program security strategy
Website script programs, also use information in the request to match different security strategies.
if ( request ? rule ){
action->response
}
Taking PHP language as an example, common access control methods
Access control based on request method
if ($_SERVER['REQUEST_METHOD'] !== 'POST') {
// If it is not a POST request, return 405 Method Not Allowed
header('Allow: POST');
header('HTTP/1.1 405 Method Not Allowed');
exit;
}
Access control based on URI
$uri = parse_url($_SERVER['REQUEST_URI'], PHP_URL_PATH);
if ($uri === '/admin') {
// Execute certain operations
header('HTTP/1.1 403 Forbidden');
exit;
}
Access control based on request parameters
if (empty($_GET['api_key']) || $_GET['api_key'] !== 'expected_value') {
header('HTTP/1.1 403 Forbidden');
exit;
}
Access control based on protocol version
if (isset($_SERVER['SERVER_PROTOCOL']) && $_SERVER['SERVER_PROTOCOL'] == 'HTTP/1.1') {
// Allowed HTTP/1.1 operations
} else {
// May return an error or perform a downgrade operation
header('HTTP/1.1 426 Upgrade Required');
// Can also provide an upgrade URL or more information
}
Access control based on request header fields, Host, UA, Referer,
$allowedHosts = ['example.com', 'www.example.com'];
if (!in_array($_SERVER['HTTP_HOST'], $allowedHosts)) {
header('HTTP/1.1 403 Forbidden');
exit('Access denied.');
}
$userAgent = $_SERVER['HTTP_USER_AGENT'];
if (strpos($userAgent, 'UnwantedBot') !== false) {
header('HTTP/1.1 403 Forbidden');
exit;
}
$referer = $_SERVER['HTTP_REFERER'];
if (empty($referer) || parse_url($referer, PHP_URL_HOST) !== 'alloweddomain.com') {
header('HTTP/1.1 403 Forbidden');
exit;
}
Based on IP address
$allowedIPs = ['127.0.0.1'];
if (!in_array($_SERVER['HTTP_REMOTE_ADDR'], $allowedIPs)) {
header('HTTP/1.1 403 Forbidden');
exit;
}
$allowedIPs = ['127.0.0.1'];
if (!in_array($_SERVER['REMOTE_ADDR'], $allowedIPs)) {
header('HTTP/1.1 403 Forbidden');
exit;
}
Common tools
Not limited to the above scenarios, the 403 bypassing technology lies in the request'sModificationTo break through the restrictions, the following are some existing tools.
byp4xx
https://github.com/lobuhi/byp4xx
bypass-403
https://github.com/iamj0ker/bypass-403
Burpsuite_403Bypasser
https://github.com/sting8k/BurpSuite_403Bypasser
403bypasser
https://github.com/yunemse48/403bypasser
In the face of complex web scenarios, various types ofMalformedrequest, but this is actually the server'sMalformedImproper handling of requests leading to the failure of security policies.
The following are some special behaviors of servers or web frameworks in request parsing, which implement 403 bypassing.
Vulnerability scenario
Single node
nginx misconfiguration leading to directory traversal when rewriting uri
location /files {
alias /home/;
}
location /admin {
return 403;
}
/fileshttps://www.freebuf.com/articles/var/www/html/admin
Directory traversal due to apache uri parsing issues and incorrect configuration
CVE-2021-41773, CVE-2021-42013
<Directory />
AllowOverride none
Require all denied
</Directory>
<Location /admin>
Require all denied
</Location>
/icons/.%2e/admin
/icons/.%%32%65/admin
Directory traversal in node.js uri parsing
CVE-2017-14849
/static//foo//etc/passwd
Bypassing restricted file reading in jetty uri with %2e
CVE-2021-28164
/%2e/WEB-INF/web.xml
Bypassing file reading restriction in jetty uri through double uri decoding
CVE-2021-28169
/static?/%2557EB-INF/web.xml
Various forms of bypassing file reading in jetty URI [.]
CVE-2021-34429
/a/b/..%00/c/d/..%00/WEB-INF/web.xml
/.%00/WEB-INF/web.xml
/./WEB-INF/web.xml
JAVA request.getRequestURI() bypass, ctf question
if (request.getRequestURI().contains("..")) {
resp.getWriter().write("blacklist");
return;
}
if (request.getRequestURI().startsWith("/download")) {
resp.getWriter().write("unauthorized access");
} else {
chain.doFilter(req, resp);
}
The URL path obtained directly through getRequestURI() has some issues, such as not automatically urldecode, nor standardize (remove extra)/and..)
//download?filename=%2e%2e/WEB-INF/web.xml
Multi-node
Scenarios for bypassing using request body parsing differences in request smuggling are omitted
Access sensitive interfaces based on URI parsing differences
nginx-node, nginx-flask
Due to the inconsistency of request parsing and processing among different nodes, the security policy fails.
client ---> proxy(nginx) ---> webserver(node, flask)
nginx exact match, configuration file as follows
location = /admin {
deny all;
}
location = /admin/ {
deny all;
}
Handling of special bytes by web frameworks and mapping of interface processing.
# nginx security policy, exact match
GET /admin --> /admin The security policy is effective
GET /admins --> /admin The security policy is not effective
GET /admin[0xa0] --> /admin The security policy is not effective
# [0xff] represents the special byte in hexadecimal
GET /admin --> /admin Interface processing logic
GET /admins --> /admins Interface processing logic
GET /admin[0xa0] --> /admin Interface processing logic
| Web framework | Special bytes |
|---|---|
| Flask 3.0.2 | \x09 \x0a \x0b \x0c \x0d \x20 # ? |
| node:18.13.0 -express 4.18.3 | \x09 \x0c \x20 # / ? \xa0 |
With different versions of nginx, the handling of special bytes (400) may vary, leading to different actual verification effects.
Reference Link
https://developer.mozilla.org/en-US/docs/Web/HTTP/Status/403
https://portswigger.net/web-security/host-header/exploiting/lab-host-header-authentication-bypass
https://portswigger.net/web-security/access-control/lab-referer-based-access-control
https://portswigger.net/web-security/access-control/lab-url-based-access-control-can-be-circumvented
评论已关闭