
r77 can hide the following entities in all processes:
Files, directories, connections, named pipes, scheduled tasks;
Processes;
CPU usage;
Registry keys&values;
Services;
TCP&UDP connections;
This tool is compatible with 32-bit and 64-bit versions of Windows 7 and Windows 10.
Hiding through prefix
All entities named with the prefix '$77' will be hidden:
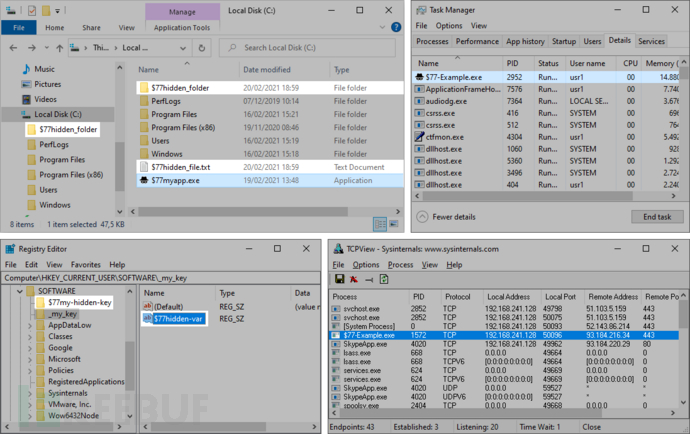
Configuration system
The dynamic configuration system allows researchers to hide processes through PID or hashes, hide the file system through complete paths, or hide TCP&UDP connections by specifying ports:
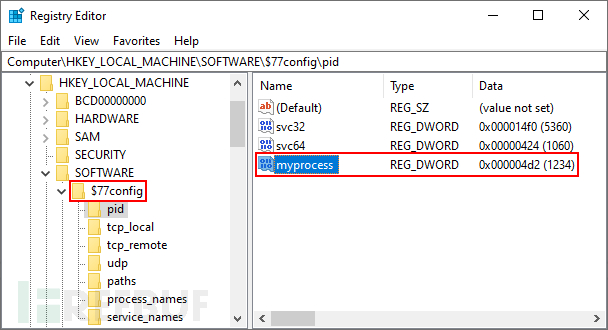
Configuration information is stored in 'HKEY_LOCAL_MACHINE\SOFTWARE\$77config' and can be written by any process without elevated privileges. The DACL of this key is set to grant full access to any user.
The '$77config' key will automatically hide after the Rootkit is injected into the registry editor.
Installation tool
r77 can be installed directly using the 'Install.exe' program. The installation tool will start the r77 service before the user logs in, and the background process will inject commands into all currently running and subsequently generated processes. Two processes are required to inject 32-bit and 64-bit processes, respectively, and both can be hidden using the configuration system and PID.
The 'Uninstall.exe' program is responsible for uninstalling r77 from the system and releasing the Rootkit's binding relationship with all processes.
Fileless persistence
The Rootkit will reside in system memory and will not write any files to the disk, and this mechanism is implemented in multiple stages.
Stage 1
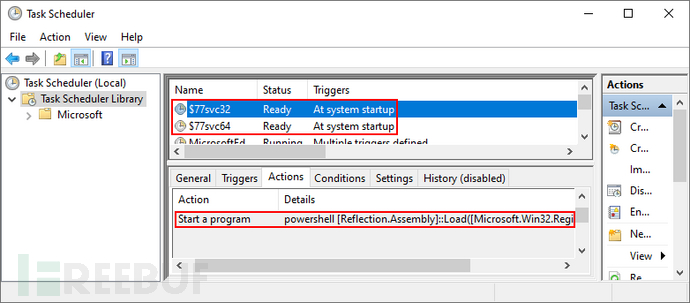
The installer creates two scheduled tasks for the 32-bit and 64-bit r77 service. Scheduled tasks indeed need to store files named $77svc32.job and $77svc64.job, which is the only exception to the fileless concept. However, once the Rootkit is running, the scheduled tasks will also be hidden by prefix.
The scheduled task will start 'powershell.exe' with the following command:
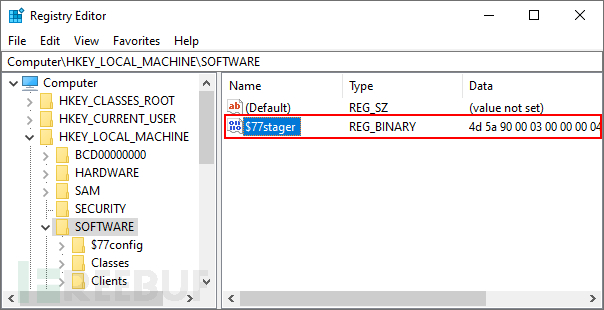
[Reflection.Assembly]::Load([Microsoft.Win32.Registry]::LocalMachine.OpenSubkey('SOFTWARE').GetValue('$77stager')).EntryPoint.Invoke($Null,$Null)This command is inline and does not require a .ps1 script. Here, the .NET Framework functionality of PowerShell is used to load the C# executable file from the registry and execute it in memory. Due to the maximum command line length of 260 (MAX_PATH), there is only enough space to execute simple Assembly.Load().EntryPoint.Invoke().
Stage 2
The executed C# code is the stager, which will create an r77 service process using the Process Hollowing technique. The r77 service is a local executable file, compiled in both 32-bit and 64-bit architectures. The parent process is set to winlogon.exe to increase deceptive (ambiguity). Additionally, these two processes are hidden by ID and are not visible in the Task Manager.
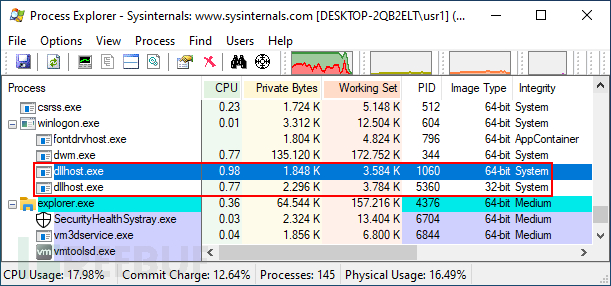
No executable files or DLLs have been stored on the disk. The stager is stored in the registry and loads the r77 service executable file from its resources.
Test environment
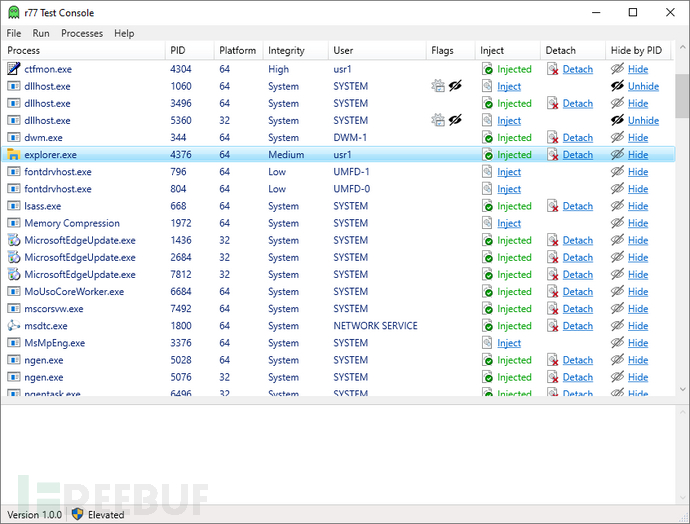
The test console can be used to inject r77 into a single process or to contact the binding relationship between the process and the Rootkit:
Tool download
r77 Rootkit 1.2.0.zip:【Click to download】(Password to extract: bytecode77)
Project address
r77-Rootkit:【GitHub Gateway】
Reference materials
https://bytecode77.com/downloads/r77%20Rootkit%20Technical%20Documentation.pdf
3 JD open-source hotkey—Automatic detection of hotkey, distributed consistency caching solution
3 Reasons to worry about bossware
What are parents worried about-
9. Get the information about network protocols supported on this computer
Be vigilant about the security issues of IoT device backdoors.
facebook hire through hacker cup(Facebook Hacker Cup)
Are you still confused about the timeout of SFTP connection?
评论已关闭