Preface:
In my recent work, I have been involved in APP testing and would like to share some personal experiences with everyone. My level is limited, please don't scold the big guys.
Firstly, learning to decompile is essential for APP defense and attack. There are roughly the following methods.
dex2jar
dex2jar is an Android decompilation tool that can convert .dex files to .jar files, which can help us analyze specific code.
Project address:
https://github.com/pxb1988/dex2jar/releases
Use:
Change the suffix of the tested apk to zip and extract it to get the .dex file.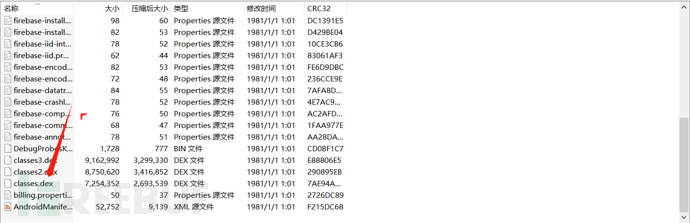
Extract the .dex file separately.
Use the command:d2j-dex2jar <.dex path> -o <output path+name.jar>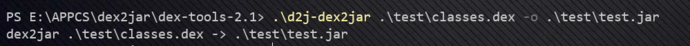
The .jar file will be in the output path
jd-gui

How to open the .jar file obtained, it is the jd-gui tool.
Project address:
https://github.com/java-decompiler/jd-gui/releases
jd-gui can provide a graphical interface for developers to test .jar file code.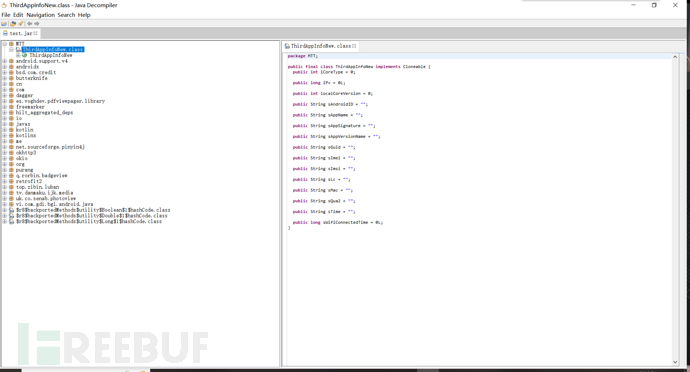
At this time, you can test whether the code has been obfuscated. The class files and methods that have been obfuscated are named with a, b, c, and so on.
Android killer
The first generation wonder Android killer, no more words, just see the picture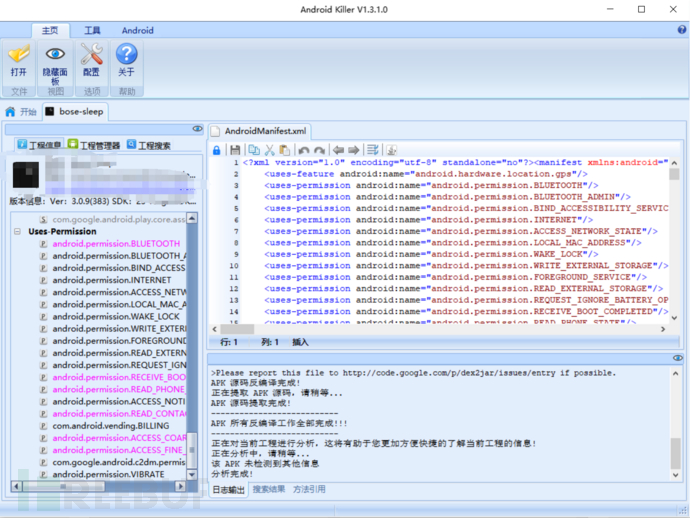
Android killer is a graphical tool that integrates various Android testing tools such as adb and dex2jar, which is very friendly to beginners.
Project address:
https://github.com/liaojack8/AndroidKiller
Apktool
apktool can also be used for decompilation and even recompilation.
Project address:
https://ibotpeaches.github.io/Apktool/
Use the command:java -jar apktool.jar d xxx.apk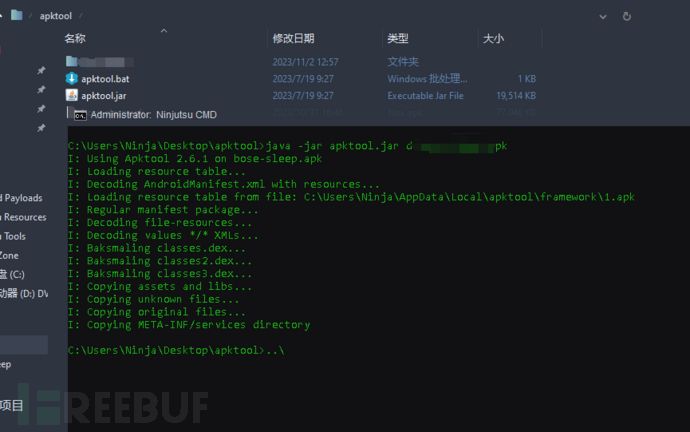
The decompiled content will be generated in the current directory.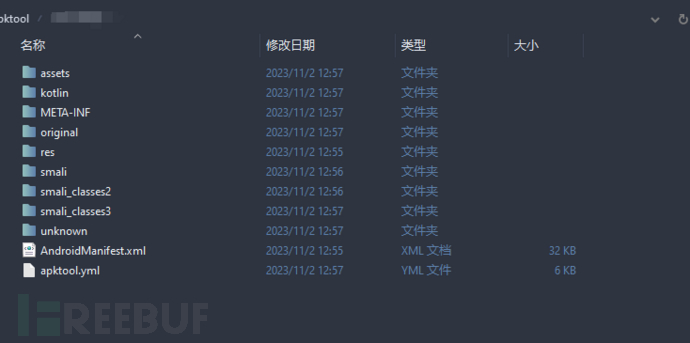
Of course, there are other ways, such as ApkBurster, etc., but I still use these tools in my daily life. I wish everyone can become APP defense and attack experts as soon as possible.
Expanding the Android attack surface: Analysis of React Native Android applications
Incremental installation and Android V4 signature introduction
Exploration and practice of optimizing the file size of Android dynamic link libraries
Android penetration testing 12: IDA dynamic debugging so
Full analysis of Android security strengthening technology (Part 2)
How to Use Yaazhini to Scan Security Vulnerabilities in Android APK API
Google Launches 'Email Masking' Feature to Help Users Hide Their Email Address
How to use CiLocks to bypass the lock screen function of Android
评论已关闭