
Brute-force four-digit PIN code;
Brute-force six-digit PIN code;
Use dictionary brute-force to crack the lock screen password;
Bypass lock screen protection (Antiguard), currently not supported for all operating system versions;
Device Root (SuperSU), currently not supported for all operating system versions;
Steal files;
Reset data;
Tool requirements
Adb (Android SDK);
USB cable;
Android emulator (Nethunter/Termux), requires Root;
Computer;
Compatibility
This tool supports normal use on Windows, Linux, and macOS operating systems, and has been fully tested on Kali Linux.
Tool installation
Researchers can use the following command to clone the source code of the project locally:
git clone https://github.com/tegal1337/CiLocks
Tool usage
After cloning the project locally, researchers need to switch to the project directory and provide executable permissions to CiLocks, and then run it directly:
cd CiLocks chmod +x cilocks bash cilocks
About Android emulator
Firstly, we need to install Busybox and then perform the Root operation on the device.
If the brute-force attack is not successful, please comment out the following code:
`# adb shell input keyevent 26`
Tool operation screenshot
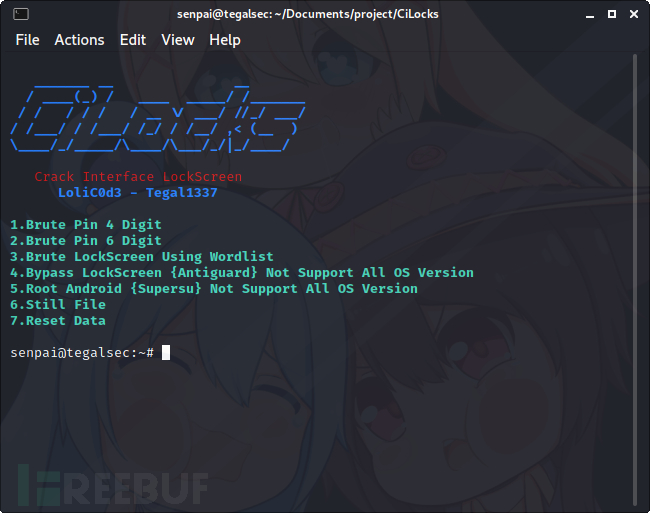
Operation demonstration
Bypass lock screen protection:https://youtu.be/PPMhzt4lGmU
Brute-force PIN code:https://youtu.be/D2xjJUQ9Lsw
Project address
CiLocks:【GitHub link】
Reference materials
https://stackoverflow.com/questions/29072501/how-to-unlock-android-phone-through-adb
http://www.hak5.org/episodes/hak5-1205
https://github.com/kosborn/p2p-adb
https://forum.xda-developers.com/t/universal-guide-root-any-android-device-manually.2684210/
https://stackoverflow.com/questions/14685721/how-can-i-do-factory-reset-using-adb-in-android
评论已关闭