About FindFunc
FindFunc is a powerful IDA Pro plugin that can help researchers easily find code functions that contain specific program sets, code byte patterns, specific naming, strings, or meet other various constraints. In short, the main purpose of FindFunc is to find known functions in binary files.
Use rule filtering
The main function of FindFunc is to allow users to specify a set of 'rules' or constraints that the code functions in IDA Pro must meet. FindFunc then searches and lists all functions that meet all the rules.

FindFunc plans and sorts rules in an intelligent manner, and the functional overview is as follows:
1. Currently, there are six rules available;
2. Code matching considers addressing size prefix and operand size prefix;
3. Function identification module;
4. Intelligent scheduling of performance rules;
5. Store/load rules to a file in simple ASCII format;
6, Provides a separate option page for experiments;
7, Copy rules between option pages via clipboard (format is the same as file format);
8, Save the entire session (all option pages) to a file;
9, Advanced copying of instruction bytes;
Tool requirements
IDAPro 7.x(7.6+)
Python 3
x86/x64 architecture
Tool download
FindFunc is an IDA Pro plugin developed in Python and does not require the installation of other dependency packages. Researchers can directly use the following command to clone the source code of this project locally:
git clone https://github.com/FelixBer/FindFunc.git
Next, copy the findfuncmain.py file in the project to the plugin directory of IDA Pro.
Available rules
Code pattern matching
mov r64, [r3*2 * 8 + 0x100] mov r, [r * 8 - 0x100] mov r64, [r*32 * 8 + imm] pass mov r, word [eax + r*32 * 8 - 0x100] any r64, r64 push imm push any
Search for given value (constant)
mov eax, 0x100 mov eax, [0x100] and al, [eax + ebx*8 + 0x100] push 0x100
Byte pattern matching
11 22 33 44 aa bb cc 11 22 33 ?? ?? bb cc -> ?? can be any byte
Advanced code copy
Copy all bytes
B8 44332211 mov eax,11223344 68 00000001 push 1000000 66:894424 70 mov word ptr ss:[esp+70],ax
Data will be copied in the following form:
b8 44 33 22 11 68 00 00 00 01 66 89 44 24 70
Copy non-constant values only
B8 44332211 mov eax,11223344 68 00000001 push 1000000 66:894424 70 mov word ptr ss:[esp+70],ax
Data will be copied in the following form:
b8 ?? ?? ?? ?? 68 ?? ?? ?? ?? 66 89 44 24 ??
Copy opcodes only
B8 44332211 mov eax,11223344 68 00000001 push 1000000 66:894424 70 mov word ptr ss:[esp+70],ax
Data will be copied in the following form:
b8 ?? ?? ?? ?? 68 ?? ?? ?? ?? 66 89 ?? ?? ??
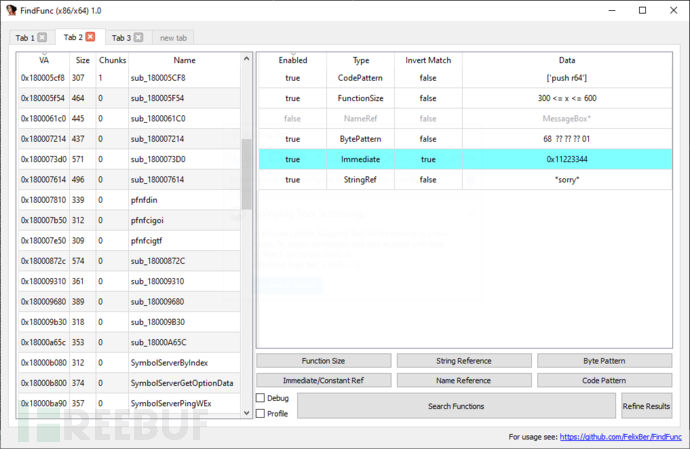
Tool operation screenshot
Project address
FindFunc:【GitHub link】
评论已关闭