
1. When searching for sensitive information in files within a nested directory structure, EvilTree has a significant advantage in that it can visually display which files contain the keywords/regular expression patterns provided by the user and their positions in the folder hierarchy;
2. The "tree" command itself is a magical tool for analyzing directory structures, and providing a standalone alternative command for post-intrusion testing is very convenient because it is not pre-installed in every Linux distribution, and its functionality is partially restricted on the Windows operating system.
Tool download
Since this tool is developed based on Python 3, researchers are first required to install and configure the Python 3 environment on their local devices. Next, use the following command to clone the project source code to the local machine:
git clone https://github.com/t3l3machus/eviltree.git
Tool usage examples
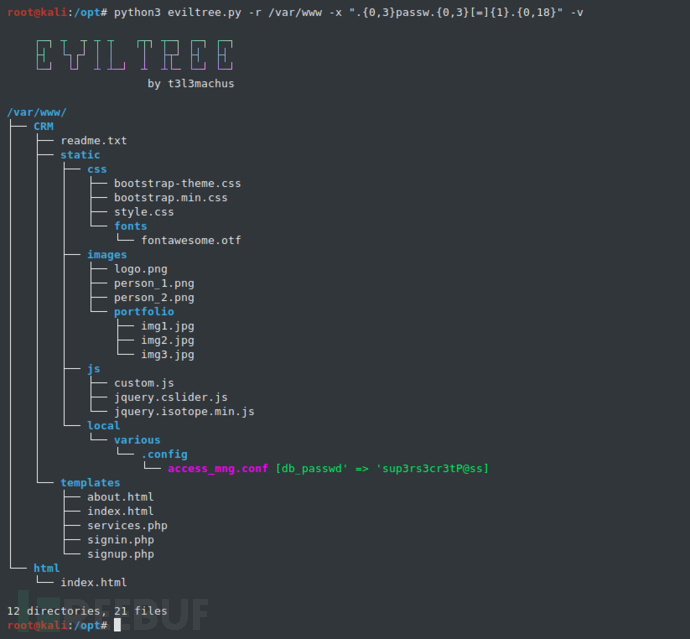
Example 1 - Execute a regular expression search to find the string "password = something" in /var/www:
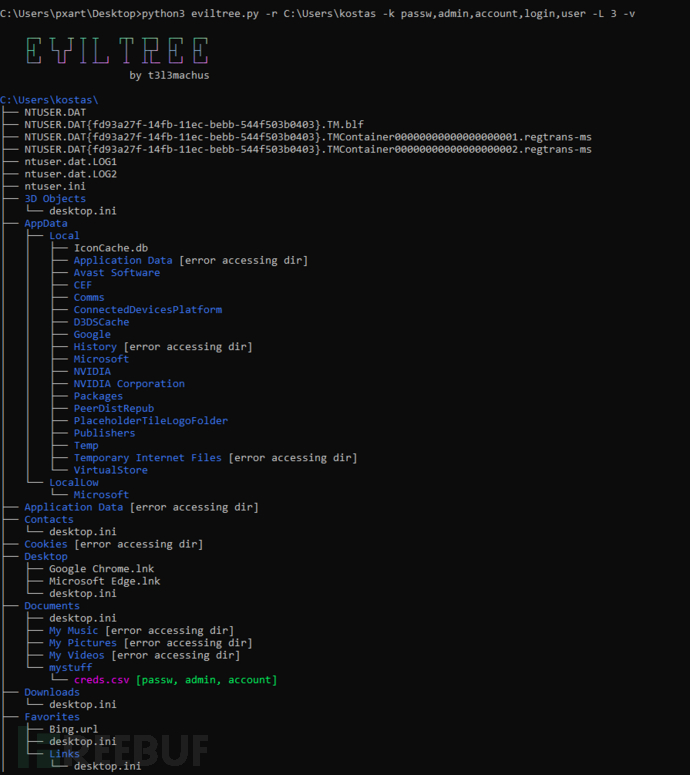
Example 2 - Use comma-separated keywords to search for sensitive information:
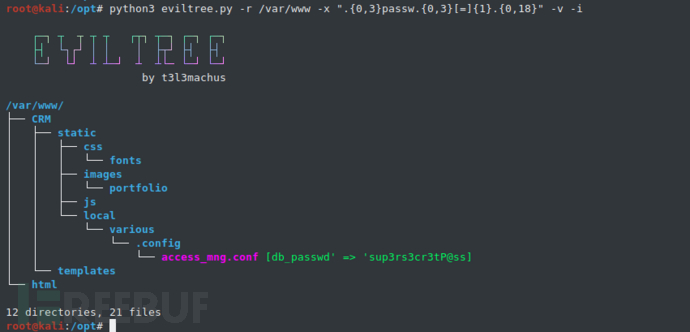
Example 3 - Use the "-i" parameter to only display the matching keywords/regular expressions content (reduce the length of the output content):
Useful keywords/regular expression patterns
Regular expressions available for searching passwords
-x ".{0,3}passw.{0,3}[=]{1}.{0,18}"Keywords available for searching sensitive information
-k passw,db_,admin,account,user,token
Project address
EvilTree:【GitHub Gateway】
Reference materials
评论已关闭