
Windows 11 21H2 64-bit
Windows 10 21H2 64-bit
Windows 8.1 64-bit
Note: Windows 7 does not support outputting UTF-8 reports in the command line terminal.
Build platform
Windows 10 1809 64-bit
Microsoft Visual Studio Community 2017
Tool features
1. Emotet generates its process name based on a specific dictionary of words and the serial number of the C drive, and EmoCheck can scan the running processes on the host and find the Emotet process from the process name.
2. Emotet will save the encoded process name in a specific registry entry, and EmoCheck can find and decode the registry value, and find it in the process list.
3. Supports detection of Emotet versions updated in April 2020.
4. Supports detection of Emotet versions updated in December 2020.
Tool download
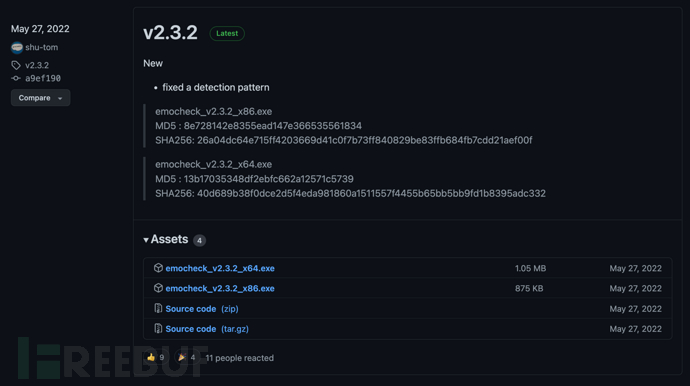
Researchers can access the project's [Releases pageDownload the latest version of this tool:
Command options
Specify the report output directory (default: current directory: )
/output [your output directory] -output [your output directory]
Disable console output:
/quiet -quiet
Output the report in JSON data format:
/json -json
Enable debug mode (no report):
/debug -debug
Display tool help information:
/help -help
Report example
Text format
[Emocheck v0.0.2] Scan time: 2020-02-10 13:06:20 ____________________________________________________ [Result] Detected Emotet process. [Emotet Process] Process Name : mstask.exe Process ID : 716 Image Path : C:\Users\[username]\AppData\Local\mstask.exe ____________________________________________________ Please remove or isolate the suspicious executable file.
JSON format
{
"scan_time":"2020-02-10 13:06:20",
"hostname":"[your hostname]",
"emocheck_version":"0.0.2",
"is_infected":"yes",
"emotet_processes":[
{
"process_name":"mstask.exe",
"process_id":"716",
"image_path":"C:\\Users\\[username]\\AppData\\Local\\mstask.exe"
}
]
}Report generation path
[current directory]\yyyymmddhhmmss_emocheck.txt [output path]\[computer name]_yyyymmddhhmmss_emocheck.txt [output path]\[computer name]_yyyymmddhhmmss_emocheck.json
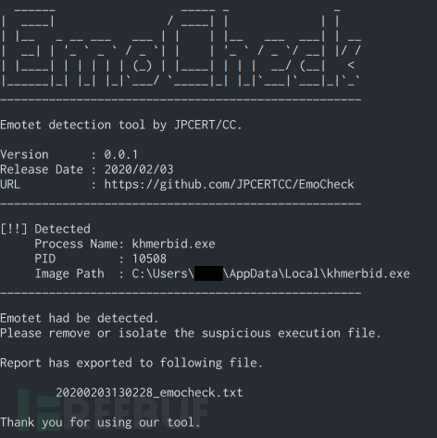
Tool operation screenshot
Project address
EmoCheck:【GitHub link】
评论已关闭