Idle Chat:
During this period, some automation scenarios have been created using the SOAR system, and I wanted to sort out and record the distinctive parts, but I didn't know how to categorize them. It seems that the S (Security) - O (Orchestration) - A (Automation) - R (Response) has been used as O-A. It can only be said that the collective wisdom of the masses is boundless, both a deep well and a valley :).
Ps: The following list of tasks can be completely implemented through scripts, and some of them were indeed done through scripts before. The reason for trying to implement them using SOAR is: (Having a hammer, one must use it~~~)
Script vs SOAR
Implementing certain functions solely through scripts, once personnel changes or turnover occur, due to differences in coding style, programming specifications, insufficient documentation, and operating environment, it is not only inconvenient to maintain the original scripts when changing users or transferring work, but also more time is needed to learn, and sometimes even refactoring is required.
If the script is used in a production environment to implement some functions, higher requirements are placed on the quality of script writing. It would be even better if functions and problems can be realized and solved through productization and standardization methods. Currently, the SOAR system can be considered as an option to replace scripts and complete some work, while also conveniently accumulating and inheriting security experience.
1. Currently, SOAR has three types of auxiliary businesses in operation
1. Based on scenarios, enhance and strengthen the capabilities of the security system to accelerate the operational process
1.1 Enhance antivirus system capabilities
Scenario description:Each time a large-scale trojan or virus appears domestically, several fixed departments will have some terminals affected. Sometimes they are reinfected after being disinfected, sometimes the virus cannot be killed, and occasionally there are no detections of infection, with intelligence provided by brothers and security vendors. Looking at the causes, 1) the virus library is updated later than the virus appears; 2) there are cases where the antivirus system is not updated in a timely manner; 3) the antivirus system is lightweightly deployed, and some old viruses are not in the terminal virus library. Note: The types of operating systems within the network, basically what can be thought of, are: (
Current solutions for the above issues: (Dear compatriots, if you have good methods, please share more, thank you!)
Issue 1): The virus can be detected and killed, but it will be reinfected repeatedly.
Solution: Link with firewalls and terminal management systems to limit network access for terminals that have been successfully scanned within the same network segment, with data only going out and not coming in until all the viruses within the network are cleared.
Issue 2)The virus can be detected, but it is not manageable.
Solution: Use terminal management systems and firewalls to isolate the infected terminals at two levels, actively remind manual processing, and restrict network access to the terminals after processing is completed.
Issue 3)The virus has not been detected.
Solution: Link with situational awareness, traffic analysis systems, and other security systems. When other systems issue virus alerts, but the antivirus system does not, remind the security personnel to contact the vendor for antivirus upgrade. At the same time, isolate the affected terminals with terminal management systems and firewalls, and follow the same subsequent processing methods as issues 1) and 2). ·············
In summary: In case of insufficient system capabilities, we compensate with the diversity of devices within the network. 
Logical diagram: Enhance antivirus capabilities

Scenario: Enhance antivirus system capabilities

Scenario: Enhance antivirus system capabilities through information collection in the same network segment

Scenario: Enhance antivirus system capabilities after review and unblocking
1.2 One-click configuration for the 'Many configuration parameters, prone to errors' function of security devices
Scenario description: When configuring SSL certificate removal on 3 Xian'an Century devices, it is necessary to configure at least 11 parameters from the 'Certificate Decomposition Information Table' collected by the security personnel. This task is not often done, and some parameters may be forgotten to fill in the method during configuration _-_! One-click configuration, a one-time solution.
Solution: After SOAR reads the certificate decomposition parameters from the excel table, it generates 9 commands to run on the specified devices.
 Logical diagram: One-click configuration for SSL certificate removal
Logical diagram: One-click configuration for SSL certificate removal 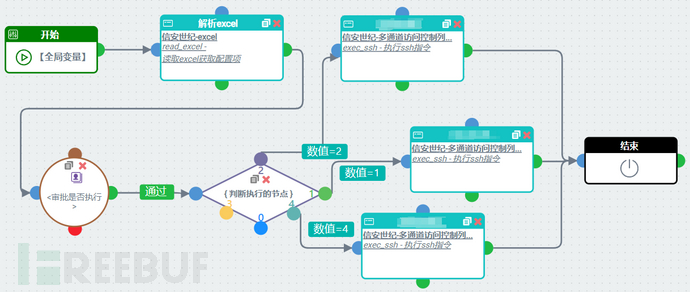
Scenario: One-click configuration for SSL certificate removal
2. Verify the functionality of the security system
(1) Verify system availability: Most of the existing security systems are connected to the log platform, and can actively alert the operation and maintenance personnel when the system is abnormal. However, there are cases where the system status is displayed as normal without any alarms, but the system policy does not take effect.
Ps: In this case, we will only know that the system is abnormal when there is a problem. The troubleshooting process is arduous, and in the end, it is found that the device function is not working, and you can imagine the mood at that time, which everyone understands.
Solution approach:Configure a policy on the devices that have experienced the above problems, according to the effective characteristics of the policy, cooperate with other systems within the network through the SOAR system, and check the existence of the characteristics on a timed basis to judge whether the system function is normal.
For example, the network access system NAC, which analyzes unauthenticated A terminals from the mirror traffic and sends redirection data packets to A to achieve mandatory authentication; when the function fails, the access terminals do not need to be authenticated to access the network. The solution is: regularly simulate the sending of access data packets by terminal A to check whether NAC sends redirection packets to A. If not found, it indicates that NAC is abnormal.

Logic diagram: NAC system availability verification
 Script: NAC system availability verification
Script: NAC system availability verification
Ps: This script is only for explaining the solution to the problem and does not include the function of executing scripts on a timed basis
3. Daily small tasks
Ps: Don't know how to classify, just some things that need to be done from time to time.
(1) Automatically obtain OA-approved DNS applications and record them in the asset system
Scenario description:Timely task monitoring OA, after finding a new DNS application form, synchronize the data to the asset system, and send WeChat Enterprise reminders at the same time. Avoid cumbersome manual asset entry operations.

Logic diagram: Asset entry

Script: OA approval data acquisition

Script: OA approval for asset entry
2) Technical support for dynamic password OTP
A. Obtain users who have not configured OTP and send reminders
Scenario description:Timely monitoring, find users who have not configured OTP and failed to log in, remind them proactively, and guide them to solve the problem themselves. If a reminder has already been given, no further reminders will be sent.

Script: OTP login failure

Script: Reminder information for OTP login failure
B. Check users whose dynamic password OTP is about to expire and send messages to remind them proactively
Scenario description:Obtain the users whose OTP is about to expire in the past 1 day, 7 days, 15 days, and 30 days, and send a reminder through WeChat Enterprise to notify them. Avoid the impact on users' use of OTP login after expiration.

Script: Reminder before OTP expiration
(3) Firewall configuration backup
Scenario description: Back up firewall configuration information through command scheduling and notify security personnel of the summary backup results.

Script: Firewall configuration backup
Old hat:
A big thank you to all the friends who have persevered to this point. The above are personal opinions, and I welcome everyone to discuss and exchange ideas together :) . If anyone has better scenarios, please feel free to share. Let's work together to make progress!
Currently, it is unknown how far SOAR can run on this unproductive path of O-A. As the understanding of SOAR deepens, there are indeed many scenarios that can be automated in work. Let's summarize these first, and sort out and summarize the follow-up achievements as they come.
Ps: With SOAR, the work before has indeed become easier, but there are more things to arrange scripts. Here's a weak wish, can the colleagues attending the next meeting scatter fewer thoughts about convenience? :(
评论已关闭