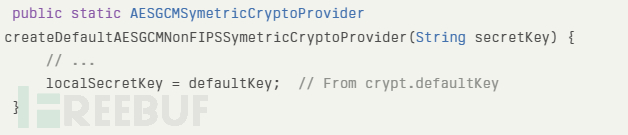
According to the NetSPI team, the vulnerability exists incom.solarwinds.whd.symmetric.AESGCMSymetricCryptoProviderclass, which is responsible for managing AES-GCM encryption of credentials stored in database backups and configuration files. Researchers have identified two main flaws:
Static and predictable encryption key
The default AES-GCM key (defaultKeyis hardcoded inwhd-crypto.jarfiles incryptconfig.propertiesThis allows for easy decryption without further system access of marked{AES}<base64>secret information.
For example,.whd.propertiesThis key is used for the PostgreSQL password embedded in
The second key derivation mechanism further exacerbated the risk.SecretKeyServiceImplThe class uses the PostgreSQL password embedded ininit_codean XOR operation with a static hexadecimal value (0xBABEFACE) to generate the key.
Due toinit_codeTypically below 0x10000, brute force attacks become computationally trivial:
Nonce reuse and key stream recovery
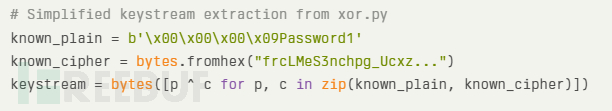
The security of AES-GCM depends on the use of a unique nonce for each encryption. However, Web Help Desk reused nonces in operation, allowing attackers to recover the key stream from known plaintext-ciphertext pairs.
Attackers can use known credentials (such asPassword1)Perform an XOR operation with the ciphertext to extract the key stream, and then decrypt other secret information encrypted with the same nonce:
Exploitation Pathways
Hardcoded keys:Decompile JAR files to extractcryptconfig.propertiesto obtaindefaultKey.
Brute-force the converted key:Calculateinit_code ^ 0xBABEFACEfor subscriber IDs (≤ 65,535 possibilities).
Decrypt secret information:Decrypt backups or.whd.propertiesthe AES-GCM ciphertext.
For example, use key 19950 to decryptfrcLMeS3nchpg_Ucxz...and obtainedPassword1which demonstrated how low-entropy keys make actual attacks possible.
In a penetration test, the NetSPI team decrypted aoauth2_client_secretand query the account password for LDAP. These credentials allow access throughConnect-AzAccountAccess Azure AD and perform lateral movement within the network.
Mitigation Measures
Limit backup access permissions:Grant access to .zip and .properties files only to necessary personnel.
Rotate all embedded confidential information:After the upgrade is complete, reset the database password, application programming interface (API) keys, and credentials for Lightweight Directory Access Protocol (LDAP) / Simple Mail Transfer Protocol (SMTP).
Audit the usage of AES-GCM:Ensure that the random numbers (one-time random values) used for each encryption are unique (for example, use counter-based random numbers or random random numbers with 96 bits of entropy).
Reference Source:
SolarWinds Web Help Desk Vulnerability Allows Hackers to Access Stored Passwords – PoC Released
评论已关闭