Introduction -- Chae$4
As the world of cyber threats develops at an astonishing speed, staying ahead of these digital dangers is becoming increasingly crucial for businesses. In January 2023, Morphisec discovered a shocking trend that many customers, mainly from the logistics and financial sectors, were attacked by a new advanced variant of the Chae$4 malware. Observations show that from April to June 2023, the complexity of the threat increased in multiple iterations.
Due to Morphisec's cutting-edge AMTD (Automatic Mobile Target Defense) technology, many of these attacks were intercepted before they could cause significant damage.

This is not an ordinary Chae$4 variant. It has undergone major reforms: from being completely rewritten in Python language, which led to a lower detection rate by traditional defense systems, to a comprehensive redesign and enhanced communication protocols. Moreover, it now also has a set of new modules, further enhancing its malicious capabilities.
The target of this malware is not random. It specifically focuses on customers of well-known platforms and banks, such as Mercado Libre, Mercado Pago, WhatsApp Web, Itau Bank, Caixa Bank, and even MetaMask. In addition, many content management (CMS) services have also been unable to escape, including WordPress, Joomla, Drupal, and Magento. It is noteworthy that the Chaes malware is not new in the field of cybersecurity. Its debut can be traced back to November 2020, when Cybereason researchers highlighted that its business mainly targets e-commerce customers in Latin America.
The new Chae$4 variant has been named by Morphisec as 'Chae$4' (Chae$4) because it is the fourth major variant, and the debug prints in the core module show 'Chae$4'.
ChaesHistorical Record and Overview
In November 2020, Cybereason released an initial research report on the Chaes malware. The report emphasizes that the malware has been active since at least mid-2020, primarily targeting e-commerce customers in Latin America, particularly Brazil.
This malicious software primarily targets MercadoLibre users, characterized by a multi-stage infection process, capable of stealing sensitive and financial data related to MercadoLibre, as well as utilizing various programming languages and LOLbins.
By January 2022, Avast published a subsequent study indicating a surge in the activity of Chaes in the fourth quarter of 2021. Avast delved into the different components of the malware, revealing its latest update: a refined infection chain, enhanced communication with the C2, new integrated modules (referred to as 'extensions'), and fine-grained details about each infection stage and module.
A few weeks later, in February 2022, this threat actor released a response to the Avast research, as shown in the following figure:
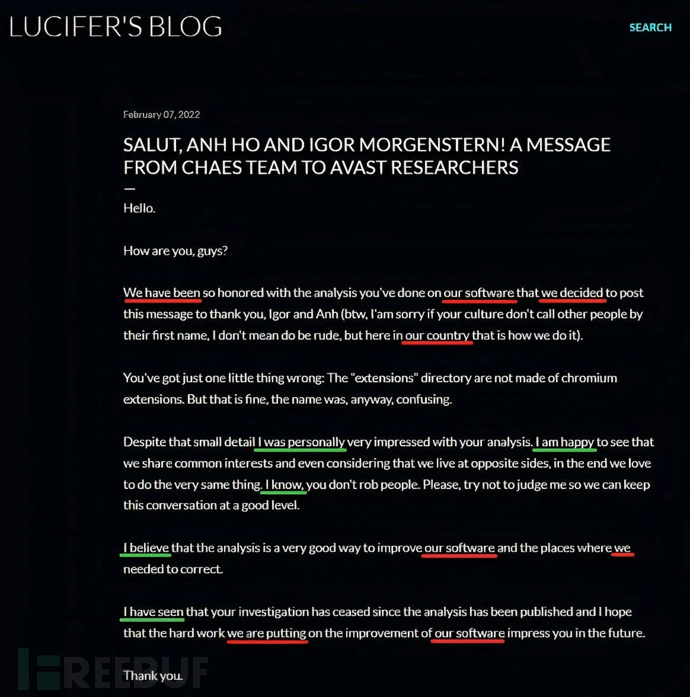
It has proven to be elusive to determine the nature of the threat actors--whether individuals or groups. The red highlighted parts suggest the possibility of a group, while the green highlighted parts reflect personal annotations. Given the ambiguity of the person's identity, the name 'Lucifer' was chosen for this threat actor. This decision was influenced by the blog name and identifier 'Lucifer6', which was used for encrypting communication with the C2 server.
Summarizes a series of developments, with December 2022 marking another critical moment as the research group SideChannel, from the Storm team, published further insights, introducing the malware's use of WMI to collect system data.
Upgrading to version 4
These previously mentioned research publications cover versions 1-3 of the CHAES malware. This latest version of Chaes introduces significant transformations and enhancements and is referred to as version 4 by Morphisec.
Major changes include:
- Improved code architecture and modularization.
- Addition of an encryption layer and enhanced stealth features.
- A shift to Python, experiencing decryption and dynamic execution in memory.
- Monitoring and intercepting activities of the Chromium browser using a customized method, replacing Puppeteer.
- An expanded service directory for credential theft.
- Utilization of WebSockets for primary communication between modules and the C2 server.
- Implementation of DGA for dynamic parsing of C2 server addresses.
Given the depth and breadth of the content of this review, the structure of the analysis is designed to cater to a wide range of readers, from SOC and CISO to detection engineers, researchers, and security enthusiasts.
The analysis first outlines the infection chain, which remains relatively consistent, followed by a concise summary of each module of the malware. Subsequent sections will delve deeper into the specific content of each stage/module.
Due to the use of repetitive mechanisms at various stages/modules of the malware, we have designated a section titled 'Additional Components.' Here, readers can find the complex details of each mechanism referenced throughout the entire post.
This structured approach ensures that readers can quickly gather an overview of the malware or immerse themselves in its complex components.
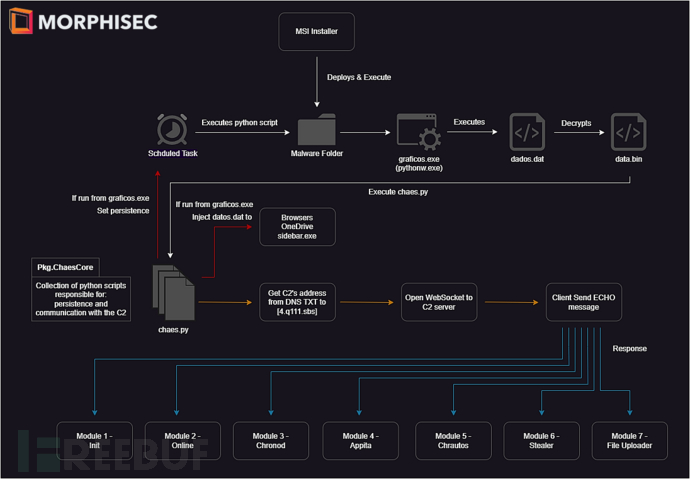
Note: Since there have been no major updates to the previous analysis and research notes (as mentioned earlier) in terms of delivery methods, this review will focus on the recent developments. For those unfamiliar with the infection methods, please refer to the referenced research.
The infection begins with the execution of a malicious, almost undetectable MSI installer, which is usually disguised as a Java JDE installer or antivirus software installer. Executing the malicious installer will cause the malware to}}
Required files are deployed and downloaded in a dedicated hardcoded folder under the %APPDATA%/<PROTUUESE_NAME> folder.
This folder contains Python libraries, Python executable files with different names, encrypted files, and Python scripts that will be used later. Next, the malicious software unpacks the core module, which we call ChaesCore, responsible for setting persistence using scheduled tasks and migrating to the target process. After the initialization phase, ChaesCore begins its malicious activities and communicates with the C2 address to download external modules and load them into the infected system.
Throughout the investigation, seven different modules were identified that can be independently updated without changing the core functions:
1. init Module - the first module sent by the attacker, used for identity recognition/new victim registration. It collects a large amount of data about the infected system.
2. Online Module - sends online messages back to the attacker. Like a beacon module, it monitors which victims are still active.
3. Chronod Module - a credential theft and clipper. This module is responsible for intercepting browser activity to steal user information, such as credentials sent during the login process, bank information during communication with bank websites, and has the clipping function to attempt to steal BTC, ETH, and PIX transfers.
4. Appita Module - very similar in structure and usage to the Chronod module, but it appears to be specifically targeted at the Itau bank's applications (itauplicativo.exe).
5. Chrautos Module -- an improved module based on the Chronod and Appita modules. It provides a better code architecture and can easily expand the goals and tasks of the module. The current version focuses on banking and WhatsApp data, but is still under development.
6. Theft Module - responsible for stealing data from browsers based on Chromium. The stolen data includes login information, credit cards, Cookies, and auto-fill data.
7. File Upload Module - capable of searching for files on the infected system and uploading them to the C2 server. In the current version, the module only uploads data related to the MetaMASK Chrome extension.
Most modules already existed in some form in previous versions, but this version provides a reimplementation for modules that have improved features, different codebases, and unique technologies to achieve their goals.
Another matter of note is the intense interest of participants in cryptocurrencies, which is represented by the use of the clipper to steal BTC and ETH, as well as the theft of MetaMask credentials and files through the file upload module.
评论已关闭