Introduction
With the rapid development of the digital age and the explosive growth of data volume, the importance of data security is rapidly increasing. Data in the network world is constantly facing the risks of being leaked, tampered with, and attacked. The data security issue originates from the change in the nature of data, such as business mobility: remote office and remote video conferences have become essential needs and high-risk areas for security vulnerabilities; terminal diversification has broken the original network boundaries, bringing pressure to the security protection; capability openness: openness brings risks such as API interface attacks and information leakage; third-party cooperation, applications, and SDKs have exacerbated the security risks of applications; scenario diversification: the complexity of business scenarios, centralized storage of data, and data sharing lead to data leakage, data ownership and responsibility separation, and under the pressure of rapid business delivery, the difficulty of comprehensive security control increases, causing business risks, etc.
With the three horses of the Chinese government, the 'Cybersecurity Law', the 'Data Security Law', and the 'Personal Information Protection Law', the top-level design of security laws has entered a comprehensive implementation stage, and the three laws complement each other to jointly constitute the legal security system of China's data security. They have also elevated data security to the level of law, which has also led to more and more law firms increasing their efforts to actively participate in data security and compliance construction work and enterprise data security compliance operations.As an established internet manufacturer, NetEase Technology has businesses worldwide, storing and processing a large amount of data assets, focusing on data governance and operation for more than a decade.
Data security situation and governance thinking

NetEase believes that the current situation of data security in China can be summarized from the following aspects:
- Laws and regulations:The state's attention to data security is increasing, and relevant laws, regulations, and standards are also being established and improved step by step. For example, the
- Infrastructure:Although China has made great achievements in information construction, data security also faces many challenges, such as the diversification, concealment, and influence of foreign policies of attack methods.
- Event impact:In recent years, due to the frequent occurrence of data leaks, illegal use and other events, the public awareness of data security has also gradually increased, and individuals and enterprises have begun to pay more and more attention to data security, and investment has also been increasing gradually.
- Talent construction:Although the demand for data security is growing, at present, there is a serious shortage of professional data security talents in China, and talent shortage has become a major problem restricting the work of data security.
NetEase believes that data security governance actually needs to focus on the reasons for the data problems themselves. Data security issues actually arise from the change in the nature of data, such as the mobileization of business data, the opening up of data capabilities, and the diversification of data scenarios mentioned earlier, which ultimately lead to the following impacts:It is difficult to see data assets, difficult to monitor data risks, difficult to effectively protect data, and difficult to trace data leaksThe four difficult situations, leading to inappropriate protection efforts, business imbalance, and high costs, etc. NetEase believes that to do well in data security operations, the following dimensions need to be considered:
- Data security is a top-down construction project, and it is first necessary to further improve laws and regulations:Detailed regulations are made for the security requirements of each link in the process of data collection, storage, processing, transmission, and destruction, and severe penalties are imposed on related violations.
- Carry out data security management with data assets as the core:Taking data assets as the core, the unified management of metadata at the level of data assets and data levels can be realized, which can be based on the classification and grading of data security and risk assessment to manage the basic attributes of data assets and monitor the use risks, and then link up with data security protection capabilities to build an effective data security governance solution that is in line with actual business.
- Prevention of data security risks:The core goal of data security governance is to reduce data security risks, therefore, establishing effective risk discovery means plays an important role in preventing the occurrence of data security incidents.
- Driving data security capability building with data usage scenarios:According to the actual usage of data, sort out multiple data business scenarios, collect the data interaction methods in data collection, production, application, operation and maintenance, sharing, and other scenarios, further abstract out data security measures to support and ensure business security, and then analyze the dependency relationship between data scenarios and security measures, thereby forming complete data security scenario-based operational steps.
- Formulating data security strategies: According to the management requirements of the entire lifecycle of data, the DMSS framework can be referred to, and targeted security strategies can be formulated through security strategies, combined with the security needs of business scenarios, to achieve security protection in the process of data flow.
Formulation of data security management specifications
The renowned consulting and analysis company in the information technology field, Gartner, has proposed the DSG (Data Security Governance) framework. Gartner believes that data security is not a simple stack of tools, but a complete chain from the decision-making level to the technical level, from management systems to tool support, running through the entire organizational structure from top to bottom. In fact, from balancing risks, identifying data, defining strategies, coordinating controls to the final management of risks, it is a full-cycle data security governance process. In summary, the DSG framework is a priority sorting indicator after balancing business needs and risks, and then defining data security strategies. To support the implementation of security strategies, the upper management of enterprises recommends formulating management specifications. The formulation of data management specifications can be considered from the following dimensions:
- Formulating data security strategies:The upper management of enterprises needs to formulate a clearly defined data security policy, including current policies, legislative provisions, industry standards, and best practices. This strategy must include all steps involved in information asset management, such as creating, storing, using, sharing, backing up, and destroying data.
- Understanding data assets:The upper management of enterprises should inventory and classify all internal data assets, clarify data owners, and establish data classification, marking, and protection levels.
- Data security training and education:While formulating policies, it is also necessary to ensure that all employees understand the implementation and importance of the policies, and enhance their data security awareness through regular training and education.
- Development of data handling and control:The upper management of enterprises needs to formulate data handling and control measures to ensure that appropriate physical and logical protection measures are taken when personnel handle sensitive, private, or non-public information, to prevent the misuse or improper storage of data.
- Data security impact assessment:For all data processing and changes, the top level of the enterprise needs to carry out a data security impact assessment to ensure that any change will not pose a threat to the data security of the enterprise.
- Continuous review and update:The top level of the enterprise not only needs to review the data security policy regularly, update it as necessary according to technological development and new threats, but also supervise and inspect the implementation of internal data processing.
- Emergency plan:In addition to preventive measures, enterprises should also formulate emergency plans for data security incidents, determine the steps to be taken when incidents occur, plan in advance for the handling of data leaks and losses, and try to minimize potential losses.
Implementation of data security classification and classification
Data classification and classification helps organizations better manage their data, more effectively protect their data, and better meet regulatory requirements. The classification framework can be divided from low to high into general data, important data, and core data according to the degree of harm caused by the data once it is tampered with, destroyed, leaked, or illegally obtained or utilized, to national security, public interest, or the legitimate rights and interests of individuals and organizations. The definitions of the three levels can be referred to in the following descriptions:
Level 1 data (general data):General data assets, with lower sensitivity, once leaked may cause certain damage to the interests of organizations or individuals.
Level 2 data (important data):Important data assets, with higher sensitivity, once leaked will cause damage to the safety and interests of organizations or individuals.
Level 3 data (core data):Core data assets, with the highest sensitivity, once leaked will cause particularly serious damage to the safety and interests of organizations or individuals.
The classification framework can be referred to from the following dimensions (the state has also issued relevant classification guidelines as shown in the figure below):
a) Citizen individual dimension:According to whether data can identify natural persons or be associated with natural persons, data is divided into personal information and non-personal information.
b) Public management dimension:In order to facilitate the management of data by national organs and promote data sharing and openness, data is divided into public data and social data.
c) Information dissemination dimension:According to whether data has public communication attributes, data is divided into public communication information and non-public communication information.
d) Industry field dimension:According to the industry fields involved in data processing, data is divided into industrial data, telecommunications data, financial data, transportation data, natural resources data, health and health data, education data, scientific and technological data, etc. Other industry fields can refer to GB/T 4754—2017 'National Economic Industry Classification'.
e) Organizational and operational dimension:Based on the requirements of national and industry data classification and classification, data processors can also divide the data of individuals or organizational users separately as user data according to the organizational and operational dimensions, and classify other data from the perspective of facilitating business production and management.

Based on Wanzhong's own data governance work, it is recommended that the implementation path for classification and grading can refer to the following processes:
- Investigation and analysis:Conduct a current situation demand investigation, including the confirmation of organizational system and specifications, and the scope of classification and grading.
- Classification and grading standard formulation:Output the classification and grading plan based on the results of the investigation and communication.
- Data asset surveying: Identify, sort, and output the 'Data Asset List' for all data assets within the organization.
- Design classification and grading rules:Design the standards, methods, and implementation strategies for data classification and grading.
- Manual + tool completes data classification and grading: Based on the written classification and grading methods and strategies, use manual assistance labeling + tool automatic identification for classification and grading labeling of the sorted data asset list, and output the draft of the 'Data Classification and Grading List'.
- Manual verification results:According to the characteristics of the organization and industry, manually adjust the strategy, check and verify the results of the labeling of the tool, ensure the accuracy of labeling, and output the 'Data Classification and Grading List' and 'Sensitive Data List'.
- Form classification and grading catalog:Form data cataloging, data resourceization, data serviceization, and data security.
- Regular assessment and optimization:Regularly assess the implementation of data classification and grading in enterprises, optimize and improve the classification and grading strategy according to the actual situation, and ensure the continuous and effective construction of data security compliance.
However,What really troubles enterprises is how to define the classification and grading of data; the principle of classification is based on systematics, standardization, stability, scalability, and clarity; the principle of grading is based on compliance, executability, timeliness, autonomy, rationality, and objectivity. Taking the classification of personal information as an example, there are relevant standards that can be referred to, as shown in the following figure:
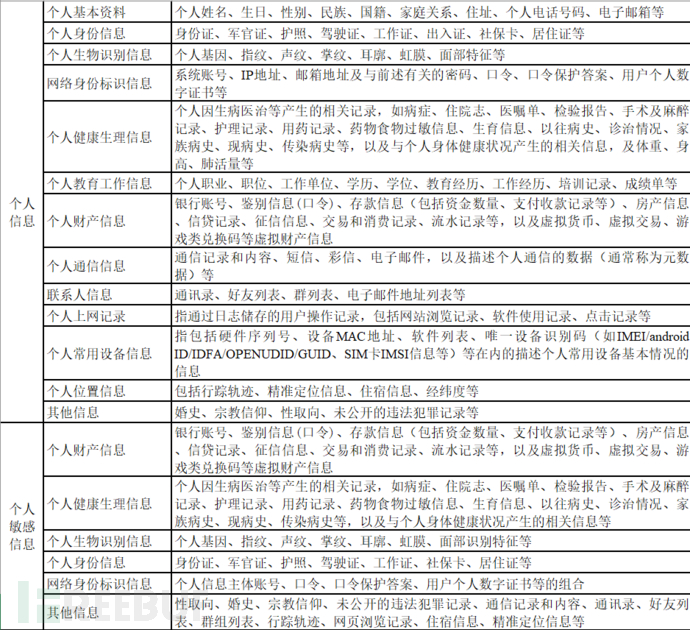
There are two ways to define classification and grading: one is rapid grading, and the other is classification-based grading. When it is not possible to determine the data security level through the 'rapid grading' method, the data provider analyzes and determines the level based on the scope and extent of the impact of the data content involved. The relevant explanations of the impact extent can be referred to in the following table:
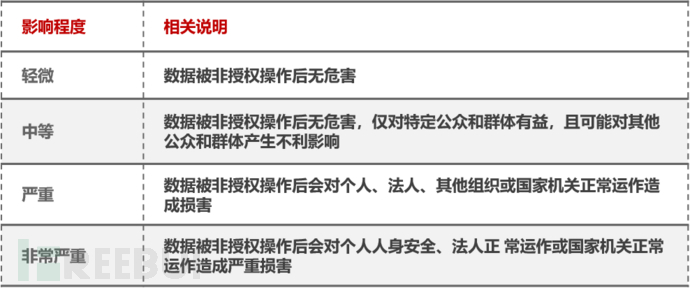
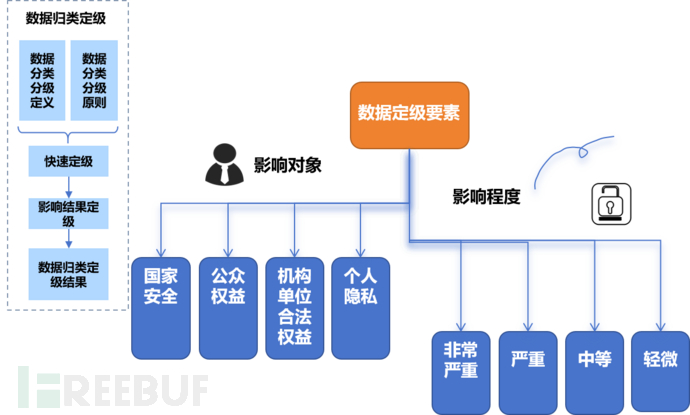
Summary
Data security governance and operation is formed by multiple independent work subsets, which effectively link individual entities through the establishment of an overall (general) working mechanism, thus forming an integrated, continuous, and manageable work process. Data security governance is the foundation for ensuring the stable operation of business in a secure environment. As part of the overall security governance of the organization, data security has both integrity and independence. Integrity emphasizes the combination with overall governance work, such as pre-event vulnerability detection, on-site security disposal, and post-event review and analysis. Independence emphasizes the pertinence of data security management to operational goals, such as data asset sorting (such as data flow, data classification and grading), data security protection strategies, continuous data security assessment, and the setting of data security operation and monitoring indicators.
评论已关闭