Chapter 1: Understanding Emergency Response
As cybersecurity professionals, we are not unfamiliar with cybersecurity. Cybersecurity refers to the protection of the hardware, software, and data within the network system, ensuring that it is not destroyed, altered, or leaked due to accidental or malicious reasons, guaranteeing the continuous, reliable, and normal operation of the system, and uninterrupted network services. In the face of various strange viruses and countless security vulnerabilities, establishing an effective cybersecurity emergency response system and continuously improving it has become an inevitable requirement for the development of the information society.
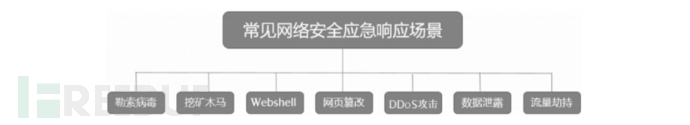
So far, network security emergency response is on the horizon. Network security emergency response refers to the monitoring, analysis, coordination, handling, and protection of asset security for security incidents that have occurred or may occur. Network security emergency response is mainly to make people aware of and prepared for network security, so that they can respond in an orderly manner and handle properly when they encounter sudden network security incidents.
Chapter 2: Emergency Response Process

For beginners, first we should know how to deal with a real emergency response work, and learning through the full process is more conducive to our quick start.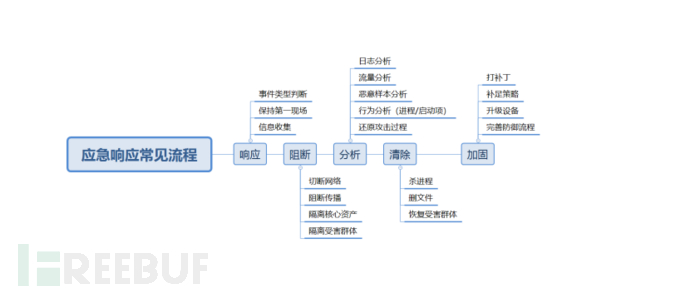
First, response:
(1) Event type judgment:
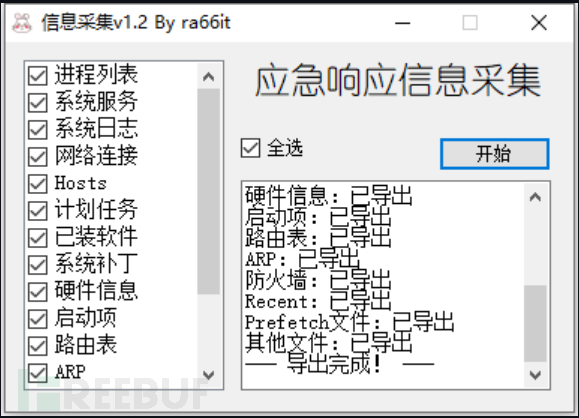
(2) Information collection
Information collection mainly involves: traffic, logs, memory of suspicious processes, compromised system images, malicious samples, customer asset collection, vulnerability test reports related to assets, and logs of defense equipment. Here is a recommended emergency response tool, link as follows:
https://github.com/ra66itmachine/GetInfo/
- Blocking
So-called blocking only has three steps: shut down the site, shut down the service, and pull out the network cable.
(1) Cutting off the network
There are many situations: business operations are normal after collapse, business operations are delayed after collapse, and business operations are suspended after collapse. Different situations require different network cuts.
The purpose of cutting off the network is to observe virus behavior, observe traffic characteristics, block internal communication, and block external connections.
For example: a large-scale collapse of a hospital, but business operations are normal, at this time, you can choose to cut off some unimportant hosts to observe behavior.
(2) Blocking spread
Spread includes: internal spread (infection), external spread (external link)
Internal spread (infection): process injection/migration, third-party software infection, service spread (ftp/ssh brute force, etc.)
External communication (external link): mining behavior, external link attack, c2 communication
Blocking the spread should start from: software level, traffic level, code level, and network level.
For example: investigate software hijacking, investigate traffic to find no file landing, use code audit to find container loading memory horses, and block the virus spreading through services.
(3) Isolation of core assets/Isolation of affected subject (group)
This step is the ultimate goal of emergency response, regardless of the implementation process or the tools used, it must be ensured that the isolated and compromised parties are isolated.
Isolating core assets is to achieve three principles: protection, avoidance of harm, and not causing harm.
Isolating the affected subject (group) is to protect the first scene, collect attacker information, and so on.
- Analysis
Analysis is the premise of abstraction, abstracting key information for analysis. The premise of abstraction is familiarity and understanding of attack methods.
(1) Analysis of Logs, Traffic, and Samples
Analyze the three major components: logs, traffic, and samples.
The main points of logs are: time, action, result; when this behavior starts and ends, what kind of action is login, logout, modification, etc., and what kind of result is login success/failure, upload/downloaded files, executed code, etc.
The main points of traffic are: status code, interaction process, data rationality; every status code of interaction, whether the interaction process conforms to the correct interaction process of this protocol, the filling of each field, whether the rendering of each traffic is normal.
The main points of the sample are: startup method, disguise method, and function; choose a sandbox or analysis tool according to the startup method; judge whether to add a shell for anti-kill and strike method according to the disguise method; judge the scope of damage according to the function.
Logs are static information, and emergency personnel need to clearly distinguish the content expressed by logs and quickly filter out suspicious points. Traffic and samples are dynamic information, and emergency personnel need to have certain penetration capabilities to distinguish interactive behavior.
(2) Behavior Analysis & Attack Restoration Process
Starting from behavior, restore the attack path and deduce the attack process.
Behavior analysis is based on the analysis of the three major components, combined with the system's performance to make analysis, such as: startup items, startup scripts, processes, memory, etc.
To restore the attack process, it is necessary to have a comprehensive judgment of the general situation of the attack and must possess penetration capabilities. On this basis, put the attack process into a sandbox to re-enact the attack process to provide assistance for subsequent steps.
①The following are the basic manual analysis and collection commands for emergency response to Windows and Linux that I have sorted out:
Step 1: System Troubleshooting
1. Windows system
Enter the command 【msinfo32】in the command line -- view services and drivers.
Enter the command 【systeminfo】in the command line -- simply view system version/host name.
2. Linux system
Enter the command 【lscpu】in the command line to view CPU-related information.
Enter the command 【uname -a】in the command line to view the current operating system information.
Enter the command 【cat /proc/version】in the command line to view the current operating system version information.
Enter the command 【lsmod】in the command line to view the information of all modules loaded into the system.
SecondStep: Startup Item
1. Windows system
Enter the command 【msconfig】in the command line to view the detailed information of startup items.
2. Linux system
By using the command 【cat /etc/init.d/rc.local】, you can view the content of the rc.local file under the init.d folder.
By using the command 【cat /etc/rc.local】, you can view the content of the rc.local file.
By using the command 【ls -alt /etc/init.d】, you can view the detailed information of all files under the init.d folder.
ThirdStep: Scheduled Task
1. Windows system
By entering the command 【Get-ScheduledTask】, you can view the information of all scheduled tasks in the current system.
Enter the command 【schtasks】in the command line to obtain information about task plans.
2. Linux system
Enter the command 【crontab -l】in the command line to view the current task plan.
Enter the command 【ls /etc/cron*】to view all task plan files under the etc directory.
FourthStep: Firewall
1. Windows system
Enter the command 【netsh】in the command line to view.
Use the command 【netsh Firewall show state】to display the current network configuration status of the firewall.
2. Linux system
None
Fifth step: Process investigation
1. Windows system
Enter the command 【tasklist】in the command line to display all processes running on the computer.
Enter the command 【tasklist /svc】to display the corresponding process and service for each process.
Enter the command 【tasklist /m】to query malicious processes that load DLLs.
Use the command 【netstat -ano | findstr "ESTABLISHED"】to view the current network connections and locate suspicious ESTABLISHED connections.
Use the command 【tasklist | find "2856"】to view the specific program.
The command 【Get-Wmi ObjectWin32_Process | select Name, ProcessId, ParentProcessId, Path】uses Get-WmiObject Win32_Process to represent obtaining all information about the process.
Use the command 【wmic process get name,parentprocessid,processid /format:csv】to display the process name, parent process ID, and process ID in csv format.
2. Linux system
Use the command 【ls -alt /proc/PID】to view the corresponding executable program.
Use the command 【kill -9 PID】to end the process.
SixthStep: Service investigation
1. Windows system
Enter the command 【services.msc】to open the 【Services】window.
2. Linux system
Entering the command 【chkconfig --list】in the command line can view the services running on the system.
SeventhStep: File trace investigation
1. Windows system
Check the related temp (tmp) directories under each disk, browser history, downloaded files, and cookie information.
The command 【forfiles /m *.exe /d +2020/2/12 /s /p c:\ /c "cmd /c echo @path @fdate @ftime" 2>null】is used to search for newly created exe files after 2020/2/12.
2. Linux system
Check the /tmp directory and the command directory /usr/bin /usr/sbin
Check the paths ~/.ssh and /etc/ssh, which are often used as some backdoor configuration paths
Use the command 【find / -ctime 0 -name "*.sh"】to find new sh files within a day
EighthStep: Log troubleshooting
1. Windows system
Use the command 【Get-WinEvent -FilterHashtable @{LogName='Security';ID='4625'}】
You can also obtain all log information under the security log with event ID 4625
FullEventLogView tool (green installation, easy to use)
2. Linux system
Logs in Linux systems are generally stored in the directory "/var/log/"
NinthStep: Memory troubleshooting and traffic analysis
Common extraction tools include Dumpit, Redline, RAM Capturer, FTK Imager, etc. -- upload the extracted files to the virustotal platform for scanning and judgment
Common memory analysis tools include Redline/Volatility, for example, wireshark
Use the command 【ip.addr ==ip】to filter specific IP addresses
Use the command 【ip.src==ip】to filter the specified source IP address
Directly enter protocols such as HTTP, HTTPS, SMTP, ARP, etc. for filtering
Use the command 【top.port==port number】or 【udp.port==port number】to filter ports
Use the command 【tcp contains strings】to search for keywords in data packets
TenthStep:Webshell in Linux system troubleshooting
find https://www.freebuf.com/articles/system/ -type f -name "*.jsp" |xargs grep "exec("
find https://www.freebuf.com/articles/system/ -type f -name "*.php" |xargs grep "eval("
find https://www.freebuf.com/articles/system/ -type f -name "*.asp" |xargs grep "execute("
find https://www.freebuf.com/articles/system/ -type f -name "*.aspx" |xargs grep "eval("
Search for web page files adapted to the current application under the directory, check if there are Webshell features, many trojans and large trojans are equipped with typical command execution feature functions, such as exec(), eval(), execute(), etc.
IV.、Clearing
What we need to do is no different from penetration - 'do a good job of cleaning up and hide yourself well'.
(1) In the case of non-resistance
In the absence of resistance, the most extreme is a complete reinstallation, slightly less is data migration followed by reinstallation of the system disk. In ordinary cases, we can carry out targeted process killing, file deletion, and anti-virus cleaning.
(2) In the case of resistance
The situation of resistance is: stubborn trojans and immortal trojans exist, or they are continuously attacked (APT).
In such a situation, the first choice is to apply patches if allowed, and then restore. Find the source of the attack behavior, patch the vulnerability first and then clear it.
V.Strengthening
Strengthening is to apply patches, impose restrictions on the system (network isolation, behavior management), upgrade defense equipment, and improve defense processes (deployment of defense equipment, personnel deployment, rule base upgrade)
Chapter 3: Emergency Response Practice
After understanding some basic concepts and guidance manuals of emergency response, of course, only practical operation can make us master the basic operations of emergency response more quickly.
Open the target machine, first look at the question, let's see what we need to do in emergency response~
Let's get started, provide us with a remote connection to the host, don't worry about it, let's log in and take a look
It was found that there was only one phpstudy_pro interface, and nothing else.
Step 1: Privilege escalation method
We first judge the type of emergency response event, then we can treat the symptoms accordingly. It's not a coincidence that the question asks to find a trojan, a backdoor, and the scenario provides the answer to find webshell. According to the套路, based on the webshell tools I have collected (as follows), let's get started~
Horse scan the site directory as shown in Figure 1, scanned out 16 suspicious backdoors as shown in Figure 2, check these .php files as shown in Figure 3, manually confirmed and none of them are, and no trojan was found as claimed
Figure 1
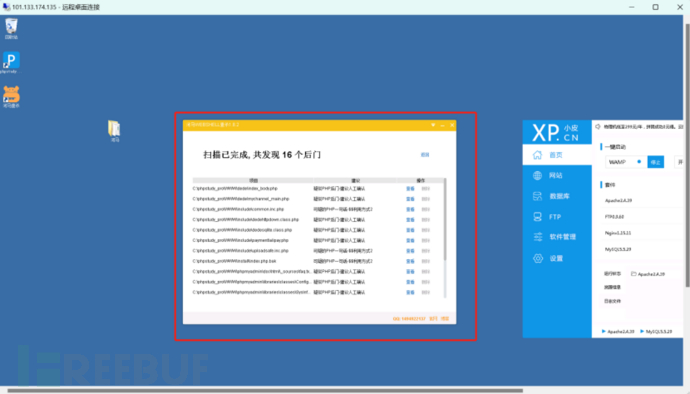
Figure 2
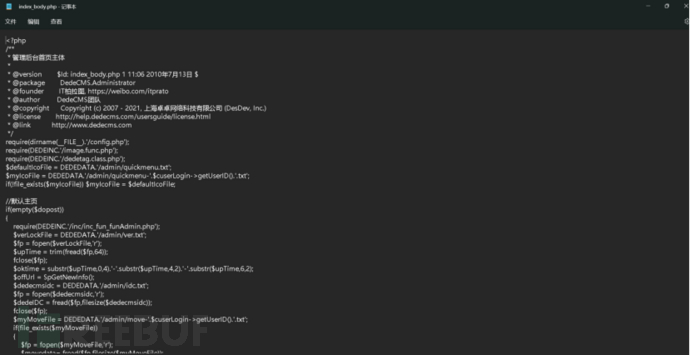
Figure 3
It seems that anti-virus bypassing has been done, let's check the apache logs
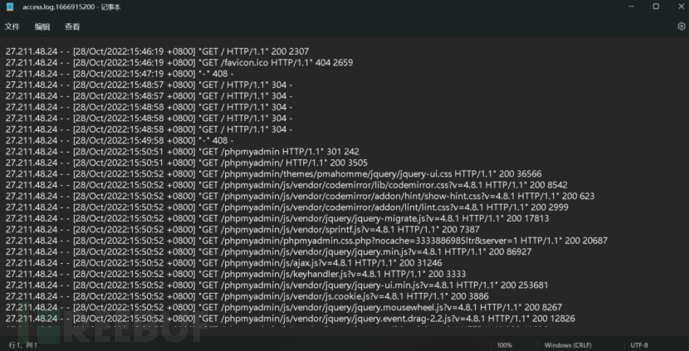
Through the logs, it can be found that at the beginning, SQL injection was being performed, various payloads, and then the directory scanning began
A preliminary look did not find the so-called trojan file, since he performed SQL injection, it is possible to get a shell through SQL and then escalate privileges, so I went to look under the sql folder
The result found the udf.dll file, then the first step of the hacker's privilege escalation should be udf privilege escalation
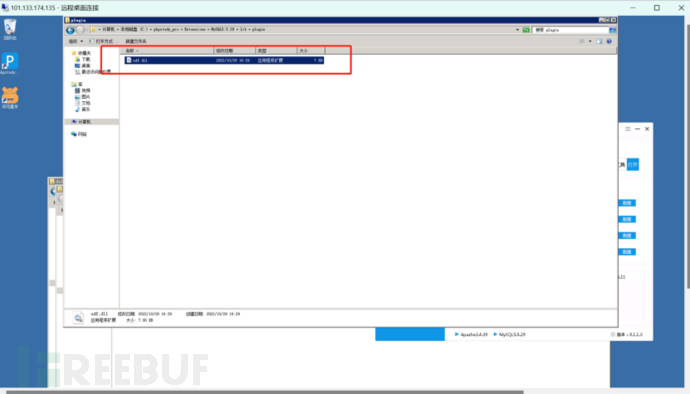
The second step is to find 'the webshell of hackers'
There is really nothing good to do here, you can only find it from the log analysis of Figure 1, which is a lot of work. The discovery is from a pile of post request logs, where a get request was found, and then a look was taken, and the result was indeed a webshell, the webshell is in /dede/inc/config_sys.php
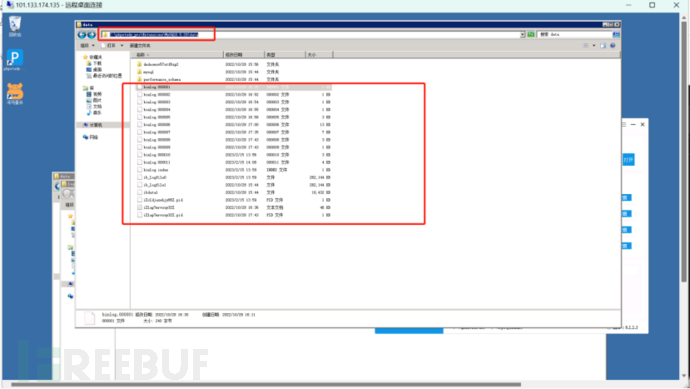
Figure 1
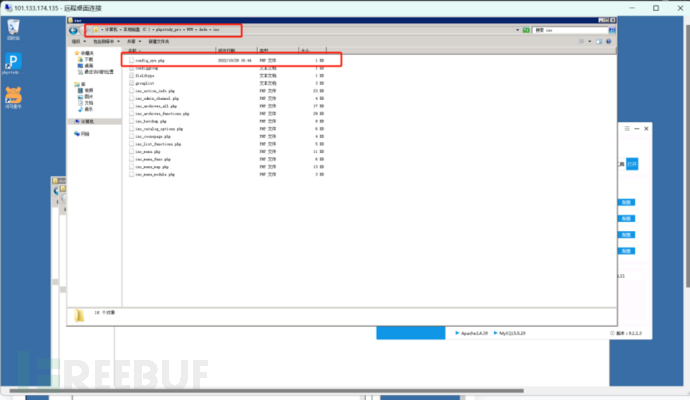
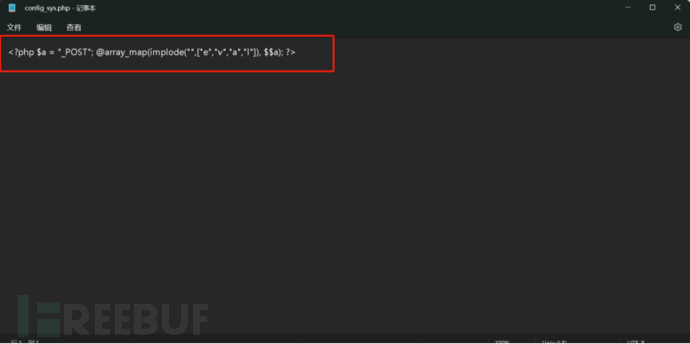
Step 3: Hacker's Account
This is relatively simple, the activity of viewing basic information in Windows and Linux, we use net user to view in Windows~
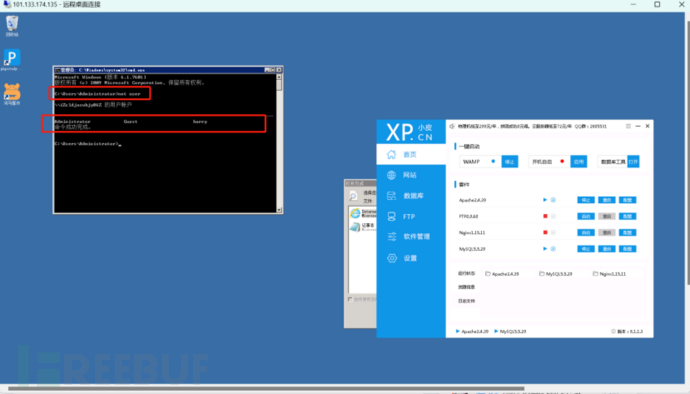
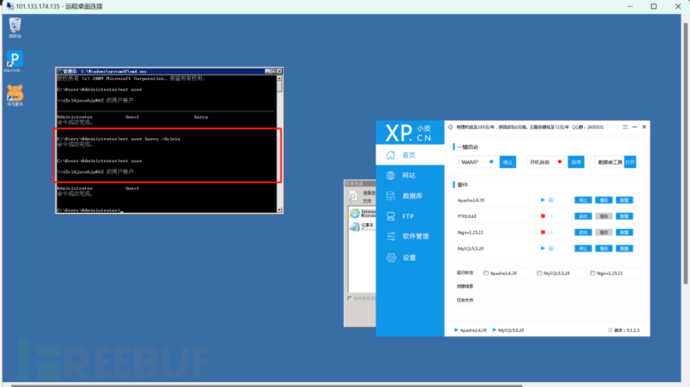
There are two ways to delete it: ① Command line mode: net user xxx /delete; ② Graphical interface: Server Manager -> Configuration -> Local Users and Groups -> Users, and delete the user
Step 4: Backdoor Trojan
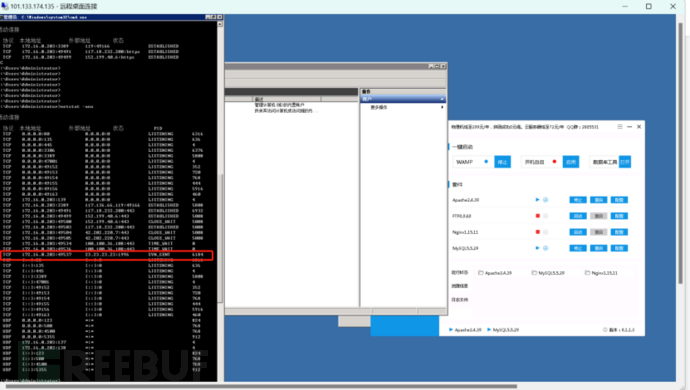
We use the command netstat -ano to view it, which is universal in both Windows and Linux, as follows, netstat -ano to view the current connections, and directly lock 23.23.23.23
Step 5: Strengthen the Server
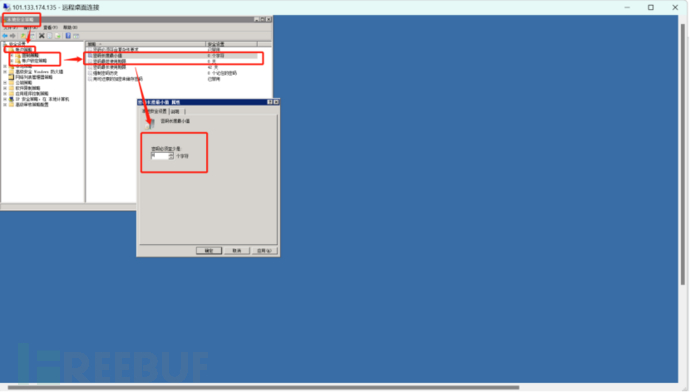
It is also a relatively simple question, we can modify the minimum password length in the Local Security Policy -> Account Policy -> Password Policy under the Start Menu.
By the way, in Linux, in the basic operations of strengthening the server, we use the vim editor to edit the /etc/pam.d/system-auth parameters.
Step 6: Delete the Trojan
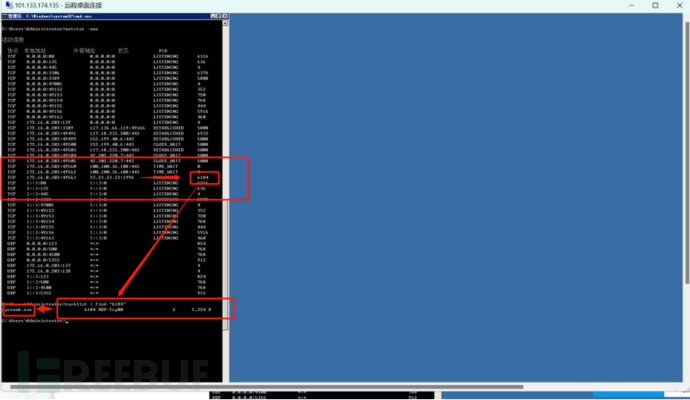
Find the process number 6184 through the IP obtained in step 4, use the command [tasklist | find "6184"] to view the specific program, and finally directly lock system6.exe, and the deletion is completed
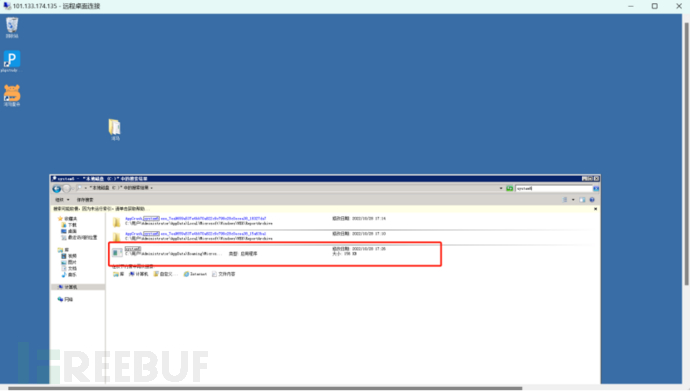
Ps: The system6.exe here is in the startup item, we can directly close the startup item in the system configuration and delete it, but it will not be successful. Here, I recommend D盾, after installation, you can also find system6.exe in the process view, and you can directly close the program and delete it.
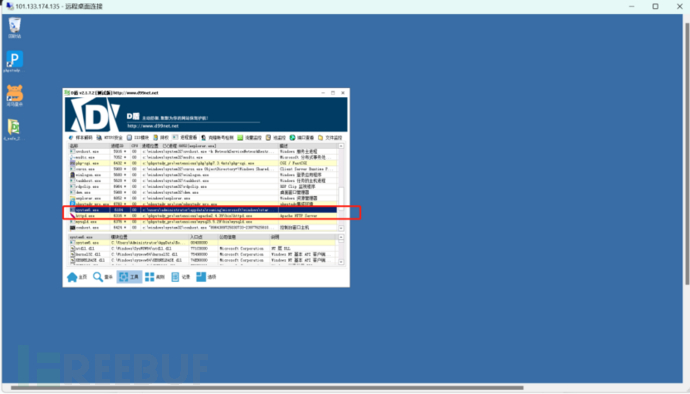
Step 7: Fix the Vulnerability
From the first step, it is known that it is a UDF privilege escalation, where UDF refers to the user-defined function. By adding new functions, the functionality of mysql is expanded. To use UDF for privilege escalation, file read and write operations need to be performed through sql, so limiting its file read and write permissions can fix the vulnerability. Here, searching for information, it is found that secure_file_priv can fix the vulnerability
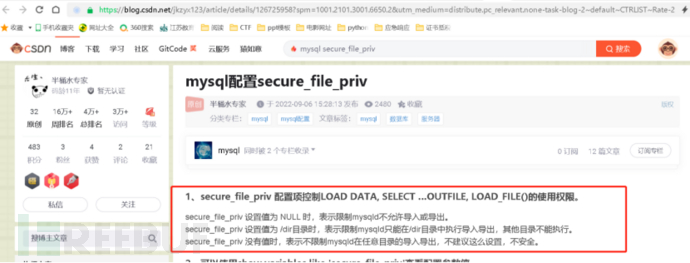
Below is the addition of secure_file_priv=null under the my.ini configuration file under the mysql configuration file [mysqld]:
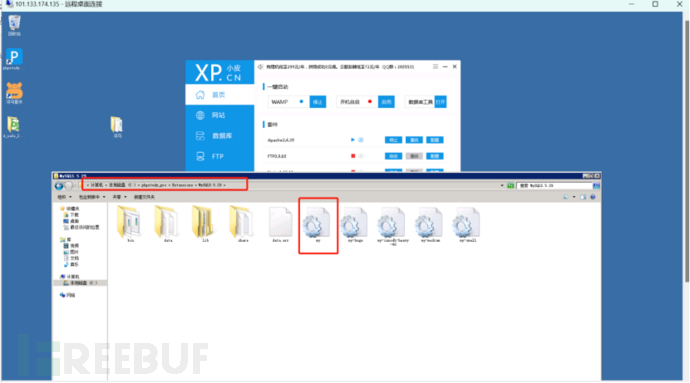
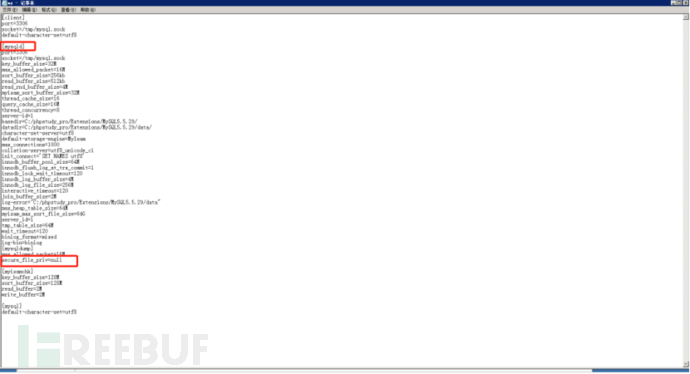
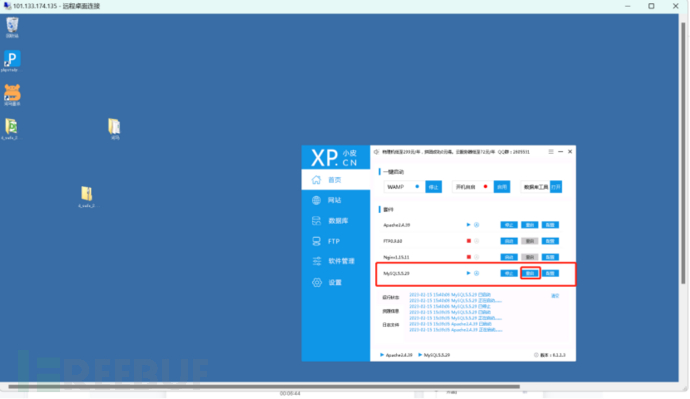
Restart the mysql database, then check it, done!
Theory plus practice, take emergency response with ease!
Chapter 4: Summary of Emergency Response
- Emergency personnel should have their own methodology, model the threats of different attacks, possess threat intelligence analysis capabilities, and combine tool assistance for on-site response and remote support.
Tools and investigation points are similar, the way to improve lies in whether the emergency personnel are familiar with this type of attack, and using features and behaviors to investigate can save more time.
3. Red and blue origin, emergency response belongs to the blue team, but must have certain penetration capabilities.
Ps: Below are some tools for improving efficiency that I have organized and summarized.
01, Multi-engine Online Virus Scanning
When a suspicious abnormal file is found, scan and detect the file using multiple different virus engines to confirm whether the file is malicious code.
①VirSCAN: Free multi-engine online virus scanning version 1.02, supporting 47 antivirus engines.
https://www.virscan.org/
②VirusTotal: A website providing free suspicious file analysis services.
https://www.virustotal.com/
③Jotti: A malicious software scanning system that uses several antivirus programs to scan suspicious files.
https://virusscan.jotti.org
02, Virus Detection and Removal Software
Under the condition of network connection, directly download antivirus software for full disk scanning and removal.
①360 Antivirus: Integrating five leading detection and removal engines with a high detection and removal rate.
https://sd.360.cn/
②Huorong Security Software: A very refined software that includes Huorong Sword, an analysis tool very useful for security professionals.
https://www.huorong.cn/
03, Virus Removal Tool
When you cannot connect to the internet, you can use a green, no-install virus removal tool to scan all files on your computer.
①Dr.Web CureIt: A green, no-install version with all the features of the standalone Dr.Web.
https://free.drweb.ru/download+cureit+free/
②Rootkit Backdoor Detection Tool: Used to check the tools behind rootkit locally.
chkrootkit:http://www.chkrootkit.org
04, Ransomware Search Engine
The most powerful tool for ransomware self-help, by entering the virus name or the encrypted file extension, you can find the decryption tool or learn about the virus details.
①【Tencent】 Ransomware Search Engine, supporting the search of over 1000+ common ransomware.
https://guanjia.qq.com/pr/ls/
②【360】 Ransomware Search Engine, supporting the search of over 800 common ransomware.
http://lesuobingdu.360.cn05
05, Webshell Detection Tool
When a website is hacked, we need a Webshell detection tool to help us find webshells and further investigate potential security vulnerabilities in the system.
①D盾_Web detection: http://www.d99net.net/index.asp
②Baidu WEBDIR+: https://scanner.baidu.com/
③Horse webshell detection: http://www.shellpub.com
06, Security Analysis Tools
①SysinternalsSuite: It includes a series of free system analysis tools, such as Process Explorer, Startup Item Analysis Tool AutoRuns, etc.
https://docs.microsoft.com/zh-cn/sysinternals/downloads/
②PCHunter: A powerful manual antivirus auxiliary tool.
http://www.xuetr.com
07, Log Analysis Tools
We often need to deal with various logs, such as system logs, WEB logs, DNS logs, etc., a simple and convenient log analysis tool can greatly improve efficiency.
①Log Parser: A log analysis tool produced by Microsoft, it is powerful and easy to use.
https://www.microsoft.com/en-us/download/details.aspx?id=24659
②EmEditor: It may be the fastest Windows text editor in the world, supporting large text up to 248 GB.
https://www.emeditor.com/#download
评论已关闭