Impacket introduction
Impacket is a collection of Python classes for handling network protocols. Impacket focuses on providing simple programming access to packets and certain protocols themselves (such as SMB1-3 and MSRPC) of the protocol implementation. Packets can be built from scratch or parsed from raw data, and the object-oriented API makes it simple to handle the deep structure of the protocol. The library provides a set of tools as examples of operations that can be performed in this library.
Impacket lateral movement tool
psexec.py: The Python version of the Microsoft tool psexec, supporting hash lateral movement and lateral movement through Windows services.

smbexec.py: Similar to psexec, it is a customized version that modifies the feature of psexec automatically installing the server to Admin$; smbexec manually installs the server files to a custom location.
atexec: Uses remote scheduled tasks to execute commands and obtain results.
wmiexec.py: Uses the WMI component to perform lateral movement through RPC on port 135.
dcomexec.py: Uses the DCOM interface provided by Windows for lateral movement, currently supporting MMC20.Application, ShellWindows, and ShellBrowserWindow objects.
In-depth analysis of tool features
psexec.py
Prerequisite: Port 445
Parameter usage help:
(1) lget {file} parameter can download the file on the target machine.
(2) The lput {src_file, dst_path} parameter is used to upload files to the target machine.
(3) -codec parameter is used to decode the return results of command execution.
Operation flow:
1. Connect to the admin$ shared folder on the remote computer.
2. Upload the Windows service program to the admin$ shared folder.
In impacket, the service program is located in the /impacket/examples/remcomsvc.py file, saved as binary data. The default exe has been marked by antivirus software of various manufacturers. You can modify the binary data to your own written exe for上线cs.
3. Open the \\target\pipe\svcctl pipe to connect to the remote machine's service control manager SCM, create and start the service.
4. After the service program is started, create the stdin, stdout, and stderr named pipes for command input and result output.
5. After the command execution is completed, reconnect to the remote computer's service control manager to stop the service, delete the service, and delete the service program.
smbexec.py
Prerequisite: Port 445
Parameter help:
(1) The -share parameter specifies the shared directory to be used, with the default being c$.
(2) The -service-name parameter specifies the name of the server, with the default being BTOBTO.
(3) The -shell_type parameter specifies the command execution environment, with options of cmd or powershell, with the default being cmd.
(4) The -mode parameter specifies the operation mode, supporting SERVER and SHARE modes, with the default being share mode.
Operation flow: (Take the default SHARE mode as an example)
1. Open the \\target\pipe\svcctl pipe to connect to the remote machine's service control manager SCM.
2. Obtain the command execution method as cmd or powershell based on the shell_type command-line parameter.
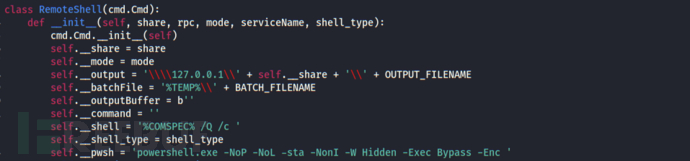
3. Create a service named 'service-name' with the program corresponding to cmd or powershell, which is determined by shell_type.
4. Redirect the command execution results to the __output file.
5. Connect to the remote shared folder and open the __output file to get the command execution results.
atexec.py
Prerequisite: Port 445
Note: atexec.exe creates remote scheduled tasks by initializing COM components, which requires the target to open port 135. Impacket uses RPC protocol, and only port 445 needs to be opened.
Operation flow:
1. Open the \\target\pipe\atsvc pipe to remotely connect to the target machine's remote scheduled task manager.
2. Create a randomly named scheduled task, where the corresponding program for the task is cmd, and the result of the command is redirected to a randomly named file in the c:\windows\temp directory with the .tmp extension.
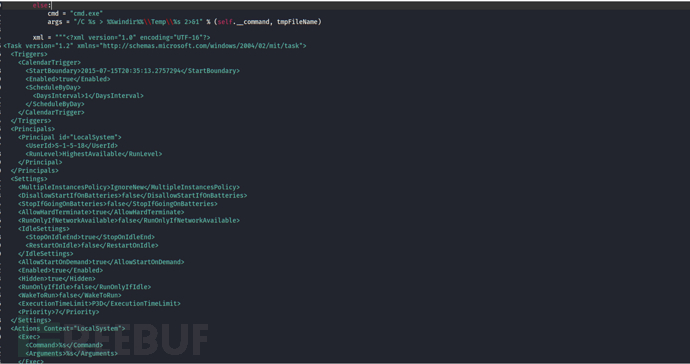
The default configuration information for the scheduled task is as follows:
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<Triggers>
<CalendarTrigger>
<StartBoundary>2015-07-15T20:35:13.2757294</StartBoundary>
<Enabled>true</Enabled>
<ScheduleByDay>
<DaysInterval>1</DaysInterval>
</ScheduleByDay>
</CalendarTrigger>
</Triggers>
<Principals>
<Principal id="LocalSystem">
<UserId>S-1-5-18</UserId>
<RunLevel>HighestAvailable</RunLevel>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>IgnoreNew</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>false</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>false</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>true</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>P3D</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="LocalSystem">
<Exec>
<Command>%s</Command>
<Arguments>%s</Arguments>
</Exec>
</Actions>
</Task>3. Wait for the scheduled task to complete and then delete the scheduled task.
4. Connect to the remote ADMIN$ shared folder to obtain the command execution results.
5. Delete the file recording the command execution results.
wmiexec.py
Prerequisites: Port 135, Port 445
Port 135 is used to connect to wmi, and port 445 is responsible for obtaining command execution results.
Parameter help:
(1) The -noOutput parameter specifies whether to obtain the command output results. If this parameter is set to True, wmiexec.py will not rely on port 445 and only need port 135.
(2) The lput {src_file, dst_path} parameter is used to upload files to the target machine.
(3) The lget {file} parameter can download files from the target machine.
(4) The -codec parameter is used to decode the return results of command execution.
(5) The lcd parameter is used to switch the working path.
(6) The -shell_type parameter specifies the command execution environment, which can be cmd or powershell, with cmd as the default.
Operation flow:
1. Determine whether to perform an SMB connection based on the value of the noOutput parameter. If the value is False, first establish an SMB connection. If the value is True, directly connect to the remote computer's //https://www.freebuf.com/articles/system/root/cimv2 via DCOM.
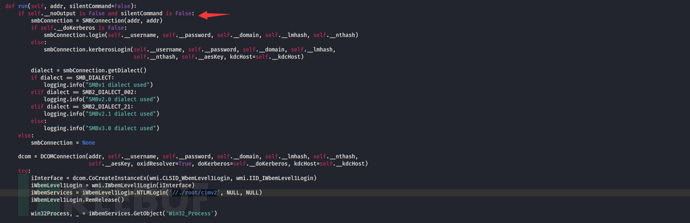
2. Obtain the Win32_Process object and create a cmd or powershell process based on the shell_type parameter.
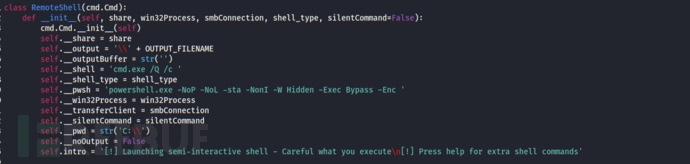
3. If command execution results need to be obtained, the results will be redirected to a file under the admin$ shared folder when creating a process, with the file name as "__current_time".
OUTPUT_FILENAME = '__' + str(time.time())
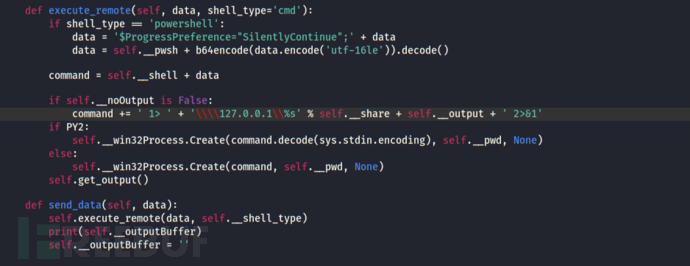
4, Obtain the command execution results by connecting to the remote computer's admin$ share.
dcomexec.py
Prerequisites: Port 135, Port 445
Port 135 is used to connect to DCOM, and port 445 is responsible for obtaining the command execution results.
The DCOM interfaces selected by dcomexec.py are as follows:
1, ShellWindows
Applicable to Windows 7, Windows 10, Windows Server 2012R2.
CLSID is: 9BA05972-F6A8-11CF-A442-00A0C90A8F39
2, ShellBrowserWindow
Applicable to Windows 10, Windows Server 2012R2.
CLSID is: C08AFD90-F2A1-11D1-8455-00A0C91F3880
3, MMC20
CLSID is: 49B2791A-B1AE-4C90-9B8E-E860BA07F889
The dcomexec.py process and the wmiexec usage have a high similarity, and the command execution results are redirected to the shared directory and then retrieved through the smb connection.
Summary
The core of the impacket lateral movement tool is actually the smbConnection and RPC protocol. A deep understanding of these protocols can greatly help and enhance our understanding of Windows authentication mechanisms.
评论已关闭