NoSQL injection
NoSQL injection is a vulnerability that attackers can use to interfere with the application's queries to the NoSQL database. NoSQL injection may allow attackers to:
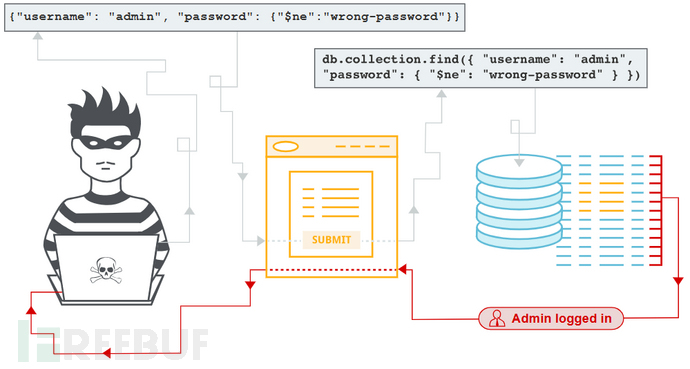
Bypass authentication or protection mechanisms.

Extract or edit data.
Lead to denial of service.
Execute code on the server
NoSQL databases store and retrieve data in formats other than traditional SQL relational tables. They use a variety of query languages instead of a general standard like SQL, and have fewer relational constraints.
More information
For more information about NoSQL databases and their differences from SQL databases, please refer to NoSQL databases.
NoSQL injection types
There are two different types of NoSQL injection:
Syntax injection: This happens when you can break the syntax of the NoSQL query, thereby injecting your own valid payload. The method is similar to that used in SQL injection, but due to the use of a series of query languages, query syntax types, and different data structures in NoSQL databases, the nature of the attack is also very different.
Operator injection - This occurs when using NoSQL query operators to operate queries.
In this topic, we will introduce how to test general NoSQL vulnerabilities, and then focus on how to exploit vulnerabilities in the most popular NoSQL database MongoDB. We also provide some experimental courses for you to practice what you have learned.
NoSQL syntax injection
You can detect NoSQL injection vulnerabilities by attempting to break the query syntax. To do this, test each input with fuzzy strings and special character pairs, if the application does not properly sanitize or filter these strings and special characters, they will trigger database errors or other detectable behaviors.
If you know the API language of the target database, use special characters and fuzzy strings related to that language. Otherwise, use various fuzzy strings to target multiple API languages.
Detect syntax injection in MongoDB
Consider a shopping application that displays products of different categories. When the user selectsSoda beveragesWhen the browser requests the URL below when the category is selected:
https://insecure-website.com/product/lookup?category=fizzy
This will cause the application to send a JSON query to retrieve relevant products from the product collection of the MongoDB database:
this.category
== 'fizzy'
To test if input may contain a vulnerability, submit a fuzzy string in the category parameter value. An example MongoDB string is
'"{
;$Foo}
$Foo \xYZ
Build the following attack using the fuzzy string:
https://insecure-website.com/product/lookup?category='%22%60%7b%0d%0a%3b%24Foo%7d%0d%0a%24Foo%20%5cxYZ%00
If this would change the original response, it may indicate that user input has not been properly filtered or sanitized.
Note
NoSQL injection vulnerabilities can occur in various situations, and you need to adjust the fuzzy string accordingly. Otherwise, you may only trigger validation errors, which means the application will never execute your query.
In this example, we inject a fuzzy string through the URL, so the string is URL-encoded. In some applications, you may need to inject payload through JSON properties. In this case, the payload will become'\"{\r;$Foo}\n$Foo \\xYZ\u0000
Determine which characters are processed
To determine which characters the application interprets as syntax, you can inject a single character. For example, you can submit ‘’’, which will result in the following MongoDB query:
this.category
== '''
If this would change the original response, it may indicate that the '' character has corrupted the query syntax and caused a syntax error. You can confirm this by submitting a valid query string in the input, for example, escaping the quote:
this.category
== '\''
If this does not result in a syntax error, it may mean that the application is vulnerable to injection attacks.
Confirm the behavior of the condition
After detecting a vulnerability, the next step is to determine whether it is possible to use NoSQL syntax to affect boolean conditions.
To test this, send two requests, one with a false condition and one with a true condition. For example, you can use conditional statements' && 0 && 'xand' && 1 && 'xSpecifically as follows:
https://insecure-website.com/product/lookup?category=fizzy'+%26%26+0+%26%26+'x
https://insecure-website.com/product/lookup?category=fizzy'+%26%26+1+%26%26+'x
If the application behaves differently, it indicates that the false condition affects the query logic, while the true condition does not. This suggests that injecting this syntax affects the server-side query.
Overriding existing conditions
Since it has been determined that it is possible to affect boolean conditions, you can try to override existing conditions to exploit the vulnerability. For example, you can inject a JavaScript condition that always evaluates to true, such as `||'1'=='1':
https://insecure-website.com/product/lookup?category=fizzy%27%7c%7c%27%31%27%3d%3d%27%31
This will result in the following MongoDB query:
this.category == 'fizzy'||'1'=='1'
Since the injected condition is always true, the modified query will return all items. This allows you to view all products in any category, including hidden or unknown categories.
Warning
Be cautious when injecting conditions that always evaluate to 'true' in NoSQL queries. Although this may be harmless in the initial context of the injection, it is common for applications to use data from a single request across multiple different queries. For example, if the application uses it to update or delete data, it may lead to unexpected data loss.
Detecting Syntax Injection in MongoDB - Lab
Target field: https://portswigger.net/web-security/nosql-injection/lab-nosql-injection-detection
AI Large Model Security: Prompt Injection Attack (Prompt Injection Attack)
DLL injection vs. Shellcode injection
Eighth. Blind injection based on boolean header injection
a hidden injection shellcode technology and defense method under Linux
How to conduct offensive and defensive exercise risk assessment for AI systems: Red Teaming Handbook
Combining ppid deception and far-thread injection to achieve DLL hollowing
评论已关闭
