One of the key steps in successfully setting up a Security Operations Center (SOC) is to define SIEM use cases.
Use cases can provide assistance and support on security analysts and threat monitoring targets. What is a use case? A use case can be a combination of multiple technical rules in a SIEM tool, or a combination of operations from multiple rules, depending on the specific requirements. Use cases can convert business threats into SIEM technical rules, then detect possible threats and send alerts to the SOC. Establishing and defining the correct use cases helps distinguish real alerts from false positives. Use cases will also provide recommended actions based on current or historical activities, which may be part of ongoing or future attacks. Understand how to set up SIEM use cases and their assistance to the SOC.
Part of the SIEM use cases

First of all, we can establish associations between various use cases. In essence, the effect of using use cases alone is not good. The combination of input or operation chains of use cases will determine the complexity or type of incoming attacks.
All use cases have three main components:
- Rules, used to detect and trigger alerts based on the target event
- Logic, define how to consider events or rules
- Operation, determine the operations that need to be executed when the logic or condition is met.
How to build a SIEM use case?
Be sure to determine a framework for the use case before starting to choose it.
1. Choose a tool, choose a tool that can design and map the use case framework. After deciding on the framework to use, start determining priorities and focus on dealing with business threats and risks that have an impact on the team's finance, reputation, and data.
2. Consider the category of attacks.This means defining commercial threats that may have an impact, such as phishing, data extraction, etc. Link each applicable type of attack to one or more commercial threats. Ultimately, we will get a map showing the relationship between business risks and attacks.
3. Creating another relationship: Specify the methods and ways to mitigate attacks by creating another relationship. Determine the listed types of attacks and place them in the selected framework. For example, we can classify external scanning attacks under the reconnaissance/targeting within the framework.
4. Establishing a connection between the two relationships: The relationship between business threats and attacks, as well as the relationship between attacks and frameworks.
On this basis, you can incorporate these relationships into the SIEM use case. The identified business threats will be high-level use cases. We can further break them down into low-level use cases. There can be two or three nested use cases in each high-level use case. Generally, when we find some overlaps in the case of how use cases apply to multiple business threats/high-level use cases. For example, if there is already a high-level use case of 'data loss', the low-level use cases nested in the data loss use case will be server leakage, exporting data from the server, and unauthorized administrative activities on the server.
Each low-level use case is logically connected to certain types of attacks, which helps define technical rules. Each low-level use case may be suitable for multiple rules, and a rule may be related to multiple low-level use cases. It is necessary to show the connection by defining its structure, because this will further define the log sources required to make the technical rules effective.
SIEM Use Case Lifecycle
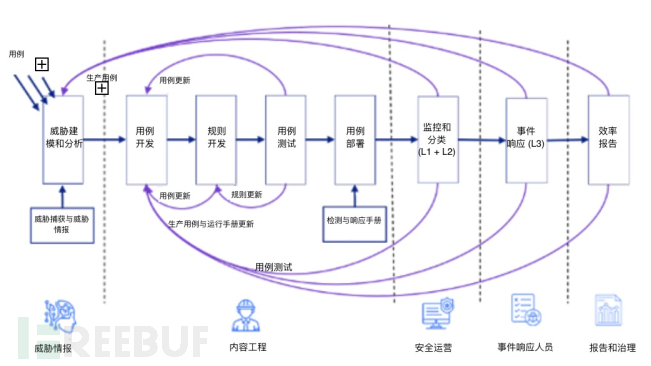
During the lifecycle of a SIEM use case, there are multiple input points. This depends on the source from which data is fed into the use case. In the daily operations of the SOC, the use case will obtain input information through level 1 or 2 SOC analysts. Most of these input information are attributed to false positive detection. If the SOC is equipped with threat hunting and intelligence functions, information will be input based on the traffic not detected in the current use case or the new threats identified in the threat intelligence input information.
Based on the false positives found by level 1 and level 2 SOC analysts, we can reduce the number of bad alerts generated by the SIEM platform by modifying the use cases. SIEM administrators or use case engineers will also study the efficiency of the use cases by identifying semi-matching events, the number of generated duplicate alerts, and other standards.
Use case management
Like any other application or product, use cases must be managed and maintained from time to time to ensure their effectiveness. Use cases must go through multiple stages to complete the cycle from planning to deployment:
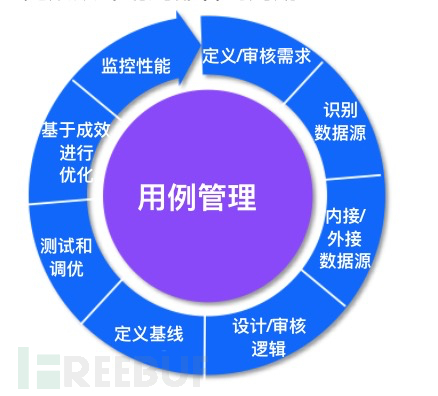
Define/audit requirements:Before setting up the SIEM use case, we need to consider business threats and risks first. For how to build use cases, please refer to the above chapters.
Identify data sources:After clearly defining the target data, we then need to consider how to find these data. Attacks are defined based on the attack source.
Internal/external data sources:Start integrating the identified data/logs sources into the SIEM. This may require some configuration at the source, depending on the specific SIEM configuration. There may also be some changes to the firewall to ensure communication between the data source and the SIEM.
Design/audit logic:After obtaining the data/logs, we can view the logs and determine the content required to detect attacks (event fields). An important factor in building this logic/rule is to identify the correct event fields to perform correlation or aggregation.
Define baseline:In the use case/rules, define thresholds/baselines to aggregate similar events.
Testing and tuning:We must test the logic and baseline defined in the use cases. Based on the test results, we need to make adjustments to ensure the reduction of noise.
Optimize based on effectiveness:Based on testing, optimize the baseline to detect attacks.
Monitor performance:Deploy the use cases in production and start monitoring performance and generated alerts to check for false positives and overall operation.
Use case framework
We can use various frameworks to build SIEM use cases. In this example, let's understand two of the most effective frameworks: MITRE ATT&CK and Lockheed Martin Cyber Kill Chain. Both frameworks consist of two parts: pre-attack and post-attack. Pre-attack includes all use cases/rules related to target selection and vulnerability discovery. Post-attack involves use cases/rules related to delivery, execution, connection, and extraction.
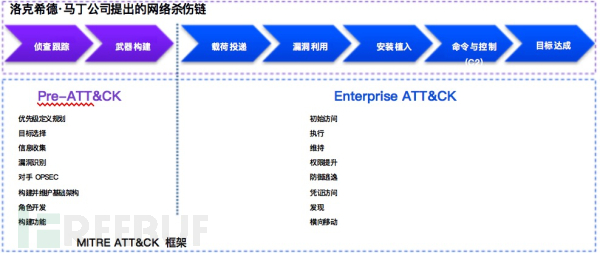
The SIEM use case is an important link to ensure that the SOC is in the best state. These use cases can determine whether an attack has been detected or missed within the network, as well as at what stage we can detect incoming threats. The level of expertise of the SOC analysts will also vary depending on the defined use cases. The higher the optimization and perfection of the use cases, the higher the quality of detection and analysis.
评论已关闭